当前位置:网站首页>Storage related contents of data in memory
Storage related contents of data in memory
2022-06-25 13:13:00 【LIn_ jt】
The storage of data in memory
We already know ,c There are several variable types in the language , Respectively :>
char // Character type
short // Short
int // integer
long // Long integer
long long // Longer integers
float // Single-precision floating-point
double // Double precision floating point
This article will introduce the storage of integer data in memory .
The first is to categorize integer types , It should be noted that ,char Types also come down to integer types , Because the character type is in memory with ascii Code value for storage .
That is, there are these members in the integer family :>
We know , When creating a variable , Will accordingly open up a space in memory , So how is the data of this variable stored in memory ?, We need to know the following first :>
One . The original code, the reverse code, the complement code
1. Original code :
The binary bit written directly according to the data is the complement of the number , Take a chestnut :
We go through -1 Directly write out the binary sequence, which is the original code of the number , It should be noted that , The highest bit of the binary sequence is the symbol , A negative number is 1, A positive number is 0
2. Inverse code :
The inverse code is based on the original code , The sign bits remain the same , Other bits are reversed , Or the example above , Let's see -1 The inverse of :>
![**[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-rHAuNVSj-1637644746297)(C:\Users\MSI-NB\AppData\Roaming\Typora\typora-user-images\image-20211122232506362.png)]**](/img/e3/3104dbe088e3e02cbdc8c6668ae819.png)
3. Complement code :
The complement is based on the original code +1 that will do :
This is all we know 1 Binary sequence
therefore , The calculation rule of the original inverse complement is :

The complement wants to be transformed into the original code, that is, the above inverse process , That's the complement -1 Get the inverse , Then the inverse sign bit remains unchanged , Other bits can be reversed by bit .
The above discussion is based on the case that the data is negative , actually , If the data is positive , The original code, inverse code and complement are the same , Take a chestnut

The original code, the inverse code and the complement are the binary sequence .
And all stored in memory are complement . You can use the original code to calculate -1+1, You will find that the result is equal to -2, Common sense tells us that this is impossible :

Two . Large and small end storage
Let's take a look at the storage of a variable in memory :
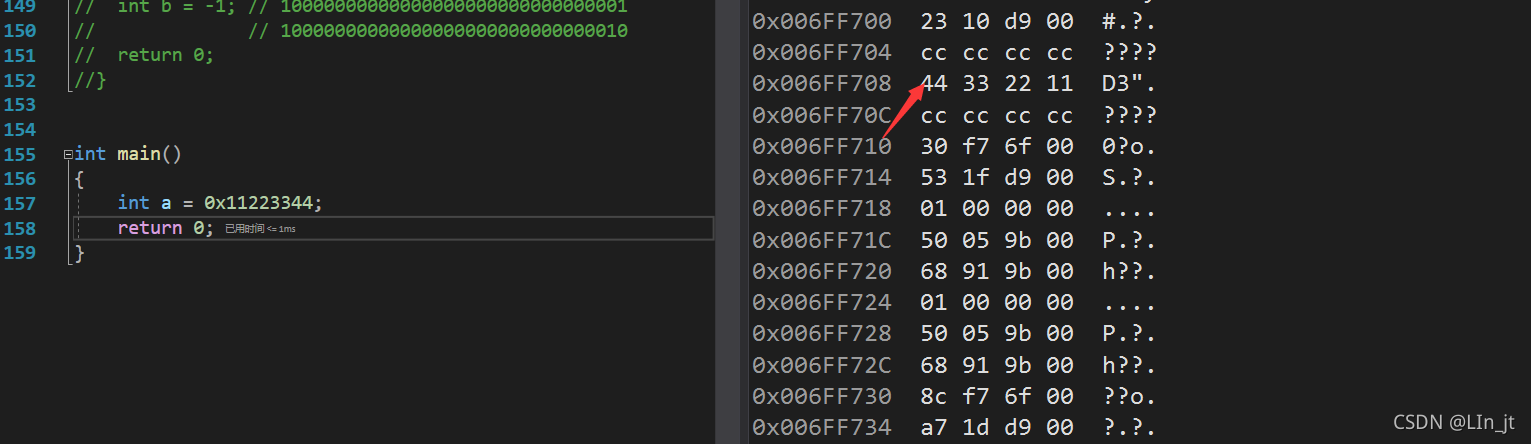
We found that , This variable is stored upside down in memory , namely 44332211 Store by , actually , Variables are stored in memory in two ways :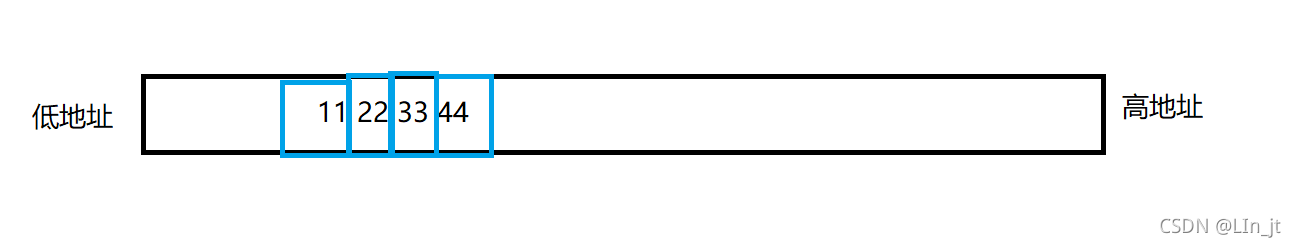
We know ,44 yes a Low order byte order , If the low byte order is stored at the high address , The high byte order is placed at the low address , It is called big end storage .
And the following

It is called small end storage , That is, the contents of the low byte order are stored at the low address , The contents of the high byte order are stored at the high address .
Now let's give the concept of big end and small end :
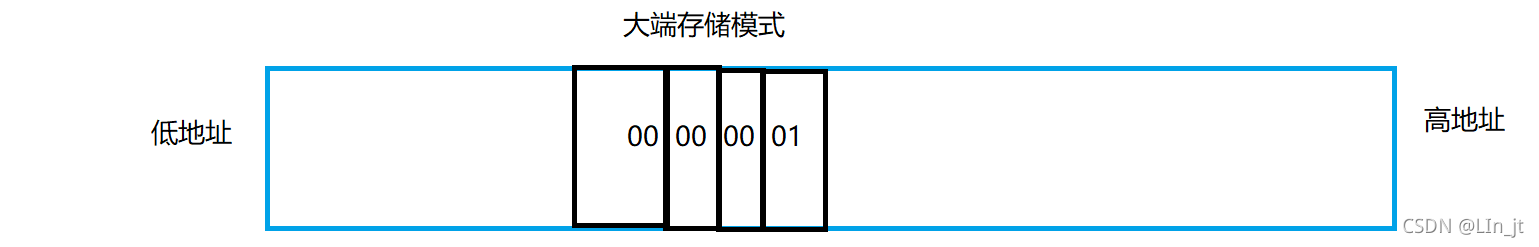
Big end storage : It refers to storing the contents of the low byte order of data at the high address , The contents of the high byte order are stored at the low address .
Small end storage : It refers to storing the contents of the low byte order of data at the low address , The contents of the high byte order are stored at the high address .
Now let's design a program to judge vs Is it big end storage or small end storage in the environment , We just need to look at the contents of the first byte of a data , namely

therefore , We only need to access the contents of the first byte , Then we need to use a char Pointer variable of type .
We designed the following program :>

The result is :>
therefore ,vs Under the compiler, integer data is stored as small end storage .
边栏推荐
- 20220620 面试复盘
- 康威定律,作为架构师还不会灵活运用?
- KDD 2022 | graphmae: self supervised mask map self encoder
- Confusion caused by the ramp
- Differences between JS and JQ operation objects
- Qt显示FFmpeg解码的图片
- 关于扫雷的简易实现
- Django framework - caching, signaling, cross site request forgery, cross domain issues, cookie session token
- [转]以终为始,详细分析高考志愿该怎么填
- Three lines of code to simply modify the project code of the jar package
猜你喜欢
深圳民太安智能二面_秋招第一份offer

Uncover gaussdb (for redis): comprehensive comparison of CODIS
An article clearly explains MySQL's clustering / Federation / coverage index, back to table, and index push down

Configuring pytorch in win10 environment

mysql导入导出数据到excel表日期出现问题

关于结构体,枚举,联合的一些知识

Serevlt初识

剑指 Offer II 032. 有效的变位词

Capabilities required by architects

Online service emergency research methodology
随机推荐
[flask tutorial] flask overview
1251- Client does not support authentication protocol MySql错误解决方案
指针,它那些不得不说的题目
与生产环境中的 console.log 说再见
关于数据在内存中存储的相关例题
Online service emergency research methodology
C # switch between Chinese and English input methods
原生js---无限滚动
KDD 2022 | GraphMAE:自监督掩码图自编码器
关于扫雷的简易实现
Back test of quantitative trading - example of futures CTA strategy (tqzfuturerenkoscalpingstrategy)
MySQL adds, modifies, and deletes table fields, field data types, and lengths (with various actual case statements)
Geospatial search: implementation principle of KD tree
买基金在哪里开户安全?还请赐教
3+1 guarantee: how is the stability of the highly available system refined?
Another night when visdom crashed
Configuring pytorch in win10 environment
Uncover gaussdb (for redis): comprehensive comparison of CODIS
JSTL tag: fmt:formatdate tag format Chinese standard time or timestamp
Drawing cubes with Visio