当前位置:网站首页>Intelligent security contract - delegatecall (2)
Intelligent security contract - delegatecall (2)
2022-08-03 18:09:00 【fingernft】
This time, let's talk about a more complex contract vulnerability case when using the delegatecall function.
Target Contract
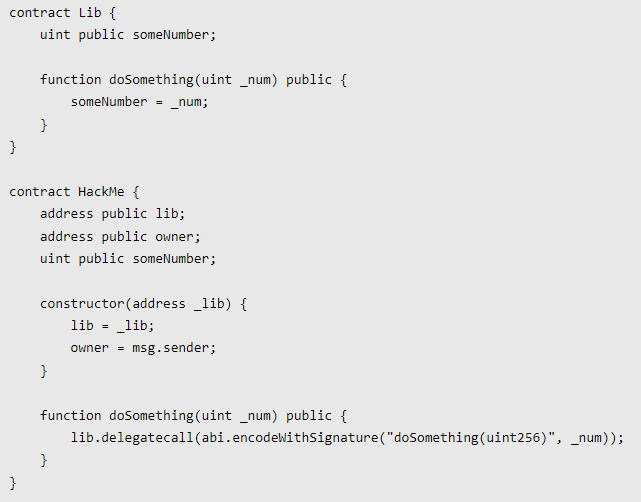 vulnerability analysisThe target of this attack is stillIt is to obtain the owner permission in the HackMe contract. We can see that in the two contracts, except for the constructor in the HackMe contract, which can modify the owner of the contract, there is no other place to modify the owner function, but it can modify the value of slot0, while the HackMe contractThe slot slot0 in the middle represents the address of Lib, then we first modify the address of Lib to our address, and when we call the HackMe contract again, the logic in our contract will be run, so the value of the slot we want to change is not the same.Is it all under our control?
vulnerability analysisThe target of this attack is stillIt is to obtain the owner permission in the HackMe contract. We can see that in the two contracts, except for the constructor in the HackMe contract, which can modify the owner of the contract, there is no other place to modify the owner function, but it can modify the value of slot0, while the HackMe contractThe slot slot0 in the middle represents the address of Lib, then we first modify the address of Lib to our address, and when we call the HackMe contract again, the logic in our contract will be run, so the value of the slot we want to change is not the same.Is it all under our control?
Attack contractThe following is our attack contract:
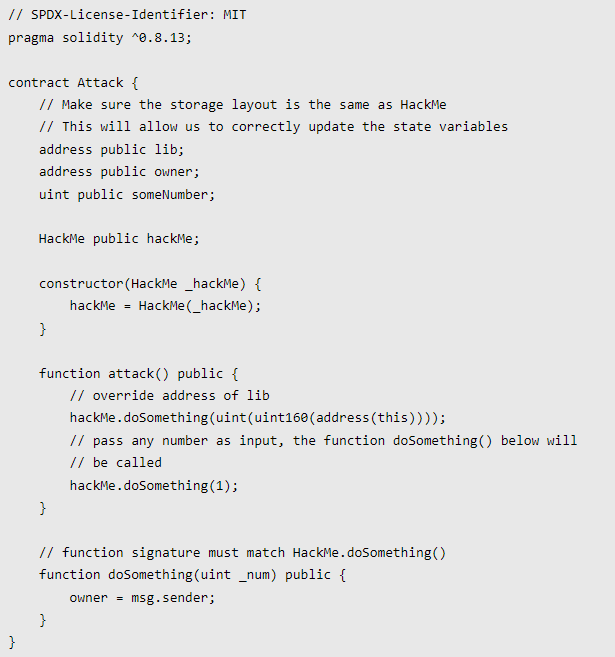
Next, let's look at the entire logic of the attack:
The Attack.attack() function first converts its own address to uint256 type (this step is to be compatible with the data type in the target contract) and calls the HackMe.doSomething() function for the first time;
The HackMe.doSomething() function uses the delegatecall function to call the Lib.doSomething() function with the address of the incoming Attack contract;
You can see that the Lib.doSomething() function changes the parameter stored at slot0 in the contract to the incoming value, so that when the HackMe contract uses delegatecall to call the Lib.doSomething() function, it will also change its location in the contract.The value of the variable stored in slot0, that is, changing the lib parameter (stored here is the address of the Lib contract) to the address of the Attack contract we passed in.At this point, the address of the Lib contract previously stored in the HackMe.lib parameter has been modified to the address of the Attack contract we passed in;
4.Attack.attack() function calls the HackMe.doSomething() function again. Since we have modified the HackMe.lib variable to the address of the Attack contract in the previous step, the HackMe.doSomething() function will no longer be used.Instead of calling the previous Lib contract, use delegatecall to call Attack.doSomething() function.At this point, let's observe the writing of the Attack contract, and find that the storage location of its variables is deliberately consistent with the HackMe contract, and it is not difficult to find that the content of the Attack.doSomething() function is also written by the attacker as owner = msg.sender, this operation is modifiedThe variable in the contract is stored in slot1.So the HackMe contract uses the delegatecall to call the Attack.doSomething() function to change the variable owner whose storage location is slot1 in the contract to msg.sender, which is the address of the attacker. At this point, the attacker has completed his attack.
Repair suggestion When we use delegatecall in the development of the contract, we should always pay attention to the contract address that it is called to always run within the logic we designed, and it cannot be allowed to exceed the applicable scope of our design.Scope, once there is a situation beyond our expected design, the contract may be used by criminals.
If you want to know more about smart contracts and blockchain knowledge, welcome to the blockchain exchange community CHAINPIP community to communicate and learn together~Community address: https://www.chainpip.com/
边栏推荐
- 【技术白皮书】第二章:OCR智能文字识别回顾——自然语言文本发展历程
- 从技术全景到场景实战,透析「窄带高清」的演进突破
- Trie思想及模板
- 2021年数据泄露成本报告解读
- 宝塔搭建企业招聘网站源码实测
- cell delay and net delay
- ImportError: /lib/libgdal.so.26: undefined symbol: sqlite3_column_table_name
- LeetCode - 102. 二叉树的层序遍历;110. 平衡二叉树;098. 验证二叉搜索树
- 智能合约安全——delegatecall (2)
- 中国算力大会昇腾鲲鹏生态论坛举办;快手成立独立to B业务部门…
猜你喜欢
随机推荐
ThreeJS简介
新“妖股”13个交易日暴涨320倍,市值3100亿美元超阿里
智能合约安全——delegatecall (2)
Is OnePlus Ace worth buying?Use strength to interpret the power of performance
这是Facebook母公司 关于元宇宙的80万亿美元豪赌
常见亲脂性细胞膜染料DiO, Dil, DiR, Did光谱图和实验操作流程
【Azure 事件中心】使用Azure AD认证方式创建Event Hub Consume Client + 自定义Event Position
LyScript 内存交换与差异对比
揭秘deepin 23,从这里开始!
VsCode预览Geojson数据
开篇-开启全新的.NET现代应用开发体验
China Hashpower Conference Ascension Kunpeng Ecological Forum was held; Kuaishou established an independent to B business department…
使用.NET简单实现一个Redis的高性能克隆版(一)
数字IC笔迹-MCMM、WNS和TNS
CodeTON Round 2 (Div. 1 + Div. 2, Rated, Prizes), problem: (D) Magical Array
yaml data format
有人知道flink sql 使用tableEnv.executeSql执行后,怎么获取到任务运行的
LeetCode - 102. 二叉树的层序遍历;110. 平衡二叉树;098. 验证二叉搜索树
云GPU如何安装和启动VNC远程桌面服务?
调用EasyCVR云台控制接口时,因网络延迟导致云台操作异常该如何解决?