当前位置:网站首页>Yyds dry goods inventory kubernetes management business configuration methods? (08)
Yyds dry goods inventory kubernetes management business configuration methods? (08)
2022-07-05 01:04:00 【wzlinux】
Learn from the previous chapters , We're right Kubernetes Medium Pod And some business loads . You can use the examples provided in the course , Try to practice in the cluster by yourself .
In use , We often need to be aware of Pod Do some configuration management , For example, how to use parameter configuration files , How to save and transfer sensitive data , wait . Some people might think , Why not put these configurations ( Not limited to parameters 、 The configuration file 、 Key, etc ) Package it into the image ? At first glance to , It seems a little feasible , But that's how it works “ Indifference to ” Too much .
- Some unchanged configurations can be packaged into the image , What about the variable configuration ?
- Information leakage , It is easy to cause security risks , Especially some sensitive information , such as password、 Secret key, etc .
- After each configuration update , All need to be repackaged , Upgrade apps . Too many mirrored versions , It also brings a great burden to image management and image center storage .
- Customization is too serious , Poor scalability , And it is not easy to reuse .
So a best practice here is to decouple the configuration information from the container image , With “ The same should change ”. stay Kubernetes in , Generally speaking, there are ConfigMap and Secret Two kinds of objects , It can be used for configuration management .
ConfigMap
First of all, let's talk about ConfigMap This object , It is mainly used to save some non sensitive data , Can be used as an environment variable 、 Command line parameters or mount to the storage volume .

ConfigMap Store information through key value pairs , It's a namespace Level of resources . stay kubectl When using , We can abbreviate it to cm.
Let's take a look at two ConfigMap Of API Definition :
so , We go through ConfigMap It can store simple key value pairs , It can also store multiple lines of text .
Now let's create these two ConfigMap:
establish ConfigMap, You can also pass kubectl create cm be based on Catalog 、 file perhaps Face value To create , Please refer to this for details Official documents .
Once created , We can view the created objects in the following ways .
Now let's see how to communicate with Pod Use in combination . In use , There are several areas that need special attention :
- Pod It has to be with ConfigMap In the same namespace below ;
- Creating Pod Before , Please make sure ConfigMap Already exist , otherwise Pod Error will be reported when creating .
In the example above , It almost covers ConfigMap Several usage scenarios of :
- Command line arguments ;
- environment variable , You can inject only some variables , It can also be fully injected ;
- Mount the file , It can be a single file , It can also be all key value pairs , Use each key value as the file name .
So let's create :
Once created , We exec Look into the container :
You can see , Environment variables have been injected correctly , The corresponding files and directories are also mounted .
on top ls -alh /config/ after , We see that there are soft links in the mounted files , All point to ..data A file in a directory . The benefits of doing this , yes kubelet It will regularly check the attached ConfigMap Is it the latest , If it's updated , Is to create a new folder to store the latest content , And synchronously modify ..data Soft link to .
Generally, we only save some non sensitive data to ConfigMap in , Sensitive data should be saved to Secret It's in .
Secret
We can use Secret To save some sensitive data information , Like passwords 、 secret key 、token etc. . In use , Follow ConfigMap The usage is basically the same , Can be used as environment variables or file mount .
Kubernetes It also has some built-in Secret, It is mainly used to save access APIServer Of service account token, Let's talk about it later in the permissions section , Let's skip .
besides , It can also be used to save the identity information of the private image center , such kubelet You can pull the image .
notes : If you're using Docker, You can also run on the target machine in advance
docker login yourprivateregistry.comTo save your valid login information .Docker Generally, the key of the private warehouse will be saved in$HOME/.docker/config.jsonIn file , Distribute the file to all nodes .
Let's see how to pass kubectl To create secret, From the command line help You can see kubectl Be able to create many types of Secret.
Let's create a Secret To save the identity information of accessing the private container warehouse :
Here we can see , created Secret The type is kubernetes.io/dockerconfigjson:
In order to prevent Secret The content in is leaked ,kubectl get and kubectl describe It will avoid directly displaying the content of the password . But we can get the complete Secret Object to further view its data :
Here we find .dockerconfigjson It's a piece of garbled code , We use it base64 Try decompression :
This actually passed with us docker login After ~/.docker/config.json It's the same in .
thus , We found that Secret and ConfigMap The biggest difference in data storage .Secret The saved data is through base64 Encrypted data .
We usually use another kind more widely Opaque Type of Secret:
Or we can use the following equivalent kubectl Command to create :
Or create objects through files , such as :
Sometimes for convenience , You can also use stringData, In this way, you can avoid using it manually in advance base64 To encrypt .
And now we have Pod Use in Secret:
Once created , Let's take a look at :
We can see the command in the log env Output , See environment variables username and password Has been injected correctly . Similarly , We can also put Secret As Volume Mount to Pod Inside .
Last
ConfigMap and Secret yes Kubernetes Common objects for saving configuration data , You can choose the right object to store data according to your needs . adopt Volume How to mount to Pod Internal ,kubelet Will be updated regularly . But inject into the container through environment variables , So you can't feel ConfigMap or Secret Content update for .
How to make Pod The business inside is aware of ConfigMap or Secret The change of , It is still a problem to be solved . But we still have some Workaround Of .
- If the business supports reload Configuration , such as
nginx -s reload, Can pass inotify Aware of file updates , Or directly and regularly reload( We can cooperate here readinessProbe Use it together ). - If our business does not have this ability , Considering the idea of immutable infrastructure , Can we use rolling upgrade ? you 're right , This is a very good way . There is currently an open source tool Reloader, It is in this way , adopt watch ConfigMap and Secret, Once the object is found to be updated , It will automatically trigger right Deployment or StatefulSet Wait for workload objects to roll up . Specific usage , Refer to the documentation of the project .
For this question , In fact, the community has been discussing better solutions , We'll see .
Welcome to scan the code to pay attention to , For more information

边栏推荐
- Ruby tutorial
- 【C】 (written examination questions) pointer and array, pointer
- Chia Tai International Futures: what is the master account and how to open it?
- The performance of major mainstream programming languages is PK, and the results are unexpected
- Discrete mathematics: Main Normal Form (main disjunctive normal form, main conjunctive normal form)
- What you learned in the eleventh week
- NPM install error forced installation
- Reasons and solutions of redis cache penetration and avalanche
- Maximum number of "balloons"
- Les phénomènes de « salaire inversé » et de « remplacement des diplômés » indiquent que l'industrie des tests a...
猜你喜欢
资深测试/开发程序员写下无bug?资历(枷锁)不要惧怕错误......

Oracle case: SMON rollback exception causes instance crash
![[wave modeling 1] theoretical analysis and MATLAB simulation of wave modeling](/img/c4/46663f64b97e7b25d7222de7025f59.png)
[wave modeling 1] theoretical analysis and MATLAB simulation of wave modeling

Arbitrum:二维费用
【纯音听力测试】基于MATLAB的纯音听力测试系统

Innovation leads the direction. Huawei Smart Life launches new products in the whole scene
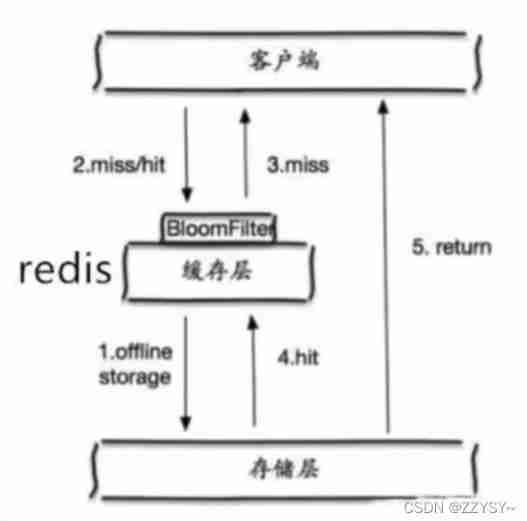
Reasons and solutions of redis cache penetration and avalanche
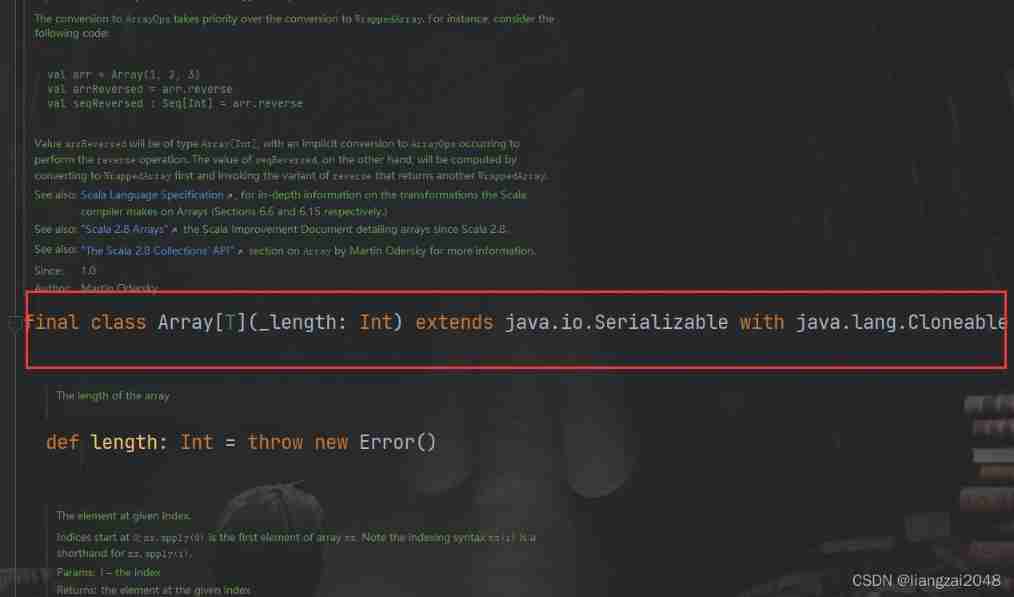
4. Scala writes HelloWorld in idea, in-depth analysis of accompanying objects, and association of source packages
![Grabbing and sorting out external articles -- status bar [4]](/img/88/8267ab92177788ac17ab665a90b781.png)
Grabbing and sorting out external articles -- status bar [4]
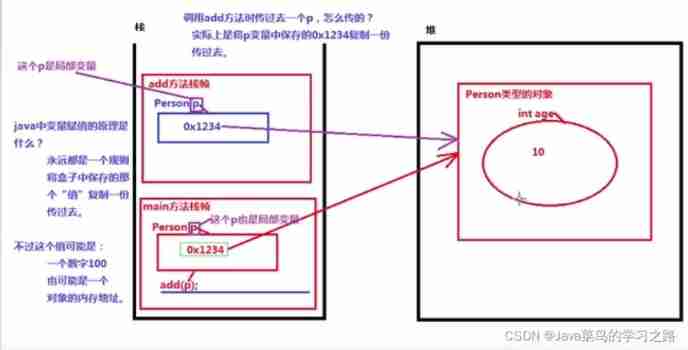
Parameter passing mechanism of member methods
随机推荐
潘多拉 IOT 开发板学习(RT-Thread)—— 实验4 蜂鸣器+马达实验【按键外部中断】(学习笔记)
Applet live + e-commerce, if you want to be a new retail e-commerce, use it!
Leetcode70 (Advanced), 322
“薪资倒挂”、“毕业生平替” 这些现象说明测试行业已经...
Daily question brushing record (13)
SAP UI5 应用开发教程之一百零六 - 如何提高 SAP UI5 应用路由 url 的可读性试读版
Summary of the function and usage of const, volatile and restrict
[Yocto RM]11 - Features
Hand drawn video website
如果消费互联网比喻成「湖泊」的话,产业互联网则是广阔的「海洋」
Discrete mathematics: reasoning rules
Complete knapsack problem (template)
107. SAP UI5 OverflowToolbar 容器控件以及 resize 事件处理的一些细节介绍
Basic operation of database and table ----- phased test II
【海浪建模2】三维海浪建模以及海浪发电机建模matlab仿真
那些一门心思研究自动化测试的人,最后都怎样了?
抓包整理外篇——————状态栏[ 四]
分布式BASE理论
Basic concept and usage of redis
[FPGA tutorial case 10] design and implementation of complex multiplier based on Verilog