当前位置:网站首页>Cross-chain bridge protocol Nomad suffers hacker attack, losing more than $150 million
Cross-chain bridge protocol Nomad suffers hacker attack, losing more than $150 million
2022-08-03 10:49:00 【Babbitt Information】

DeFi 之道讯,8 月 2 日,跨链桥协议 Nomad 遭遇攻击,超过 1.5 $100 million in user funds were transferred by hackers,Paradigm 合伙人 samczsun This security incident was analyzed.
Nomad just suffered Web3 Lost in one of the most chaotic hacks ever 1.5 亿美元.So how exactly does this happen,其根本原因是什么?Allow me to take you behind the scenes of this attack.
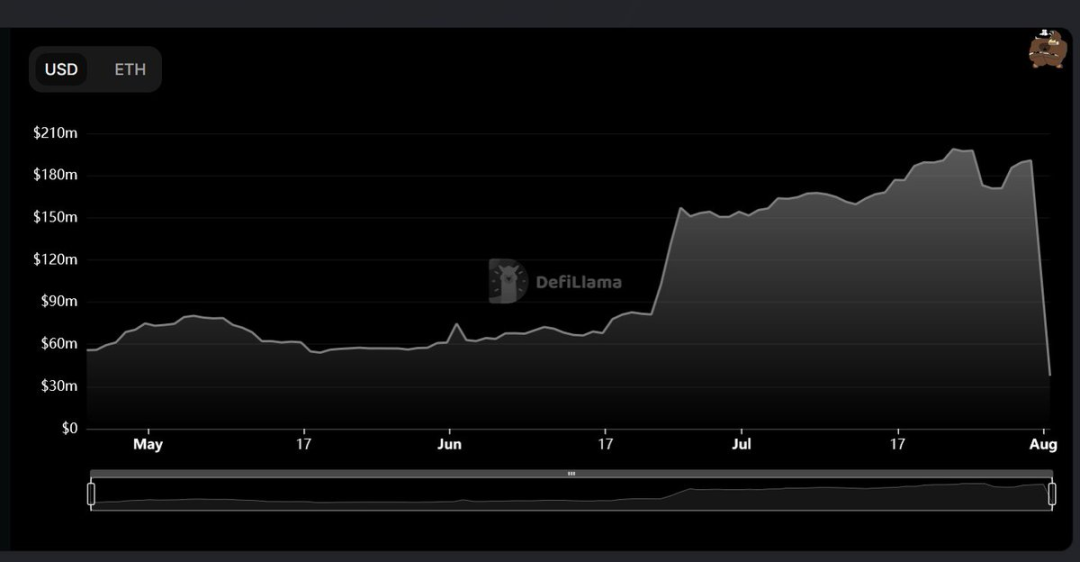
这一切都始于 @officer_cia 在 ETHSecurity Shared in the telegram group channel @spreekaway 推文,Although I didn't know what was going on at the time,但离开 Nomad The amount of assets across the chain bridge is clearly not a good sign.
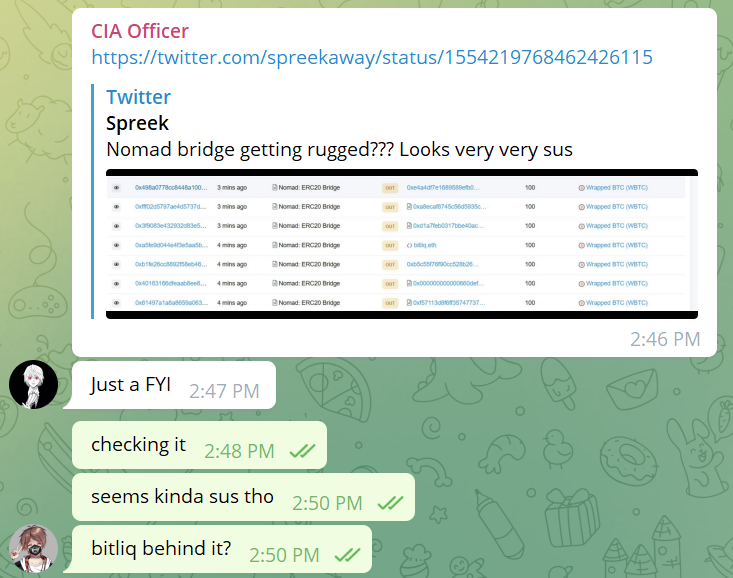
My first thought was that there was some misconfiguration of the coin's decimal point.毕竟,This cross-chain bridge appears to be in progress“发送 0.01 WBTC,返还 100 WBTC”的促销活动.
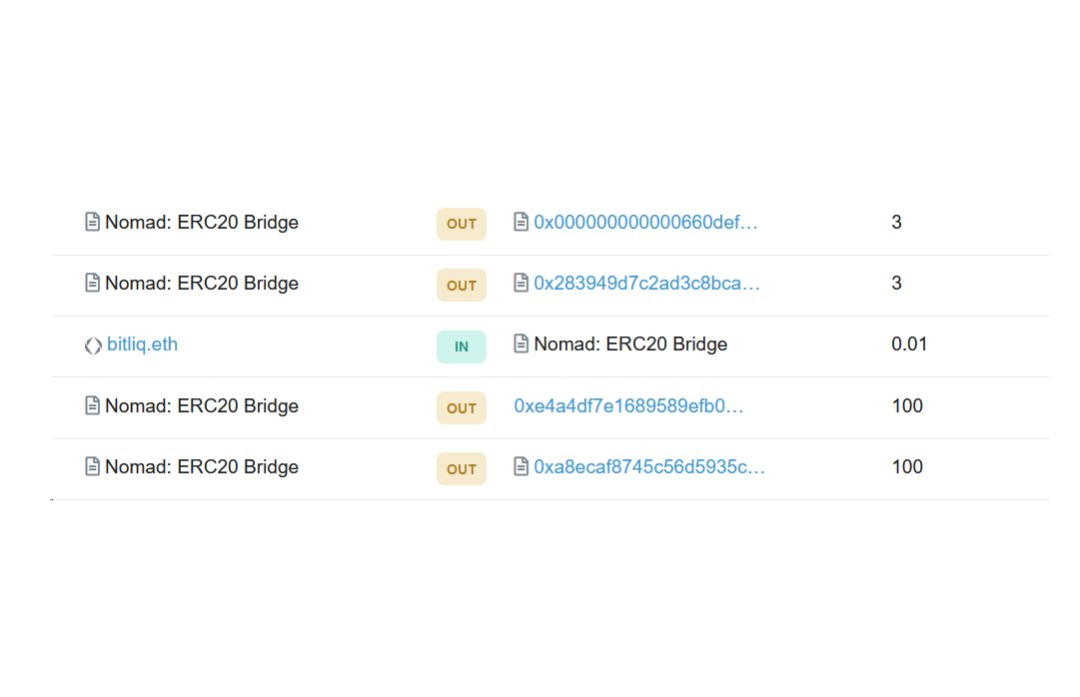
然而,在 Moonbeam After some painful manual digging around the web,我确认 Moonbeam The transaction is indeed cross-chain 0.01 WBTC,但不知何故,The asset that the Ethereum transaction crosses the chain is 100 WBTC.
https://moonscan.io/tx/0xcca9299c739a1b538150af007a34aba516b6dade1965e80198be021e3166fe4c
https://etherscan.io/tx/0xa5fe9d044e4f3e5aa5bc4c0709333cd2190cba0f4e7f16bcf73f49f83e4a5460
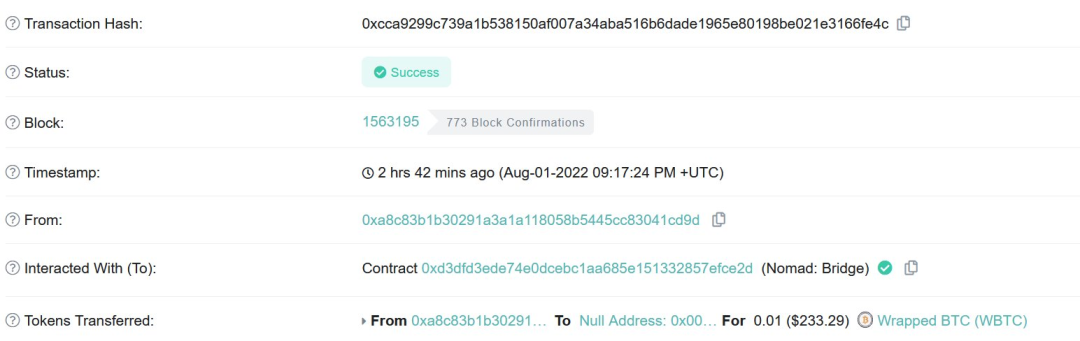
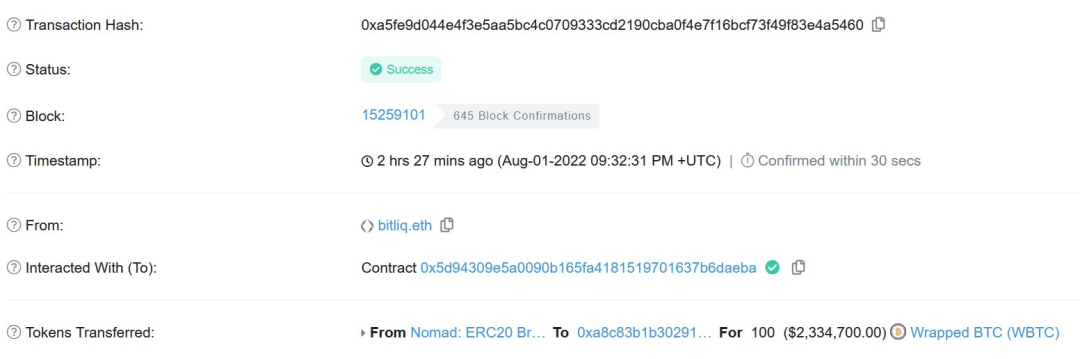
此外,WBTC Cross-chain transactions don't actually prove anything.It's just called directly process,可以说,Being able to process a message without first proving it is very bad.
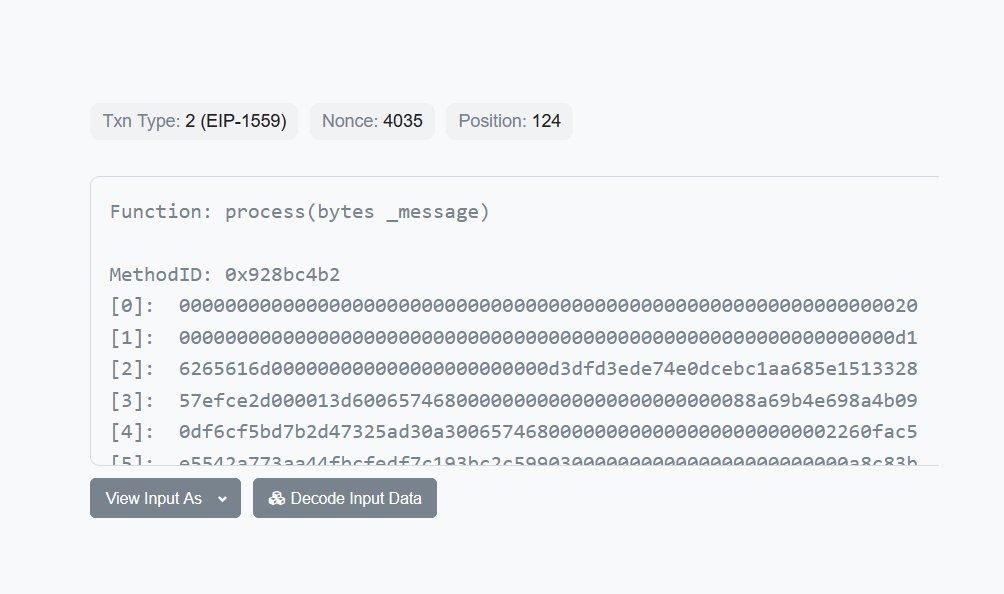
这个时候,有两种可能性,Either the proof was submitted separately in an earlier block,要么是 Replica The contract has serious loopholes.但是,There is absolutely no indication that anything has been proven recently.
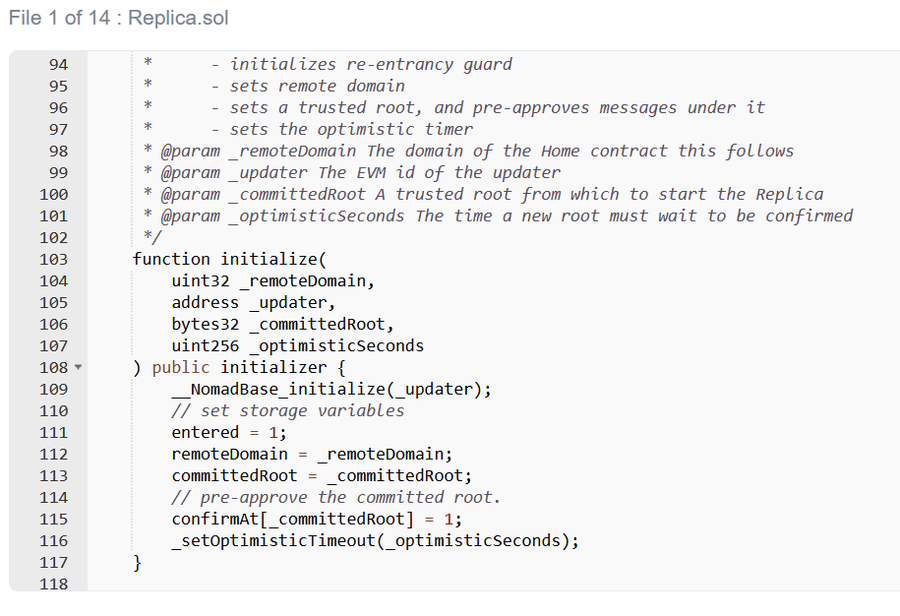
That leaves only one possibility,Replica There is a fatal loophole in the contract.那到底是怎么回事呢?A quick look shows,Submitted messages must belong to an acceptable root,否则,第 185 The line check will fail.
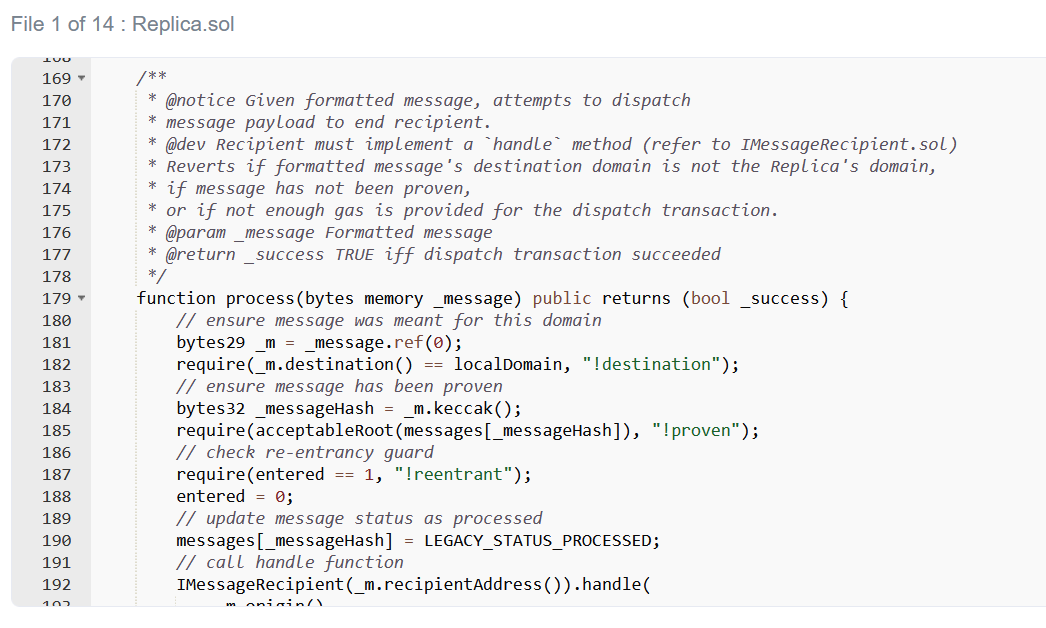
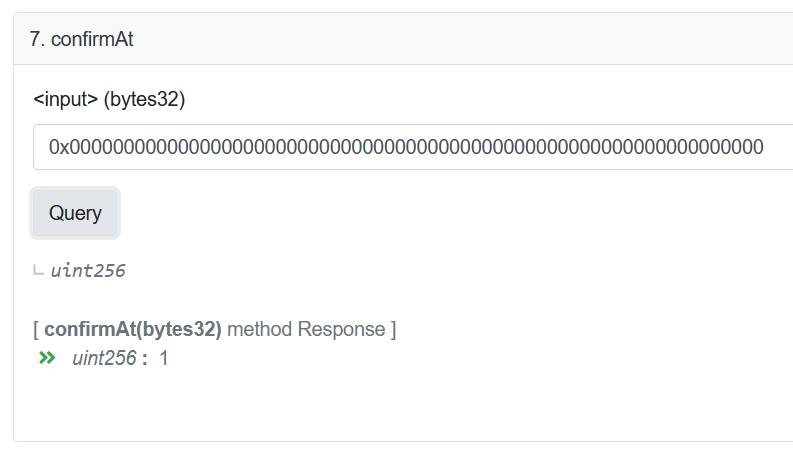
幸运的是,There is an easy way to check this assumption.I know the unproven message root will be 0x00,因为消息 [_messageHash] will be uninitialized.All I have to do is check if the contract will accept this.
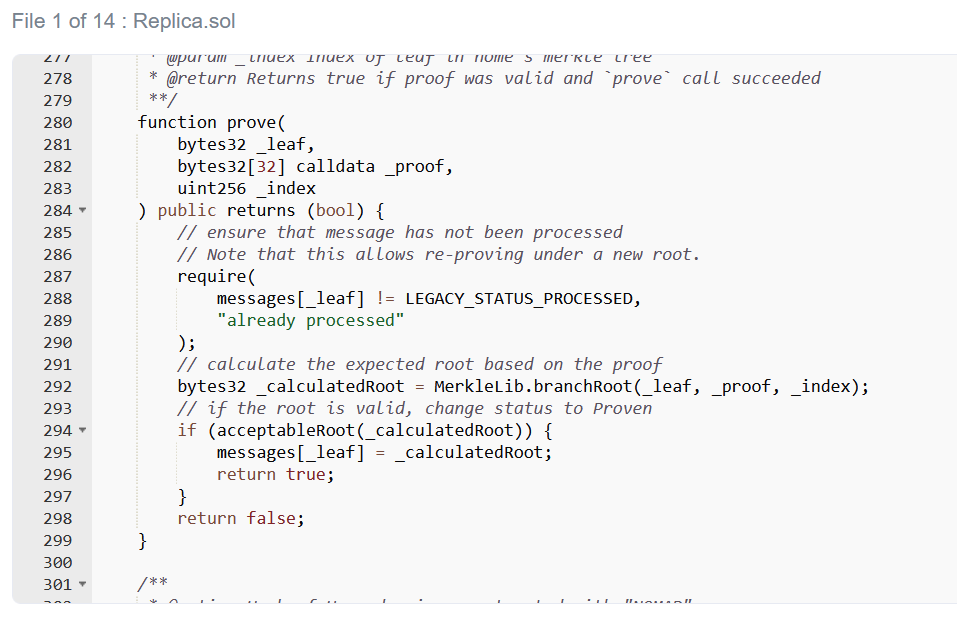
哎……
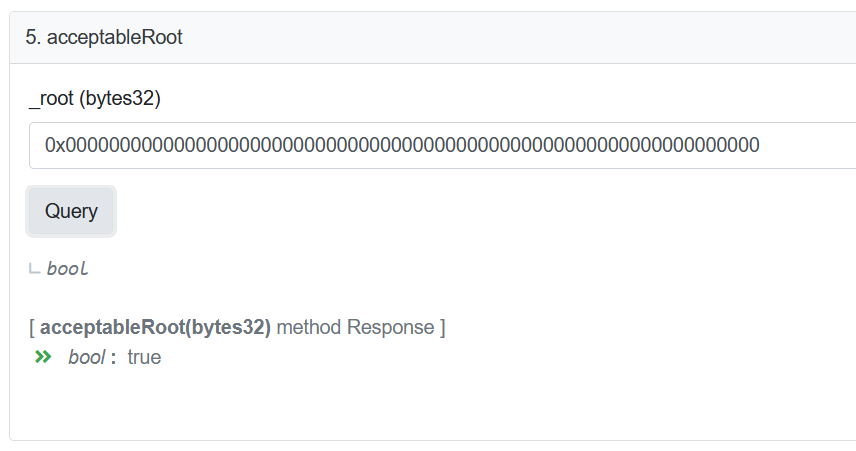
事实证明,During routine upgrades,Nomad The team initializes the root of trust as 0x00.需要明确的是,It is a common practice to use a zero value as an initialization value.不幸的是,在这种情况下,It has a small side effect,That is, each message is automatically validated.
That's why hacking is so messy,你不需要了解 Solidity 或 Merkle tree or something,All you have to do is find a valid deal,Find it with your address/Substitute another person's address,Then rebroadcast it.
总的来说,A routine upgrade marks the zero hash as a valid root,The effect is to allow in Nomad spoofed news,Attackers abuse this feature to replicate/paste transaction,And quickly drained the funds of this cross-chain bridge in a frantic melee.
译者注:此次 Nomad Cross-chain bridge hacking,Moonbeam 和 evmos Users of these two public chains will be greatly affected,其中, Moonbeam The cross-chain funds involved are relatively large.This incident reminds us once again of the risks of cross-chain bridges,After the user uses the cross-chain bridge,You should try to avoid holding cross-chain assets,Instead, it should be exchanged for the native assets of the blockchain as soon as possible,And the native asset security of the Ethereum main chain is higher than other chains.
中文推特:https://twitter.com/8BTC_OFFICIAL
英文推特:https://twitter.com/btcinchina
Discord社区:https://discord.gg/defidao
电报频道:https://t.me/Mute_8btc
电报社区:https://t.me/news_8btc

边栏推荐
- MATLAB Programming and Applications 2.6 Strings
- 月薪没到35K的程序员必须要背的面试八股,我先啃为敬!
- MATLAB programming and application 2.7 Structural data and unit data
- Activiti产生的背景和作用
- 【学习笔记之菜Dog学C】通讯录
- 开源一夏 | 教你快速实现“基于Docker快速构建基于Prometheus的MySQL监控系统”
- Mysql OCP 73 questions
- OS层面包重组失败过高,数据库层面gc lost 频繁
- [华为云在线课程][SQL语法入门][学习笔记]
- BPMN和DMN基本概念和使用案例
猜你喜欢
随机推荐
投稿有礼,双社区签约博主名额等你赢!
Analysis of the idea of the complete knapsack problem
从餐桌到太空,孙宇晨的“星辰大海”
How to use outside the PHP command in the container
程序员架构修炼之道:如何设计出可持续演进的系统架构?
鸿蒙第四次
浪潮—英伟达打造元宇宙新方案,虚拟人的故事将再破你的认知
Boolean 与numeric 无法互转
MySQL数据库高级使用
面试突击71:GET 和 POST 有什么区别?
成对连接点云分割
4 g acquisition ModbusTCP turn JSON MQTT cloud platform
8 月数据库排行榜:Oracle 分数大跌,MySQL 上涨最多
for in 和 for of的区别
跨链桥协议 Nomad 遭遇黑客攻击,损失超 1.5 亿美元
Web Server 设置缓存响应字段的一些推荐方案
一文了解,从RS485传感器到物联网关到云平台过程
RecyclerView的item高度自适应
像用户体验设计师一样思考
苏州大学:从PostgreSQL到TDengine