当前位置:网站首页>SAML2.0 notes (I)
SAML2.0 notes (I)
2022-07-02 03:09:00 【CoffeeAndIce】
List of articles
One 、 Preface
On the whole, the information on the Internet is too utilitarian , A glimpse without knowing the whole body . It is difficult for people to understand , In fact, it is a very normal way of docking , The chaos of materials has led to a surge in learning costs , It shouldn't be . In order not to step on the pit again ,markdown!!
About two chapters are used to describe
Chapter one : Understand the basic concept and corresponding docking mode and brief scheme
Chapter II : be based on java The code gives a summary of three basic working modes and possible errors in the middle of the process in the form of examples
Two 、 Get to know the concept
On the whole, it is a way to encrypt data and transmission process content by using certificate public-private key encryption and decryption , The only thing I use now is SSO.
1、SP & IDP The concept of
Service Provider(SP): Entities that provide formal business services to users , Usually you need to authenticate the identity of a user ;
Real service provider Entity , For example, provide interaction , Provide business interface
Identity Provider(IDP): Provide user identification , Ensure that the user is the identity they claim ;
Similar to authentication authorization services, it's good to understand
2、 Understanding metadata
Generate IDP Metadata: https://www.samltool.com/idp_metadata.phpGenerate SP Metadata: https://www.samltool.com/sp_metadata.php
The example is based on the local environment , So take local ip+ Private certificates are combined as instructions
2.1 IDP MetaData
The following is the basis
Catalog 2.4 certificateThe basic metadata formed
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2022-06-23T02:54:04Z" cacheDuration="PT1656384844S" entityID="https://coffeeandice/demo/idp">
<md:IDPSSODescriptor WantAuthnRequestsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIICYjCCAcugAwIBAgIBADANBgkqhkiG9w0BAQ0FADBOMQswCQYDVQQGEwJ1czESMBAGA1UECAwJR3Vhbmdkb25nMRQwEgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UEAwwMY29mZmVlYW5kaWNlMB4XDTIyMDYyMTAyMzgxNloXDTIzMDYyMTAyMzgxNlowTjELMAkGA1UEBhMCdXMxEjAQBgNVBAgMCUd1YW5nZG9uZzEUMBIGA1UECgwLZGVsYXlub21vcmUxFTATBgNVBAMMDGNvZmZlZWFuZGljZTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA7f1NEx2PSPlwU0GCAUFIeUq3WRKRaRQwlprKJ1STRuC54v9SlG404H1vI5JNRYOZ1wmMPh2YuCuWQW0VrJqOJTMXGvXpKzktYUzCB+LhcSGpe2SLheaivb/npkb73Kh9XbdtHVTK7a1rZySo0QovCresVnpxiPbZiazHEsMET3cCAwEAAaNQME4wHQYDVR0OBBYEFBjIdQPNJGwwpG5txEz8U9PGVHX7MB8GA1UdIwQYMBaAFBjIdQPNJGwwpG5txEz8U9PGVHX7MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQENBQADgYEAQEpTrrbdyZ8RBDWBQ3HKDzmF23VhXk/6SR3kUNy4qGkP0i/M9iujVvoOG7yEuZb1d178HrZjG/x7mQsXSAS3DzBwOrZKuUq5s8fdxtG93VgkeSKkN9nyaC7WkePNR25CN5PY8v1SblY0aIfdCEbdMBW6G/QLQjVI726UVhqBvMI=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIICYjCCAcugAwIBAgIBADANBgkqhkiG9w0BAQ0FADBOMQswCQYDVQQGEwJ1czESMBAGA1UECAwJR3Vhbmdkb25nMRQwEgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UEAwwMY29mZmVlYW5kaWNlMB4XDTIyMDYyMTAyMzgxNloXDTIzMDYyMTAyMzgxNlowTjELMAkGA1UEBhMCdXMxEjAQBgNVBAgMCUd1YW5nZG9uZzEUMBIGA1UECgwLZGVsYXlub21vcmUxFTATBgNVBAMMDGNvZmZlZWFuZGljZTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA7f1NEx2PSPlwU0GCAUFIeUq3WRKRaRQwlprKJ1STRuC54v9SlG404H1vI5JNRYOZ1wmMPh2YuCuWQW0VrJqOJTMXGvXpKzktYUzCB+LhcSGpe2SLheaivb/npkb73Kh9XbdtHVTK7a1rZySo0QovCresVnpxiPbZiazHEsMET3cCAwEAAaNQME4wHQYDVR0OBBYEFBjIdQPNJGwwpG5txEz8U9PGVHX7MB8GA1UdIwQYMBaAFBjIdQPNJGwwpG5txEz8U9PGVHX7MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQENBQADgYEAQEpTrrbdyZ8RBDWBQ3HKDzmF23VhXk/6SR3kUNy4qGkP0i/M9iujVvoOG7yEuZb1d178HrZjG/x7mQsXSAS3DzBwOrZKuUq5s8fdxtG93VgkeSKkN9nyaC7WkePNR25CN5PY8v1SblY0aIfdCEbdMBW6G/QLQjVI726UVhqBvMI=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/"/>
</md:IDPSSODescriptor>
</md:EntityDescriptor>
2.1.1 SingleLogoutService
As the name suggests, log out of the endpoint , You can usually consider
Location Correspondingurl by '/' ending:
Corresponding request address :https://coffeeandice/idp/sso/SingleLogoutService
Location Correspondingurl Not '/' ending :
Corresponding request address :https://coffeeandice/idp/sso/logout
<!-- With '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/"/>
<!-- Not '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/logout"/>
2.1.2 SingleSignOnService
As the name suggests, log in to the endpoint , You can usually consider
Location Correspondingurl by '/' ending:
Corresponding request address :https://coffeeandice/idp/sso/SingleSignOnService
Location Correspondingurl Not '/' ending :
Corresponding request address :https://coffeeandice/idp/sso/signon
<!-- With '/' ending -->
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/"/>
<!-- Not '/' ending -->
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/idp/sso/signon"/>
2.2 SP MetaData
The following is the basis
Catalog 2.4 certificateThe basic metadata formed
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2022-06-23T05:49:54Z" cacheDuration="PT604800S" entityID="https://coffeeandice/demo/sp">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="false" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIICYjCCAcugAwIBAgIBADANBgkqhkiG9w0BAQ0FADBOMQswCQYDVQQGEwJ1czESMBAGA1UECAwJR3Vhbmdkb25nMRQwEgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UEAwwMY29mZmVlYW5kaWNlMB4XDTIyMDYyMTAyMzgxNloXDTIzMDYyMTAyMzgxNlowTjELMAkGA1UEBhMCdXMxEjAQBgNVBAgMCUd1YW5nZG9uZzEUMBIGA1UECgwLZGVsYXlub21vcmUxFTATBgNVBAMMDGNvZmZlZWFuZGljZTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA7f1NEx2PSPlwU0GCAUFIeUq3WRKRaRQwlprKJ1STRuC54v9SlG404H1vI5JNRYOZ1wmMPh2YuCuWQW0VrJqOJTMXGvXpKzktYUzCB+LhcSGpe2SLheaivb/npkb73Kh9XbdtHVTK7a1rZySo0QovCresVnpxiPbZiazHEsMET3cCAwEAAaNQME4wHQYDVR0OBBYEFBjIdQPNJGwwpG5txEz8U9PGVHX7MB8GA1UdIwQYMBaAFBjIdQPNJGwwpG5txEz8U9PGVHX7MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQENBQADgYEAQEpTrrbdyZ8RBDWBQ3HKDzmF23VhXk/6SR3kUNy4qGkP0i/M9iujVvoOG7yEuZb1d178HrZjG/x7mQsXSAS3DzBwOrZKuUq5s8fdxtG93VgkeSKkN9nyaC7WkePNR25CN5PY8v1SblY0aIfdCEbdMBW6G/QLQjVI726UVhqBvMI=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIICYjCCAcugAwIBAgIBADANBgkqhkiG9w0BAQ0FADBOMQswCQYDVQQGEwJ1czESMBAGA1UECAwJR3Vhbmdkb25nMRQwEgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UEAwwMY29mZmVlYW5kaWNlMB4XDTIyMDYyMTAyMzgxNloXDTIzMDYyMTAyMzgxNlowTjELMAkGA1UEBhMCdXMxEjAQBgNVBAgMCUd1YW5nZG9uZzEUMBIGA1UECgwLZGVsYXlub21vcmUxFTATBgNVBAMMDGNvZmZlZWFuZGljZTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA7f1NEx2PSPlwU0GCAUFIeUq3WRKRaRQwlprKJ1STRuC54v9SlG404H1vI5JNRYOZ1wmMPh2YuCuWQW0VrJqOJTMXGvXpKzktYUzCB+LhcSGpe2SLheaivb/npkb73Kh9XbdtHVTK7a1rZySo0QovCresVnpxiPbZiazHEsMET3cCAwEAAaNQME4wHQYDVR0OBBYEFBjIdQPNJGwwpG5txEz8U9PGVHX7MB8GA1UdIwQYMBaAFBjIdQPNJGwwpG5txEz8U9PGVHX7MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQENBQADgYEAQEpTrrbdyZ8RBDWBQ3HKDzmF23VhXk/6SR3kUNy4qGkP0i/M9iujVvoOG7yEuZb1d178HrZjG/x7mQsXSAS3DzBwOrZKuUq5s8fdxtG93VgkeSKkN9nyaC7WkePNR25CN5PY8v1SblY0aIfdCEbdMBW6G/QLQjVI726UVhqBvMI=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/sp/logout"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://coffeeandice/sp/consumer" index="1"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>
2.2.1 SingleLogoutService
As the name suggests, log out of the endpoint , You can usually consider
Location Correspondingurl by '/' ending:
Corresponding request address :https://coffeeandice/sp/SingleLogoutService
Location Correspondingurl Not '/' ending :
Corresponding request address :https://coffeeandice/sp/logoutHere and IDP The difference is
In fact, we call IDP Exit login address , then IDP Just notify our exit login endpoint
<!-- With '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/sp/"/>
<!-- Not '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/sp/logout"/>
2.2.2 AssertionConsumerService
Response endpoint , It is usually a delivery login SSO The response address after , be used for SP Judge the login status response .
Tips: stayartifact PatternNext , You still need to wait for sendingArtifactResolveTo get the response message
Location Corresponding
url by '/' ending:
Corresponding request address :https://coffeeandice/sp/SingleLogoutService
Location Correspondingurl Not '/' ending :
Corresponding request address :https://coffeeandice/sp/consumer
<!-- With '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/sp/"/>
<!-- Not '/' ending -->
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://coffeeandice/sp/consumer"/>
2.3 General node
2.3.1 EntityId
Example :
https://coffeeandice/demo/trust
The overall requirement is to http or https start , Accessibility is not required , Exist only as a unique identification
Recommended format :
1、 Can be https Relative norm , Although there is no need to force
2、 Only use the form of domain name plus directory , It is suggested to distinguish sp and idp, Example trust It can be changed to sp or idp
3、 The suffix no longer needs to be ’/' ending
Other recommendations : https://spaces.at.internet2.edu/display/federation/saml-metadata-entityid
2.3.2 KeyDescriptor
This refers to the certificate used for encryption and decryption during verification , Corresponding use They will say
signingAndencryptionexplain .
Its value usually corresponds to2.4.2 cert, Used to encrypt the ratio , When IDP Turn onWantAuthnRequestsSignedAfter the configuration .
if IDP/SP Turn on WantAuthnRequestsSigned The configuration is set to true
Metadata is usually more dom Elements ds:DigestValue And ds:SignatureValue
2.3.3 NameIDFormat
in the light of
NameIDPolicy, When used for interaction, it can support the returned verification topic . It's usually SP Metadata and IDP MetadataJointly supported by anyNameID` Strategy .It usually exists 8 Patterns :( In most cases, we just need 1、2、3 that will do )
1、 No schema defined :Unspecifiedurn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
2、 Email address mode :Email Addressurn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
3、 In the certificate subject Name pattern :X.509 Subject Nameurn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName
4、windows Domain name mode :Windows Domain Qualified Nameurn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName
5、Kerberos Principal name pattern :Kerberos Principal Nameurn:oasis:names:tc:SAML:2.0:nameid-format:kerberos
6、 Entity identifier pattern ( Usually refers to entityid):Entity Identifierurn:oasis:names:tc:SAML:2.0:nameid-format:entity
7、 Persistent identifier pattern :Persistent Identifierurn:oasis:names:tc:SAML:2.0:nameid-format:persistent
8、 Temporary identifier mode :Transient Identifierurn:oasis:names:tc:SAML:2.0:nameid-format:transient
2.4 Example use certificate
2.4.1 private key
# private key
-----BEGIN PRIVATE KEY-----
MIICdQIBADANBgkqhkiG9w0BAQEFAASCAl8wggJbAgEAAoGBAO39TRMdj0j5cFNB
ggFBSHlKt1kSkWkUMJaayidUk0bgueL/UpRuNOB9byOSTUWDmdcJjD4dmLgrlkFt
FayajiUzFxr16Ss5LWFMwgfi4XEhqXtki4Xmor2/56ZG+9yofV23bR1Uyu2ta2ck
qNEKLwq3rFZ6cYj22YmsxxLDBE93AgMBAAECgYAHUTVwdAU2yiyQ8r+riDVRPWHb
xD1iTLOdvc6fXPNWR4yPlSgV1jmb+V9UaagkjgJJ4UpFkqVibDyncFItR2c9YGFw
wj2iEBnSc3fK8tcysRhb2zzjqP0DYRWusrxlqkx+yVQcIVSgNA3J7SqWsKuu6Vbh
54QEQGqwgz1JgUSMSQJBAPtyXNEP3K+O2g8ja3xtkeNhcrDDKRLBIhDmrmxWZJJ9
i9F3bh/OeN5dJhx5qibEGFrvYZWAqn8l14cEK3CiWiMCQQDyTI3oEg7rttnpWzkY
jdlco6Qh1npRcgOYgjPk7NGQ1WAWH63A5WSWZMaQcLn525BHa52P9NZIERWia4cT
nVidAkA7NE9Ebm6w63rOi7F4R7hNCJnfouQd5VmnDxnMqn7duy/brzo/xPbSrK4X
kFIO9Kcjai/Y6sW6UGeyA7pSt/dvAkAtUNYFfkMeIJ+WvkHqbrUlV1GeJn/P9bPo
dQmBmi0DmnSTDq+vcPekDQr5/qs5qK/OO7lHMDJXXiKest+bcoUdAkB8pV+HuKHi
YXkE1tgb4jSN0fxEVikidp05RF3FVOFqvS3DvIIEtQtvfIduQ4nAY28+iy1st/lZ
Dp7VsGJjTQnz
-----END PRIVATE KEY-----
2.4.2 x509.cert ( Certificate in the usual sense )
# x509.cert
-----BEGIN CERTIFICATE-----
MIICYjCCAcugAwIBAgIBADANBgkqhkiG9w0BAQ0FADBOMQswCQYDVQQGEwJ1czES
MBAGA1UECAwJR3Vhbmdkb25nMRQwEgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UE
AwwMY29mZmVlYW5kaWNlMB4XDTIyMDYyMTAyMzgxNloXDTIzMDYyMTAyMzgxNlow
TjELMAkGA1UEBhMCdXMxEjAQBgNVBAgMCUd1YW5nZG9uZzEUMBIGA1UECgwLZGVs
YXlub21vcmUxFTATBgNVBAMMDGNvZmZlZWFuZGljZTCBnzANBgkqhkiG9w0BAQEF
AAOBjQAwgYkCgYEA7f1NEx2PSPlwU0GCAUFIeUq3WRKRaRQwlprKJ1STRuC54v9S
lG404H1vI5JNRYOZ1wmMPh2YuCuWQW0VrJqOJTMXGvXpKzktYUzCB+LhcSGpe2SL
heaivb/npkb73Kh9XbdtHVTK7a1rZySo0QovCresVnpxiPbZiazHEsMET3cCAwEA
AaNQME4wHQYDVR0OBBYEFBjIdQPNJGwwpG5txEz8U9PGVHX7MB8GA1UdIwQYMBaA
FBjIdQPNJGwwpG5txEz8U9PGVHX7MAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEN
BQADgYEAQEpTrrbdyZ8RBDWBQ3HKDzmF23VhXk/6SR3kUNy4qGkP0i/M9iujVvoO
G7yEuZb1d178HrZjG/x7mQsXSAS3DzBwOrZKuUq5s8fdxtG93VgkeSKkN9nyaC7W
kePNR25CN5PY8v1SblY0aIfdCEbdMBW6G/QLQjVI726UVhqBvMI=
-----END CERTIFICATE-----
2.4.3 CSR
-----BEGIN CERTIFICATE REQUEST-----
MIIBjTCB9wIBADBOMQswCQYDVQQGEwJ1czESMBAGA1UECAwJR3Vhbmdkb25nMRQw
EgYDVQQKDAtkZWxheW5vbW9yZTEVMBMGA1UEAwwMY29mZmVlYW5kaWNlMIGfMA0G
CSqGSIb3DQEBAQUAA4GNADCBiQKBgQDt/U0THY9I+XBTQYIBQUh5SrdZEpFpFDCW
msonVJNG4Lni/1KUbjTgfW8jkk1Fg5nXCYw+HZi4K5ZBbRWsmo4lMxca9ekrOS1h
TMIH4uFxIal7ZIuF5qK9v+emRvvcqH1dt20dVMrtrWtnJKjRCi8Kt6xWenGI9tmJ
rMcSwwRPdwIDAQABoAAwDQYJKoZIhvcNAQENBQADgYEAZSuIubccAOLVf99u7Djo
K5glaXRo9TMl6EOaVlJLWf07s+FrtDwJr9g/SuYssXptpnzhETg6yQIMpubHxkuz
JFFA/GUeN+WOC9BXPKR1HE5CyxKTLYFhzmTcZ4yXh0b32COrQgeP8xEYz4Cmvt1z
ontjVJM5FdrvpdqP2AAn2DI=
-----END CERTIFICATE REQUEST-----
3、 Common working modes
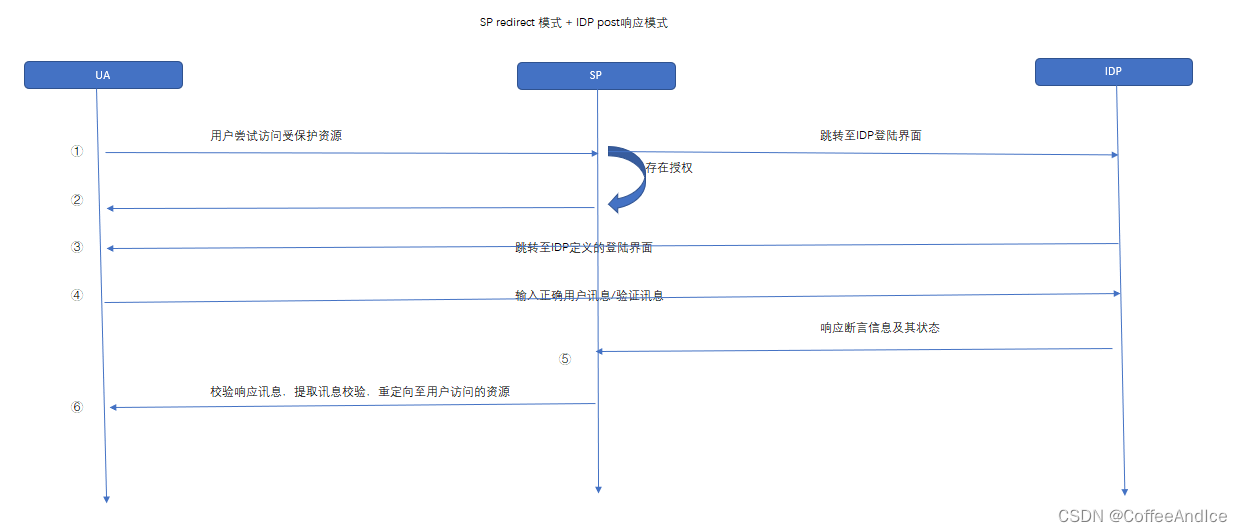
3.1 SP redirect Pattern + IDP post Response patterns
On the whole : Account messages are sent by IDP Control , Less SP Possibility of holding information
SP First, determine whether the user has a login identifier
① There is : Directly read the identifier login
② non-existent :
Step 1: be based onSP MetadataGenerate SP Fang SAMLRequest Content , Used to redirect to IDP Of SSO The login address , wait for IDP Redirect to its login interface
Step 2: After the login authorization is confirmed , be based onSP Metadatautilize post Way back SAMLResponse Content response results
3.2 SP post Pattern + IDP post Pattern
On the whole : Relative trust SP Fang , There is the possibility of information disclosure
SP It is also used to judge whether the user has a login identifier
① There is : Directly read the identifier login
② non-existent :
Step 1:SP You can define the login interface , For customer login , Then send the form with the content to IDP
Setp 2: After the login authorization is confirmed , be based onSP Metadatautilize post Way back SAMLResponse Content response results

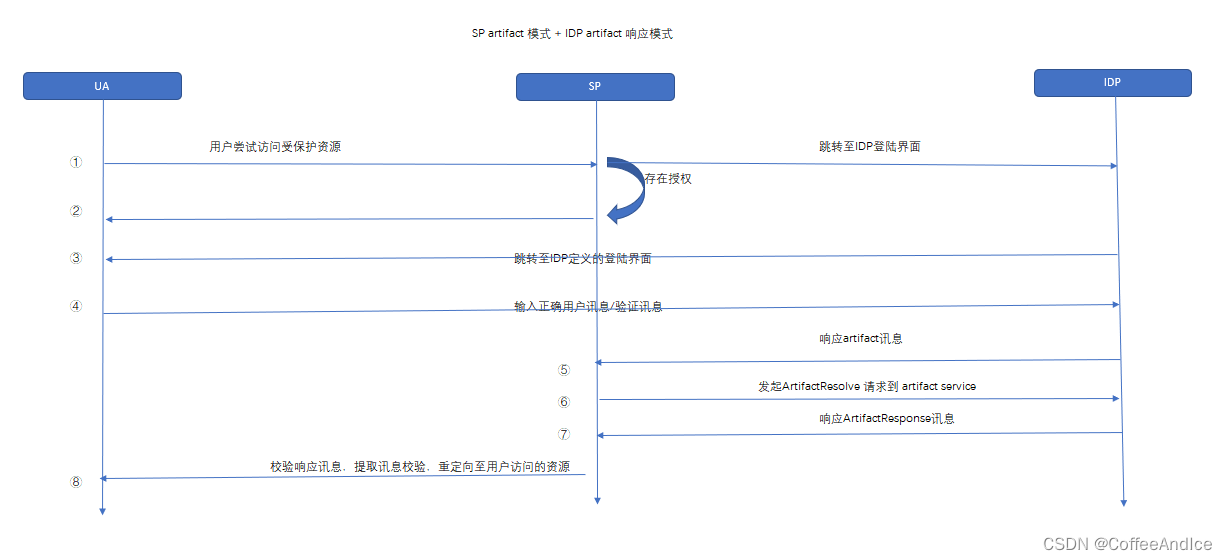
3.3 SP redirect artifact + IDP redirect artifact
On the whole : Similar to the first way , But the way of transmitting messages is usually soap, More secure ( It can also be done without ), Need to open artifact service service
SP Or judge whether the user has a login identifier
① There is : Directly read the identifier login
② non-existent :
Step 1: be based onSP MetadataGenerate SP Fang SAMLRequest Content , Used to redirect to IDP Of SSO The login address , wait for IDP Redirect to its login interface
Step 2: After login authorization ,IDP utilize redirect Means of transmission artifact to SP
Step 3:SP Accept to artifact One after the combination and splicingArtifactResolvetowardsIDP MetadataAs defined inartifact serviceThe endpoint sends a request , Waiting to returnArtifactResponse
3、 ... and 、 Other content messages
1、OpenSAML Select the version problem
because OpenSAML 4.0 Only support JDK11, Use 3.x The version is JDK 8 Final solution .
2、 Why choose OpenSAML
We don't have to rebuild the wheel , Use
OpenSamlIt's convenient for us to SAML Most of the agreement , The basis of The third docking mode is at least supported .
3、MetaData Middle key pair generation suggestions
3.1 Recommended domain name DV
You can also use OV client , For details, please refer to the customer's situation ( Because the self signed certificate issuer and signature Basically consistent )
3.2 Key length selection (2048)
It is recommended to use 2048, actually 1024 It's not safe , At the same time, if you need to use an agent ( for example nginx etc. ), be 1024 Will not be openssl Allowed to pass through
4、 Connect the front content
Generated by the corresponding certificate jks Should be IDP Provide
orSP Provided by Party after self generation cert Certificate to IDP Fang
边栏推荐
- 流线线使用阻塞还是非阻塞
- After marriage
- 【JVM】创建对象的流程详解
- Framing in data transmission
- QT environment generates dump to solve abnormal crash
- 多线程查询,效率翻倍
- /silicosis/geo/GSE184854_ scRNA-seq_ mouse_ lung_ ccr2/GSE184854_ RAW/GSM5598265_ matrix_ inflection_ demult
- Après le mariage
- Docker安装canal、mysql进行简单测试与实现redis和mysql缓存一致性
- [staff] pitch representation (treble clef | C3 60 ~ B3 71 pitch representation | C4 72 pitch representation | C5 84 pitch representation)
猜你喜欢
Formatting logic of SAP ui5 currency amount display

After marriage

AcWing 245. Can you answer these questions (line segment tree)

Use usedeferredvalue for asynchronous rendering

Xiaomi, a young engineer, was just going to make soy sauce
QT implementation interface jump

Pychart creates new projects & loads faster & fonts larger & changes appearance
C reflection practice
连通块模板及变式(共4题)

数据传输中的成帧
随机推荐
Qualcomm platform wifi-- WPA_ supplicant issue
Render header usage of El table
2022 hoisting machinery command examination paper and summary of hoisting machinery command examination
QT uses sqllite
数据传输中的成帧
QT environment generates dump to solve abnormal crash
STM32__05—PWM控制直流电机
2022-2028 global encryption software industry research and trend analysis report
JS introduction < 1 >
Qualcomm platform WiFi -- P2P issue (2)
Gradle notes
Framing in data transmission
Verilog 过程连续赋值
Named block Verilog
自定义组件的 v-model
MVVM and MVC
el-table的render-header用法
GB/T-2423.xx 环境试验文件,整理包括了最新的文件里面
Redis cluster
Verilog 过程赋值 区别 详解