当前位置:网站首页>PHP asymmetric encryption method private key and public key encryption and decryption method
PHP asymmetric encryption method private key and public key encryption and decryption method
2022-07-02 19:17:00 【Game programming】
The private key and public key are obtained as follows :
①. Access online to generate asymmetric encrypted public and private key pairs : http://web.chacuo.net/netrsakeypair
Click generate key pair , Delete RSA Generate format -> BEGIN RSA PRIVATE KEY and END PUBLIC KEY , That is, the first and last lines .
②. Access the online string text compression tool , Delete all new lines in the text 、 Tabulation key 、 Space 、 enter 、 Line break character : http://www.ab173.com/other/compress.php
Copy the generated public and private keys into the compressed text box to remove line breaks and spaces
③. Upload the public key to the merchant background , The platform will use the public key to decrypt and verify the signature .
④. The private key is kept secretly ( Encryption uses ).
<?php/** * Description: The platform decrypts the public key to obtain data ( attestation ) * Date: 2022/7/1 * @param $data */public function decrypt($data){ ksort($data); $toSign = ''; foreach ($data as $key => $value) { if (strcmp($key, 'sign') != 0 && $value != '') { $toSign .= $key . '=' . $value . '&'; } } $str = rtrim($toSign, '&'); $encrypted = ''; // Public key $pem = chunk_split($this->platform_public_key, 64, "\n"); $pem = "-----BEGIN PUBLIC KEY-----\n" . $pem . "-----END PUBLIC KEY-----\n"; $publickey = openssl_pkey_get_public($pem); $base64 = str_replace(array('-', '_'), array('+', '/'), $data['sign']); $crypto = ''; foreach (str_split(base64_decode($base64), 128) as $chunk) { openssl_public_decrypt($chunk, $decrypted, $publickey); $crypto .= $decrypted; } if ($str != $crypto) { // Attestation of failure record_log([ 'msg' => ' Attestation of failure ', 'data' => [ 'params' => $data, 'str' => $str, 'crypto' => $crypto, ], ], 'globalpay_payin_error_'); exit('Signature verification failed'); }}/** * Description: Private key encryption generates signature * Date: 2022/7/1 * @param $data * @return mixed */public function encrypt($data){ ksort($data); $str = ''; foreach ($data as $k => $v) { if (!empty($v)) { $str .= (string)$k . '=' . $v . '&'; } } $str = rtrim($str, '&'); $encrypted = ''; // Private key $pem = chunk_split($this->mch_private_key, 64, "\n"); $pem = "-----BEGIN PRIVATE KEY-----\n" . $pem . "-----END PRIVATE KEY-----\n"; $private_key = openssl_pkey_get_private($pem); $crypto = ''; foreach (str_split($str, 117) as $chunk) { openssl_private_encrypt($chunk, $encryptData, $private_key); $crypto .= $encryptData; } $encrypted = base64_encode($crypto); $encrypted = str_replace(array('+', '/', '='), array('-', '_', ''), $encrypted); $data['sign'] = $encrypted; return $data;}author :LordForce
Game programming , A game development favorite ~
If the picture is not displayed for a long time , Please use Chrome Kernel browser .
边栏推荐
猜你喜欢
yolov3 训练自己的数据集之生成train.txt
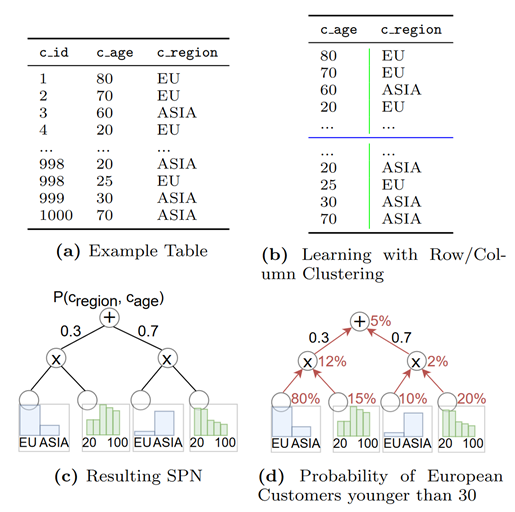
论文导读 | 机器学习在数据库基数估计中的应用

Yunna | why use the fixed asset management system and how to enable it

Juypter notebook modify the default open folder and default browser

Develop fixed asset management system, what voice is used to develop fixed asset management system

机器学习笔记 - 时间序列预测研究:法国香槟的月销量
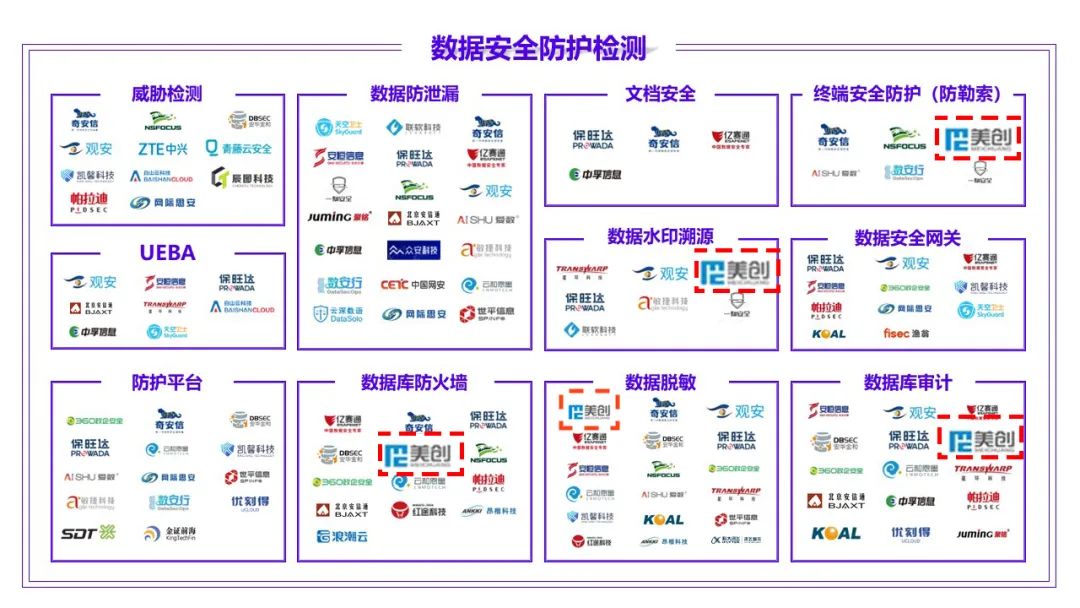
According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors
![[test development] software testing - concept](/img/24/9ee885d46f7200ae7449957ca96b9d.png)
[test development] software testing - concept
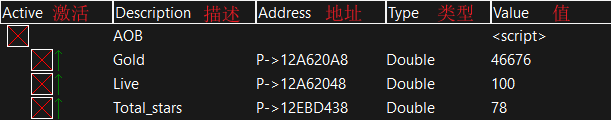
使用 Cheat Engine 修改 Kingdom Rush 中的金钱、生命、星
![[论文阅读] CA-Net: Leveraging Contextual Features for Lung Cancer Prediction](/img/ef/bb48ee88d5dc6fe876a498ab53106e.png)
[论文阅读] CA-Net: Leveraging Contextual Features for Lung Cancer Prediction
随机推荐
R language ggplot2 visualization: gganimate package creates dynamic histogram animation (GIF) and uses transition_ The States function displays a histogram step by step along a given dimension in the
juypter notebook 修改默认打开文件夹以及默认浏览器
Novice must see, click two buttons to switch to different content
Emmet基础语法
High frequency interview questions
The R language dplyr package rowwise function and mutate function calculate the maximum value of multiple data columns in each row in the dataframe data, and generate the data column (row maximum) cor
[daily question] first day
PHP非对称加密方法私钥及公钥加密解密的方法
Why should we build an enterprise fixed asset management system and how can enterprises strengthen fixed asset management
Markdown基础语法
Excel查找一列中的相同值,删除该行或替换为空值
The mybatieshelperpro tool can be generated to the corresponding project folder if necessary
R语言ggplot2可视化:可视化折线图、使用labs函数为折线图添加自定义的X轴标签信息
Use cheat engine to modify money, life and stars in Kingdom rush
2022 compilation principle final examination recall Edition
Tutorial (5.0) 10 Troubleshooting * fortiedr * Fortinet network security expert NSE 5
性能测试如何创造业务价值
使用CLion编译OGLPG-9th-Edition源码
Masa framework - DDD design (1)
电商系统中常见的 9 大坑,你踩过没?