summary
File upload vulnerability occurs in applications with upload function , If the application has no control over users' uploaded files or has defects , Attackers can take advantage of the flaws in the application upload function , Upload the Trojan 、 Virus and other harmful files to the server , Control server .
Causes and hazards of loopholes
The main reason for file upload vulnerability is : There is upload function in the application , However, the uploaded files have not been strictly verified for legitimacy or the verification function has defects , As a result, Trojan files can be uploaded to the server . File upload vulnerability is extremely harmful because malicious code can be directly uploaded to the server , It may cause the web page of the server to be tampered 、 The website was suspended 、 The server is remotely controlled 、 Being installed with a back door and other serious consequences .
Here are some ways to verify and bypass file uploading
1. Local validation ( Front end validation )
front end JS Filtering bypasses the upload vulnerability because the application passes through the front end JS Code validation , Instead of verification at the back end of the program , In this way, you can modify the front end JS Code way to bypass upload filtering , Upload the Trojan .
So how to judge whether it is front-end verification ? Personally, I think we can see whether we can get the data packets when uploading and capturing packets , Whether there is data flow , Or you can see whether the page of the uploaded image will display the address of the uploaded image
Bypass : Delete the filter code , Modify or disable Javascript
2. Back end verification and bypass
File upload common verification : Suffix name ( Direct verification ), file , The file header ( Indirect verification )
【 Help safe learning , All resources are obtained from one by one 】
① Network Security Learning Route
②20 Penetration test ebook
③ Safe attack and defense 357 Page notes
④50 A security attack and defense interview guide
⑤ Safety red team penetration Kit
⑥ information gathering 80 Search syntax
⑦100 Three actual cases of vulnerability
⑧ Internal video resources of the safety factory
⑨ Calendar year CTF Analysis of the flag race
2.1 Suffix name
2.1.1 The blacklist ( Specify the script format suffix that is not allowed to upload )
File name filtering bypasses the vulnerability mainly because the type of file upload is judged through the blacklist , And there is no complete filtering , Cause the attacker to upload files other than the blacklist type .
Blacklist judgment method : Upload files , The system prompts that uploading is not allowed xxx Format file
Bypass : Use other formats (php5,Phtml,php3) Or file case , At the same time, you can also add some interference symbols to bypass
2.1.2 .htaccess( Pseudo static Protocol )- Rewrite parsing
(Apache Only then has and starts the pseudo static module )
.htaccess File upload is the use of .htaccess Files can be Web Functions of server configuration , Realize to jpg、png Files with suffixes such as PHP The process of file parsing .
.htaccess file ( Distributed profile ) Provides a way to make configuration changes based on each directory , Files containing one or more configuration directives are placed in a specific document directory , And the instructions in the file apply to the directory and all its subdirectories ..htaccess yes Web A configuration file for the server , Can pass .htaccess File implementation Web How to parse the definition file in the server 、 Redirection and other configurations .
Bypass method : First upload 1.htaccess file .2. Then upload the picture horse .
2.1.3 Space around
Bypass method : Add a space after the file suffix in the packet to bypass
2.14 . Bypass
Bypass method : Similar to the space bypass method , Add a... After the file suffix in the data package . To achieve bypass
2.1.5 ::$data Bypass
This is a windows A unique protocol , stay window If the file name +"::
DATA After the data as a file stream processing , The suffix will not be detected , And keep it ::$DATA Previous file name , His goal is not to check the suffix
2.1.6 Cyclic filtration
Bypass : The code will php Replace with empty as :a.pphphp Will become ->a.
2.1.7 White list : Specify the format suffix that can be uploaded ( More secure )
%00 truncation 、0x00 truncation ( The principle based on address , Truncate the data behind the file )00 Truncation bypass can only bypass front-end authentication .
The main reason for truncation is the existence %00 This character ,PHP<5.3.4 when , Will treat it as a Terminator , This causes the following data to be directly ignored , Cause truncation , When uploading, if the path of the uploaded file is controllable , Can pass 00 truncation , Upload the Trojan horse .
Bypass method (path%00 truncation ):
1. take test Change it to test.php%00aaa,1.php Change it to 1.jpg In this way, you can verify the function
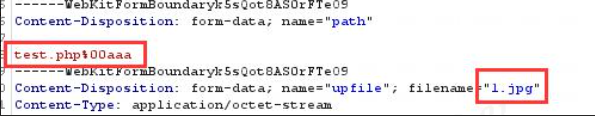
2.test.php%00aaa Medium %00 Conduct URL code , Choose %00 choice 【Convertselection】 command , choice 【URL】 command , choice 【URL-decode】 Command encoding
3. Document type verification
3.1 Header detection : Header content information ( Such as gif89a)
Different files have specific header formats , The developer checks the file type by checking the header of the uploaded file , But this detection method can also be bypassed , Just add the corresponding file header to the header of the Trojan file , In this way, the detection can be bypassed without affecting the normal operation of Trojan files .
Common file headers are as follows :
JPEG 0xFFD8FF
PNG0 x89504E470D0A1A0A
GIF 47 49 4638 39 61(GIF89a)
Bypass method :
1. Change the header information to cheat , If you add the file header of the picture file to the header file of the Trojan horse, you can bypass the detection .
GIF89a
<?php echo`$_REQUEST[cmd]`;
?>
2. Make pictures of horses 1. Insert a sentence directly into the picture , Upload .——— Using the principle of File Inclusion 2. Use cmd The command will send a normal picture 1.jpg With a Trojan horse containing one sentence a.txt file , Synthesize a new test.php Trojan files
cmd command : copy 1.jpg/b+a.txt test.php
3.2 Content-Type testing
Content-Type Used to define the type of network files and the encoding of web pages , Used to tell the file receiver what form it will take 、 What encoding reads this file . Different files will correspond to different Content-Type, such as jpg Of documents Content-Type by image/jpeg,php Of documents Content-Type by application/octet-stream.Content-Type The header of the request is in the packet , Developers will connect Content-Type Judge whether the file is allowed to be uploaded according to the type of ,
Bypass :Content-Type The type of can be tampered with by capturing packets , In this way, the data packet can be modified by capturing the packet Content-Type To bypass Content-Type Judge .MIME: You can guess the file suffix by judging the type , Use the bag capturing tool to Content-Type To tamper with , If changed to image/pjpeg、image/jpeg、image/gif、image/png One of four can bypass the filter
4. Content and others
4.1 Logical security : Conditional competition ( Equivalent to system occupation )
Definition : Race condition refers to that multiple threads access the same shared code at the same time without lock operation or synchronous operation 、 Variable 、 Documents, etc. , The result of running depends on the order in which different threads access data . First upload the file to the server , The server chooses to save and delete pictures according to rules , The flaw is that the file is not checked for legitimacy before being saved to the server , Although the file is checked after saving , But through competitive conditions loopholes , By uploading a Trojan horse with the function of writing files , Before deleting the Trojan horse, access the uploaded Trojan horse , You can write a new Trojan .
Bypass : Upload the file to the server , We will continue to access the file path , Because of the competition of conditions , It will be uploaded Webshell Purpose , Vulnerability exploitation is to send requests by constantly uploading content , Such access will generate new Trojan files , Then send another request to keep accessing this file , If the competitive condition vulnerability is successfully exploited, a new Trojan horse will be generated .
4.2 Catalog name
Bypass : By adding /. Suffixes allow the server to recognize files as folders , Achieve the purpose of uploading , Such as -x.php/.
5. Other loopholes
Script function vulnerability -cve
CVE-2017-12615
CVE-2015-5254
CVE-2019-2618
...... There are tutorials on the use of these vulnerabilities online , If you are interested, you can check the information
6. Middleware parsing vulnerability
6.1 IIS 6.0+ Parsing vulnerabilities
Analyze vulnerabilities and quickly judge ,/.php See if there is any garbled code , Some exist , No, there is no
6.1.1 Execute as a folder
Normal file name :
image/aa.jpg
Bypass :
image.asp/aa.jpg aa.jpg
Will be treated as asp analysis
6.1.2 Execute as a file
Normal file name :image.jpg Bypass :
image.asp;.jpg or xxx.asp;xxx.jpg
This file will be treated as asp perform
asp It can be changed to php If it's changed php, Then it can be regarded as php perform
7.WAF Bypass
To get around WAF, We need to know which parameters can be modified , Such as Content-Disposition: Generally, it can be modified name: Form parameter values , Do not modify filename: file name , You can modify Content-Type( File type ): file MIME, Change as appropriate waf The core of bypassing is to constantly modify the test after the parameter name that can be modified , Try to bypass .
Common bypassing methods :
7.1 Data overflow ( Garbage data filling )
utilize WAF Upper detection limit , Add a lot of junk data , Let it not match , Similar to overflow vulnerability , Generally, interference data can be added after the uploaded parameters , Remember to add between garbage data and parameters ;, Otherwise, the packet will report an error
7.2 Symbolic variation ('";)
Exploit program development vulnerabilities , Replace the symbols in the upload parameters in the data package , add to 、 Delete , Achieve the purpose of uploading . Ultimate Reality
x.jpg;.php
The semicolon represents the end of a data
7.3 Data truncation (%00; Line break )
File suffix followed by %00( Space ) truncation ,x.php%00.jpg Line break ( Similar to the program \n) It is similar to data block transmission , Such as x.php Packets actually identify
x.\np\nh\np
7.4 Duplicate data
Equivalent to recursion in function loop , The principle of writing parameters many times in a packet is also very similar to garbage data
8. defense
1. Deployment pagoda ,waf And other safety products
2. Strictly verify the uploaded content for many times
3. Check the integrity of the file content
原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/187/202207061532510581.html