当前位置:网站首页>RE1 attack and defense world reverse
RE1 attack and defense world reverse
2022-07-07 23:18:00 【Day-3】

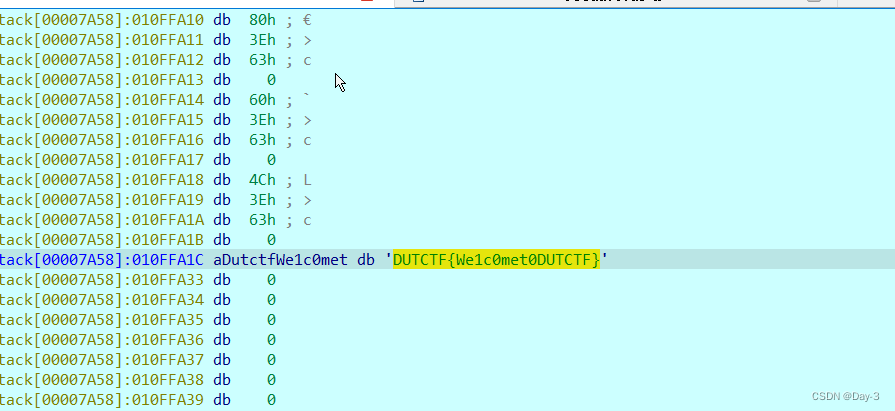
This question has no shell , Throw in IDA Check the source code , The source code is confusing , After modification, it is shown as follows :
int __cdecl main(int argc, const char **argv, const char **envp)
{
int v3; // eax
char v5[32]; // [esp+0h] [ebp-44h] BYREF
char v6[32]; // [esp+20h] [ebp-24h] BYREF
*(__m128i *)v5 = _mm_loadu_si128((const __m128i *)&xmmword_633E34);
*(_DWORD *)&v5[24] = 0;
strcpy(&v5[16], "DUTCTF}");
*(_WORD *)&v5[28] = 0;
printf(" Welcome to DUTCTF yo \n");
printf(&byte_633E60);
printf(" Input flag Well :");
scanf("%s", v6);
v3 = strcmp(v5, v6);
if ( v3 )
v3 = v3 < 0 ? -1 : 1;
if ( v3 )
printf("flag Not quite right , Try again , Come on \n");
else
printf("flag get√\n");
system("pause");
return 0;
}
At this time, the code logic is relatively clear , It is to compare the content we input with the content it generates , The same is deemed to be submitted accurately flag, At this time, our task is to check v5 The content in , So we do dynamic debugging , It's easy to find flag.
边栏推荐
- Handling file exceptions
- V20变频器手自动切换(就地远程切换)的具体方法示例
- 14、 Two methods of database export and import
- 网络安全-对操作系统进行信息查询
- 经纬度PLT文件格式说明
- Wechat forum exchange applet system graduation design completion (1) development outline
- Kubernetes' simplified data storage storageclass (creation, deletion and initial use)
- 海内外技术人们“看”音视频技术的未来
- Archlinux install MySQL
- Matlab 信号处理【问答随笔·2】
猜你喜欢
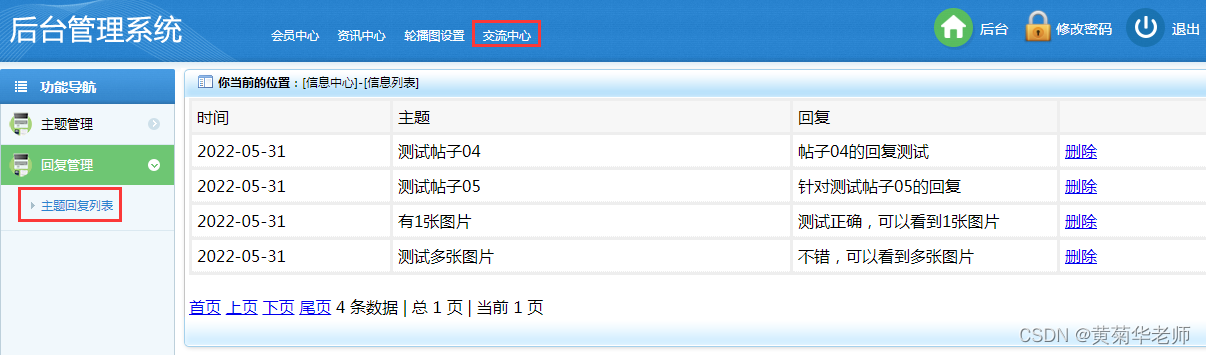
Wechat forum exchange applet system graduation design (3) background function

微信论坛交流小程序系统毕业设计毕设(3)后台功能
Cases of agile innovation and transformation of consumer goods enterprises
Innovation today | five key elements for enterprises to promote innovation
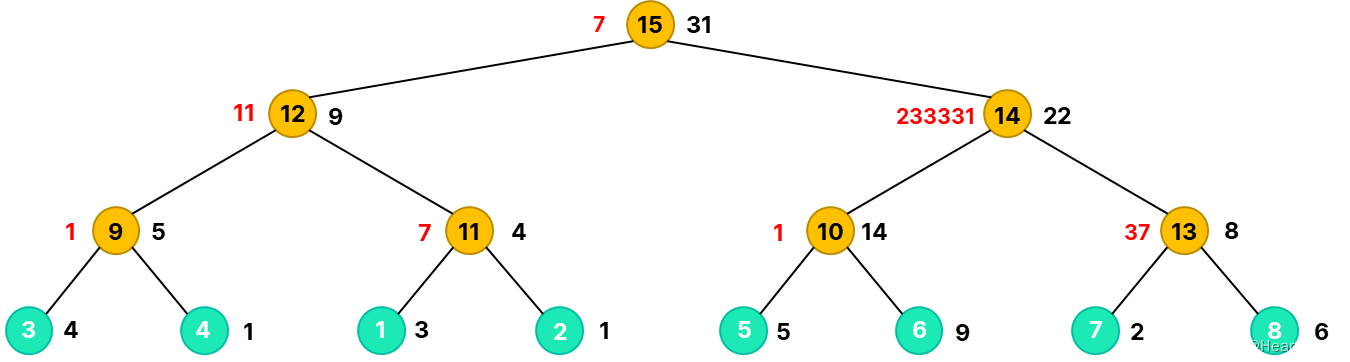
2021ICPC上海 H.Life is a Game Kruskal重构树

Are the microorganisms in the intestines the same as those on the skin?
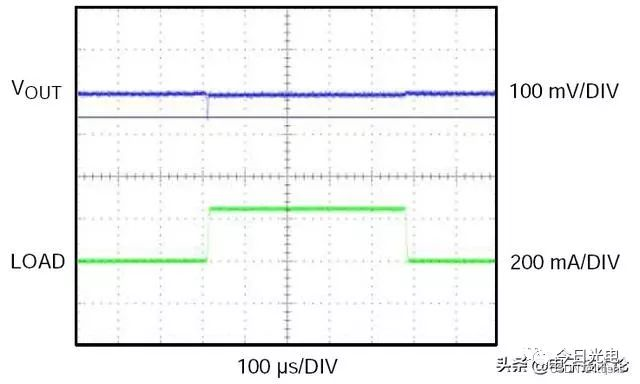
LDO稳压芯片-内部框图及选型参数
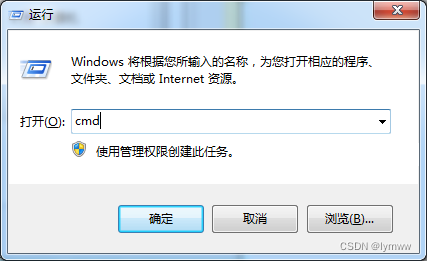
When copying something from the USB flash disk, an error volume error is reported. Please run CHKDSK

U盘拷贝东西时,报错卷错误,请运行chkdsk
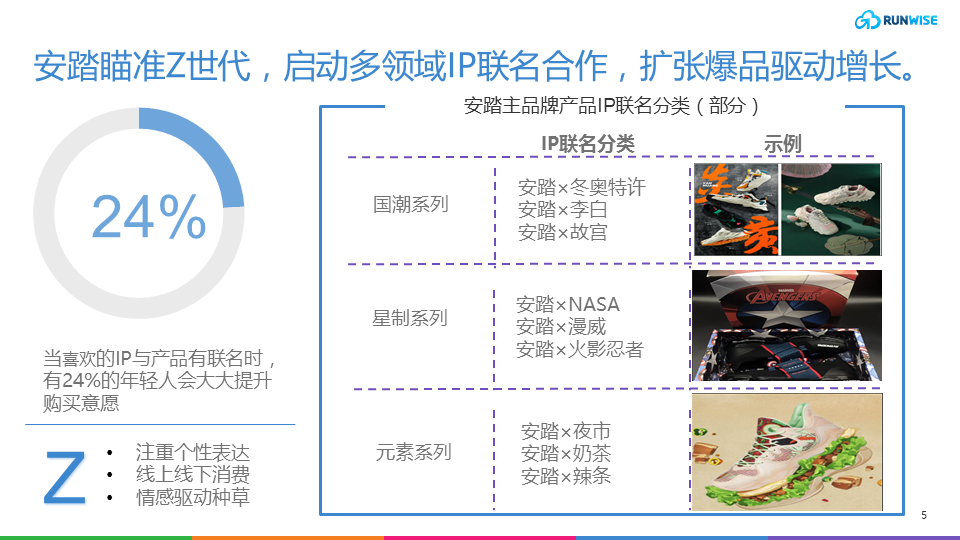
Anta DTC | Anta transformation, building a growth flywheel that is not only FILA
随机推荐
ArcGIS:字段赋值_属性表字段计算器(Field Calculator)依据条件为字段赋值
Wechat forum exchange applet system graduation design (5) assignment
Adrnoid开发系列(二十五):使用AlertDialog创建各种类型的对话框
Network security sqlmap and DVWA explosion
Unity3D学习笔记4——创建Mesh高级接口
Coreseek:第二步建索引及測试
iNFTnews | Web5 vs Web3:未来是一个过程,而不是目的地
U盘拷贝东西时,报错卷错误,请运行chkdsk
Txt file virus
为什么市场需要低代码?
Software test classification
Opencv scalar passes in three parameters, which can only be displayed in black, white and gray. Solve the problem
Talk about DART's null safety feature
Network security - joint query injection
opencv scalar传入三个参数只能显示黑白灰问题解决
海内外技术人们“看”音视频技术的未来
What are the similarities and differences between smart communities and smart cities
Install Fedora under RedHat
FPGA基础篇目录
微信论坛交流小程序系统毕业设计毕设(7)中期检查报告