当前位置:网站首页>Configure ARP table entry restrictions and port security based on the interface (restrict users' private access to fool switches or illegal host access)
Configure ARP table entry restrictions and port security based on the interface (restrict users' private access to fool switches or illegal host access)
2022-07-02 16:54:00 【All documents are printed】
Application scenarios : To prevent unauthorized users from accessing the network 、 Users access the switch privately 、 Routers and other devices , Bring security risks to the company's network management . Prohibit by relevant technical means , There are two methods as follows : Configure port security and interface based ARP Table entry restrictions
The operation principle and configuration of the two methods are introduced respectively :
One 、 Port security : Learn the dynamics of the device port MAC Address translation to security MAC Address . Enable this function under the interface , And limit the maximum number of interfaces that can be learned MAC Number of entries , When the set value is exceeded , Messages of subsequent users will be discarded , So as to ensure the terminal access security of the interface , Enhance device security .
1.1 Security MAC Addresses fall into the following three categories :
(1) Security dynamic MAC Address ( Can make port-security But it does not enable Sticky, After the device is restarted, the table item will be lost , It will not be aged by default , Unless aging time is configured )
(2) Security static MAC Address ( Can make port-security Manually configured static MAC Address , It will not be aged and the equipment restart table item will not be lost )
Configuration command :port-security enable port-security mac-address 0001-0002-0003 vlan 10
(3)Sticky MAC Address ( Can make port-security And enable Sticky, It will not be aged and the equipment restart table item will not be lost , This is recommended )
Configuration steps ( Operate in the interface view ):
port-security enable
port-security mac-address sticky
port-security max-mac-num 10
port-security protect-action restrict
(4) The protection of port security is divided into the following three types :
- restrict( discarded , And report to the police , This is recommended )
- Protect( discarded , Don't report to the police )
- Shutdown( The interface status is changed to erro-down, And report to the police )
Two 、ARP Table entry restrictions : In order to prevent a user host connected to an interface from initiating ARP During the attack, the whole device ARP Table resources are exhausted . Configure the maximum dynamics that the interface can learn under the interface ARP Number of entries , After this setting value is exceeded, new dynamics will not be allowed ARP Table item .
scene 1:ARP Table entry restrictions
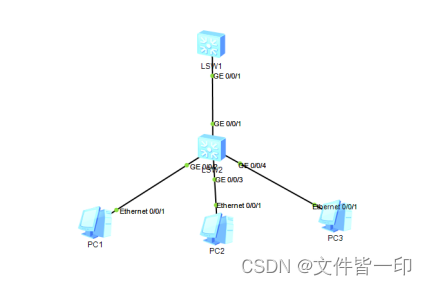
LSW1 On the configuration
#
Configure interface GE0/0/1(LSW1) You can learn at most 2 individual VLAN10 The corresponding dynamic ARP Table item .
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
arp-limit vlan 10 maximum 2
#
perhaps Configure interface VLANIF10 You can learn at most 10 A dynamic ARP Table item .
#
interface Vlanif10
ip address 192.168.100.254 255.255.255.0
dhcp select interface
arp-limit maximum 10
#
stay LSW1 On the implementation display arp all see ARP Table item record , Only learn PC1 and PC2 Of ARP Table item .
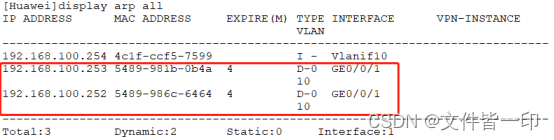
perform display arp-limit see ARP Restrict entry records

except PC3 cannot access 192.168.100.254,PC1 and PC2 All accessible . I forgot to cut the picture .

scene 2: Configure port security
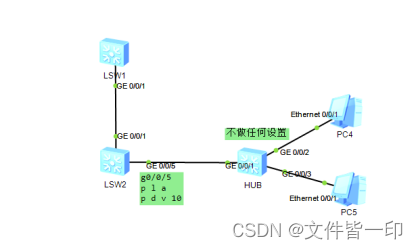
LSW2 To configure :
#
vlan batch 10
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 10
#
PC4 and PC5 Can access the network
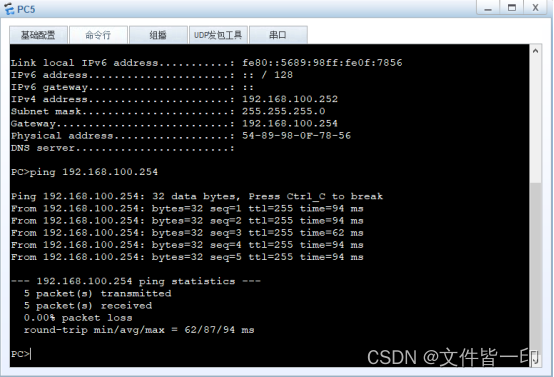
stay LSW1 Check out ARP Table item

stay GE0/0/5 After opening port security on the port , Then watch PC4 and PC5 Can I access the gateway
[Huawei-GigabitEthernet0/0/5]port-security enable
[Huawei-GigabitEthernet0/0/5]port-security protect-action protect
[Huawei-GigabitEthernet0/0/5]port-security mac-address sticky
[Huawei-GigabitEthernet0/0/5]port-security max-mac-num 1
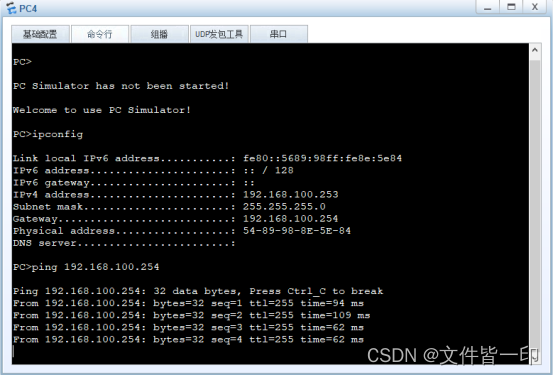
Carry out orders reboot, take LSW1 restart , eliminate ARP Table item (reset arp all Command in ENSP Can't use ).

stay PC4 and PC5 Test whether you can access the gateway 192.168.100.254, Only found PC4 You can visit ,PC5 Rejected .


perform display arp all see GE0/0/1 Learned under the interface ARP entry
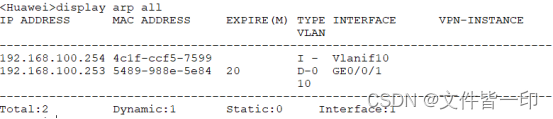
recommend : Change the port security protection function restrict, Report the alarm while discarding the message .
[Huawei-GigabitEthernet0/0/5]port-security protect-action restrict
The alarms output by the equipment are as follows
Jun 27 2022 01:32:25-08:00 Huawei DS/4/DATASYNC_CFGCHANGE:OID 1.3.6.1.4.1.2011.5
.25.191.3.1 configurations have been changed. The current change number is 13, t
he change loop count is 0, and the maximum number of records is 4095.
Jun 27 2022 01:32:32-08:00 Huawei L2IFPPI/4/PORTSEC_ACTION_ALARM:OID 1.3.6.1.4.1
.2011.5.25.42.2.1.7.6 The number of MAC address on interface (10/10) GigabitEthe
rnet0/0/5 reaches the limit, and the port status is : 1. (1:restrict;2:protect;3
:shutdown)
边栏推荐
- Summary | three coordinate systems in machine vision and their relationships
- Global and Chinese market of jacquard looms 2022-2028: Research Report on technology, participants, trends, market size and share
- Yyds dry inventory uses thread safe two-way linked list to realize simple LRU cache simulation
- Atcoder beginer contest 169 (B, C, D unique decomposition, e mathematical analysis f (DP))
- unity Hub 登錄框變得很窄 無法登錄
- Seal Library - installation and introduction
- Rock PI Development Notes (II): start with rock PI 4B plus (based on Ruixing micro rk3399) board and make system operation
- Hard core! One configuration center for 8 classes!
- Leetcode1380: lucky numbers in matrix
- lsf基础命令
猜你喜欢
Win11应用商店无法加载页面怎么办?Win11商店无法加载页面

隐私计算技术创新及产业实践研讨会:学习

unity Hub 登錄框變得很窄 無法登錄

关于举办科技期刊青年编辑沙龙——新时代青年编辑应具备的能力及提升策略的通知...

OpenPose的使用
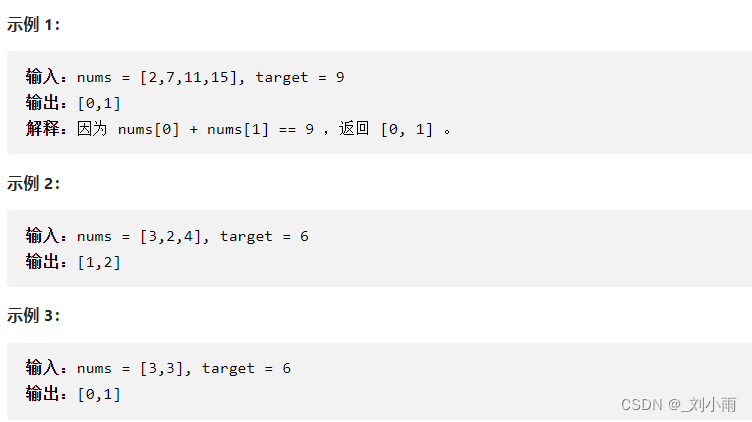
LeetCode 1. 两数之和
Penetration tool - intranet permission maintenance -cobalt strike

Summary of monthly report | list of major events of moonbeam in June
电脑设备打印机驱动安装失败如何解决

Privacy computing technology innovation and industry practice seminar: Learning
随机推荐
What is the difference between self attention mechanism and fully connected graph convolution network (GCN)?
Global and Chinese market of jacquard looms 2022-2028: Research Report on technology, participants, trends, market size and share
隐私计算技术创新及产业实践研讨会:学习
图书管理系统(山东农业大学课程设计)
How to solve the failure of printer driver installation of computer equipment
Cell:清华程功组揭示皮肤菌群的一种气味挥发物促进黄病毒感染宿主吸引蚊虫...
Notice on holding a salon for young editors of scientific and Technological Journals -- the abilities and promotion strategies that young editors should have in the new era
Penetration tool - intranet permission maintenance -cobalt strike
LeetCode 1. 两数之和
Interview summary of large factories
Yyds dry inventory uses thread safe two-way linked list to realize simple LRU cache simulation
[fluent] dart data type list set type (define set | initialize | generic usage | add elements after initialization | set generation function | set traversal)
OpenHarmony如何启动远程设备的FA
数字IC手撕代码--投票表决器
AcWing 300. Task arrangement
Aike AI frontier promotion (2.15)
LeetCode 2. 两数相加
Sim2real environment configuration tutorial
流批一体在京东的探索与实践
PhD Debate-11 预告 | 回顾与展望神经网络的后门攻击与防御