当前位置:网站首页>Web security -- Logical ultra vires
Web security -- Logical ultra vires
2022-07-02 08:27:00 【Defeat of Fujiwara Qianhua】
Attack access control
From the technical point of view, logical ultra vires means that there are defects in access control . The following attacks on access control are logical ultra vires .
Request from client ,Web The application should recognize the following two points :
- Verify user identity
- The confirmation request sequence is proposed by the user
Based on these two points ,web The server decides whether to allow a request to perform a specific operation or access the resources it requests . Access control is an important defense mechanism for applications , Because it is responsible for making these key decisions . If there are defects in visiting Confucius , Attackers can often break through the entire application , Control its management functions and access sensitive data belonging to other users .
Concept
Access control vulnerability : The application allows an attacker to perform an operation that the attacker is not qualified to perform
The differences between various vulnerabilities can actually be attributed to the differences in the way these core vulnerabilities are expressed , And the difference between the skills they need to use .
classification
Access control can be divided into three categories :
- Vertical access control
- Horizontal access control
- Context sensitive access control
Vertical access control allows different users to access different functions of the application . For example, you are CSDN Check out my article , If you don't like it , You can't take my article off the shelf , This is the authority of the administrator . In this case , Applications define ordinary users and administrators through this control
Horizontal access control allows users to access a group of the same type 、 Extremely extensive resources . You are a CSDN user , I am also CSDN user ,, What we can do on this is the same .
Context sensitive access control ensures that it is based on the current state of the application , Restrict user access to only allowed content . For example, in a certain process , Users need to complete multiple stages of operation , Context sensitive access control can prevent users from accessing these stages in a specified order .
If the user can access the functions or resources he does not have permission to access , It means that there are defects in access control , That is, there is a logical ultra vires loophole . There are mainly three types of attacks targeting access control , They correspond to three kinds of access control respectively :
- Vertical permission promotion : A user can perform a function , But the role assigned to him does not have this permission . That is, ordinary users perform the actions of administrators
- Increase the level of authority : A user can view or modify resources of the same level that he is not qualified to view or modify . If you can edit my article
- Business logic loopholes : Users can take advantage of vulnerabilities in the application state machine to gain access to key resources . For example, users can avoid the payment steps in the shopping settlement sequence
actual combat
pikachu The level is beyond authority
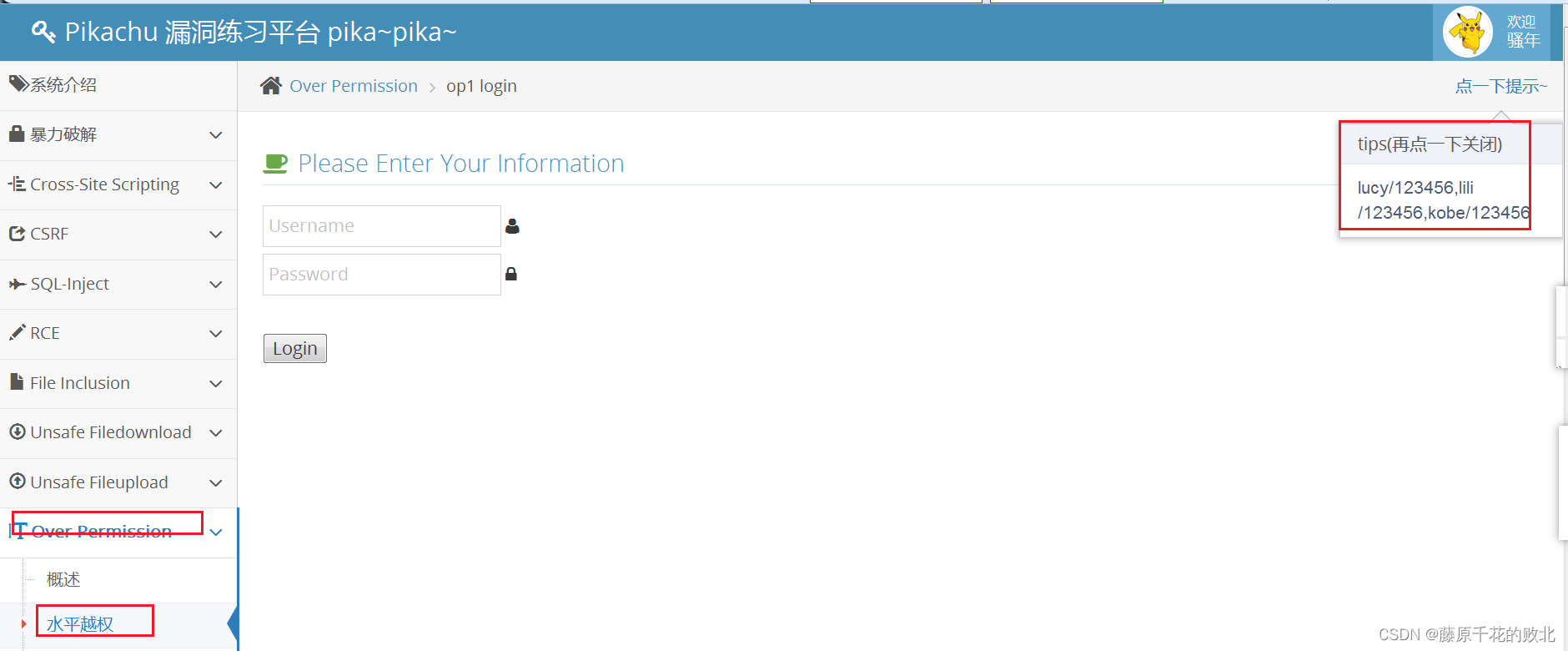
The level is beyond authority , That is to use my account , Check the learning resources of your account . See Tips , A user kobe、lucy.
- Sign in kobe account number

- As shown in the figure above , use burpsuite Grab the bag “ Check the information ”

- take kobe Change it to lucy, return lucy Information about

Reference resources
Almost copy 《 The classic of hacker attack and Defense Technology Web Actual combat 》
边栏推荐
- 樂理基礎(簡述)
- Deep understanding of JVM
- Rotating linked list (illustration)
- Matlab-其它
- Opencv's experience of confusing X and Y coordinates
- Comparison between setTimeout and requestanimationframe (page refresh)
- OpenCV关于x,y坐标容易混淆的心得
- Static library and dynamic library
- 用数字 5,5,5,1 ,进行四则运算,每个数字当且仅当用一次,要求运算结果值为 24
- Implementation of bidirectional linked list (simple difference, connection and implementation between bidirectional linked list and unidirectional linked list)
猜你喜欢

Jumping | Blue Bridge Cup
Carla-ue4editor import Roadrunner map file (nanny level tutorial)
双向链表的实现(双向链表与单向链表的简单区别联系和实现)
Sqlyog remote connection to MySQL database under centos7 system

c语言自定义类型——结构体,位段(匿名结构体,结构体的自引用,结构体的内存对齐)
Use the kaggle training model and download your own training model

乐理基础(简述)

web安全--逻辑越权
On the back door of deep learning model

ARP及ARP欺骗
随机推荐
Simple implementation scheme of transcoding and streaming (I)
My VIM profile
2022 Heilongjiang latest food safety administrator simulation exam questions and answers
STM32疑难杂症之ST-LINK Connection error INVALID ROM TABLE
How to apply for a secondary domain name?
Use C language to receive JSON strings
乐理基础(简述)
Intelligent manufacturing solutions digital twin smart factory
Global and Chinese markets for magnetic resonance imaging (MRI) transmission 2022-2028: Research Report on technology, participants, trends, market size and share
install. IMG production method
STL quick reference manual
Get the width and height of the screen in real time (adaptive)
Global and Chinese market of medicine cabinet 2022-2028: Research Report on technology, participants, trends, market size and share
使用Matplotlib绘制图表初步
Implementation of bidirectional linked list (simple difference, connection and implementation between bidirectional linked list and unidirectional linked list)
Chinese garbled code under vscade
sqli-labs第12关
Rotating linked list (illustration)
Data reverse attack under federated learning -- gradinversion
Introduction to parameters of CarSim pavement 3D shape file