当前位置:网站首页>Summary of remote connection of MySQL
Summary of remote connection of MySQL
2022-07-03 06:33:00 【Thousands of sails burn】
Preface
MySQL It is one of the most popular databases , It is also the preferred database for persistent storage of small and medium-sized enterprises .
Different from our daily study , in application ,MySQL Services will be attached to a server . If MySQL Deployed on a cloud server , thus , To manipulate the database, you need to connect to the server first , Then enter the database operation , Not very convenient .
therefore , Learning remote connections MySQL The method of is a required course when the database is on the server .
But for the sake of safety ,MySQL The remote connection of is not easy with one click , Especially in MySQL8.x version , We will introduce .
preparation
At this stage , Make sure you have entered the database service you want to access remotely , The usual interface is as follows :

Release remote host access
Generally speaking ,MySQL Only allow users to access on the local host . By inquiring user surface , You can also see the allowed host information :
select host,user from mysql.user
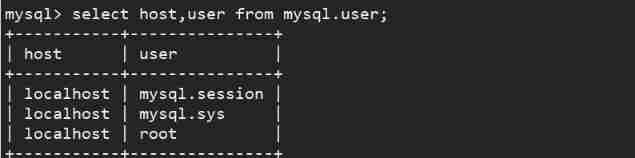
host Below the field localhost Represents that only local hosts are accepted .
therefore , Our work is very clear , Is to modify the access permission information , Enable the specified user to accept remote access . Generally speaking , We have two ways to achieve this effect .
The first one is : Change account permissions ( Suggest )
Since the remote host has no permission to connect , We can go through GRANT Statement to modify the permissions of the specified user .
GRANT The syntax of the statement is roughly :GRANT jurisdiction ON Database objects TO user .
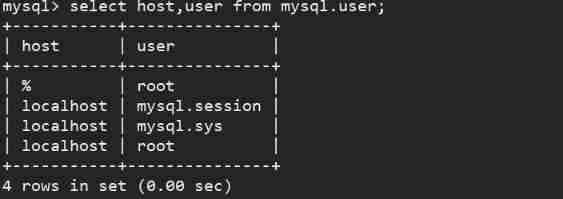
Grant all permissions for all database operations to Any mainframe (’%’) Access to the root user , So any connected to the database root Users can access all information .
GRANT ALL PRIVILEGES ON *.* TO 'root'@'%' IDENTIFIED BY ' Your password ' WITH GRANT OPTION;
Refresh the permissions :
flush privileges;
Query again , You can find that a new record will be added ,host Field % Means any host :
If you just want to grant A separate host Access right , be % It can be modified to the specified IP:
GRANT ALL PRIVILEGES ON *.* TO 'root'@'172.16.28.71' IDENTIFIED BY
' Your password ' WITH GRANT OPTION;
The effect is similar to :

Refresh the permissions :
flush privileges;
The second kind : Modified table method
Use GRANT Statement is to add a new record directly , I personally suggest doing it in the above way .
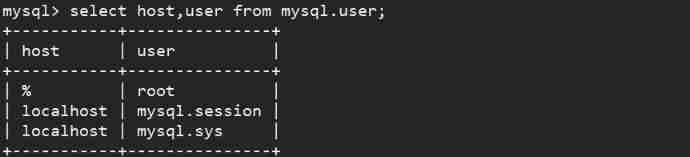
however , We can also adopt direct modification user by root Of host Field contents , Use it directly UPDATE Statement modification table :
UPDATE mysql.user SET host = '%' WHERE user = 'root';
Refresh the permissions :
flush privileges;
The effect is as shown in the picture , Directly modifying host field value , Instead of adding .
To this step , Most of the time , We can use database tools such as :Web SQLyog、Navicat、Dbeaver Wait, connect to our remote database .
MySQL 8.x Points for attention
But please pay attention to , If your MySQL The version is 8.x Words , Due to the different ways of password encryption , The following prompt may appear when connecting :
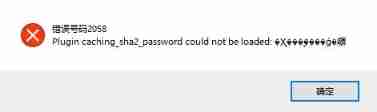
therefore , We have to Change the encryption method To achieve remote connection , Use ALTER sentence :
ALTER USER 'root'@'%' IDENTIFIED WITH mysql_native_password BY ' Your password ';
Finally, don't forget to refresh permissions :
flush privileges;
OK, This is the end of the tutorial , If you have any problems , Welcome to comment in the comment area
Reference resources
边栏推荐
- Common interview questions
- JMeter linked database
- ROS+Pytorch的联合使用示例(语义分割)
- ruoyi接口权限校验
- The dynamic analysis and calculation of expressions are really delicious for flee
- 技术管理进阶——你了解成长的全貌吗?
- Simple understanding of ThreadLocal
- The mechanical hard disk is connected to the computer through USB and cannot be displayed
- Summary of the design and implementation of the weapon system similar to the paladin of vitality
- Install VM tools
猜你喜欢
随机推荐
ODL framework project construction trial -demo
【code】if (list != null && list.size() > 0)优化,集合判空实现方式
【LeetCode】Day93-两个数组的交集 II
[untitled] 5 self use history
有意思的鼠標指針交互探究
How matlab modifies default settings
轻松上手Fluentd,结合 Rainbond 插件市场,日志收集更快捷
Code management tools
pytorch练习小项目
Migrate data from Amazon aurora to tidb
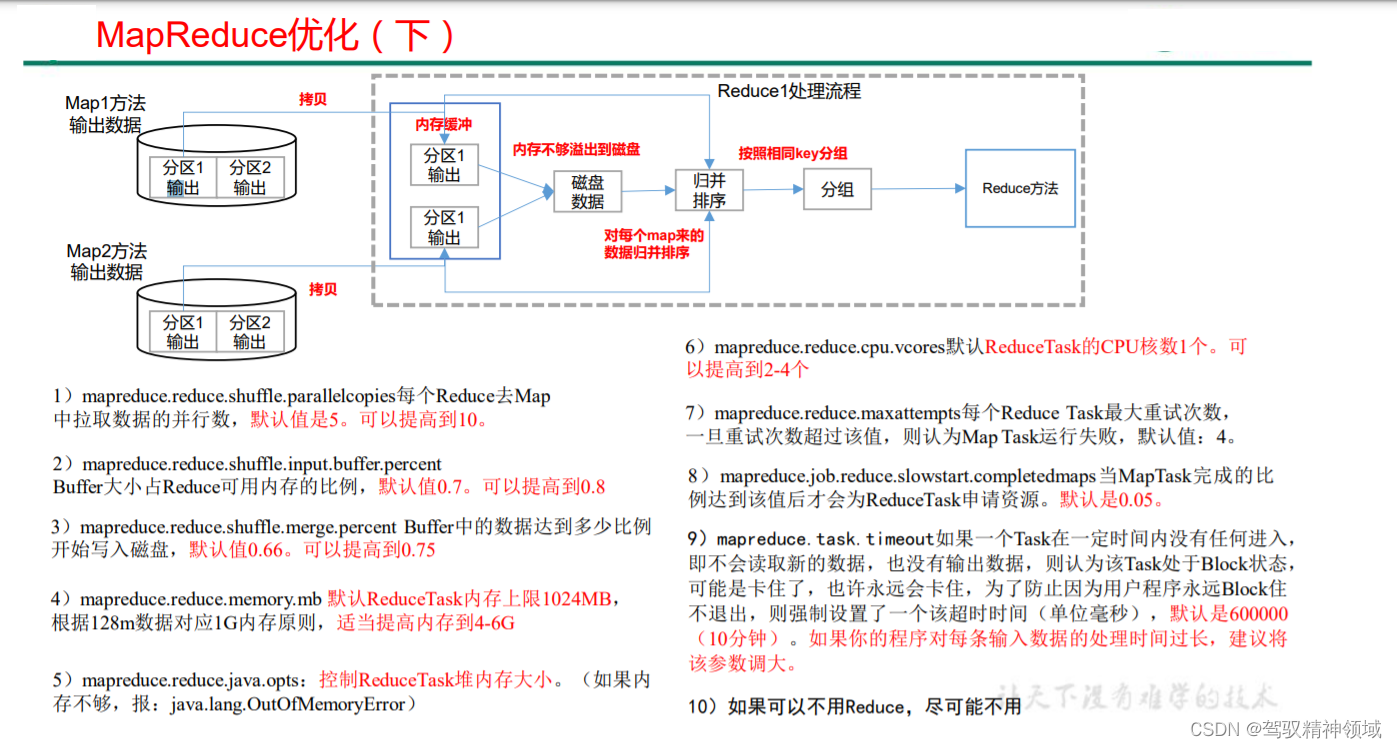
Chapter 8. MapReduce production experience
opencv
[C /vb.net] convert PDF to svg/image, svg/image to PDF
Judge whether the date time exceeds 31 days
opencv鼠标键盘事件
Mysql database
Oracle Database Introduction
Pdf files can only print out the first page
Unit test framework + Test Suite
使用conda创建自己的深度学习环境