当前位置:网站首页>Usage of ieda refactor
Usage of ieda refactor
2022-07-02 19:20:00 【thoughtCodes】
IEDA refactor Usage of
- Catalog
- summary
- Design thinking
- Analysis of implementation ideas
- 1.Refacot this
- 2.rename
- 3.rename file
- 4.change sinnature
- 5.Edit pro value
- 5.Type m
- 5.make static
- 6.convert to instance method
- 7.move class/member
- 8.copy class
- 9.safe delete
- 6.Extract
- inline super class
- Invert bolean
- find and repalce duliate:
- pull up member:
- pull down member:
- user inteface:
- inherit from replace
- remove middlman
- wrap method return value
- encapsulate Fields:
- replace temp with query
- replace constrct with factory
- replace constructor with build
- genirity
- migrate
- interliatelize
- migrate to anroidRx
- Sequence and method of use
- Expand to achieve
- Performance parameter test :
- References and recommended readings
Survive by day and develop by night.
talk is cheap, show me the code,make a better result.
Catalog

summary
I've always wanted to write this usage , I used it before , Only part of it is used , Now outline , When we write the corresponding code according to the business requirements , This is very important .
demand :
Design thinking
Analysis of implementation ideas
1.Refacot this
Select object , Right click to pop up the suggestion list , Select refactoring .
2.rename
This is simpler , Use naming conventions , Rename it .
3.rename file
Rename the currently selected file
4.change sinnature
Usually it's changing the method , Change method parameters .
5.Edit pro value
Change the attribute value , The directory object does not , May be pro Document has
5.Type m
Type related
5.make static
Action object , Directory does not , Method objects have , It should be to turn the method into static Of .
6.convert to instance method
Turn the method into static Of , and 5 What's the difference ?
7.move class/member
Mobile class directory structure
8.copy class
Will file copy To the specified directory , Local directory failed .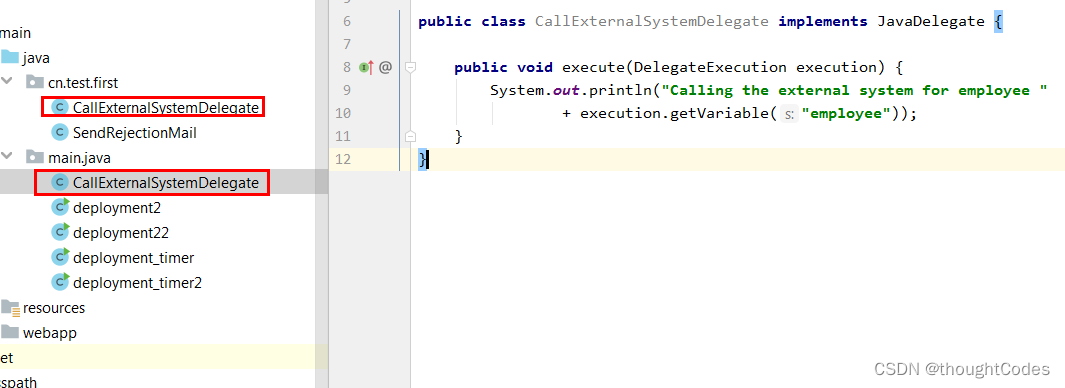
9.safe delete
This is simpler , Safe deletion , File to be deleted file does not exist .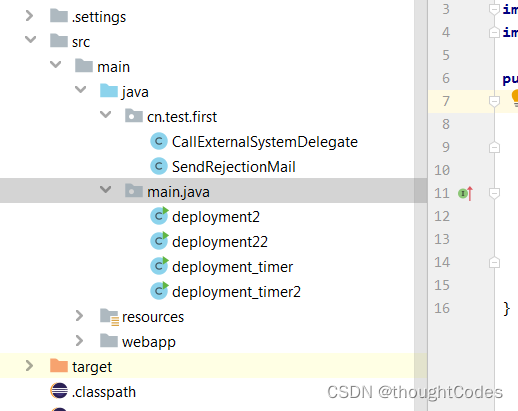
6.Extract
variable
Failed to select file at present , The selected expression should be :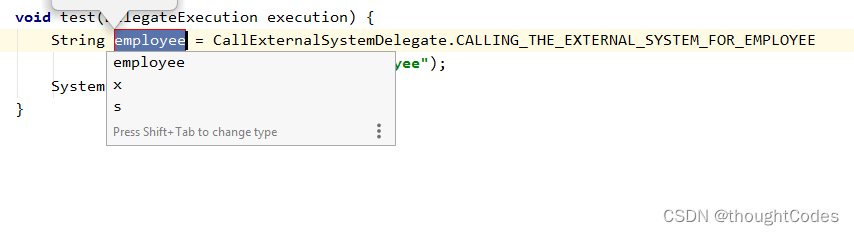
The extraction expression is constant :
constant
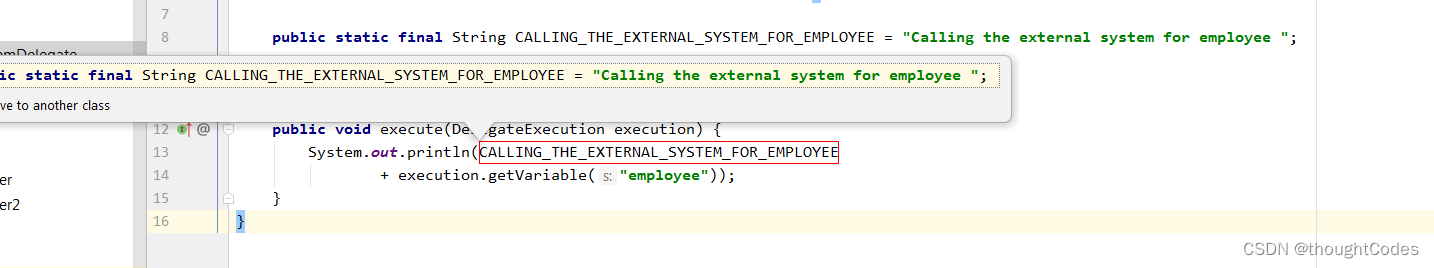
Filed
Select variable , Property name failed , Similarly, you choose an expression :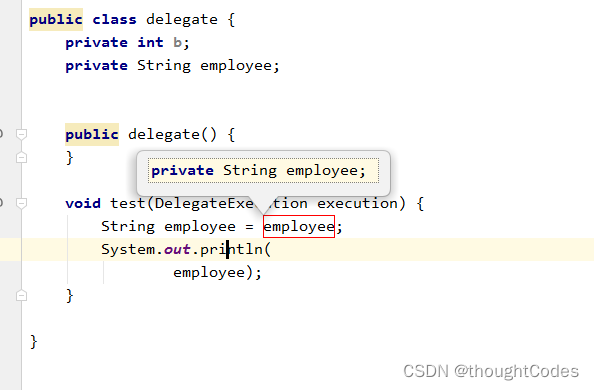
But notice this IEDA Logic is not automatically drawn in , Is to treat the expression as a member variable .
paraeter
Failed to select a single variable name or function list . What should be chosen is the expression :
Choose the former :
After refactoring :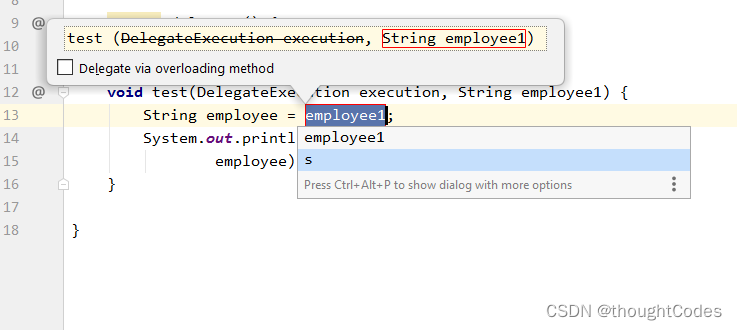
however IEDA There is no corresponding project extraction in logic .
object
Failed to select a single variable name or function list .
method:

Select the code line in the specific method , Extraction method :
Type parameter
Invalid selection method list .
Method object
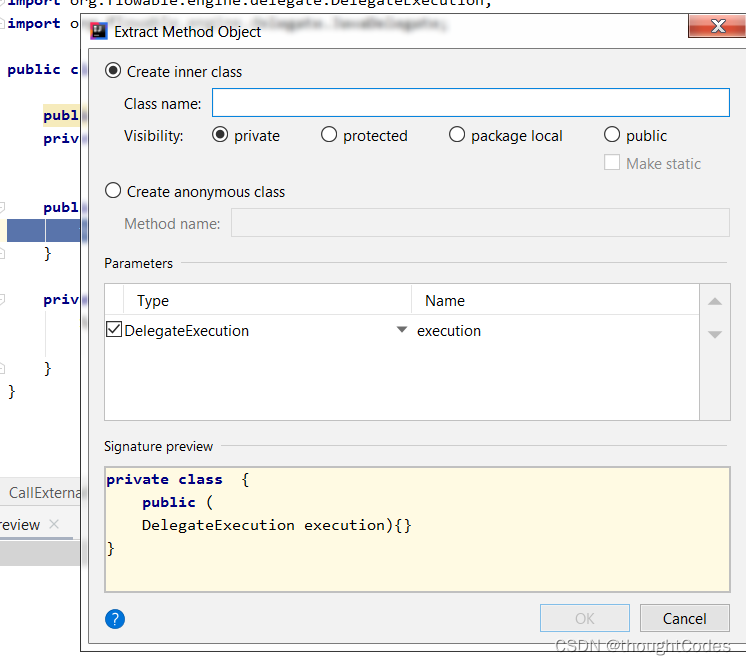
Turn the calling method into an internal class and an anonymous class :
delegate
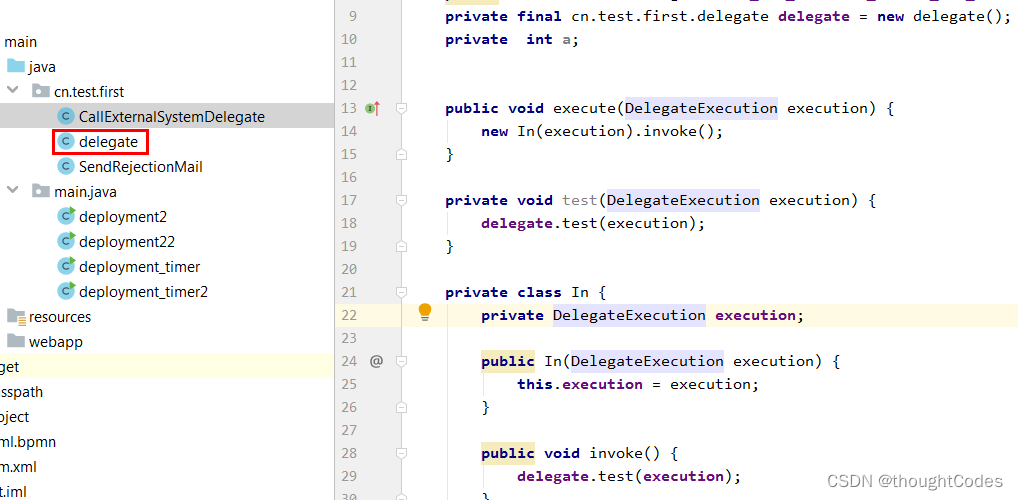
Usually it is to generate a new class , As a delegate . Called by the delegate object .
interface:

result :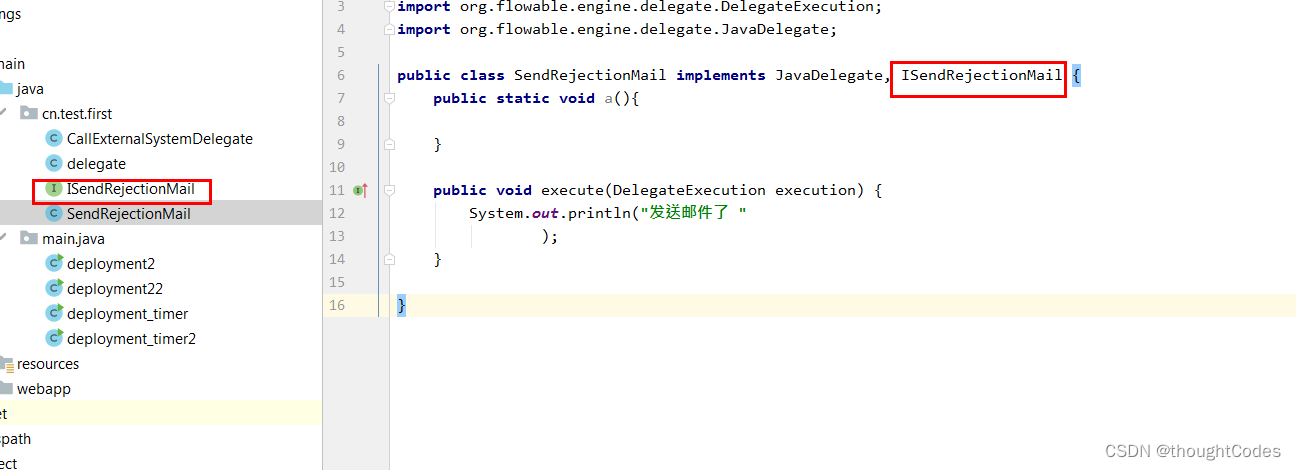
super class
First choose :
result :
Will extract int Attribute and add corresponding extends class :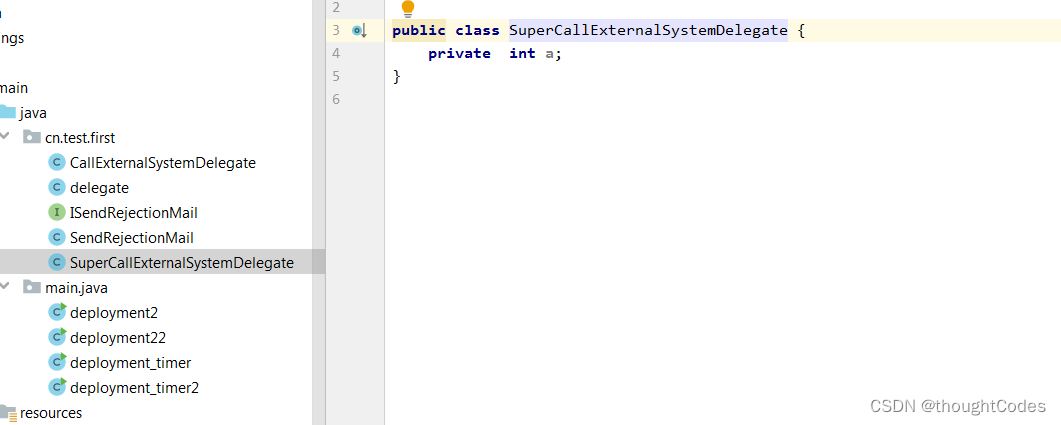
inline super class
Select parent class : After analysis and quotation :
result :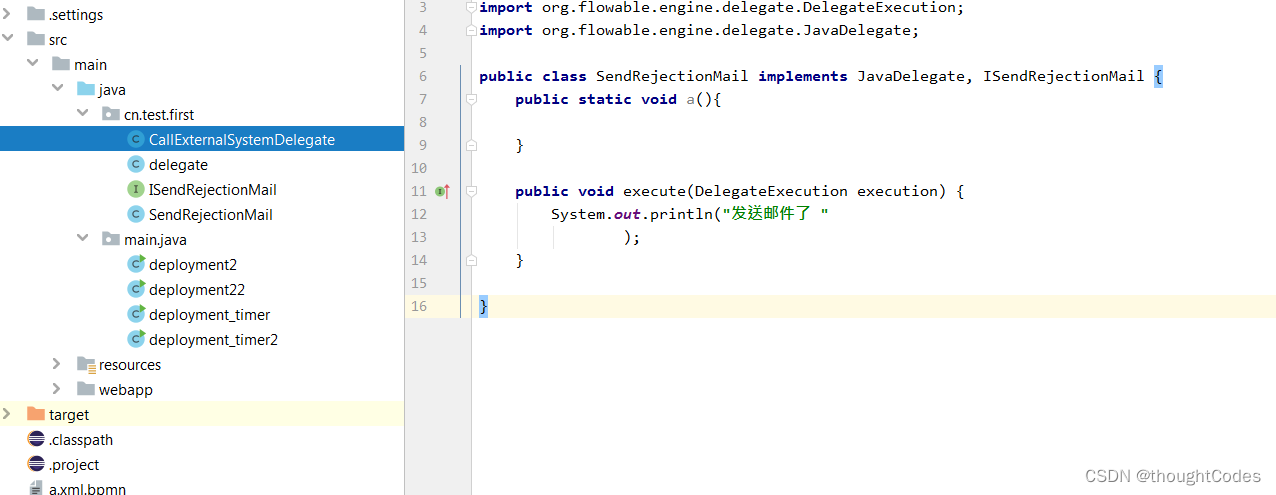
Invert bolean
I don't know yet
find and repalce duliate:

pull up member:
pull down member:
Select the corresponding parent class , extract
user inteface:
Choose the method to use , Analyze , Interfaces can be used instead of
inherit from replace

Generate a delegate class , An interface is implemented internally .
remove middlman
The service class has completely become “ A middleman ”, At this point, you should let the client call the entrusted class directly .
wrap method return value
Encapsulation method
encapsulate Fields:

replace temp with query
Replace temporary results with queries
replace constrct with factory
Replace the construction method with the factory method ,
Select the method line : 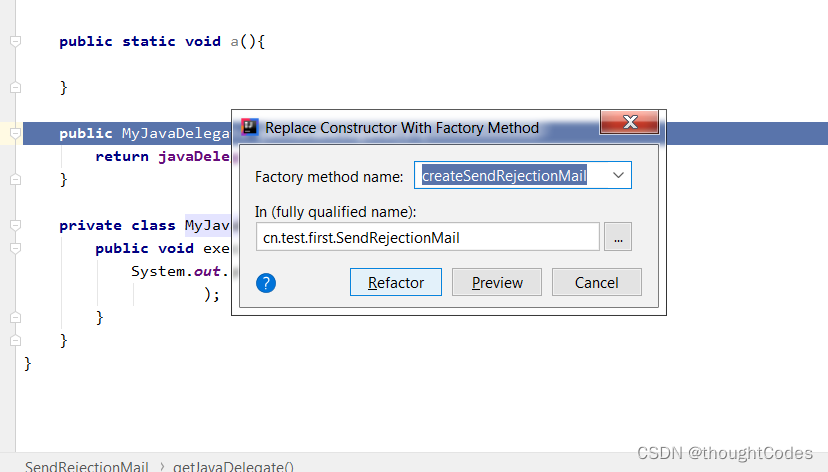
replace constructor with build
use builder Pattern construction method :
genirity
java The generics in , This information is scarce
migrate
transfer , Generally, it provides javaex,junit,swing Migration options :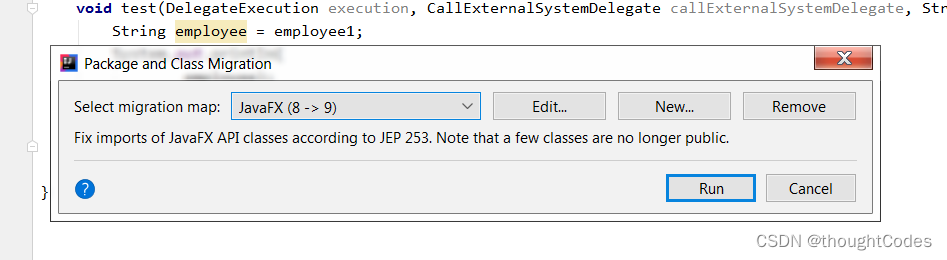
interliatelize
online
migrate to anroidRx
Migrate to the corresponding androidRx:
Starting from the basic objects, there are probably so many , The menus that appear for different objects are not the same .
Sequence and method of use
From the perspective of granularity , look down :
Mainly
1.varibale,constant,filed Wait for the operation
2.function Internal level , Mainly extracting parameters , Object etc. .
3. Choosing multiple lines is method, or method object ( As an anonymous class , Internal class processing )
In fact, it is also different from the extraction menu .
Then it's based on class File level refactoring :
For a single class :
1. Delete , Move , Delete etc.
2. A higher level : Rename, etc .
This part can have operating system management , It only provides another editing entry .
For many categories : From a design point of view : Usually 3 individual :
delagate,interface,superclass,
The first objects to choose are extends,impl Keywords, etc , This part can be realized
For a mature project , Actual letter extends It seems to use more .
For its relationship expansion .
Then there are some pattern Has applied best practices .
Such as builder,factorypattern. Will generate a builder File and call file .
Then there is class lib Level ,
does jar transfer ,class Generic :
That's right Java Development is basically enough ,
If there is, it is the file conversion between systems, such as :
Transfer to androidX file .
So far, the analysis is finished .
Expand to achieve
- Entry level implementation :
- Partial source code implementation .
- The source code to achieve
Theory provides the basis . Generally optimized to pattern It's about the floor .
Performance parameter test :
nothing
References and recommended readings
Welcome to , Dear brother , If it helps you , A little praise and a little attention !~
边栏推荐
- Emmet基础语法
- NPOI导出Excel2007
- Mysql高级篇学习总结6:索引的概念及理解、B+树产生过程详解、MyISAM与InnoDB的对比
- 新手必看,點擊兩個按鈕切換至不同的內容
- C文件输入操作
- 论文导读 | 关于将预训练语言模型作为知识库的分析与批评
- R language ggplot2 visual Facet: gganimate package is based on Transition_ Time function to create dynamic scatter animation (GIF)
- Date tool class (updated from time to time)
- 论文导读 | 机器学习在数据库基数估计中的应用
- 新手必看,点击两个按钮切换至不同的内容
猜你喜欢

Imitation Jingdong magnifying glass effect (pink teacher version)

How can retail enterprises open the second growth curve under the full link digital transformation

Yunna | why use the fixed asset management system and how to enable it

机器学习笔记 - 时间序列预测研究:法国香槟的月销量
高级性能测试系列《24. 通过jdbc执行sql脚本》
![[100 cases of JVM tuning practice] 01 - introduction of JVM and program counter](/img/c4/3bba96fda92328704c2ddd929dcdf6.png)
[100 cases of JVM tuning practice] 01 - introduction of JVM and program counter

Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5

Novice must see, click two buttons to switch to different content
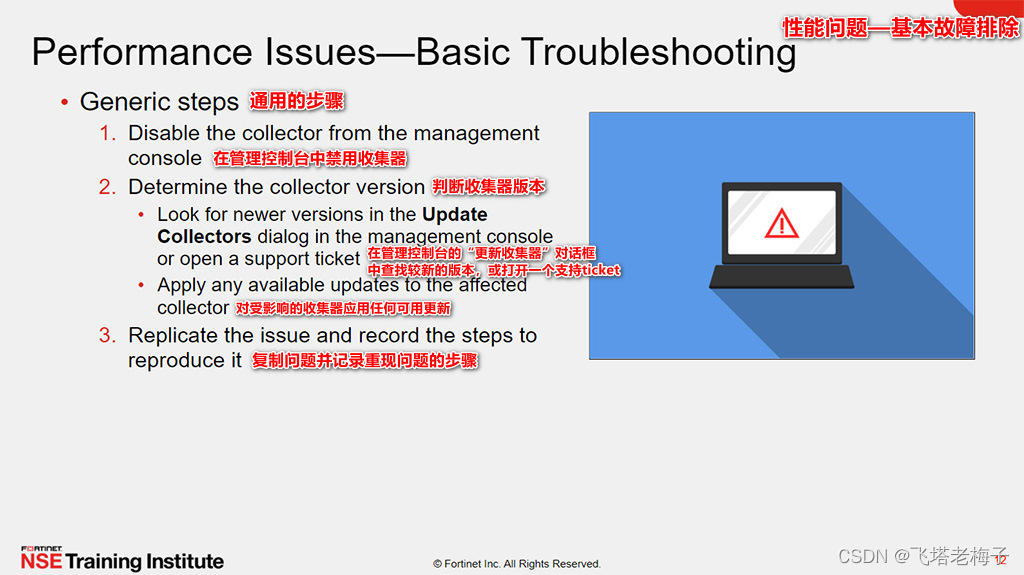
教程篇(5.0) 10. 故障排除 * FortiEDR * Fortinet 網絡安全專家 NSE 5
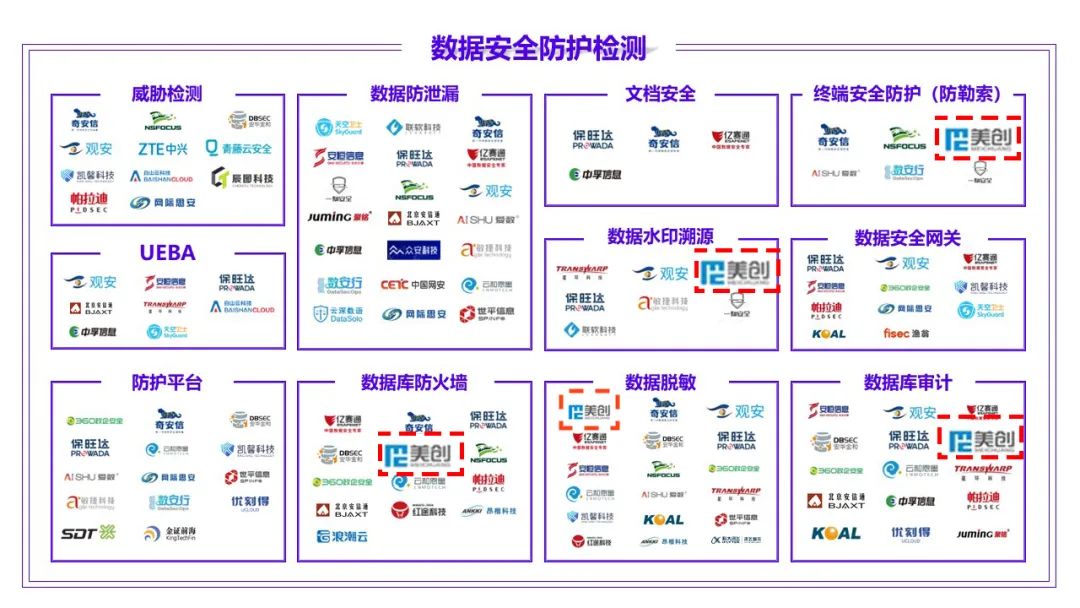
中国信通院《数据安全产品与服务图谱》,美创科技实现四大板块全覆盖
随机推荐
Kubernetes three open interfaces first sight
Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5
mybatiesHelperPro工具必须的可以生成到对应项目文件夹下
[test development] takes you to know what software testing is
R language dplyr package Na_ The if function converts the control in the vector value into the missing value Na, and converts the specified content into the missing value Na according to the mapping r
Excel finds the same value in a column, deletes the row or replaces it with a blank value
机器学习笔记 - 时间序列预测研究:法国香槟的月销量
R language dplyr package filter function filters dataframe data. If the name of the data column (variable) to be filtered contains quotation marks, you need to use!! SYM syntax processing, otherwise n
Crypto usage in nodejs
消息队列消息丢失和消息重复发送的处理策略
Introduction to the paper | analysis and criticism of using the pre training language model as a knowledge base
R语言ggplot2可视化分面图(facet):gganimate包基于transition_time函数创建动态散点图动画(gif)
PHP非对称加密方法私钥及公钥加密解密的方法
【JVM调优实战100例】02——虚拟机栈与本地方法栈调优五例
ORA-01455: converting column overflows integer datatype
Golang concurrent programming goroutine, channel, sync
ORA-01455: converting column overflows integer datatype
How performance testing creates business value
Digital scroll strip animation
日期工具类(不定时更新)