当前位置:网站首页>Sign SSL certificate as Ca
Sign SSL certificate as Ca
2022-07-06 02:47:00 【uiop_ uiop_ uiop】
In order to solve ssl Problems with certificate signing . for example : Apply for free ssl There is no way to add certificates dns Parse entry ,vps No domain name filing , Make it impossible to complete the formal ssl Certificate issued .SSL Self signature is not reliable , Many browsers may also not recognize self signed certificates . In order to eradicate this problem directly , We act directly as CA, Use self signature CA Certificate to issue the required SSL certificate . I stepped on a lot of pits during this period , Finally finished .
ssl.conf
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = req_ext
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = GB
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = England
localityName = Locality Name (eg, city)
localityName_default = Brighton
organizationName = Organization Name (eg, company)
organizationName_default = Hallmarkdesign
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = IT
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_max = 64
commonName_default = 【SERVER_DOMAIN_NAME_WITH:PORT_NUMBER】
[ req_ext ]
subjectAltName = @alt_names
[alt_names]
IP.1 = 【YOUR_SERVER_PUBLIC_IP】
DNS.1 = 【SERVER_DNS_DOMAIN】
sign.conf
subjectAltName=IP:【SERVER_IP_ADDRESS】,DNS:【DNS_NAME】Here are the specific commands .
cd ~
openssl rand -writerand .rnd
cd 【WORKING_DIRECTORY】
openssl genrsa -des3 -out rootCA.key 4096
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 99999 -out rootCA.crt
openssl genrsa -out server.key 2048
openssl req -new -sha256 -out server.csr -key server.key -config ssl.conf
openssl x509 -req -in server.csr -CA rootCA.crt -CAkey rootCA.key -CAcreateserial -out server.crt -days 99999 -sha256 -extfile sign.confThe back end here is flask For example . The following configuration ssl Certificate and private key
ssl_context = ("server.crt", "server.key")Then in order to complete the whole trust chain , take rootCA.crt Import as “ Trusted root certificate ” that will do . Android and Windows All the tests were successful , Painless access https Interface , no need 443 It is normal to replace the port with another port , in front 【SERVER_DOMAIN_NAME_WITH:PORT_NUMBER】 Just mark the port , for instance test.example.com:6666
design sketch :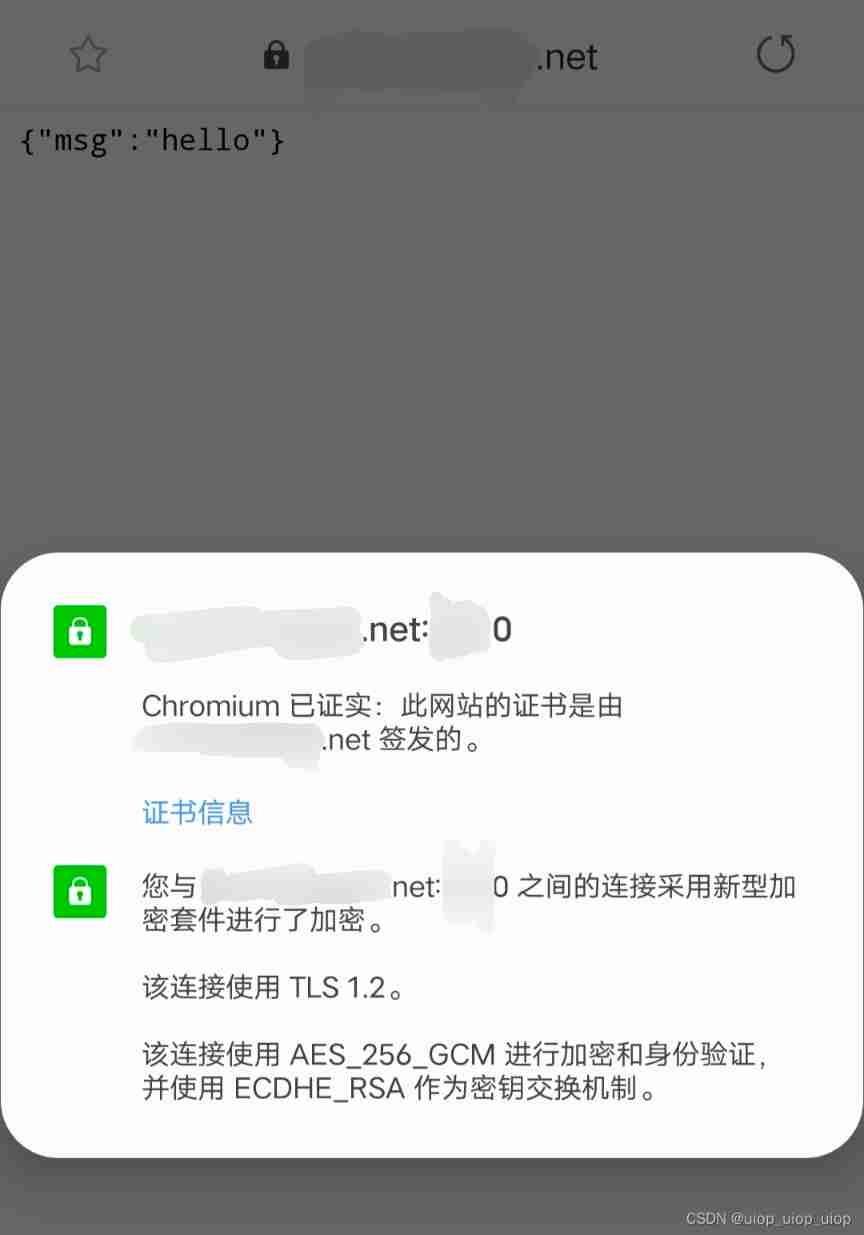
You may encounter the situation that there is no record when you visit , But try restarting the back-end service program
边栏推荐
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9
- 微服务间通信
- Fault analysis | analysis of an example of MySQL running out of host memory
- Crawler (9) - scrape framework (1) | scrape asynchronous web crawler framework
- Is there a case where sqlcdc monitors multiple tables and then associates them to sink to another table? All operations in MySQL
- Pat 1046 shortest distance (20 points) simulation
- 【Unity3D】GUI控件
- tcpdump: no suitable device found
- QT release exe software and modify exe application icon
- 2020.02.11
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9](/img/ed/0edff23fbd3880bc6c9dabd31755ac.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9
Apt installation ZABBIX
![[matlab] access of variables and files](/img/cf/6f3cfdc4310fcf0bdcaa776d68261e.jpg)
[matlab] access of variables and files
MySQL advanced notes
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12](/img/b1/926d9b3d7ce9c5104f3e81974eef07.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12
A copy can also produce flowers

PMP practice once a day | don't get lost in the exam -7.5
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6](/img/38/51797fcdb57159b48d0e0a72eeb580.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6
RobotFramework入门(一)简要介绍及使用
力扣今日题-729. 我的日程安排表 I
随机推荐
Summary of Bible story reading
微服务间通信
Pat grade a 1033 to fill or not to fill
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
Elimination games
淘宝焦点图布局实战
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 7
Advanced technology management - what is the physical, mental and mental strength of managers
Redis skip table
2.12 simulation
Technology sharing | what if Undo is too big
深度解析链动2+1模式,颠覆传统卖货思维?
【若依(ruoyi)】启用迷你导航栏
MySQL winter vacation self-study 2022 11 (8)
After changing the GCC version, make[1] appears in the compilation: cc: command not found
Dachang image library
1. Dynamic parameters of function: *args, **kwargs
HDU_ p1237_ Simple calculator_ stack
Sword finger offer 30 Stack containing min function
Microsoft speech synthesis assistant v1.3 text to speech tool, real speech AI generator