当前位置:网站首页>UCI and data multiplexing are transmitted on Pusch - placement of data and UCI positions (Part III)
UCI and data multiplexing are transmitted on Pusch - placement of data and UCI positions (Part III)
2022-07-03 09:39:00 【Communication pawn】
data and uci Placement of reuse positions
Frequency hopping will not be introduced this time , Follow the procedure of no frequency hopping .
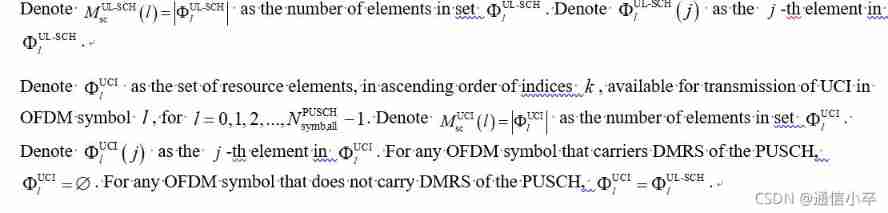
Parameters 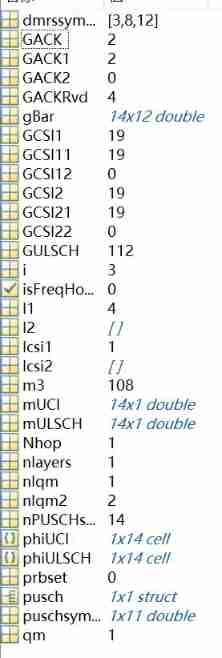
step1: stay harq-ack Of bit The number is less than or equal to 2 When , Do the following .
### This Agreement specifically states , If ack Of bit The number is less than or equal to 2 Always follow bit Number equals 2 To calculate the space for reservation .



for i = 1:numel(lprime)
sym = lprime(i);
while mACKcount(i) < GACKRvdTemp(i)
if sym > nPUSCHsymall
% Check for the symbol number greater than the number
% of PUSCH allocated symbols in each hop and avoid out
% of bounds indexing
break;
end
if mUCI(sym) > 0
% Total number of reserved elements remaining per hop
numACKRvd = GACKRvdTemp(i)-mACKcount(i);
if numACKRvd >= mUCI(sym)*nlqm
d = 1;
mREcount = mBarULSCH(sym);
else
d = floor((mUCI(sym)*nlqm)/numACKRvd);
mREcount = ceil(numACKRvd/nlqm);
end
phiBarRvd{sym} = phiBarULSCH{sym}((0:mREcount-1)*d+1);
mACKcount(i) = mACKcount(i) + mREcount*nlqm;
end
sym = sym+1;
end % while
end % for Nhop
% Number of reserved elements in each OFDM symbol
mPhiSCRVD = zeros(nPUSCHsymall,1);
for i = 1:nPUSCHsymall
mPhiSCRVD(i) = length(phiBarRvd{i});
end
step2: stay harq-ack Of bit Number greater than 2 When , Do the following .




% Step 2
% ACK (oACK > 2)
if ~GACKRvd && GACK
GACKTemp = [GACK1 GACK2];
lprime = [l1 l2];
mACKcount = [0 0];
mACKcountall = 0;
for i = 1:numel(lprime)
sym = lprime(i);
while mACKcount(i) < GACKTemp(i)
if sym > nPUSCHsymall
% Check for the symbol number greater than the number
% of PUSCH allocated symbols in each hop and avoid out
% of bounds indexing
break;
end
if mUCI(sym) > 0
% Total number of remaining HARQ-ACK bits to be
% accommodated per hop
numACK = GACKTemp(i)-mACKcount(i);
if numACK >= mUCI(sym)*nlqm
d = 1;
mREcount = mUCI(sym);
else
d = floor((mUCI(sym)*nlqm)/numACK);
mREcount = ceil(numACK/nlqm);
end
% Place coded HARQ-ACK bits in gBar at relevant
% positions
k = phiUCI{sym}((0:mREcount-1)*d+1);
gBar(sym,k+1,1:nlqm) = -1; % -1 for HARQ-ACK
mACKcountall = mACKcountall+(mREcount*nlqm);
mACKcount(i) = mACKcount(i)+(mREcount*nlqm);
phiUCItemp = phiUCI{sym}((0:mREcount-1)*d+1);
phiUCI{sym} = setdifference(phiUCI{sym},phiUCItemp);
phiBarULSCH{sym} = setdifference(phiBarULSCH{sym},phiUCItemp);
mUCI(sym) = length(phiUCI{sym});
mBarULSCH(sym) = length(phiBarULSCH{sym});
end
sym = sym+1;
end % while
end % for Nhop
end % if oACK > 2
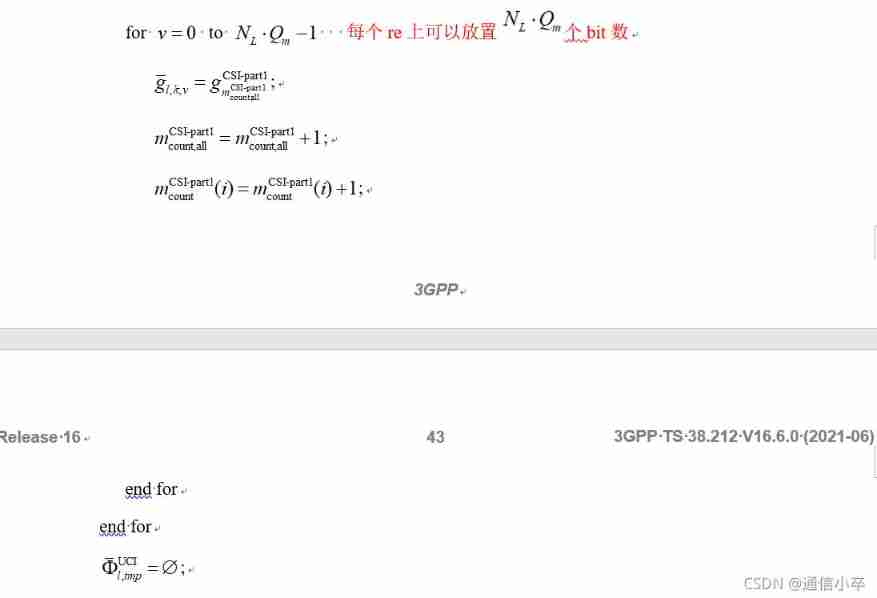
step3:CSI stay PUSCH transmission , Placement .
Let's first introduce csi port1 Placement
stay csi port1 Although it is considered to be harq-ack Reserved space , When placing, remove it and leave it for harq-ack Space .
stay csi port2 When placing, I didn't consider giving it before harq-ack Reserved space ,csi port2 It's likely to be reserved for harq-ack The space occupied .
Of course, all the above are self transmission harq-ack Of bit The number is less than or equal to 2 When , Normal greater than 2 When , stay csi port1 and 2 The occupied space has been eliminated before placement , They cannot occupy .






% Step 3
% CSI part 1
if GCSI1
lprime = [lcsi1 lcsi2];
mCSIcount = [0 0];
mCSIcountall = 0;
GCSI1Temp = [GCSI11 GCSI12];
for i = 1:numel(lprime)
sym = lprime(i);
while mUCI(sym)-mPhiSCRVD(sym) <= 0
sym = sym+1;
if sym > nPUSCHsymall
break; % exit loop at end of symbols
end
end
while mCSIcount(i) < GCSI1Temp(i)
if sym > nPUSCHsymall
% Check for the symbol number greater than the number
% of PUSCH allocated symbols in each hop and avoid out
% of bounds indexing
break;
end
% Number of resource elements available for CSI part 1 in
% each symbol
mUCIDiffmPhiRvd = mUCI(sym)-mPhiSCRVD(sym);
% Total number of remaining CSI part 1 bits to be
% accommodated per hop
numCSI1 = GCSI1Temp(i)-mCSIcount(i);
if mUCIDiffmPhiRvd > 0
if numCSI1 >= mUCIDiffmPhiRvd*nlqm
d = 1;
mREcount = mUCIDiffmPhiRvd;
else
d = floor((mUCIDiffmPhiRvd*nlqm)/numCSI1);
mREcount = ceil(numCSI1/nlqm);
end
phitemp = setdifference(phiUCI{sym},phiBarRvd{sym});
% Place coded CSI part 1 bits in gBar at relevant
% positions
k = phitemp((0:mREcount-1)*d+1);
gBar(sym,k+1,1:nlqm) = -2; % -2 for CSI part 1
mCSIcountall = mCSIcountall+(mREcount*nlqm);
mCSIcount(i) = mCSIcount(i)+(mREcount*nlqm);
phiUCItemp = phitemp((0:mREcount-1)*d+1);
phiUCI{sym} = setdifference(phiUCI{sym},phiUCItemp);
phiBarULSCH{sym} = setdifference(phiBarULSCH{sym},phiUCItemp);
mUCI(sym) = length(phiUCI{sym});
mBarULSCH(sym) = length(phiBarULSCH{sym});
end % end if
sym = sym+1;
end % while
end % for Nhop
end % if Gcsi1
% CSI part 2
if GCSI2
lprime = [lcsi1 lcsi2];
mCSIcount = [0 0];
mCSIcountall = 0;
GCSI2Temp = [GCSI21 GCSI22];
for i = 1:numel(lprime)
sym = lprime(i);
while mUCI(sym) <= 0
sym = sym+1;
if sym > nPUSCHsymall
break; % exit loop at end of symbols
end
end
while mCSIcount(i)<GCSI2Temp(i)
if sym > nPUSCHsymall
% Check for the symbol number greater than the
% number of PUSCH allocated symbols in each hop and
% avoid out of bounds indexing
break;
end
if mUCI(sym) > 0
% Total number of CSI part 2 bits remaining to be
% accommodated per hop
numCSI2 = GCSI2Temp(i)-mCSIcount(i);
if numCSI2 >= mUCI(sym)*nlqm
d = 1;
mREcount = mUCI(sym);
else
d = floor((mUCI(sym)*nlqm)/numCSI2);
mREcount = ceil(numCSI2/nlqm);
end
% Place coded CSI part 2 bits in gBar at relevant
% positions
k = phiUCI{sym}((0:mREcount-1)*d+1);
gBar(sym,k+1,1:nlqm) = -3; % -3 for CSI part 2
mCSIcountall = mCSIcountall+(mREcount*nlqm);
mCSIcount(i) = mCSIcount(i)+(mREcount*nlqm);
phiUCItemp = phiUCI{sym}((0:mREcount-1)*d+1);
phiUCI{sym} = setdifference(phiUCI{sym},phiUCItemp);
phiBarULSCH{sym} = setdifference(phiBarULSCH{sym},phiUCItemp);
mUCI(sym) = length(phiUCI{sym});
mBarULSCH(sym) = length(phiBarULSCH{sym});
end % if
sym = sym+1;
end % while
end % for Nhop
end % if GCSI2
step4 :data stay PUSCH transmission , Placement .
There is no interval for data placement. This placement rule , Equal pilot ,harq-ack csi-port1 csi-port2 Just put it next to each other after placing it , This special case is harq-ack Of bit The number is less than or equal to 2 When ,data It can also occupy the space needed before .
% Step 4
% UL-SCH
mULSCHcount = 0;
if GULSCH
for sym = 0:nPUSCHsymall-1
if mBarULSCH(sym+1) > 0
% Place coded UL-SCH bits in gBar at relevant positions
k = phiBarULSCH{sym+1}(1:mBarULSCH(sym+1));
gBar(sym+1,k+1,1:nlqm) = -4; % -4 for UL-SCH
mULSCHcount = mULSCHcount+(mBarULSCH(sym+1)*nlqm);
end % if
end % for sym
end % if Gulsch
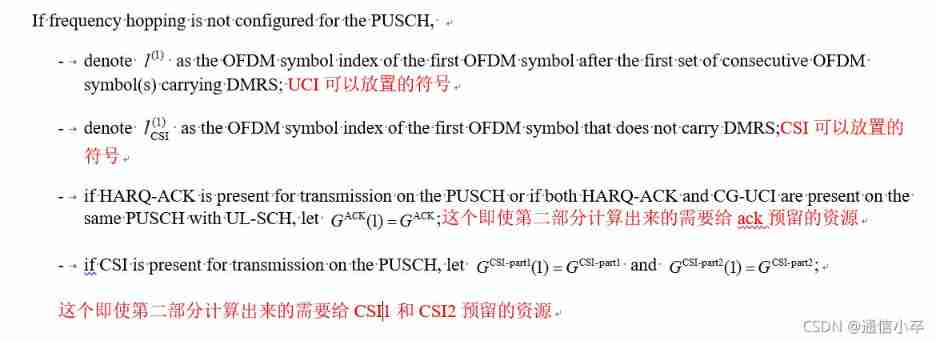
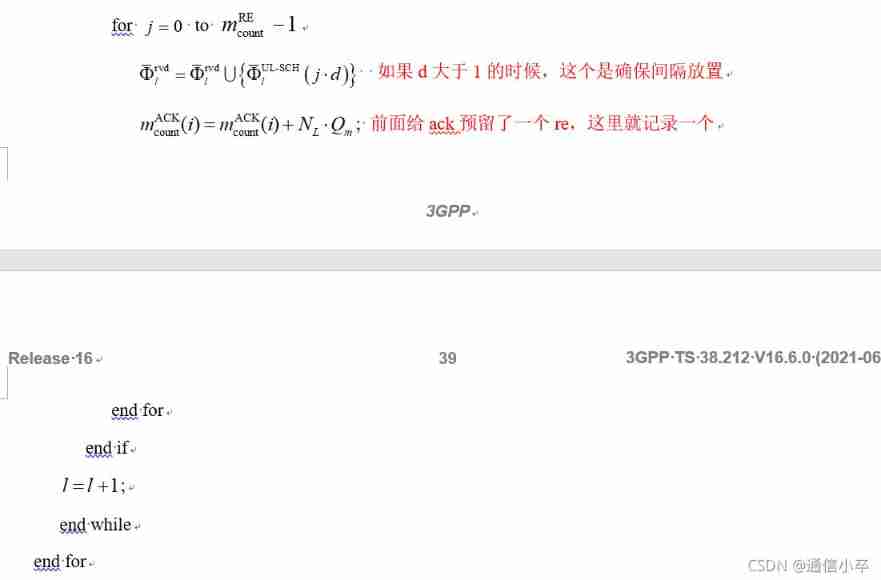
step5 : If harq-ack stay PUSCH On the transmission of bit The number is less than or equal to 2 Words , This one needs to be repositioned
Why does this need to be repositioned less than 2bit Of harq-ack, Because at the beginning, it was reserved according to 2bit Of harq-ack Space reserved , There is no real place for data , In addition, put it in the back csi port2 as well as data It is possible to ack The reserved position is placed csi part2 Or data , in other words , May be covered , In this area, it is placed in the reserved position , At the beginning, it is reserved according to 2bit Maximum reserved , This time, it is placed according to the truth harq-ack Needed bit( Less than or equal to 2bit) Count to place .
This placement is selected from the previously reserved space , What really needs to be transmitted bit The number is smaller than the reserved space , It will be placed at intervals in the reserved space . such as , Reserved 4 Space , This time just 2 Space , The first and third of the four choices will be placed .


% Step 5
% ACK (oACK <= 2)
if GACKRvd && GACK
lprime = [l1 l2];
mACKcount = [0 0];
mACKcountall = 0;
GACKTemp = [GACK1 GACK2];
for i = 1:numel(lprime)
sym = lprime(i);
while mACKcount(i) < GACKTemp(i)
if sym > nPUSCHsymall
% Check for the symbol number greater than the
% number of PUSCH allocated symbols in each hop and
% avoid out of bounds indexing
break;
end
if mPhiSCRVD(sym)>0
% Total number of remaining HARQ-ACK bits to be
% accommodated per hop
numACK = GACKTemp(i)-mACKcount(i);
if numACK >= mPhiSCRVD(sym)*nlqm
d = 1;
mREcount = mPhiSCRVD(sym);
else
d = floor((mPhiSCRVD(sym)*nlqm)/numACK);
mREcount = ceil(numACK/nlqm);
end
% Place coded HARQ-ACK bits in gBar at relevant
% positions
k = phiBarRvd{sym}((0:mREcount-1)*d+1);
gBar(sym,k+1,1:nlqm) = gBar(sym,k+1,1:nlqm)+5; % Add 5 to get the locations of ACK, overlapped with UL-SCH or CSI2
mACKcountall = mACKcountall+(mREcount*nlqm);
mACKcount(i) = mACKcount(i)+(mREcount*nlqm);
end % if
sym = sym+1;
end % while
end % for Nhop
end % if oack <= 2
step6: There is no substantive operation , Just output the result of the previous processing to another array

% Step 6
% Return the multiplexed output
cackInd = zeros(0,1);
ccsi1Ind = zeros(0,1);
ccsi2Ind = zeros(0,1);
culschInd = zeros(0,1);
culschAckInd = zeros(0,1);
ccsi2AckInd = zeros(0,1);
if GULSCH || GACK || GCSI1 || GCSI2
t = 0;
cwLen = sum(mULSCH(:))*nlqm;
cw = zeros(cwLen,1); % Initialize temporary codeword
for sym = 0:nPUSCHsymall-1
for j = 0:mULSCH(sym+1)-1
k = phiULSCH{
sym+1}(j+1);
cw(t+1:t+nlqm) = gBar(sym+1,k+1,:);
t = t+nlqm;
end
end
cackInd = sort([find(cw == -1); find(cw > 0)]);
ccsi1Ind = find(cw == -2);
ccsi2Ind = find(cw == -3);
culschInd = find(cw == -4);
culschAckInd = find(cw == 1);
ccsi2AckInd = find(cw == 2);
else
% Inputs ulsch, ack, csi1, csi2 are empty, return empty
cw = zeros(0,1);
end
边栏推荐
- Win10 install elk
- Construction and test of TFTP server under unbuntu (Debian)
- Quickly use markdown to edit articles
- Leetcode daily question (1856. maximum subarray min product)
- Leetcode daily question (745. prefix and suffix search)
- Nodemcu-esp8266 development (vscode+platformio+arduino framework): Part 2 --blinker_ Hello_ WiFi (lighting technology - Mobile App control routine)
- Long类型的相等判断
- 文件系统中的目录与切换操作
- Jetson nano custom boot icon kernel logo CBOOT logo
- Error output redirection
猜你喜欢
Learning C language from scratch -- installation and configuration of 01 MinGW
Vscode Arduino installation Library
![[CSDN]C1训练题解析_第三部分_JS基础](/img/b2/68d53ad09688f7fc922ac65e104f15.png)
[CSDN]C1训练题解析_第三部分_JS基础
PolyWorks script development learning notes (4) - data import and alignment using file import

Flink-CDC实践(含实操步骤与截图)
![[kotlin learning] control flow of higher-order functions -- lambda return statements and anonymous functions](/img/a3/b442508af9b059d279cffb34dee9bf.png)
[kotlin learning] control flow of higher-order functions -- lambda return statements and anonymous functions

小王叔叔的博客目录【持续更新中】
![[combinatorics] Introduction to Combinatorics (combinatorial thought 2: mathematical induction | mathematical induction promotion | multiple induction thought)](/img/0e/dff6d3c6b7bf388bf71b0965533c25.jpg)
[combinatorics] Introduction to Combinatorics (combinatorial thought 2: mathematical induction | mathematical induction promotion | multiple induction thought)
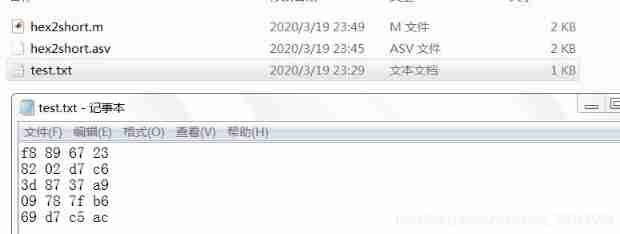
Matlab reads hexadecimal numbers and converts them into signed short

Overview of image restoration methods -- paper notes
随机推荐
ERROR: certificate common name “www.mysql.com” doesn’t match requested host name “137.254.60.11”.
The idea of compiling VBA Encyclopedia
Common software open source protocols
Install database -linux-5.7
Leetcode daily question (2305. fair distribution of cookies)
LeetCode每日一题(1024. Video Stitching)
LeetCode每日一题(516. Longest Palindromic Subsequence)
Modify idea code
顺利毕业[3]-博客系统 更新中。。。
[CSDN]C1训练题解析_第三部分_JS基础
Idea uses the MVN command to package and report an error, which is not available
[CSDN]C1训练题解析_第四部分_Web进阶
Flink learning notes (VIII) multi stream conversion
Starting from 0, use pnpm to build a demo managed by monorepo
数字身份验证服务商ADVANCE.AI顺利加入深跨协 推进跨境电商行业可持续性发展
[solution to the new version of Flink without bat startup file]
Database execution error: SQL_ mode only_ full_ group_ by:
Leetcode daily question (2212. maximum points in an archery competition)
Hudi data management and storage overview
Nodemcu-esp8266 development (vscode+platformio+arduino framework): Part 3 --blinker_ MIOT_ Light (lighting technology app control + Xiaoai classmate control)