当前位置:网站首页>AWD learning
AWD learning
2022-07-02 06:39:00 【zb0567】
The basic flow
1、 Pull down the title file
2、 Quickly analyze the problem loopholes
3、 Patch the vulnerability and send it back
4、 Problem solving 、 attack
5、 Grab flow 、 defense
One 、 Target information collection
PWN Drone aircraft 、 adopt XSHELL Connect , download LIBC Document and ELF file , Please back up after downloading
commonly nc ip + port
libc Generally in lib/x86_64-linux-gnu Of libc-2.23.so file This is the runtime , So download
Create a copy of the game file , take pwn and so Copy in the file
Need to find yourself pwn The port of the topic , Every team pwn The mounting ports are the same
nmap Scan the tool pwn Drone aircraft , You can get the port of the topic for example nmap 127.0.0.1 nc Connect to
netstat -nultp Self scanning Only know your target ip And ports are useless Generally speaking, target plane ip It's all continuous , There are traces to follow
ifconfig Check the network of this computer nmap -sP 192.168.58.0/24
commonly pwn Topic ratio ctf Simple , And there are many loopholes Be the first to write EXP Carry out the first round of attack
After discovering the vulnerability, no matter whether it will be exploited , Patch up , rename PWN file , In case of being used by others
Two 、 commonly PWN Topic common vulnerabilities and patch analysis
Common vulnerabilities
Stack overflow vulnerability
read(0,&buf ,0X40uLL);
read(0,&s,0x90uLL)
read(&format,24LL) This is not a loophole
Repair form :
This kind of vulnerability is generally due to accept character overflow , Lead to the vulnerability of modifying the return address
read Generally, you can only read 20 Characters , however , If followed by 0x20, That's equivalent to reading more 16 Characters , Lead to loopholes
repair :
Limited data entry Yes read and copy It works
Change the data input address to BSS Segment and other readable segments The corresponding is get function
Format string vulnerability
print(&buf,&buf)
print(&format)
Heap overflow hole
Write across the border
malloc Distribute
Quickly analyze the process , Find digital stream
Start with the input stream , Follow the input stream to find vulnerabilities Stain analysis
Example :
(1) stay linux Run the program , Prompt for input ./change_rdx
stay main We found in the function read(0,&buf,0x60uLL) Stack overflow vulnerability Corresponding to the above rbp-30h 30 Bit
Check this line , The right choice copy toassembly choice yes
stay linux below gdb change_rdx debugging
b *0x00000000004006EE
r
Pictured


c10 - be0 Certainly more than 0x60


take 60h It is amended as follows 0x30, First step patch, Second parts cancel, Then it becomes as shown in the figure
return main see read(0,&buf,0x30uLL)
stay edit Of keypatch Of patcher On the file patch
Or in patch program Of assemble You can also modify
After patching, use patch program Of apply pachthes to input files Files after patching in the light of ida7.0
Name it _patched
b *0x0000000000400704
r

Can only read 0x30 The data of as long as
(2)gets(&s,argv);
choose segement to jump You can choose .bss Mode view
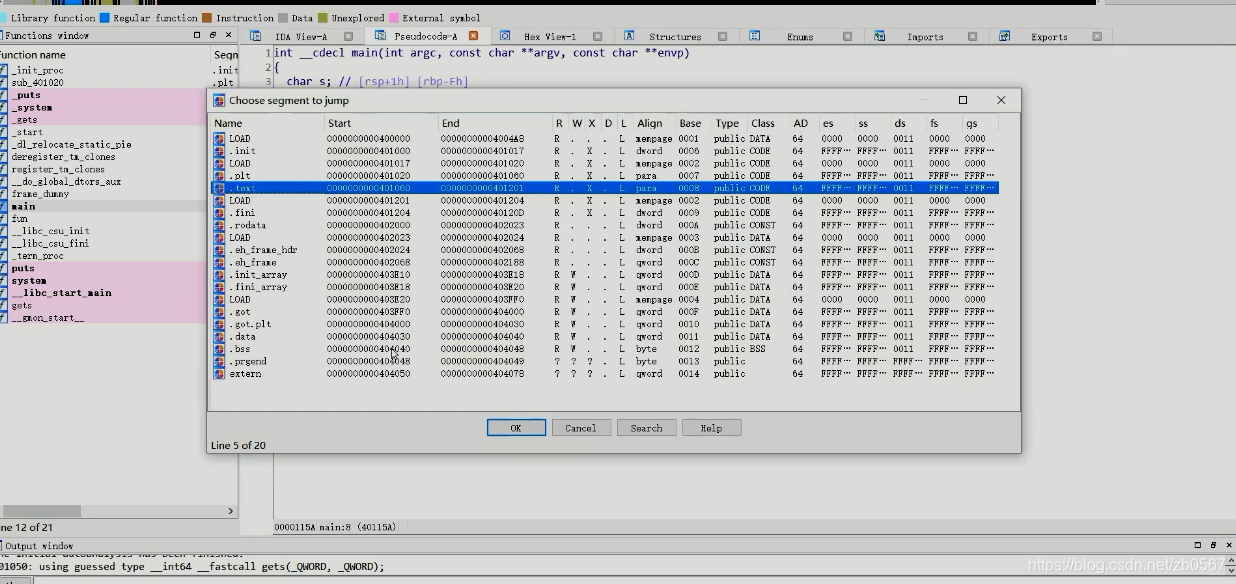
copy assembly

modify 1156 Of assembly Change to mov rdi,0x0000000000404040

Then return main function

0x404040 Your address corresponds to .bss Start segment address of
alike puts(&s) Also changed to mov rdi,404040h The address of At this time, apply it
After patching, use patch program Of apply pachthes to input files
Upload the file , then gdb change_buf_to_bss
Add breakpoint at call _gets, 401162
b *0x0000000000401162
r
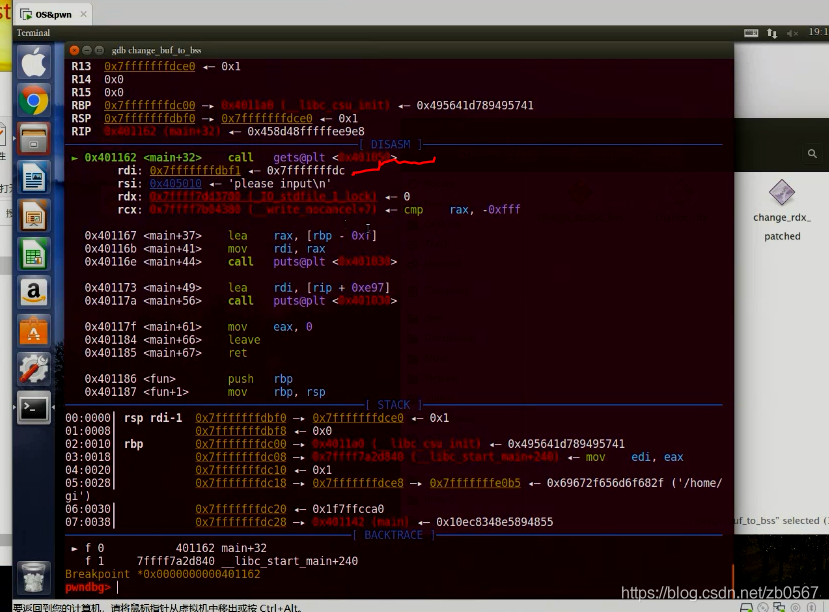
Input ni
aaaaaaaaaaaaaaaaaaa

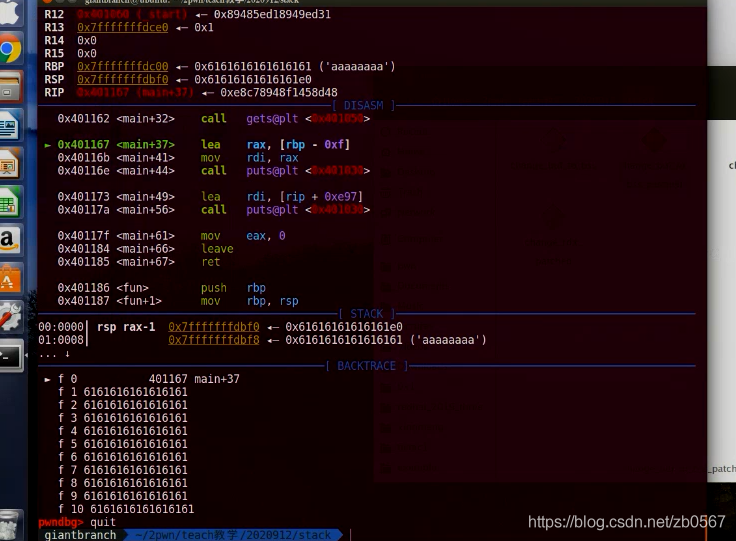
Put the patched one in
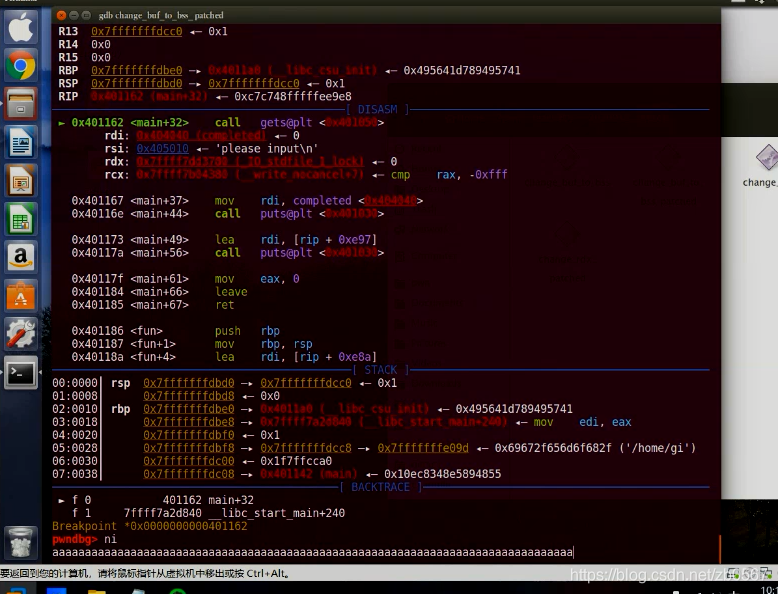

By comparison , There is no difference between the two functions
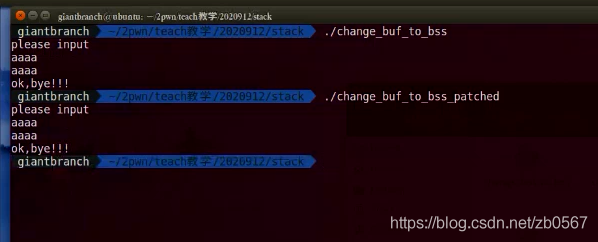
Input parameters The stack is changed to bss Pile it up
(3) The format string is generally in the form of print(&FMT)
Common modification methods Add a format string before the data
modify printf Function is puts function ./fmt_change_pringf_to_puts
aaa command not found
sed -i s/alarm/isnan/g ./fmt_change_printf_to_puts Modify the clock
%p Basic vulnerabilities can be tested

View source code

format It's a loophole
find puts Of plt surface , instead of plt.got Neither got surface
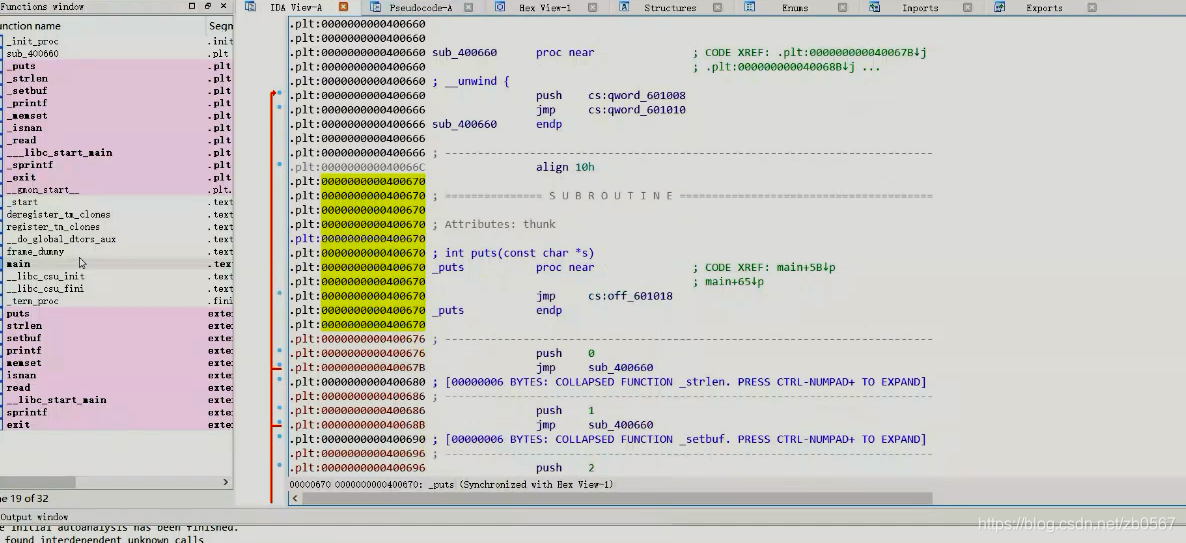
hold call printf Change to call 0x000000000400670 text It's his output function


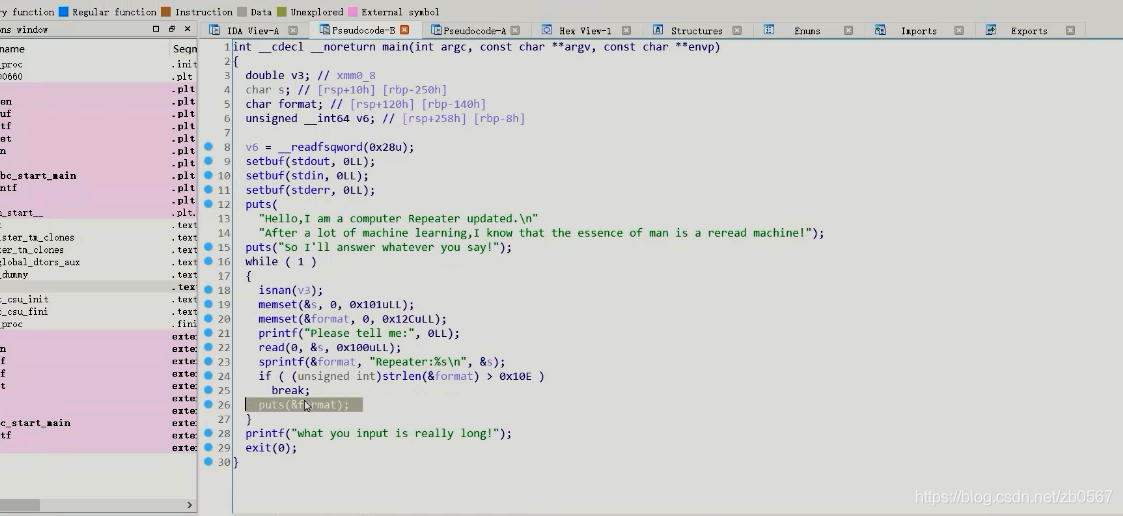
After patching, use patch program Of apply pachthes to input files
What's the difference between tests

(4) Heap overflow
There are mainly heap overflows UAF
Direct fixation malloc Of size Limit attack data flow
Don't worry about loopholes , find malloc Fix size

Find the added function
Heap overflow utilization environment , Application and release of heap
Evade check, And limit the current
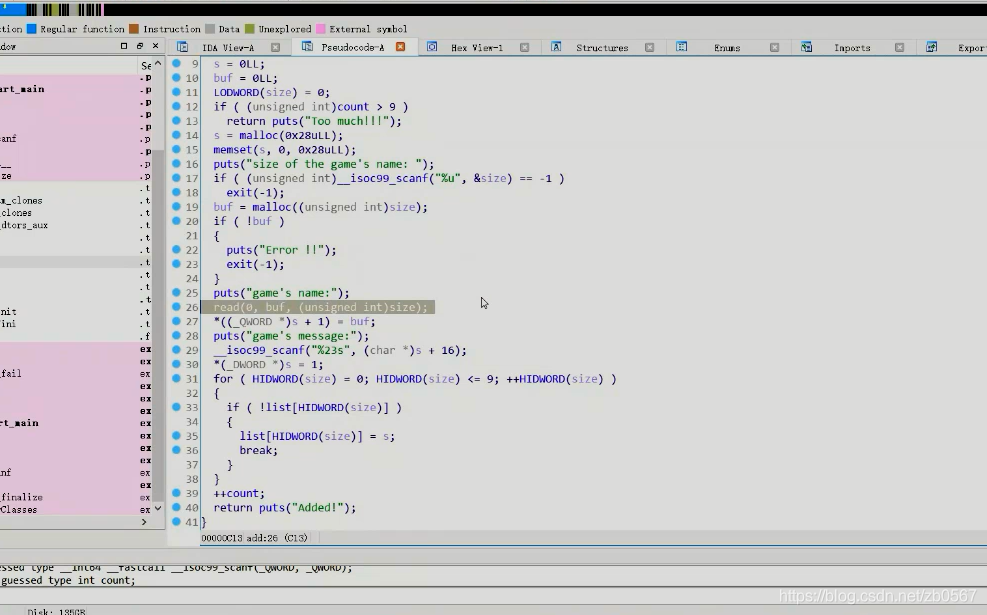
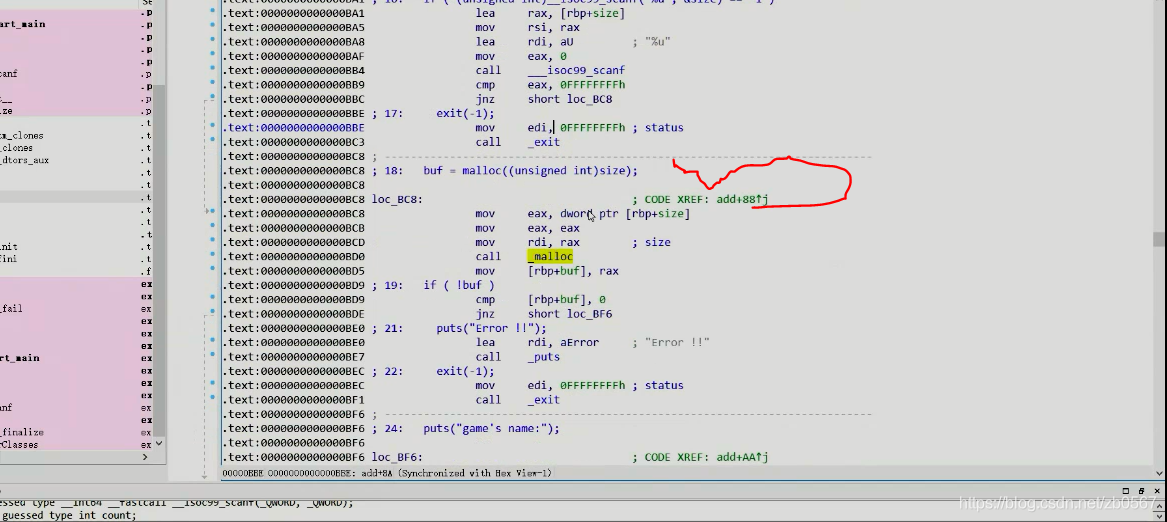
mov eax,dwprd ptr [rbp+size]
It is amended as follows mov eax,0x80
meanwhile read Inside size It is also revised to

mov eax,dwprd ptr [rbp+size]
It is amended as follows mov eax,0x80 Finally arrive mov edx,0x80

Before and after the patch

Backstepping Traffic grab
commonly root jurisdiction
pwn Prevent and catch traffic
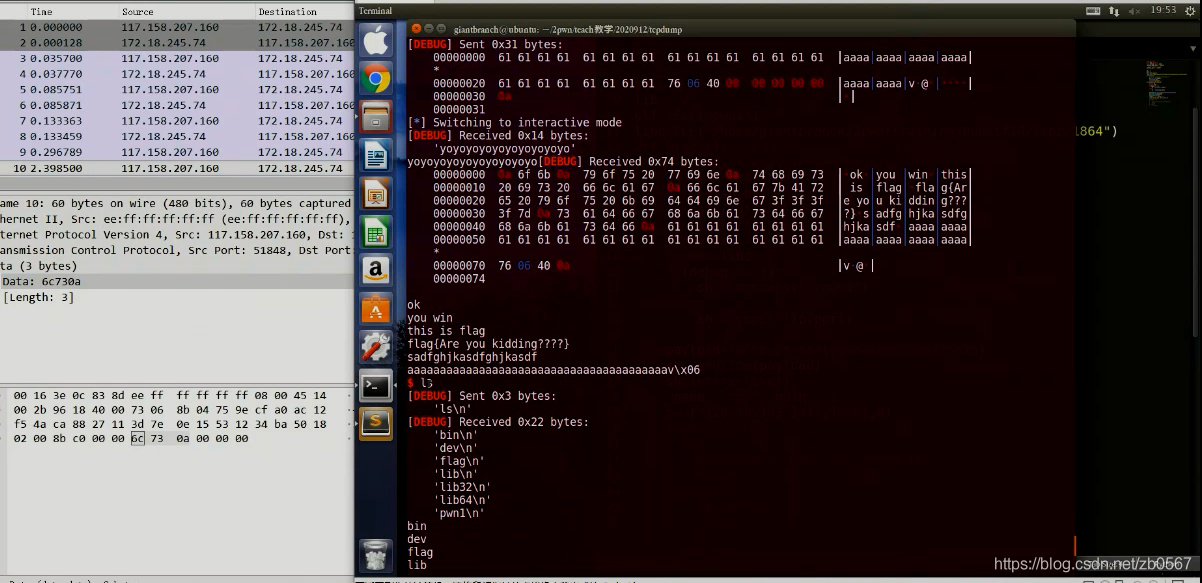
tcpdump -s 0 -w flow.pcap port Port number
Will generate... In the directory flow.pacp file

payload="a"*40+"\x76\x06\x40\x00\x00\x00\x00\x00"
边栏推荐
- Golang -- map capacity expansion mechanism (including source code)
- Introduce two automatic code generators to help improve work efficiency
- 实现strStr() II
- Does the assignment of Boolean types such as tag attribute disabled selected checked not take effect?
- web自动化切换窗口时报错“list“ object is not callable
- Apt command reports certificate error certificate verification failed: the certificate is not trusted
- 程序员的自我修养—找工作反思篇
- 由於不正常斷電導致的unexpected inconsistency;RUN fsck MANUALLY問題已解决
- Error "list" object is not callable in Web automatic switching window
- Redis - cluster data distribution algorithm & hash slot
猜你喜欢

Win10桌面图标没有办法拖动(可以选中可以打开可以删除新建等操作但是不能拖动)

VSCODE 安装LATEX环境,参数配置,常见问题解决

【文献阅读与想法笔记13】 Unprocessing Images for Learned Raw Denoising
ctf三计
Thread hierarchy in CUDA

实习生跑路留了一个大坑,搞出2个线上问题,我被坑惨了
由于不正常断电导致的unexpected inconsistency;RUN fsck MANUALLY问题已解决

Redis - hot key issues
QQ email cannot receive the email sent by Jenkins using email extension after construction (timestamp or auth...)

ctf-web之练习赛
随机推荐
Cglib agent - Code enhancement test
Code skills - Controller Parameter annotation @requestparam
Latex参考文献引用失败 报错 LaTeX Warning: Citation “*****” on page y undefined on input line *
Latex 编译报错 I found no \bibstyle & \bibdata & \citation command
Uploading attachments using Win32 in Web Automation
Fe - weex uses a simple encapsulated data loading plug-in as the global loading method
Function execution space specifier in CUDA
Latex在VSCODE中编译中文,使用中文路径问题解决
记录一次RDS故障排除--RDS容量徒增
Redis——缓存击穿、穿透、雪崩
程序员的自我修养—找工作反思篇
AWD学习
压力测试修改解决方案
实现strStr() II
Tensorrt command line program
selenium的web自动化中常用的js-修改元素属性翻页
Virtualenv and pipenv installation
No process runs when querying GPU, but the video memory is occupied
Latex 报错 LaTeX Error: The font size command \normalsize is not defined问题解决
Idea announced a new default UI, which is too refreshing (including the application link)