当前位置:网站首页>Azure solution: how can third-party tools call azure blob storage to store data?
Azure solution: how can third-party tools call azure blob storage to store data?
2022-07-04 12:12:00 【Nancy198305】
51CTO Blog address : https://blog.51cto.com/14669127
Azure Training video address : https://space.bilibili.com/2000820534
Azure Blob Storage It is Microsoft's cloud based data storage solution ,Blob Storage Optimized for storing large amounts of unstructured data , For example, the text 、video Or binary data, which does not follow a specific data model or definition , A lot of third parties vender In order to support Microsoft 365 Data for backup or archiving , Both support backup storage media yes Azure Blob Storage, So in this case , User IT Admin How to create Azure Blob Storage To connect third-party tools as data storage media ?
today , I will share with you the specific creation process and the configuration information integrated with third-party tools .
· Create a Azure Storage account
· stay Azure Storage Account Created in Container
· Upload Blob
explain :Azure Storage Account Is an essential part of cloud technology , Contains Azure Storage All data objects of :blob、 file 、 queue 、 Tables and disks .
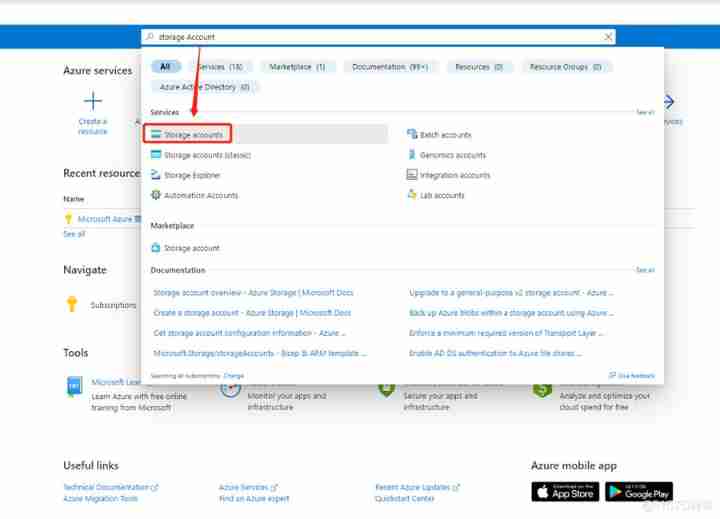
1. stay Azure Portal On the search Storage Account, And then click on , As shown in the figure below :
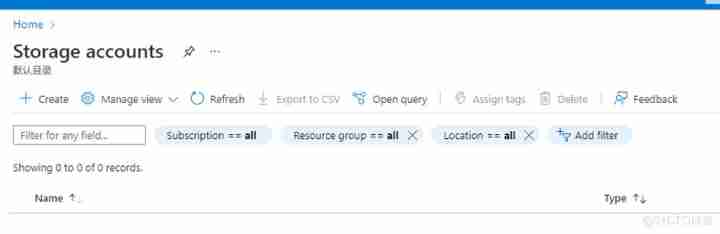
2. stay Storage Account page , Click on Create, As shown in the figure below :
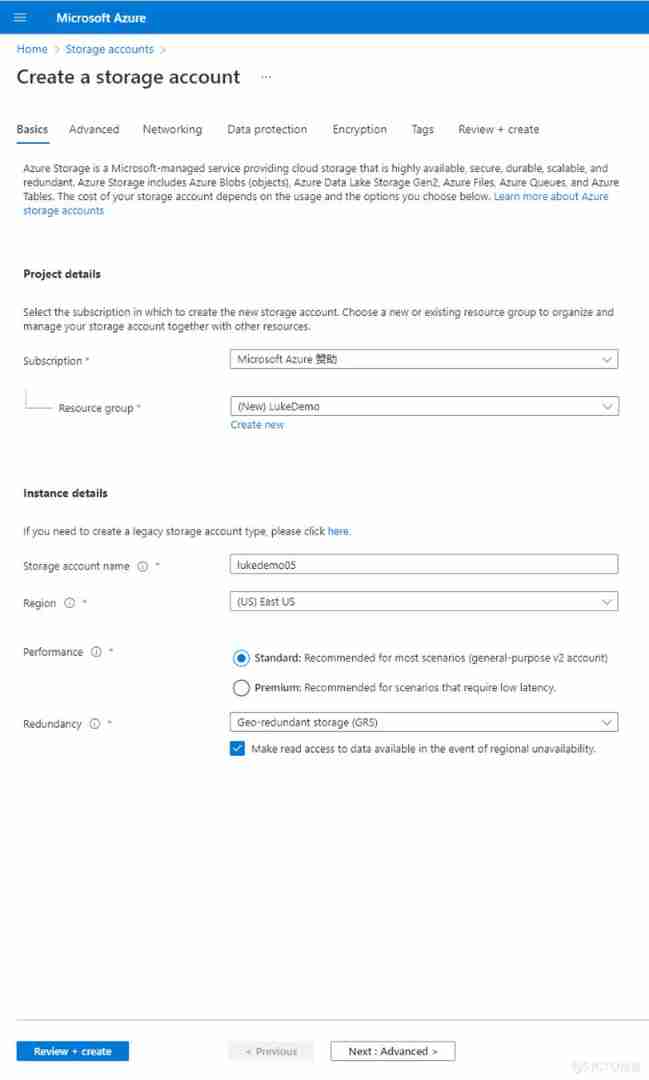
3. Creating account page , Fill in the basic information , Click on review+create, As shown in the figure below :
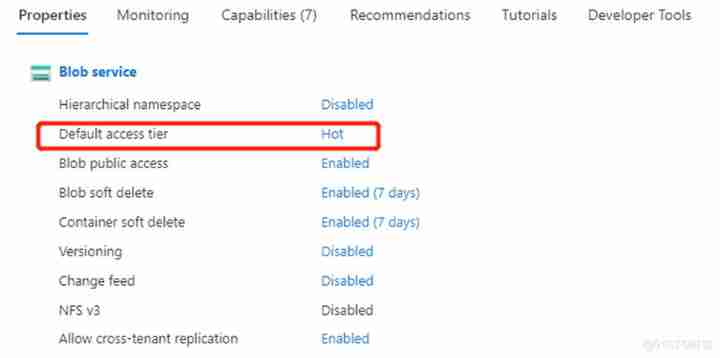
explain :Access Tier It is divided into Hot and Cool Two kinds of , Generally, the frequently accessed data will be located in Hot This floor , The availability of hot storage is higher than that of cold storage 99.9%, The infrequently accessed data will be stored in the cold access layer , Because the cost of cold storage tier is lower , More data can be stored at a lower cost , As shown below :
4. Storage account Once I've created it , We enter resource page , Can be created according to requirements Container,File Share,Azure tables wait , Now let's click... In the left navigation Container, As shown below :
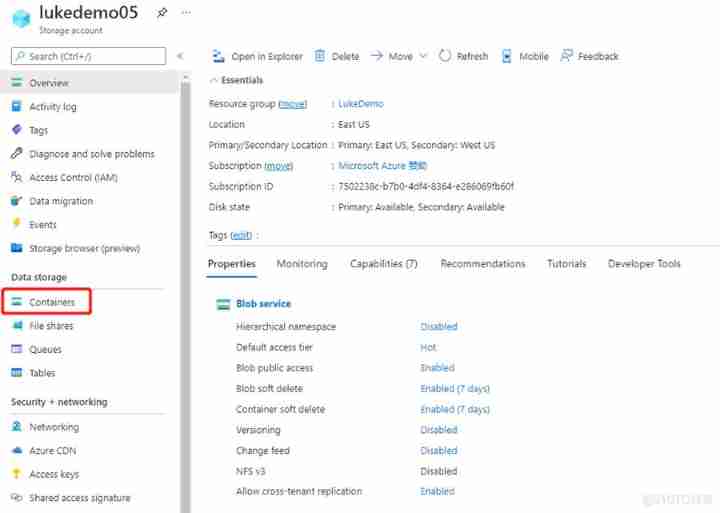
5. stay Container page , Click on create To create Container, Used to store Blob, As shown below :
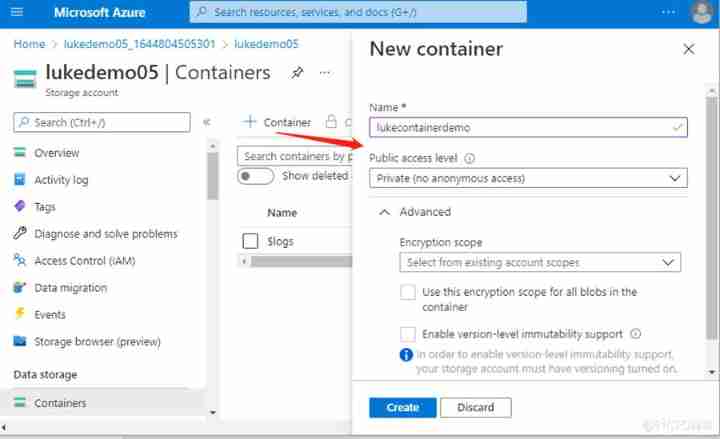
6. Next , We can click “Upload” Button to upload blob 了 , As shown below :
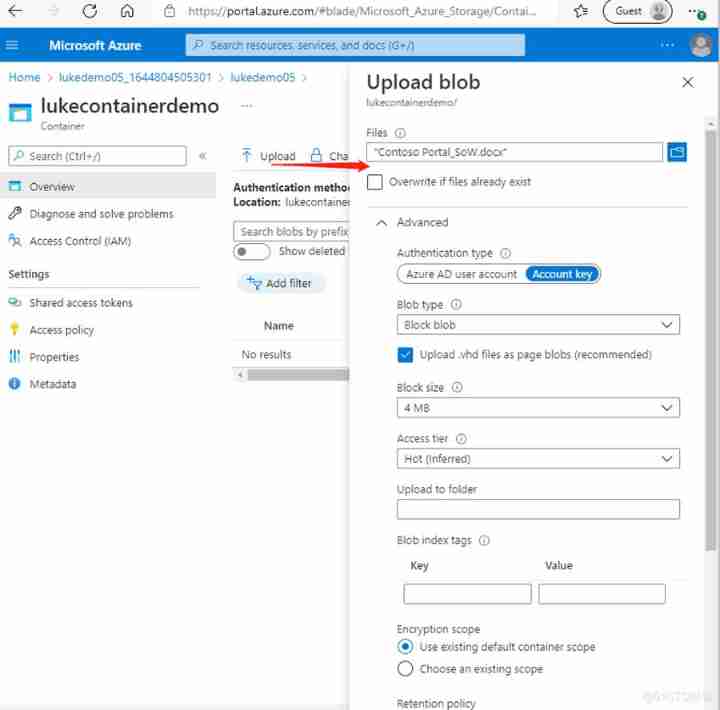
explain : If we want a third-party file call Azure Blob Storage To do data storage , Then what we need to provide is Storage Account Name+
Access Key+ Container Name+ End Point.
Access key The acquisition method is as follows :
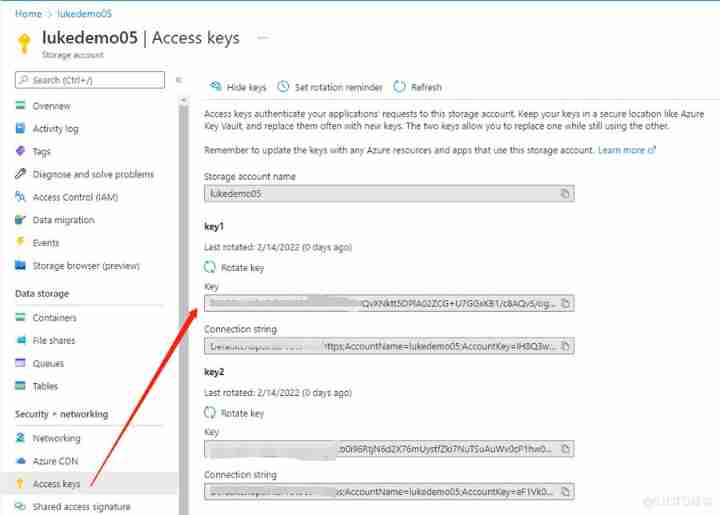
EndPoint Access method , It only needs Blob Service Of Endpoint, As shown below :
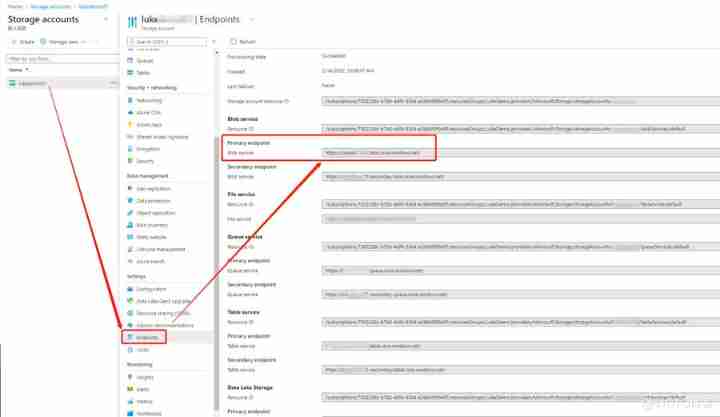
If you are using , Encounter other questions , Welcome to discuss offline at any time .
边栏推荐
- AI should take code agriculture? Deepmind offers a programming version of "Alpha dog" alphacode that surpasses nearly half of programmers!
- Iptables cause heartbeat brain fissure
- 2018 meisai modeling summary +latex standard meisai template sharing
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 21
- 8.8.1-PointersOnC-20220214
- JD home programmers delete databases and run away. Talk about binlog, the killer of MySQL data backup
- The latest idea activation cracking tutorial, idea permanent activation code, the strongest in history
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 5
- os. Path built-in module
- 'using an alias column in the where clause in PostgreSQL' - using an alias column in the where clause in PostgreSQL
猜你喜欢

Here, the DDS tutorial you want | first experience of fastdds - source code compilation & Installation & Testing
Detailed array expansion analysis --- take you step by step analysis
Reptile learning winter vacation series (2)
![[the way of programmer training] - 2 Perfect number calculation](/img/fd/4bb8560f601daddaa8895f20215be4.jpg)
[the way of programmer training] - 2 Perfect number calculation

Introduction of network security research direction of Shanghai Jiaotong University
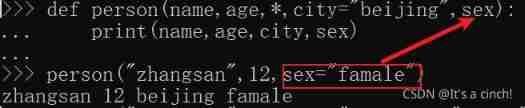
Function parameters (positional parameters, default value parameters, variable parameters, named keyword parameters, keyword parameters)
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24](/img/2e/b1f348ee6abaef24b439944acf36d8.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 5](/img/68/4f92ca7cbdb90a919711b86d401302.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 5

Decrypt the advantages of low code and unlock efficient application development
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12](/img/b1/926d9b3d7ce9c5104f3e81974eef07.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12
随机推荐
Properties and methods of OS Library
13、 C window form technology and basic controls (3)
Foreach (system.out:: println) usage
Summary of Shanghai Jiaotong University postgraduate entrance examination module -- cryptography
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 14
Practical dry goods: deploy mini version message queue based on redis6.0
Xiaobing · beauty appraisal
Method of setting default items in C # ComboBox control code
Clockwise rotation method of event arrangement -- PHP implementation
JD home programmers delete databases and run away. Talk about binlog, the killer of MySQL data backup
How to judge the advantages and disadvantages of low code products in the market?
Detailed array expansion analysis --- take you step by step analysis
LxC shared directory permission configuration
[Android reverse] function interception instance (③ refresh CPU cache | ④ process interception function | ⑤ return specific results)
Four sorts: bubble, select, insert, count
OSI model notes
Sys module
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
Data transmission in the network
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16