当前位置:网站首页>Flow characteristics of kitchen knife, ant sword, ice scorpion and Godzilla
Flow characteristics of kitchen knife, ant sword, ice scorpion and Godzilla
2022-07-05 17:18:00 【qq_ fifty-one million five hundred and fifty thousand seven hun】
Ant sword :
ini_set
ini_set_time
ini_set_limit
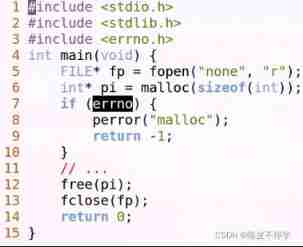
@ini_set(“display_errors”,“0”)
Part of the code is transmitted in clear text , Better identification
kitchen knife :
The old version adopts plaintext transmission , It's very recognizable
The new version uses base64 encryption , The detection idea is to analyze traffic packets , Find a lot of base64 You need to pay attention to encrypting ciphertext
Ice scorpion :
Ice scorpion 1: Ice scorpion 1 There is a key negotiation process , This process is plaintext transmission , And there are two flows , Used to verify
Ice scorpion 2: Because there are many built-in UA head , So when one is the same IP Repeated requests , however UA You need to pay attention when your head is different
Ice scorpion 3: Because the negotiation process is omitted , So you can bypass a lot of traffic , But other features remain , such as ua head
Ice scorpion packets are always accompanied by a large number of content-type:application What, what , No matter what GET still POST, Requested http in ,content-type by application/octet-stream
And their accept Such lengths are always equal , Normally, according to the application scenario and different files , The length is different
Godzilla :
cookie There is a small mistake in this value , Is a normal request cookie There is no semicolon at the end , Subsequent authors may make adjustments
And response , Godzilla will respond three times , And I think there is another place to pay attention to webshell Connect , Therefore, a long-term connection is usually set , therefore connection It's going to be here keep-alive
边栏推荐
- 调查显示传统数据安全工具面对勒索软件攻击的失败率高达 60%
- Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword
- Browser rendering principle and rearrangement and redrawing
- CMake教程Step3(添加库的使用要求)
- C# TCP如何限制单个客户端的访问流量
- NPM installation
- Error in compiling libssh2. OpenSSL cannot be found
- It is forbidden to copy content JS code on the website page
- Oracle缩表空间的完整解决实例
- Embedded UC (UNIX System Advanced Programming) -3
猜你喜欢
Embedded UC (UNIX System Advanced Programming) -2

Practical example of propeller easydl: automatic scratch recognition of industrial parts

Embedded UC (UNIX System Advanced Programming) -1

ECU简介
Etcd 构建高可用Etcd集群
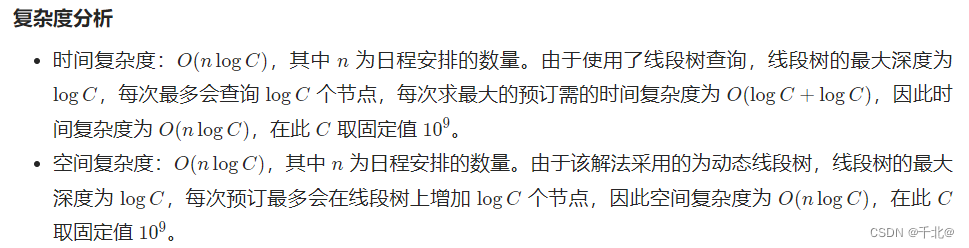
【729. 我的日程安排錶 I】

激动人心!2022开放原子全球开源峰会报名火热开启!
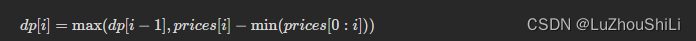
【剑指 Offer】63. 股票的最大利润
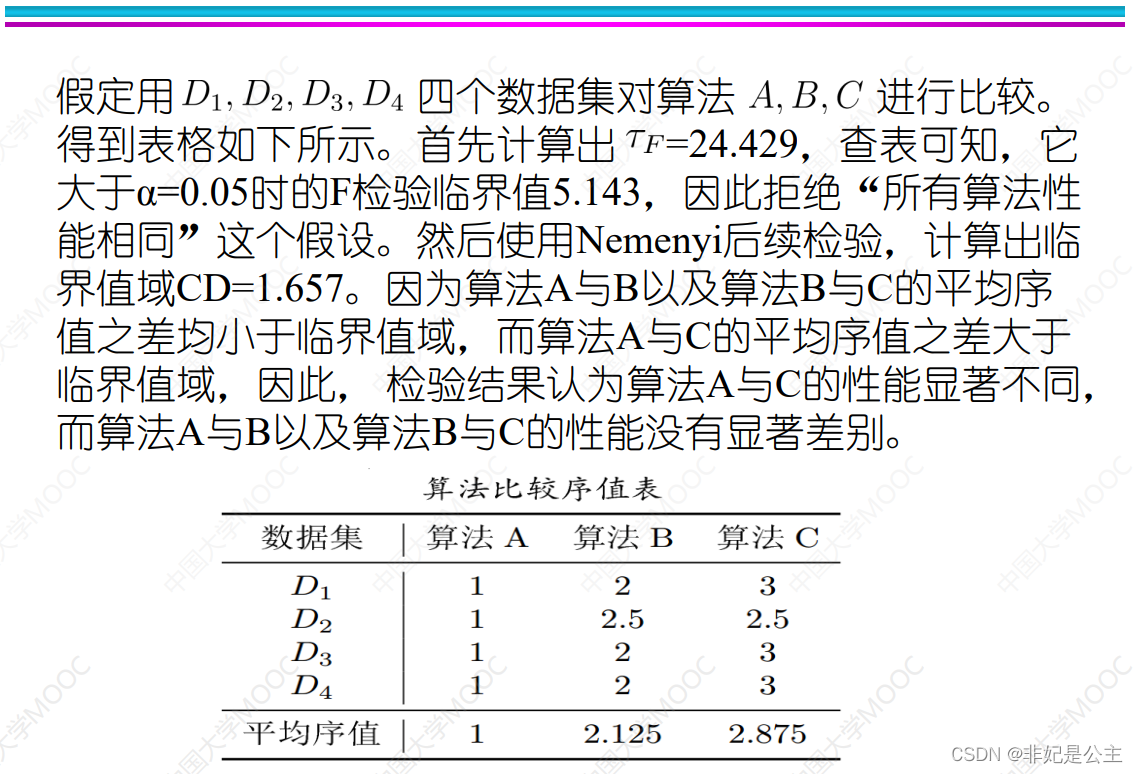
机器学习02:模型评估
![[Web attack and Defense] WAF detection technology map](/img/7c/60a25764950668ae454b2bc08fe57e.png)
[Web attack and Defense] WAF detection technology map
随机推荐
Is it safe to open an account for digging wealth stocks? How is it safe to open a stock account?
[wechat applet] read the life cycle and route jump of the applet
基于51单片机的电子时钟设计
Rider 设置选中单词侧边高亮,去除警告建议高亮
CMake教程Step3(添加库的使用要求)
thinkphp3.2.3
Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword
一个满分的项目文档是如何书写的|得物技术
ternary operator
Embedded-c Language-4
Error in composer installation: no composer lock file present.
【7.7直播预告】《SaaS云原生应用典型架构》大咖讲师教你轻松构建云原生SaaS化应用,难题一一击破,更有华为周边好礼等你领!
[729. My schedule I]
Embedded UC (UNIX System Advanced Programming) -2
【729. 我的日程安排錶 I】
It is forbidden to copy content JS code on the website page
Three traversal methods of binary tree
stirring! 2022 open atom global open source summit registration is hot!
[Jianzhi offer] 61 Shunzi in playing cards
C how TCP restricts the access traffic of a single client