当前位置:网站首页>Using emqx cloud to realize one machine one secret verification of IOT devices
Using emqx cloud to realize one machine one secret verification of IOT devices
2022-07-01 22:52:00 【EMQX】
Data security is the top priority of Internet of things applications . Manufacturers often use symmetric encryption 、 Asymmetric encryption 、 digital signature 、 Digital certificate and other methods to authenticate the equipment , To prevent the access of illegal devices . In the use of certificates , One type and one density 、 Different schemes such as one machine and one secret , One machine one secret scheme sets a unique device certificate for each device end in advance , Two way verification can be carried out when the device communicates with the server , After the verification is passed , Only when the device end and the server end are in normal data transmission . Compared with other schemes , One machine and one secret can achieve independent verification and authorization for each device , With higher security .
As a safe and reliable full custody MQTT Message cloud service , EMQX Cloud Support multiple authentication methods , Including basic certification ( user name / password , client ID/ password ) And JWT、PSK and X.509 Certification , At the same time, the external database can be configured as the data source to verify the authentication information .
This article will use Redis Store the database as the authentication data source , Explain how to pass the Common Name To verify information , Connect to EMQX Cloud, Realize client-side one machine one secret authentication . If the client certificate does not contain the specified unique Common Name, You cannot pass the certification .
Through this paper , Readers can realize one machine and one secret for their IOT devices 、 The ability of bidirectional identity authentication between the device and the server and establishing a secure channel , Effectively prevent forged device attacks 、 The device key is cracked 、 Forge server instructions 、 Monitor or tamper with key information 、 Attack means such as stealing keys through security vulnerabilities in the equipment production line .
Operation process
One 、 To configure TLS/SSL Two-way authentication
1、 preparation
Purchase server certificate , And resolve its domain name to the deployment connection address .
Generate client root ca Self signed certificate , Use self signed root ca The certificate issuing client certificate needs to ensure Common Name only .
# CA Certificate generation client-ca.crt,subj Adjust according to actual use . openssl req \ -new \ -newkey rsa:2048 \ -days 365 \ -nodes \ -x509 \ -subj "/C=Common Name/O=EMQ Technologies Co., Ltd/Common Name=EMQ CA" \ -keyout client-ca.key \ -out client-ca.crt # Client secret key generation client.key openssl genrsa -out client.key 2048 # Generate client certificate request file client.csr,Common Name Carry authentication information for the client openssl req -new -key client.key -out client.csr -subj "/Common Name=346a004d-1dab-4016-bb38-03cca7094415" # use CA The certificate signs the client certificate , Generate client.crt openssl x509 -req -days 365 -sha256 -in client.csr -CA client-ca.crt -CAkey client-ca.key -CAcreateserial -out client.crt # View the client certificate information openssl x509 -noout -text -in client.crt # Certificate of verification openssl verify -CAfile client-ca.crt client.crt
2、 The configuration process
Sign in EMQX Cloud Console . Enter deployment details , Click on +TLS/SSL configure button , Configure certificate content , You can upload files or fill in the certificate directly TLS/SSL Authentication type :
① One way Authentication : Only the client verifies the server certificate .
② Two-way authentication : Client and server mutually verify certificates .
In this sample document, we use Two-way authentication For example , Fill in the following in the deployment console :
① Public key certificate : Server certificate
② Certificate chain : Certificate chain , Usually, when the third-party organization issues the certificate, it will provide
③ Private key : Private key
④ client CA certificate : When selecting two-way authentication , You need to provide the client CA certificate
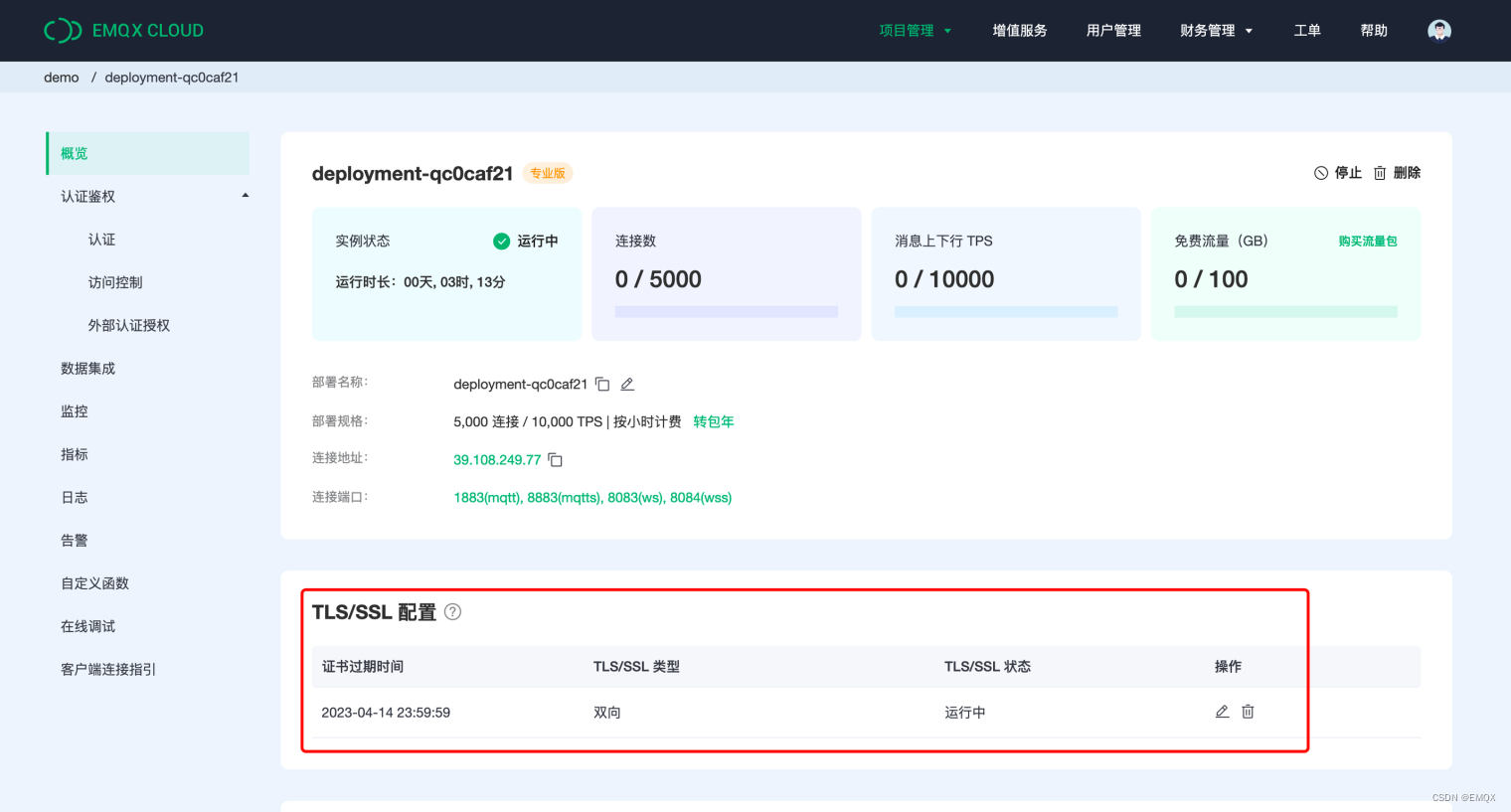
After completion , Click ok , Until the status is running , namely TLS/SSL Two way authentication configuration is complete .
Two 、 To configure Redis authentication / Access control
This article takes Redis authentication / Take access control as an example , Of course, you can also use other external authentication data sources , In the scenario described in this article , Recommended for comparison Redis authentication / Access control .
1、 establish VPC Peer to peer connection
stay EMQX Cloud Deployment details page , establish VPC Peer to peer connection , It is convenient for the professional version to deploy intranet access to you Redis Authentication database .

2、 To configure Redis authentication / Access control
redis To configure
In your ECS , Create a Redis service . For the convenience of demonstration , Use here Docker Quickly build .
docker run -itd --name redis -p 6379:6379 redis:latestThere are two ways to configure data in this example ( A choice ):
HMSET tls_domain:346a004d-1dab-4016-bb38-03cca7094415 password pubic HMSET tls_subject:346a004d-1dab-4016-bb38-03cca7094415 password pubic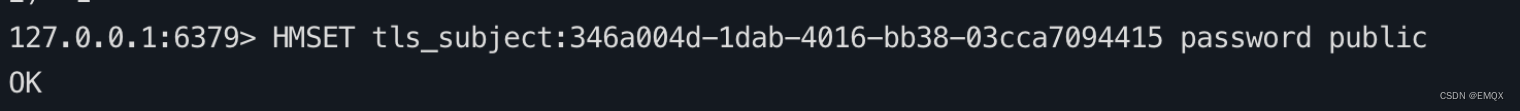
Redis authentication / Access control configuration
When authenticating ,EMQX Cloud The current client information will be used to populate and execute the user configured authentication query command , Find out that the client is in Redis Authentication data in .
Can be certified in SQL Use the following placeholders in , Execution time EMQX Cloud Will be automatically populated as client information ::
- %u: user name
- %c: client ID
- %C:TLS Certificate common name ( Domain name or subdomain name of the certificate ), Only when the TLS Valid when connected
- %d:TLS certificate subject, Only when the TLS Valid when connected
You can adjust the authentication query command according to your business needs , Use any Redis Supported commands (opens new window), However, in any case, the authentication query command needs to meet the following conditions :
① The first data in the query result must be password,EMQX Use this field to compare with the client password
② If the salt configuration is enabled , The second data in the query result must be salt Field ,EMQX Use this field as the salt( salt ) value
Click authentication in the deployment - External authentication authorization - Redis authentication / Access control , Click Configure authentication , You can create a new certification .
The authentication query command has the following two ways :
HMGET tls_domain:%C password HMGET tls_subject:%d passwordThat is, the device needs to carry the client certificate 、 Client secret key and its Common Name 、password The way to authenticate .

Test verification
We use MQTT X The simulation client carries the following information to connect to EMQX Cloud.
① Server side CA
② Common Name by 346a004d-1dab-4016-bb38-03cca7094415 Client certificate for 、 Client secret key
③ password:public

Click on Upper right corner connect, appear connected Indicates that the connection was successful . thus , With designation common name Your device has been successfully connected to EMQX Cloud, That is, one machine and one secret device are verified and connected to EMQX Cloud Have succeeded .

Conclusion
So far we're done EMQX Cloud Client-side one machine one certificate verification process , Successfully connected to deployment . Compared with other schemes , One machine and one secret can achieve independent verification and authorization for each device , With higher security , If you also set up a unique access credential for each of your IOT devices , You can refer to this article for configuration .
Copyright notice : This paper is about EMQ original , Reprint please indicate the source .
Link to the original text :https://www.emqx.com/zh/blog/one-device-one-secret-authentication-for-iot-devices-with-emqx-cloud
边栏推荐
- 【无标题】
- rxjs Observable of 操作符的单步调试分析
- Two schemes of transforming the heat map of human posture estimation into coordinate points
- 恶意软件反向关闭EDR的原理、测试和反制思考
- 旅游管理系统
- Hide the creation and use of users
- Lc669. Prune binary search tree
- Mixconv code
- 下班前几分钟,我弄清了v-model与.sync的区别
- Mysql5.7 set password policy (etc. three-level password transformation)
猜你喜欢
![[image segmentation] 2021 segformer neurips](/img/2f/a8631cbe9a46419b8dbd5205e1f5b5.png)
[image segmentation] 2021 segformer neurips
【图像分割】2021-SegFormer NeurIPS

使用 EMQX Cloud 实现物联网设备一机一密验证

Appium automated testing foundation - Supplement: introduction to desired capabilities parameters

MySQL中对于索引的理解

Intelligent computing architecture design of Internet
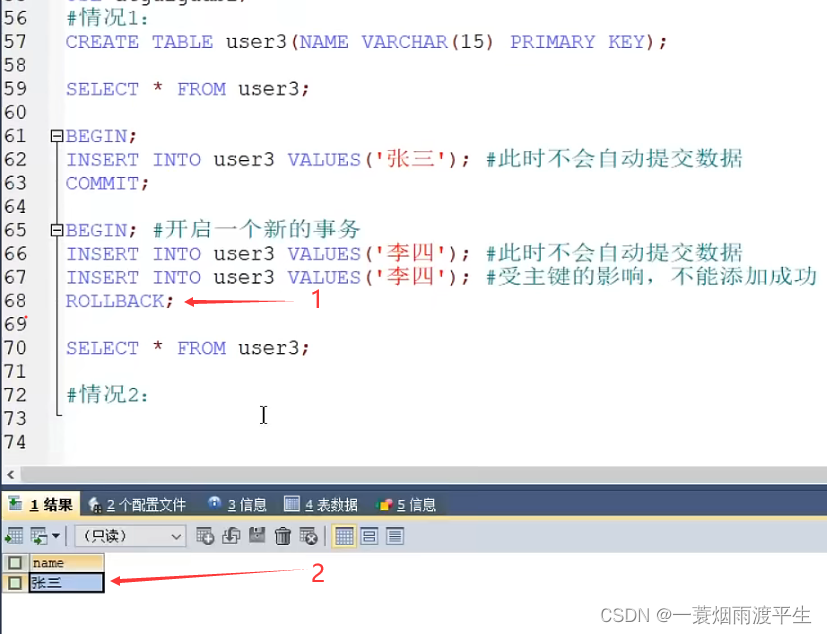
Understanding of transactions in MySQL
C#/VB.NET 给PDF文档添加文本/图像水印

Fiori 应用通过 Adaptation Project 的增强方式分享

“信任机器”为发展赋能
随机推荐
C#/VB. Net to add text / image watermarks to PDF documents
map容器
恶意软件反向关闭EDR的原理、测试和反制思考
MySQL MHA high availability configuration and failover
[daily training] 66 add one-tenth
Favorite transaction code management tool in SAP GUI
阿洛迷茫后的思考
Measurement of reference loop gain and phase margin
nn. Parameter] pytoch feature fusion adaptive weight setting (learnable weight use)
【JetCache】JetCache的使用方法与步骤
MySQL中对于索引的理解
MySQL view exercise
友善串口助手使用教程_友善串口调试助手怎么进行配置-友善串口调试助手使用教程…
Two schemes of transforming the heat map of human posture estimation into coordinate points
Tourism Management System
[literacy] deep / shallow, local / global features in machine learning image processing
Kubernetes创建Service访问Pod
使用 EMQX Cloud 实现物联网设备一机一密验证
Pytorch nn. functional. Simple understanding and usage of unfold()
[C language] detailed explanation of malloc function [easy to understand]