当前位置:网站首页>Hash table acwing 841 String hash
Hash table acwing 841 String hash
2022-07-02 12:42:00 【T_ Y_ F666】
Hashtable AcWing 841. String hash
Original link
Algorithm tags
String hash Hash
Ideas
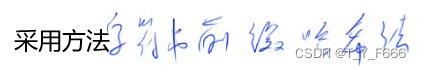
Simulation example 
Then the corresponding string hash
seek hash
Treat the corresponding string as a segment p Hexadecimal number 
Be careful : Characters cannot be mapped to 0
reason : If the A It maps to 0, Will cause all AA, AAA, …… Will all be 0.
Conflict handling
For data range < 2^64 data ,P Usually take 131 or 13331, warrantable hash Probability of conflict <0.01%
Code
#include<bits/stdc++.h>
#define int long long
#define ull unsigned long long
#define rep(i, a, b) for(int i=a;i<b;++i)
#define Rep(i, a, b) for(int i=a;i>b;--i)
using namespace std;
// P Map the corresponding string hash value
// For data range < 2^64 data
//P Usually take 131 or 13331
// This ensures that hash Probability of conflict <0.01%
const int N = 100005, P = 131;
// h The storage string prefix corresponds to hash value p Store the decimal number
ull h[N], p[N];
char s[100005];
inline int read(){
int s=0,w=1;
char ch=getchar();
while(ch<'0'||ch>'9'){if(ch=='-')w=-1;ch=getchar();}
while(ch>='0'&&ch<='9') s=s*10+ch-'0',ch=getchar();
return s*w;
}
void put(int x) {
if(x<0) putchar('-'),x=-x;
if(x>=10) put(x/10);
putchar(x%10^48);
}
// Corresponding string hash value
ull get(int l, int r){
return h[r]-h[l-1]*p[r-l+1];
}
signed main(){
ios::sync_with_stdio(false);
cin.tie(0);
cout.tie(0);
int n=read(), m=read();
scanf("%s", s+1);
// from 1 Start mapping
p[0]=1;
rep(i, 1, n+1){
p[i]=p[i-1]*P;
h[i]=h[i-1]*P+s[i];
}
while(m--){
int l1=read(), r1=read(), l2=read(), r2=read();
if(get(l1, r1)!=get(l2, r2)){
puts("No");
}else{
puts("Yes");
}
}
return 0;
}
Originality is not easy.
Reprint please indicate the source
If it helps you Don't forget to praise and support 
边栏推荐
- 线性DP AcWing 902. 最短编辑距离
- Calculate the maximum path sum of binary tree
- Distributed machine learning framework and high-dimensional real-time recommendation system
- This "little routine" is set on the dough cake of instant noodles. No wonder programmers are always hungry
- 深拷貝 事件總線
- 线性DP AcWing 898. 数字三角形
- 堆 AcWing 838. 堆排序
- OpenCV中cv2.VideoWriter_fourcc()函数和cv2.VideoWriter()函数的结合使用
- Fluent fluent library encapsulation
- JS8day(滚动事件(scroll家族),offset家族,client家族,轮播图案例(待做))
猜你喜欢
上手报告|今天聊聊腾讯目前在用的微服务架构
Openssh remote enumeration username vulnerability (cve-2018-15473)

AI中台技术调研
China traffic sign detection data set

Simple use of drools decision table

JS7day(事件对象,事件流,事件捕获和冒泡,阻止事件流动,事件委托,学生信息表案例)

NTMFS4C05NT1G N-CH 30V 11.9A MOS管,PDF

哈希表 AcWing 841. 字符串哈希

Js7day (event object, event flow, event capture and bubble, prevent event flow, event delegation, student information table cases)

线性DP AcWing 898. 数字三角形
随机推荐
NTMFS4C05NT1G N-CH 30V 11.9A MOS管,PDF
[FFH] little bear driver calling process (take calling LED light driver as an example)
C#修饰符
Leetcode - Sword finger offer 37, 38
Calculate the maximum path sum of binary tree
通过反射执行任意类的任意方法
Shutter encapsulated button
JDBC 预防sql注入问题与解决方法[PreparedStatement]
线性DP AcWing 896. 最长上升子序列 II
Programmers can't find jobs after the age of 35? After reading this article, you may be able to find the answer
Redis avalanche, penetration, breakdown
Error in kubeadm join: [error port-10250]: port 10250 is in use [error fileavailable--etc kubernetes PKI
Input box assembly of the shutter package
What is the relationship between NFT and metauniverse? How to view the market? The future market trend of NFT
China traffic sign detection data set
Is the neural network (pinn) with embedded physical knowledge a pit?
单指令多数据SIMD的SSE/AVX指令集和API
线性DP AcWing 898. 数字三角形
There is a hidden danger in CDH: the exchange memory used by the process of this role is XX megabytes. Warning threshold: 200 bytes
JS6day(DOM结点的查找、增加、删除。实例化时间,时间戳,时间戳的案例,重绘和回流)