当前位置:网站首页>DDoS attacks - are we really at war?
DDoS attacks - are we really at war?
2022-07-06 02:31:00 【zy18165754120】
Arbor Networks The chief safety scientist of Craig Labovitz Use the company's ATLAS Internet mapping technology analyzes DDoS attack , According to him , The biggest problem these websites face is flood attack .
He said , stay 2010 During the year ,Arbor Networks It was observed that 50+ Gbps Many in the range DDoS attack .
“ These large-scale flooding attacks usually exceed the total inbound bandwidth capacity of the backbone links of the data center and operators ( Usually it is OC192 / 10 Gbps)”, He was in His security blog says .
and , He went on to add , Despite thousands of tweets 、 News articles and endless hype , But most of the attacks last week were relatively small and simple .
He explained that the :“ In short , In addition to the strict censorship of the media , These attacks are not noticeable ”.
for example , stay Cablegate The third day after the initial release of the document (12 month 1 Japan ) , His company analyzed a number of WikiLeaks Hosting site DDoS Activities , He said ,DDoS Traffic never exceeds 3-4 Gbps.
He claimed that , Mitigating attacks on this scale is important for 1/2 layer ISP And large content / Managed service providers are fairly routine , And more disturbing than the imminent threat to critical infrastructure ——“ Or as an Internet engineer explained ‘ Easy to stop ’ ”.
Labovitz Express , In an incident last week , about 20% Retaliatory attack DDoS HTTP The request comes from a new LOIC variant , Predictably enough ,LOIC-2.
“LOIC A new version of the —— Yes LOIC Complete rewrite of —— Support extra ‘ hive ’ Remote control command channel , Include RSS、Twitter and Facebook”, He said .
“ what's more ,LOIC-2 Support two new ‘ Slow down ’ Attack methods ( That is, the client intentionally extends HTTP Transaction time to increase the burden on the victim server DDoS Strategy )”, He added .
and ,Arbor Networks The chief scientist went on to say , Although the last round of attacks led to a brief interruption , But most operators and hosting service providers can quickly filter attack traffic .
Besides , He said , These attacks are mainly aimed at web pages or mild reading blogs , Rather than a more critical back-end infrastructure for commercial transactions .
“ By the end of this week , Anonymous followers mostly abandoned their attack plans because they were ineffective ,” He said .
“ therefore , Final , I suggest going around WikiLeaks supporters and opponents DDoS An attack is far from a cyber war ,” He added .
“ Although its title is far from sexy , But network sabotage may be a more appropriate description . Similarly , The foreign policy column will hactivist DDoS The number is equivalent to the sit in of young people all over the world .”
边栏推荐
- 0211 embedded C language learning
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
- 729. My schedule I / offer II 106 Bipartite graph
- Easy to use js script
- Spark accumulator
- Multi function event recorder of the 5th National Games of the Blue Bridge Cup
- PAT甲级 1033 To Fill or Not to Fill
- 在线怎么生成富文本
- 729. 我的日程安排表 I / 剑指 Offer II 106. 二分图
- Initial understanding of pointer variables
猜你喜欢
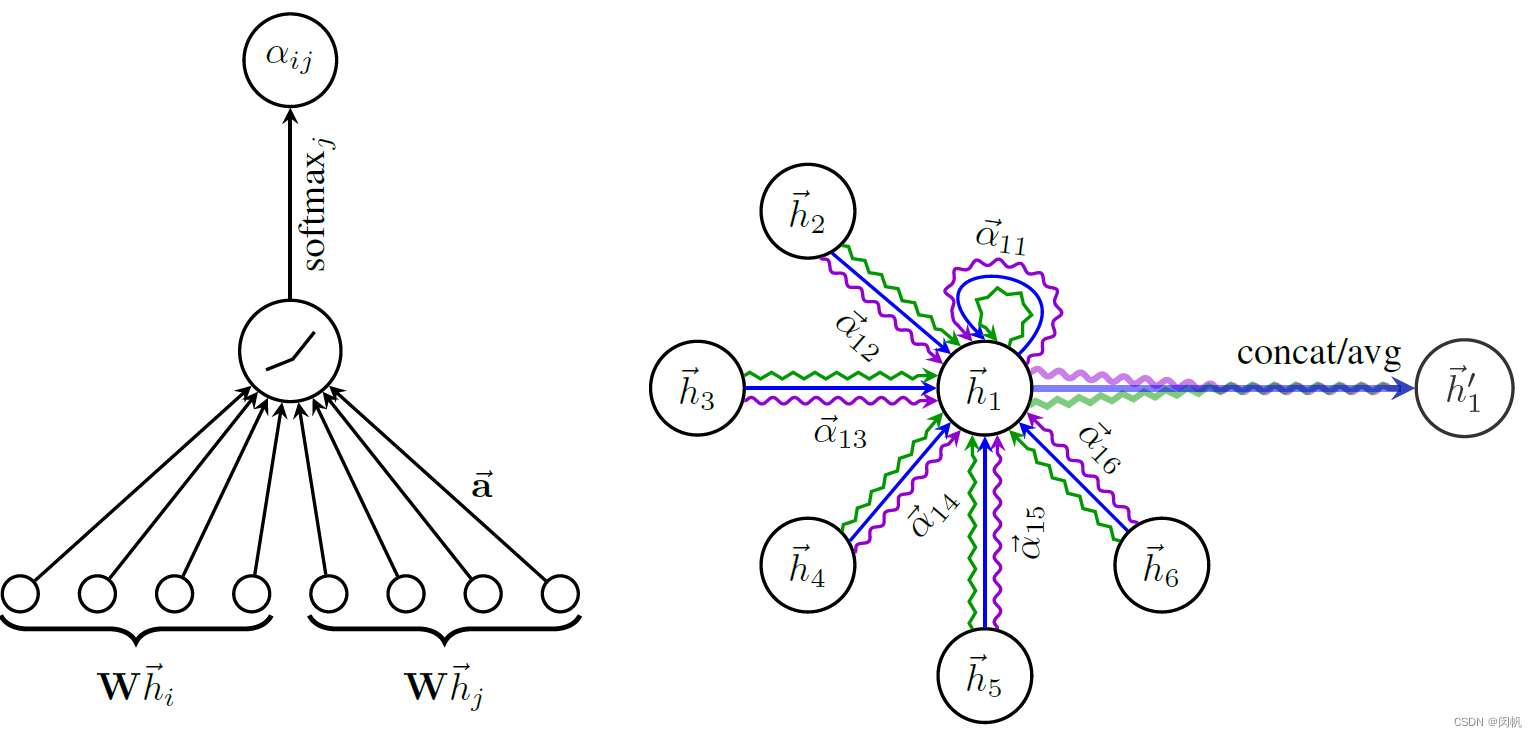
Paper notes: graph neural network gat
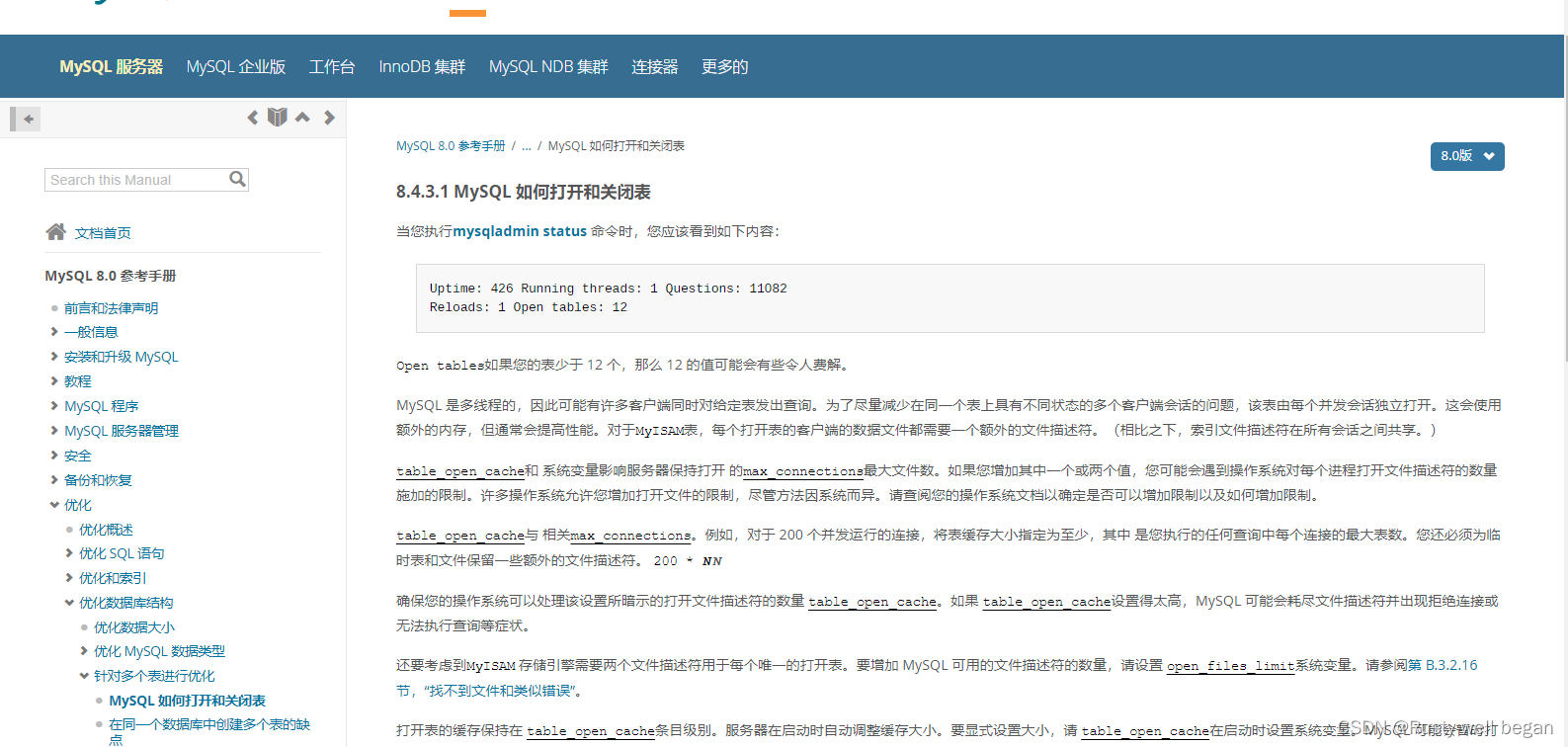
【MySQL 15】Could not increase number of max_open_files to more than 10000 (request: 65535)
2022年版图解网络PDF
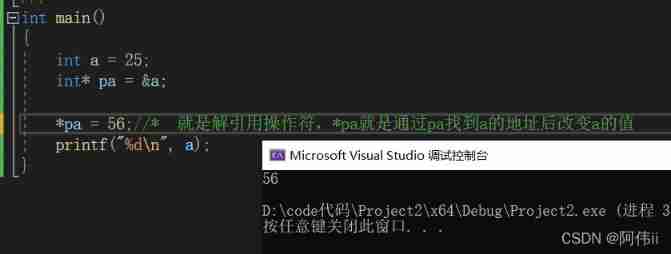
Initial understanding of pointer variables
Minecraft 1.18.1、1.18.2模组开发 22.狙击枪(Sniper Rifle)
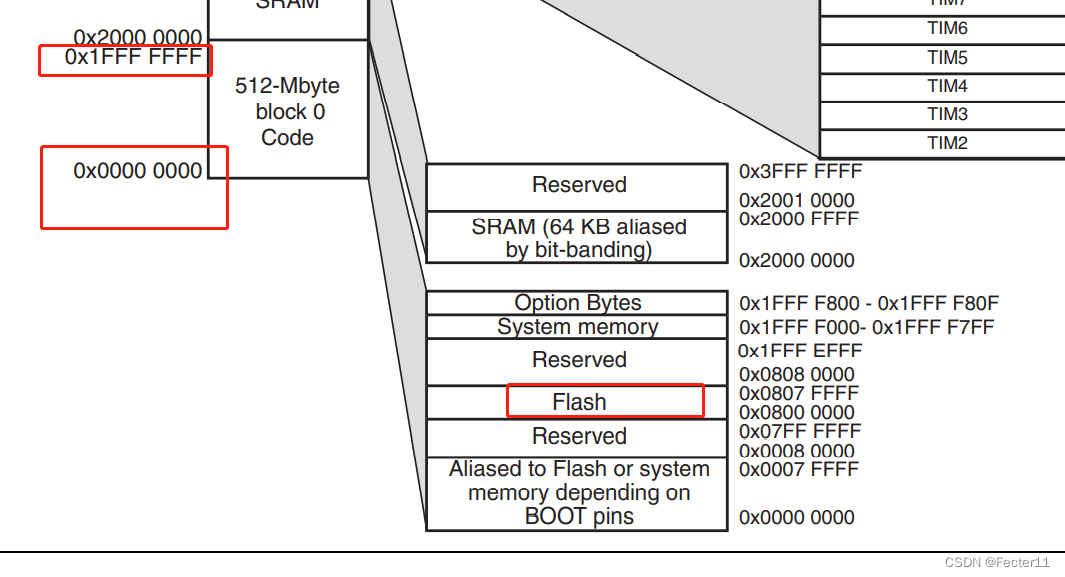
零基础自学STM32-野火——GPIO复习篇——使用绝对地址操作GPIO

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23](/img/72/a80ee7ee7b967b0afa6018070d03c9.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
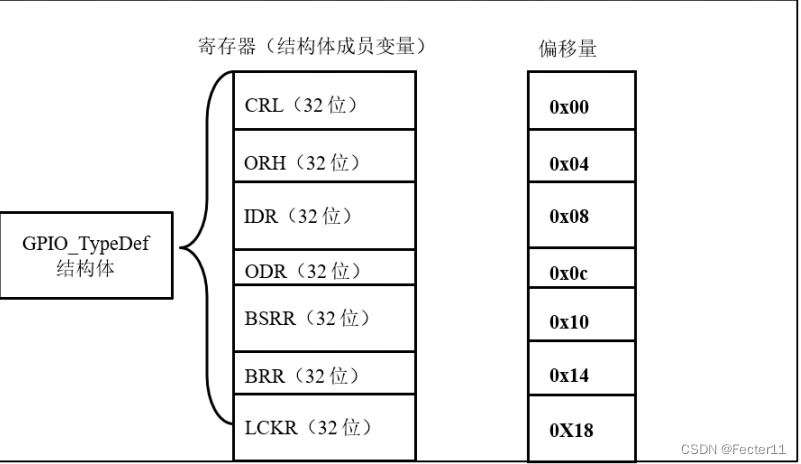
Zero foundation self-study STM32 - Review 2 - encapsulating GPIO registers with structures
![[community personas] exclusive interview with Ma Longwei: the wheel is not easy to use, so make it yourself!](/img/aa/af98b588efd61d71b1b02609817c49.png)
[community personas] exclusive interview with Ma Longwei: the wheel is not easy to use, so make it yourself!
随机推荐
模板_快速排序_双指针
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17
Global and Chinese market of wheelchair climbing machines 2022-2028: Research Report on technology, participants, trends, market size and share
Spark accumulator
RDD creation method of spark
MySQL winter vacation self-study 2022 11 (8)
Use the list component to realize the drop-down list and address list
Use image components to slide through photo albums and mobile phone photo album pages
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Data preparation
Have a look at this generation
Global and Chinese markets of screw rotor pumps 2022-2028: Research Report on technology, participants, trends, market size and share
How to generate rich text online
【社区人物志】专访马龙伟:轮子不好用,那就自己造!
ftp上传文件时出现 550 Permission denied,不是用户权限问题
2022 edition illustrated network pdf
The third level of C language punch in
Déduisez la question d'aujourd'hui - 729. Mon emploi du temps I
After changing the GCC version, make[1] appears in the compilation: cc: command not found
有没有sqlcdc监控多张表 再关联后 sink到另外一张表的案例啊?全部在 mysql中操作