当前位置:网站首页>Explanation of traceroute command
Explanation of traceroute command
2022-07-02 17:21:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
adopt traceroute We can know the path of information from your computer to the host on the other end of the Internet . Of course, every packet has the same starting point (source) Arrive at the same destination (destination) The path may be different , But basically the route is the same most of the time .linux In the system , We call it traceroute, stay MS Windows In Chinese, it means tracert. traceroute By sending small packets to the destination device until it returns , To measure how long it takes . Every device on one path traceroute To be tested 3 Time . The output includes the time of each test (ms) And the name of the device ( If so ) And its IP Address .
in the majority of cases , We will be in linux Under the host system , Execute the command line directly :
traceroute hostname
If there is no t raceroute command , It can be done by
yum -y install traceroute Command installation (root Permission online installation )
1. Command format :
traceroute[ Parameters ][ host ]
2. Command function :
traceroute Instructions let you track the routing of network packets , The default packet size is 40Bytes, Users can set it separately .
Specific parameter format :traceroute [-dFlnrvx][-f< Survival value >][-g< gateway >…][-i< Network interface >][-m< Survival value >][-p< Communication port >][-s< Source address >][-t< Service type >][-w< Timeout seconds >][ Host name or IP Address ][ Packet size ]
3. Command parameter :
-d Use Socket The level of troubleshooting function .
-f Set the survival value of the first detection packet TTL Size .
-F Set do not disconnect .
-g Set source routing gateway , Up to 8 individual .
-i Use the specified network interface to send out packets .
-I Use ICMP Respond instead of UDP Information .
-m Set the maximum survival value of the detection packet TTL Size .
-n Use it directly IP Address, not host name .
-p Set up UDP The communication port of the transmission protocol .
-r Ignore the ordinary Routing Table, Send the packet directly to the remote host .
-s Set the packet sent by the local host IP Address .
-t Set the TOS The number .
-v Display the execution process of the instruction in detail .
-w Set the time to wait for the remote host to report .
-x Turn packet correctness check on or off .
4. Using examples :
example 1:traceroute Simple to use 、 The most common usage
command :
traceroute www.baidu.com
Output :
explain :
Record by serial number from 1 Start , Every record is a jump , Each hop represents a gateway , We see three times per line , The unit is ms, In fact, that is -q Default parameters . After the probe packet sends three packets to each gateway , The return time of the gateway response ; If you use traceroute -q 4 www.58.com , Means to send... To each gateway 4 A packet .
Sometimes we traceroute When it's a mainframe , You'll see that some lines are indicated by asterisks . This is the case , Maybe the firewall is blocked ICMP The return information of , So we don't get any packet return data .
Sometimes we have a long delay at a gateway , Maybe a gateway is blocked , It could also be the physical device itself . Of course, if one DNS When something goes wrong , Cannot resolve the host name 、 Domain name , It will be There is a phenomenon of long delay ; You can add -n Parameters to avoid DNS analysis , With IP Format output data .
If between different segments in the LAN , We can go through traceroute To find out what the problem is , Is it a host problem or a gateway problem . If we have a problem accessing a server remotely , We use traceroute Tracking the gateway that the packet passes through , Submit IDC Service provider , It also helps to solve problems ; But at present, it seems difficult to solve such problems at home , That's where we found the problem ,IDC It's impossible for service providers to help us solve .
example 2: Hops setting
command :
traceroute -m 10 www.baidu.com
Output :
example 3: Show IP Address , Don't look up the hostname
command :
traceroute -n www.baidu.com
Output :
example 4: The basic use of the detection package UDP Port settings 6888
command :
traceroute -p 6888 www.baidu.com
Output :
example 5: Set the number of probe packets to a value 4
command :
traceroute -q 4 www.baidu.com
Output :
example 6: Bypass the normal routing table , Send directly to the host connected to the network
command :
traceroute -r www.baidu.com
Output :
It is reported that the network is unreachable .
example 7: Set the waiting response time of outgoing detection packet to 3 second
command :
traceroute -w 3 www.baidu.com
Output :
Traceroute How it works :
Traceroute The simplest basic usage is :traceroute hostname
Traceroute The design of the program is to use ICMP And IP header Of TTL(Time To Live) Field (field). First ,traceroute Send one TTL yes 1 Of IP datagram( Actually , Every time I send you 3 individual 40 Bytes of package , Include source address , Destination address and time tag of the package ) Destination , When the first router on the path (router) Receiving this datagram when , It will TTL reduce 1. here ,TTL Turn into 0 了 , So the router will put this datagram lose , And send back one 「ICMP time exceeded」 news ( Including hair IP The source address of the package ,IP All contents of the package and router IP Address ),traceroute After receiving this message , We know that this router exists on this path , next traceroute Send out another TTL yes 2 Of datagram, Find the first 2 Router …… traceroute Every time will send out datagram Of TTL Add 1 To find another router , This repetitive action continues until a certain datagram Arrive at the destination . When datagram After arriving at the destination , The host will not send back ICMP time exceeded news , Because it's the destination , that traceroute How to know the destination has arrived ?
Traceroute Sending out UDP datagrams When we get to our destination , What it chooses to deliver port number It's a number that the average app doesn't use (30000 above ), So when this UDP datagram After arriving at the destination, the host will send back a 「ICMP port unreachable」 The news of , And when traceroute When I received the news , We know that the destination has arrived . therefore traceroute stay Server There is no such thing as Daemon The program .
Traceroute Extract hair ICMP TTL Of the expiration message device IP Address and domain name resolution . Every time ,Traceroute All print out a series of data , Including the domain name of the routing device and IP Address , The time it takes for three bags to go back and forth .
windows And tracert:
Format :
tracert [-d] [-h maximum_hops] [-j host-list] [-w timeout] target_name
Parameter description :
tracert [-d] [-h maximum_hops] [-j computer-list] [-w timeout] target_name
The diagnostic utility has different lifetime by sending messages to the destination (TL) Of Internet Control information protocol (CMP) Response message , To determine the route to the destination . Every router on the path must forward the ICMP Before responding to a message, insert it TTL It's worth at least 1, therefore TTL Is a valid jump count . When the TTL Value reduced to 0 when , The router sends back ICMP Timeout information . By sending TTL by 1 And in the subsequent transmission, each time TTL It's worth adding 1, Until the target responds or reaches the maximum TTL value ,Tracert You can determine the route . By checking the messages sent back by the intermediate router ICMP Overtime (ime Exceeded) Information , You can determine the router . Be careful , Some routers “ quiet ” To discard the time to live (TLS) Expired message and to tracert Invalid .
Parameters :
-d Specifies that the address is not resolved for the computer name .
-h maximum_hops Specifies the maximum number of hops to find the target .
-jcomputer-list Specified in the computer-list Loose source routing in .
-w timeout Waiting for timeout The number of milliseconds specified for each reply .
target_name The name of the target computer .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/148091.html Link to the original text :https://javaforall.cn
边栏推荐
- QWebEngineView崩溃及替代方案
- 剑指 Offer 27. 二叉树的镜像
- Sword finger offer 25 Merge two sorted linked lists
- Configure ARP table entry restrictions and port security based on the interface (restrict users' private access to fool switches or illegal host access)
- IP address translation address segment
- IPtables中SNAT、DNAT和MASQUERADE的含义
- Fuyuan medicine is listed on the Shanghai Stock Exchange: the market value is 10.5 billion, and Hu Baifan is worth more than 4billion
- Chapter 3 of hands on deep learning - (1) linear regression is realized from scratch_ Learning thinking and exercise answers
- Configure MySQL under Linux to authorize a user to access remotely, which is not restricted by IP
- LSF basic command
猜你喜欢
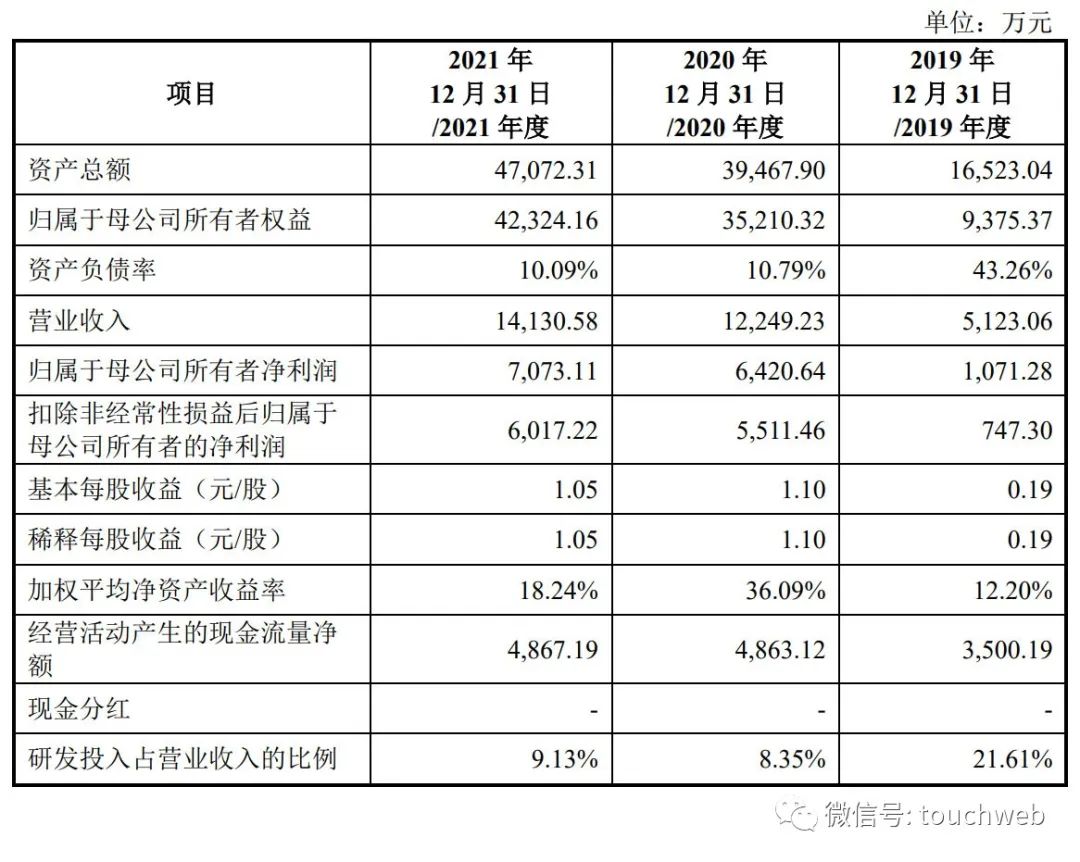
Listing of chaozhuo Aviation Technology Co., Ltd.: raising 900million yuan, with a market value of more than 6billion yuan, becoming the first science and technology innovation board enterprise in Xia

871. Minimum refueling times

Eth data set download and related problems

对接保时捷及3PL EDI案例

Sword finger offer 21 Adjust the array order so that odd numbers precede even numbers

Qstype implementation of self drawing interface project practice (II)
Configure MySQL under Linux to authorize a user to access remotely, which is not restricted by IP

Interpretation of key parameters in MOSFET device manual

伟立控股港交所上市:市值5亿港元 为湖北贡献一个IPO

Eye of depth (III) -- determinant of matrix
随机推荐
一年頂十年
2020 "Lenovo Cup" National College programming online Invitational Competition and the third Shanghai University of technology programming competition (a sign in, B sign in, C sign in, D thinking +mst
默认浏览器设置不了怎么办?
Usage of sprintf() function in C language
超卓航科上市:募资9亿市值超60亿 成襄阳首家科创板企业
Vscode setting delete line shortcut [easy to understand]
A case study of college entrance examination prediction based on multivariate time series
七张图,学会做有价值的经营分析
Error when uploading code to remote warehouse: remote origin already exists
[fluent] dart data type map type (create map set | initialize map set | traverse map set)
IDEA2021.1 安装教程
Introduction to Hisilicon hi3798mv100 set top box chip [easy to understand]
PhD battle-11 preview | review and prospect backdoor attack and defense of neural network
The beginning of life
例题 非线性整数规划
Ocio V2 reverse LUT
IPtables中SNAT、DNAT和MASQUERADE的含义
Eye of depth (II) -- matrix and its basic operations
ssb门限_SSB调制「建议收藏」
Cell: Tsinghua Chenggong group revealed an odor of skin flora. Volatiles promote flavivirus to infect the host and attract mosquitoes