当前位置:网站首页>Virtual private network foundation
Virtual private network foundation
2022-06-24 22:31:00 【Zhuge iron and steel cloud】
One 、vpn The concept of
×××(Virtual Private Network): Virtual private network , It provides us with a way to use the public network , It is a connection mode that can safely remotely access the private network inside the enterprise . We know that a network connection usually consists of three parts : The client 、 Transmission media and servers .××× It also consists of these three parts , The difference is ××× The connection uses the tunnel as the transmission channel , This tunnel is built on the basis of public network or private network
Two 、vpn The type of
××× It's a bit confusing . Different manufacturers are selling their ××× Products are classified in different ways , They are mainly divided from the perspective of products . Different ISP In the development of ××× Different classification methods have been introduced in business , They are mainly divided from the perspective of business development . Users often have their own division methods , Mainly according to their own needs .
1> By access mode
This is what users and operators are most concerned about ××× The divisions . In general , The user may be on a dedicated line ( Int ) Netted , It may also be dial-up , This will depend on the specific circumstances of support . Based on the IP Online ××× There are two corresponding access methods : Special line access mode and dial-up access mode .
(1) A dedicated line ×××: It is for those who have been connected through a dedicated line ISP Provided by the user of the edge router ××× Solution . This is a kind of “ Always online ” Of ×××, It can save the cost of the traditional long-distance special line .
(2) dial ×××( also called VPDN): It is used to dial PSTN or ISDN Access ISP Provided by the user ××× Business . This is a kind of “ Connect on demand ” Of ×××, It can save users' long-distance telephone charges . It's important to point out that , Because users are generally roaming users , yes “ Connected on demand , therefore VPDN Identity authentication is usually required ( Such as the use of CHAP and RADIUS)
2 > By protocol implementation type
This is a ××× Manufacturer and ISP The most concerned about the division . According to the hierarchical model ,××× It can be established on the second layer , It can also be established on the third layer ( Some people even classify some security protocols at higher levels as ××× agreement .)
(1) The second layer tunnel protocol : This includes point-to-point tunneling protocols (PPTP)、 Second layer Forwarding Protocol (L2F), The second layer tunnel protocol (L2TP)、 Multiprotocol label switching (MPLS) etc. .
(2) Layer 3 Tunneling Protocol : This includes the generic routing encapsulation protocol (GRE)、IP Security (IPSec), These are the two most popular three-layer protocols .
The difference between layer 2 and layer 3 tunneling protocols mainly lies in the layers of the network protocol stack where user data is encapsulated , among GRE、IPSec and MPLS It is mainly used to realize special line ××× Business ,L2TP It is mainly used for dialing ××× Business ( But it can also be used to realize dedicated lines ××× Business ), Of course, these agreements are not in conflict with each other , It can be used in combination .
notes :MPLS Some books classify it as the second layer , Some books are classified as the third layer , But strictly speaking, it should belong to 2.5 layer . Because it lies between the traditional layer 2 and layer 3 protocols , Its upper layer protocol and lower layer protocol can be various protocols in the current network . Such as :IPX,APPLETALK etc. .
3 > Press ××× Division of initiation methods of
This is the customer and IPS Most concerned about ××× classification .××× Business can be realized independently by customers , It can also be done by ISP Provided .
(1) launch ( Also called customer based ):××× The starting and ending points of service provision are customer-oriented , Its internal technical composition 、 Implementation and management of ××× Customers can see . Need client and tunnel server ( Or gateway ) We install the tunnel software . Client's software initiated tunnel , Terminate the tunnel at the company tunnel server . here ISP There is no need to do anything to support the establishment of the tunnel . After checking the user id (ID) And password verification , It is very easy for the client and the tunnel server to build a tunnel . Both parties can also communicate in an encrypted way . Once the tunnel is built , The user will feel ISP No longer involved in communication .
(2) The server initiates ( Also known as customer transparent or web-based ): In the Central Department of the company or ISP It's about (POP、Point of presence) install ××× Software , Customers do not need to install any special software . Mainly for ISP Provide comprehensive management ××× service , The starting and ending points of service provision are ISP Of POP, Its internal composition 、 Implementation and management of ××× The customer is completely transparent .
In the tunneling protocol described above , at present MPLS Can only be used for server initiated ××× The way .
4 > Press ××× Classification of service types
Depending on the type of service ,××× The business is roughly divided into three categories : Access ×××(Access ×××)、 Intranet ×××(Intranet ×××) And extranet ×××(Extranet ×××). Usually the intranet ××× It's a special line ×××.
(1) Access ×××: This is when employees or small branches of an enterprise remotely access the internal network of the enterprise through the public network ××× The way . The remote user is usually a computer , Not the Internet , Therefore, it is composed of ××× Is a host to network topology model . It should be pointed out that access ××× Different from the previous dialing ×××, This is a confusing place , Because remote access can be accessed in the form of dedicated lines , It can also be accessed by dialing .
(2) Intranet ×××: This is a virtual network built through the public network between the headquarters and branches of the enterprise , This is a network to network connection in a peer-to-peer manner ×××.
(3) extranets ×××: This is the acquisition of the enterprise 、 Merger or strategic alliance between enterprises , The virtual network built by different enterprises through the public network . This is a network to network connection in an unequal way ×××( It is mainly different in security policy ).
5 > Divided by bearing body
Operation ××× Business enterprise ; They can build their own ××× The Internet , You can also outsource this business to ××× merchant . This is the customer and ISP Most concerned issues .
(1) build by oneself ×××: This is a customer initiated ×××. Enterprises install at the site ××× Client software , Install at the edge of the enterprise network ××× gateway software , Completely independent of the operators to build their own ××× The Internet , Operators do not need to do anything right ××× Support for . Enterprises build themselves ××× The advantage is that it can directly control ××× The Internet , Independent of the operator , also ××× The access device is also independent . But the disadvantage is ××× The technology is very complex , Formed in this way ××× Cost is very high ,QoS It's hard to guarantee .
(2) outsource ×××: Enterprises put ××× Service outsourcing to operators , The operator plans according to the requirements of the enterprise 、 Design 、 Implement and operate the customer's ××× Business . Enterprises can reduce the cost of organization, operation and maintenance ××× The cost of , And operators can also open up new IP Business value-added services market , Get higher returns , And improve customer retention and loyalty . The author will outsource the current ××× There are two kinds of : Web based ××× And based on CE( User edge devices ) Management type ×××(Managed ×××). Web based ××× Usually at the presentation point of the operator network (POP) Install carrier class ××× Switching equipment . be based on CE Management type ××× Business is a trusted third party responsible for designing what the enterprise wants ××× Solution , And manage on behalf of the enterprise , The security gateway used ( A firewall 、 Router, etc ) On the user's side .
6 > Press ××× Business hierarchy model division
That's according to a ISP Provide users with ××× The service work is divided into several layers ( Note that it is not divided according to which layer the tunnel protocol works on ).
(1) dial ××× Business (VPDN): This is one of the first division methods VPDN( In fact, it is divided according to the access mode , Because it's hard to know VPDN Which floor does it belong to ).
(2) Virtual leased line (VLL): This is a simulation of the traditional leased line service , use IP The network simulates the leased line , From the perspective of users at both ends, such a virtual leased line is equivalent to the leased line in the past .
(3) Virtual private routing network (VPRN) Business : This is the third floor IP A simulation of a routing network . You can put VPRN Understand it as the third layer ××× technology .
(4) Virtual private LAN segment (VPLS): This is IP Wan emulation LAN Technology . You can put VPLS Understand it as a second layer ××× technology .


-----------------------------------
vpn Basic knowledge summary of
https://blog.51cto.com/gejielin/88639
边栏推荐
猜你喜欢

Heartless sword Chinese English bilingual poem 003 The sea of books

Creating files, recursively creating directories

一个女孩子居然做了十年硬件。。。

“阿里健康”们的逻辑早就变了

电力系统| IEEE论文投稿流程

Uncover the secret of station B. is it true that programmers wear women's clothes and knock code more efficiently?

波卡生态发展不设限的奥义——多维解读平行链

Redis hop table

Genesis公链与美国一众加密投资者齐聚Consensus 2022
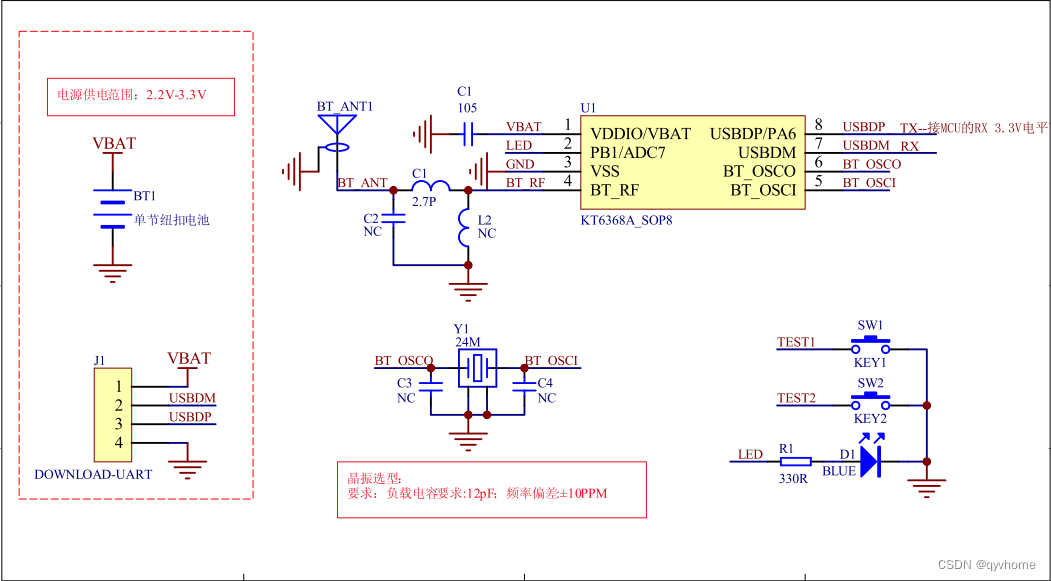
Description of software version selection of kt6368a Bluetooth dual-mode transparent chip
随机推荐
first-order-model实现照片动起来(附工具代码) | 机器学习
In the first year of L2, arbitrum nitro was upgraded to bring more compatible and efficient development experience
Chapter 10 project stakeholder management
Why can some programmers get good offers with average ability?
字符串习题总结2
“阿里健康”们的逻辑早就变了
无心剑汉英双语诗003. 《书海》
The logic of "Ali health" has long changed
Embedded development: tips and tricks -- clean jump from boot loader to application code
NiO, bio, AIO
socket(1)
socket done
零代码即可将数据可视化应用到企业管理中
Huada 4a0gpio settings
Redis hop table
leetcode:45. Jumping game II [classic greed]
Cross border e-commerce, early entry and early benefit
第二批入围企业公示!年度TOP100智能网联供应商评选
How to grab the mobile phone bag for analysis? Fiddler artifact may help you!
电力系统| IEEE论文投稿流程