当前位置:网站首页>Brief introduction to revolutionary neural networks
Brief introduction to revolutionary neural networks
2022-07-05 13:51:00 【Deer holding grass】
Convolutional Neural Networks
Computers learn and mine the relevant characteristics of target attributes (Features) To identify and explore the target .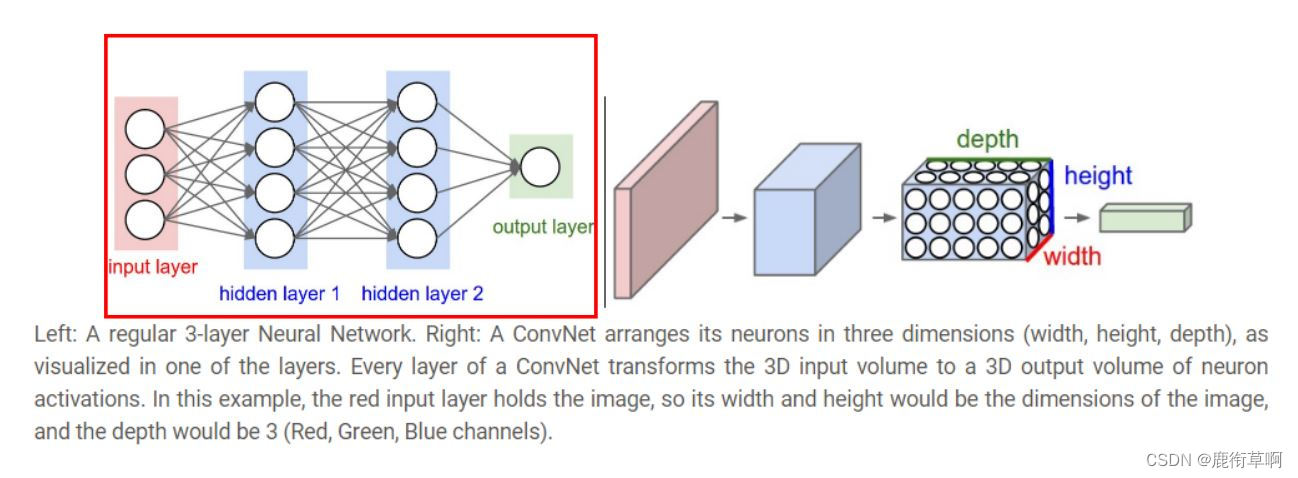
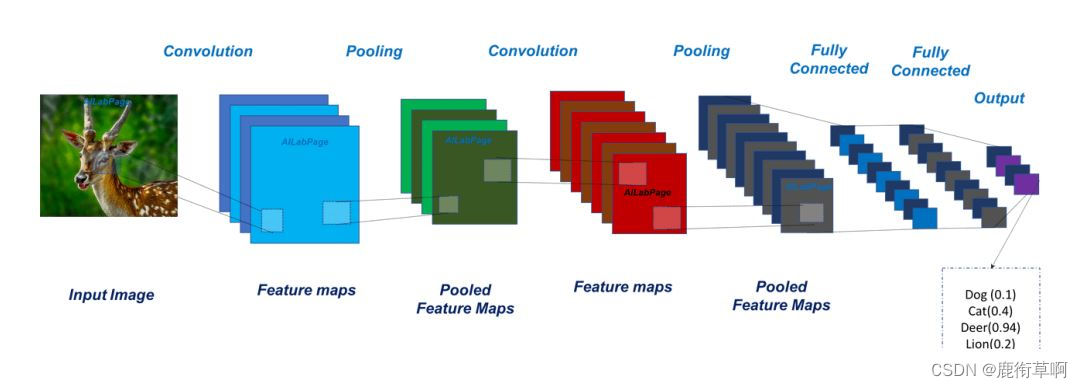
Convolution layer Convolutional Layer
Pooling layer Pooling Layer
Fully connected layer Fully-Connected Layer
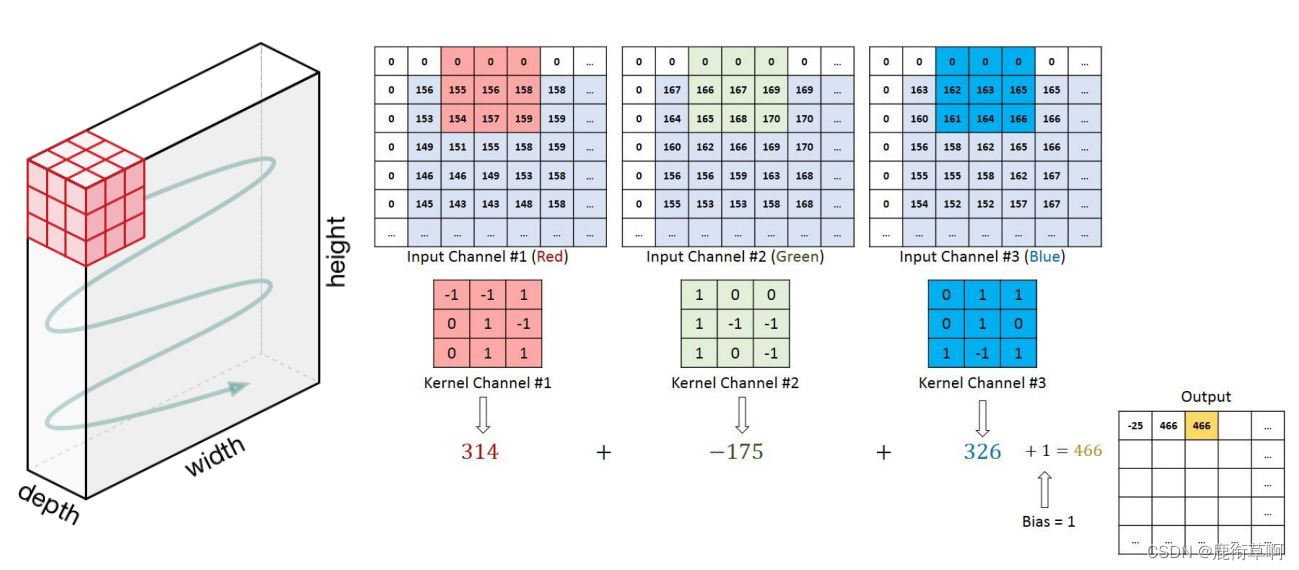
1. Convolution Layer: The Kernel
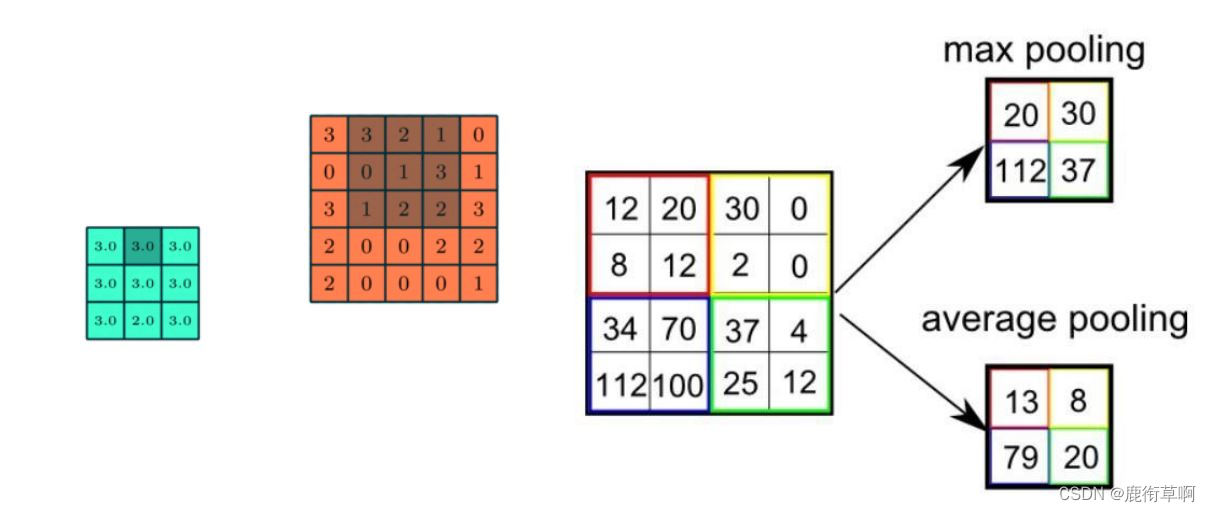
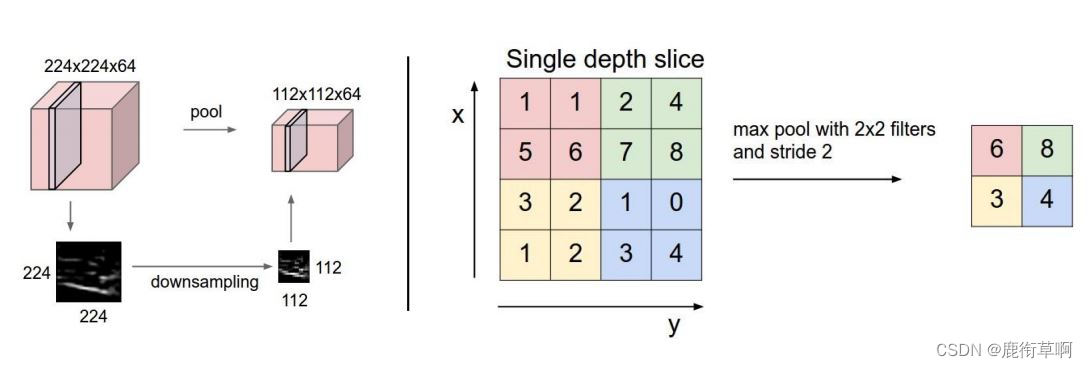
2. Pooling Layer
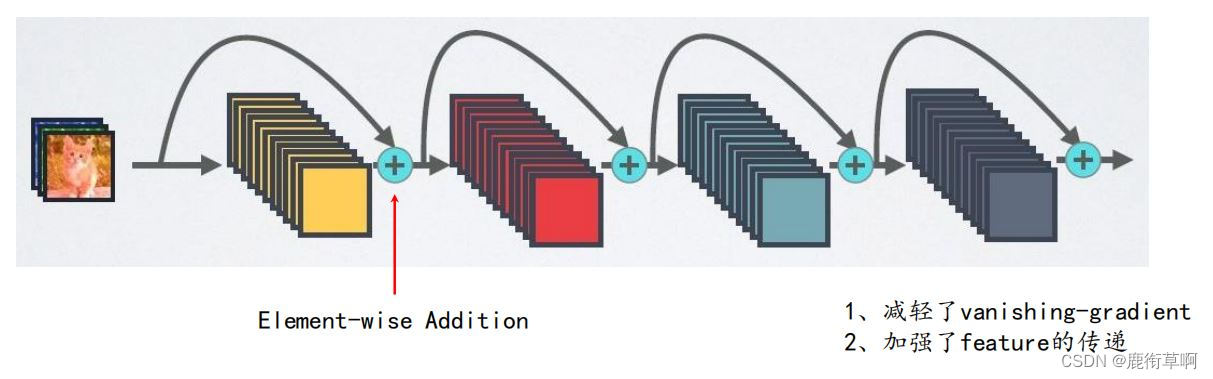
3. ResNet
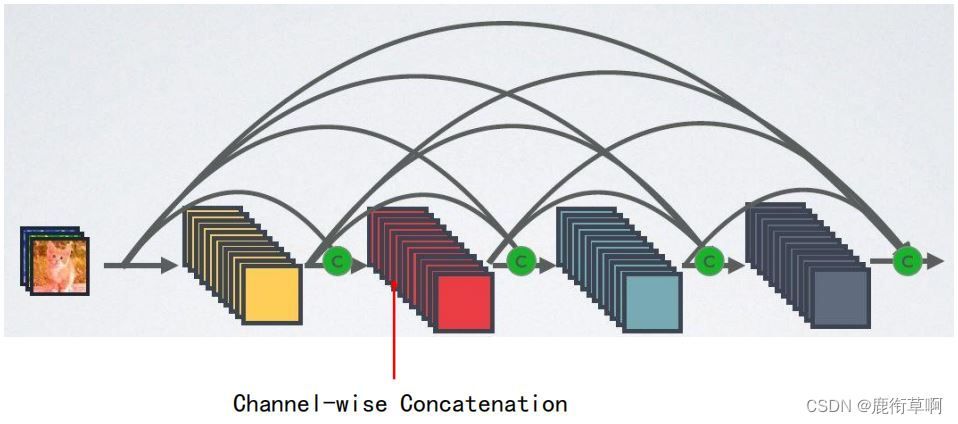
4. DenseNet
- To reduce the vanishing-gradient
- Strengthened feature The transfer
- Make more effective use of feature
- To some extent, the number of parameters is reduced
边栏推荐
- Usage, installation and use of TortoiseSVN
- Datapipeline was selected into the 2022 digital intelligence atlas and database development report of China Academy of communications and communications
- Win10 - lightweight gadget
- Solve the problem of invalid uni app configuration page and tabbar
- asp. Net read TXT file
- 2022建筑焊工(建筑特殊工种)特种作业证考试题库及在线模拟考试
- js 从一个数组对象中取key 和value组成一个新的对象
- Intranet penetration tool NetApp
- About the problem and solution of 403 error in wampserver
- [server data recovery] a case of RAID5 data recovery stored in a brand of server
猜你喜欢
When using Tencent cloud for the first time, you can only use webshell connection instead of SSH connection.
我为什么支持 BAT 拆掉「AI 研究院」
How to apply the updated fluent 3.0 to applet development
ZABBIX monitoring
Nantong online communication group
redis6主从复制及集群
::ffff:192.168.31.101 是一个什么地址?
The development of speech recognition app with uni app is simple and fast.
Ordering system based on wechat applet
Attack and defense world crypto WP
随机推荐
Laravel framework operation error: no application encryption key has been specified
Liste des liens (simple)
Integer = = the comparison will unpack automatically. This variable cannot be assigned empty
stm32逆向入门
STM32 reverse entry
"Baidu Cup" CTF competition in September, web:upload
ELK 企业级日志分析系统
ETCD数据库源码分析——集群间网络层客户端peerRt
Catch all asynchronous artifact completable future
asp. Net read TXT file
Win10 - lightweight gadget
53. Maximum subarray sum: give you an integer array num, please find a continuous subarray with the maximum sum (the subarray contains at least one element) and return its maximum sum.
49. 字母异位词分组:给你一个字符串数组,请你将 字母异位词 组合在一起。可以按任意顺序返回结果列表。 字母异位词 是由重新排列源单词的字母得到的一个新单词,所有源单词中的字母通常恰好只用一次。
What is information security? What is included? What is the difference with network security?
Don't know these four caching modes, dare you say you understand caching?
Jetpack Compose入门到精通
Aspx simple user login
Redis6 master-slave replication and clustering
ZABBIX monitoring
Idea remote debugging agent