当前位置:网站首页>How does wechat prevent withdrawal come true?
How does wechat prevent withdrawal come true?
2022-07-06 17:22:00 【TiggerRun】
WxPcHook
Hook technology There may be nothing strange anymore , But I only recently learned , Keen interest oh , Many people say that this is to make money
Use the teacher's words at the beginning of the article “ Only for technical exchange , Legal boundaries must not be touched ”
I have learned a lot recently by watching videos and so on . But learning from video has a drawback , Others have told you how to solve this problem . Like going CE Search for some feature codes in . For example, I want to talk about “ Anti withdrawal ” The teaching of big guys lets you search from the beginning revoke This keyword ( This is the end of my search CALL Look at some tutorial articles later ), I feel a little bit lucky , So I try to pass the knowledge I learned before , Solve this problem by yourself .
Final effect
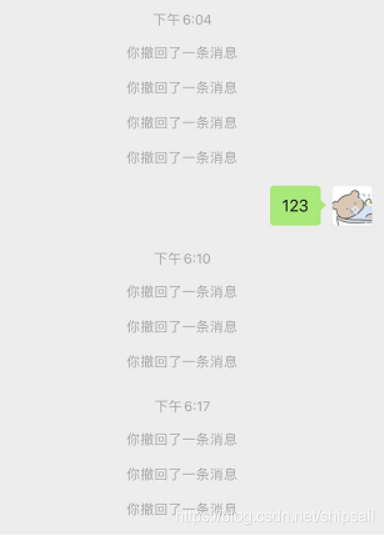
Scenario
We can receive messages CALL Get the following parameters
1. Who sent it to you ?
2. What happened ?
3. What type ?
4. There is also a string of encrypted similar hash String ( It may be the role of identification )
If we are programmers , When we do the recall function, we must pass the parameter to the function, which should be the message ID Well ?
Now we know nothing about the inside of the program , So I want to pursue what we can't see through what we can see .
See the visible changes
We are wx Recall a message , Original message , Output a “ So and so Recalled a message ”
So in CheatEngine Mid search “ withdraw ”
Back to 20 Multiple results 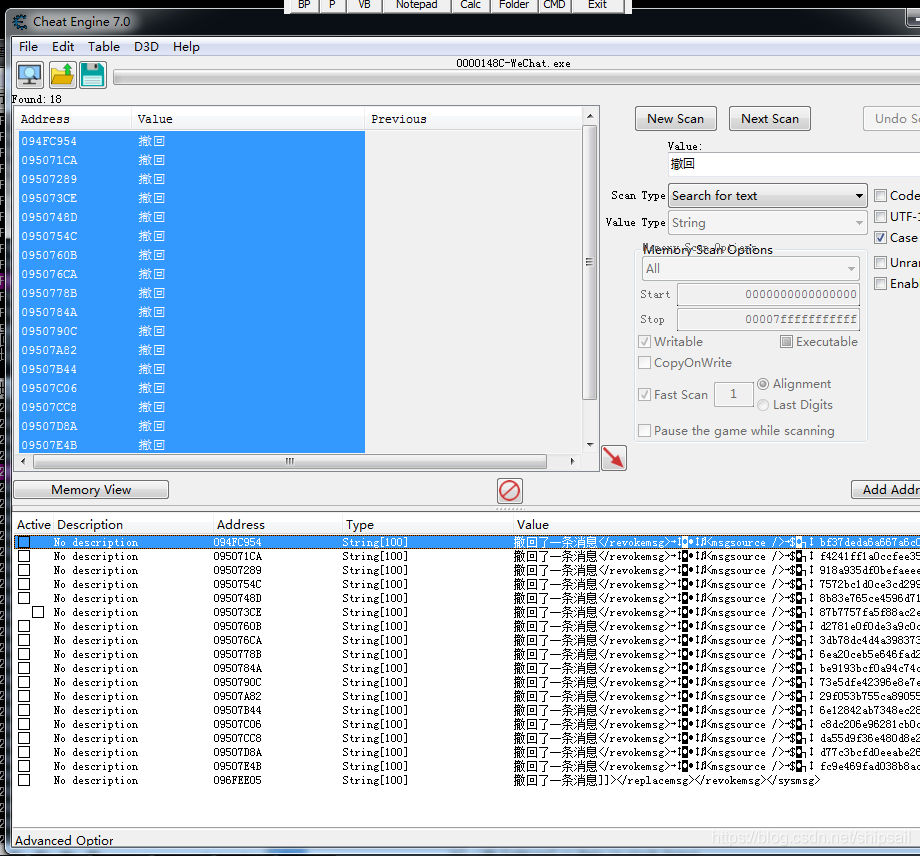
You can put “Type” String Unicode The length is larger , In this way, we can see a lot of data following this record .
20 Multiple data , Testing is very convenient , Directly pull them down for further testing
The second step is to select the variable address
We repeat the withdrawal , Find the variable address that follows the change , Random variables can be deleted directly , Because it's a temporary variable .
In this way, the scope can be narrowed more accurately .
Step 3 memory breakpoint
Function when recalling a message , You definitely need to access memory to get data .
You can use memory breakpoints , Query the function calls in the stack
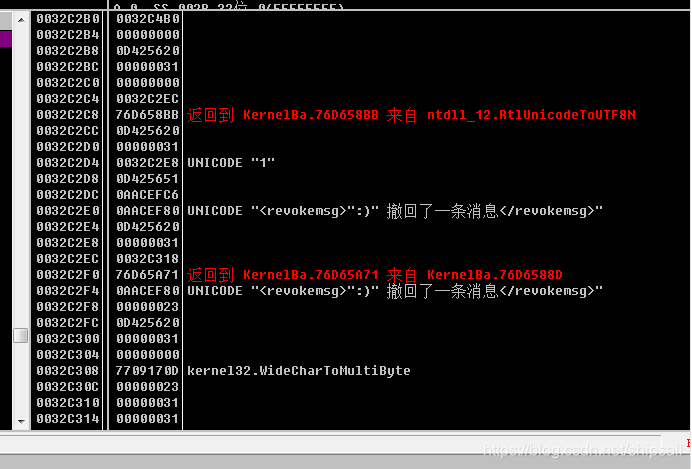
Here we see the upcoming withdrawal The message content , And the content to be output , This indicates that there may be the function address we want nearby . Continue to look at the bottom of the stack .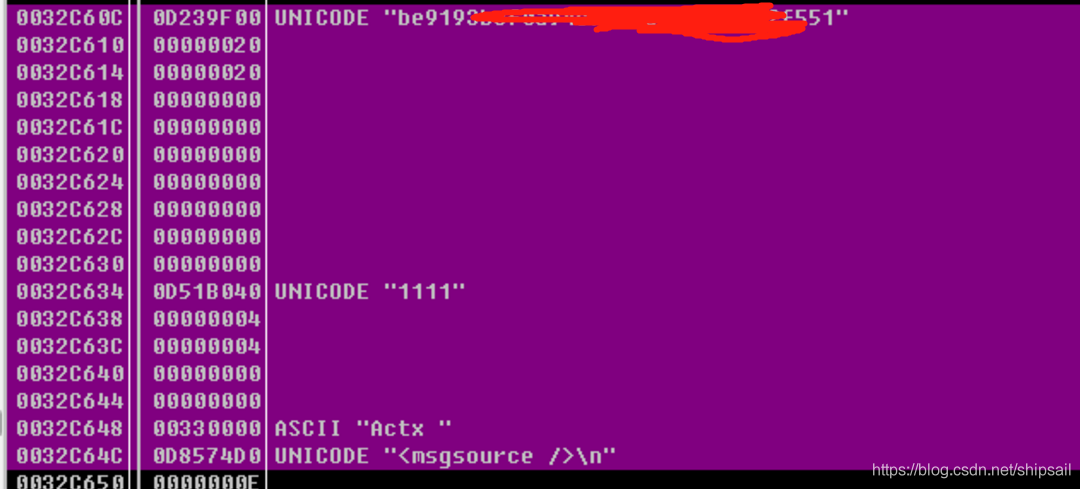
There is news that we want to withdraw , And the string of encrypted strings in the message . Find the required parameter data !!
I'll break at this function address
Function tracking
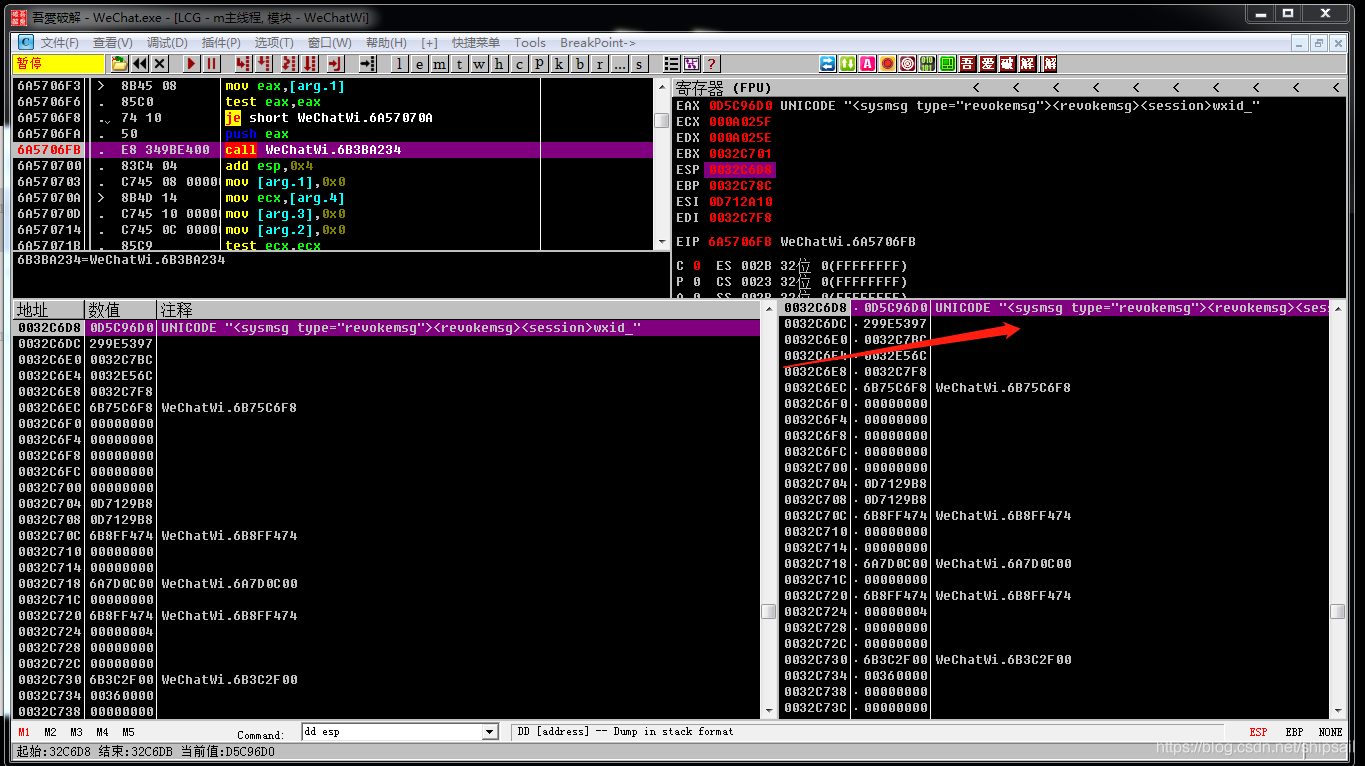
- When receiving the letter , Do not perform the magic
- When you withdraw , The function is executed
This indicates that this is the function required for the recall operation 【 It's probably what we want 】
mov eax,[arg.1] // Pass in the parameter
test eax,eax
...
push eax
call function
add esp,0x4 // Balance the stack
I modified call direct jmp To the next command , Found that the message was not withdrawn , But click continue , The message was withdrawn !
This explanation : This function is the only way , But not the most important , The recalled function should be after it .
Then I follow up the function foolishly , Find a cycle into . Let's think of it as a message cycle , In short, I didn't follow .
Another way of thinking …
The previously disconnected function passed in a parameter [arg.1], Keep it eax,eax It is pushed into the stack for the function to be called to use , So here comes the question ,[arg.1] Is the stack we see esp Some parameters in
<?xml version="1.0" encoding="utf-8"?>
<sysmsg type="revokemsg">
<revokemsg>
<session>wxid_0h3n1axxxxxxxx</session> Buddhist code
<msgid>1701xxxxx</msgid> Buddhist code
<newmsgid>79069xxxxxxxxx</newmsgid> Buddhist code
<replacemsg><![CDATA[":)" Recalled a message ]]></replacemsg>
</revokemsg>
</sysmsg>
Scene simulation
VOID func1(msg,param){
// win Message loop for
switch(msg){
case " withdraw ":
revokeMsg(param);
break;
default:
break;
}
}
// Our current function
VOID revokeMsg(param){
func3(param); // What we want call
}
VOID func3(arg_1){
// Did some functions
}
So the function that calls this function , That is, the outer function , So we should continue to look for the outer layer , Look in the stack .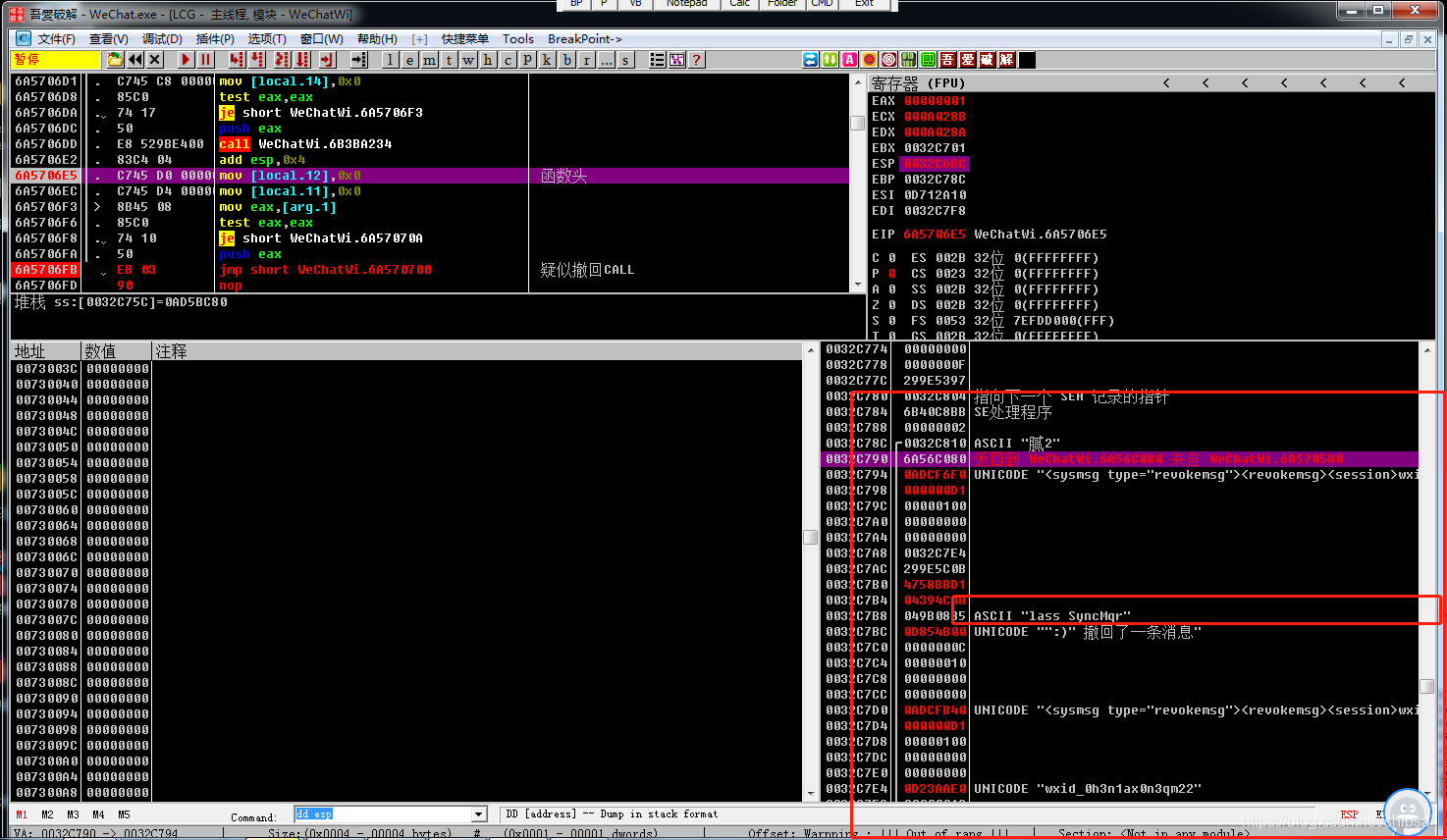
See here , This is already the outer layer , Further down, there will be no message parameters , And saw
LASS SycnMgr I don't know what this is
A guess
Mgr:MySQLGroupReplication
Sycn: Sync
MySQL Group Replication yes MySQL Officially launched a new high availability and high expansion solution , Provide high availability 、 High expansion 、 Highly reliable ( Strong consistency ).
No matter Wx Does it mean this , This Probably It's a message loop 【 Now it's just speculation , I didn't tell you that this is the signature of a message cycle 】
We follow up on this CALL Lower breakpoint , Found this CALL The call of is before our previous breakpoint ( Of course, this is taken for granted , Because we found it here through the bottom of the stack )
I use it directly F8 Try this function , It is found that the message on the interface has not been withdrawn , It shows that this is not the real entrance we want . Then look at the assembly code window online , Find the main function entry , And set a breakpoint .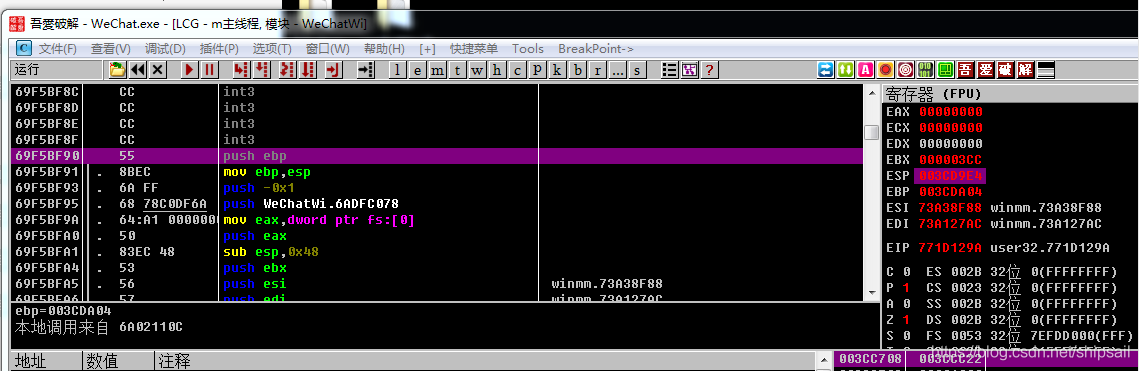
When you withdraw , It can still be disconnected .
Directly modify the assembly ,push ebp by ret
For the time being, I don't care where I will return , Let's try it first , Sure enough, the news was not withdrawn , And the program didn't crash .
In this way, we can easily locate the one that prevents withdrawal CALL The location of .
Back to that LASS SycnMgr, How do I judge that it is a characteristic character of message cycle ?
After we find what should be called the outermost layer Recall function , The outer layer should be a message cycle ???
Let's do it , Track down
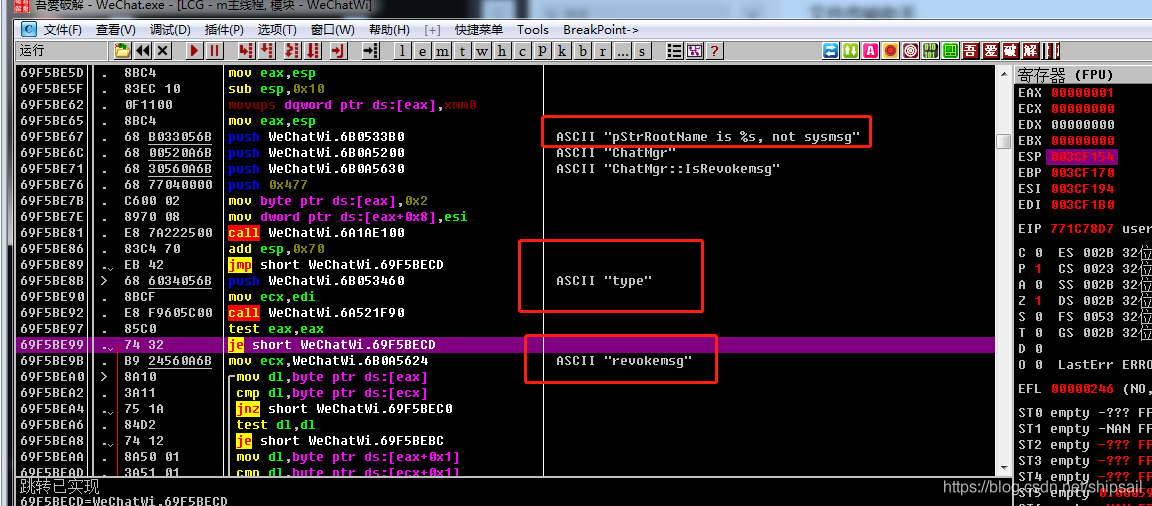
Here we can probably see that it is a message cycle ??
Determine the message type ??? Etc., etc. ...
expectation
I use the latest version 2.8 Version of , Interested partners can study with me .
“ This article is only for technical exchange , Legal boundaries cannot be touched ”
边栏推荐
- Resume of a microservice architecture teacher with 10 years of work experience
- Idea breakpoint debugging skills, multiple dynamic diagram package teaching package meeting.
- JVM垃圾回收概述
- Activiti目录(三)部署流程、发起流程
- Flink 解析(七):时间窗口
- Many papers on ByteDance have been selected into CVPR 2021, and the selected dry goods are here
- Login to verify the simple use of KOA passport Middleware
- Only learning C can live up to expectations top5 S1E8 | S1E9: characters and strings & arithmetic operators
- 关于Selenium启动Chrome浏览器闪退问题
- Interpretation of Flink source code (III): Interpretation of executiongraph source code
猜你喜欢
【逆向】脱壳后修复IAT并关闭ASLR
TCP's three handshakes and four waves
Some feelings of brushing leetcode 300+ questions
arithmetic operation
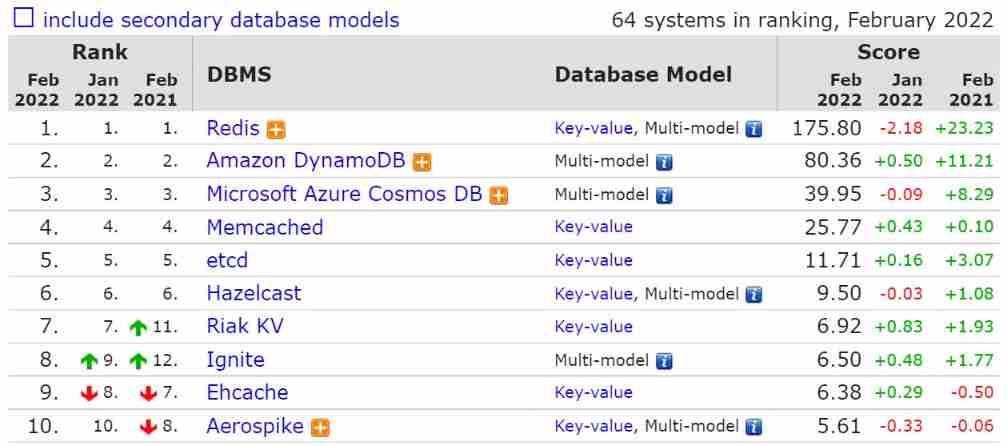
February database ranking: how long can Oracle remain the first?
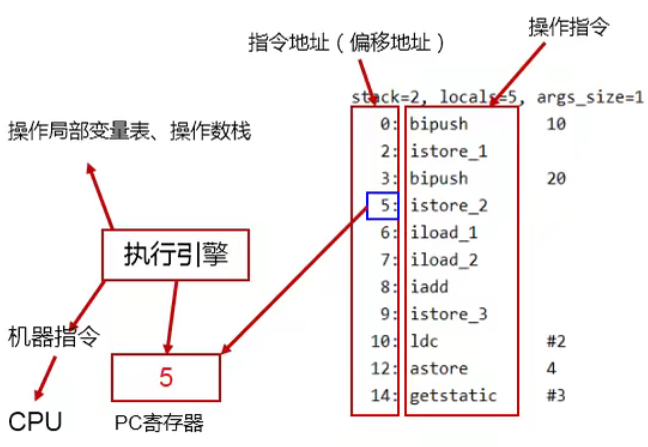
Program counter of JVM runtime data area
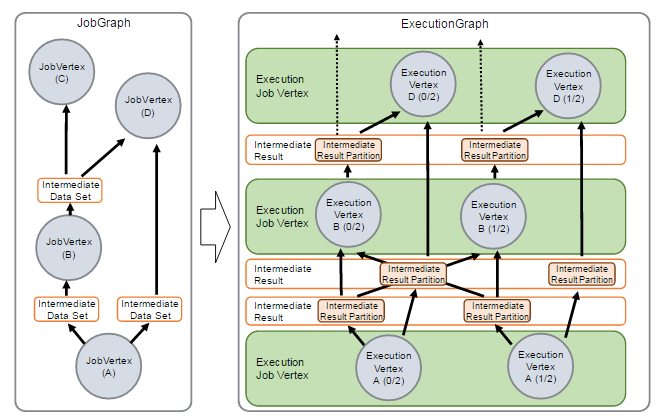
Flink源码解读(三):ExecutionGraph源码解读
Coursera cannot play video
8086 CPU 内部结构
Alibaba cloud server builds SVN version Library
随机推荐
Wu Jun's trilogy insight (V) refusing fake workers
Only learning C can live up to expectations top5 S1E8 | S1E9: characters and strings & arithmetic operators
唯有学C不负众望 TOP5 S1E8|S1E9:字符和字符串&&算术运算符
Flink 解析(四):恢复机制
yum install xxx报错
Login to verify the simple use of KOA passport Middleware
Akamai浅谈风控原理与解决方案
Flink 解析(五):State与State Backend
暑假刷题嗷嗷嗷嗷
Programmer orientation problem solving methodology
8086 CPU 内部结构
[CISCN 2021 华南赛区]rsa Writeup
Flink 解析(七):时间窗口
SQL tuning notes
Wu Jun's trilogy experience (VII) the essence of Commerce
GCC error: terminate called after throwing an instance of 'std:: regex_ error‘ what(): regex
微信防撤回是怎么实现的?
8086 segmentation technology
8086 memory
JVM类加载子系统