当前位置:网站首页>[technology development-24]: characteristics of existing IOT communication technology
[technology development-24]: characteristics of existing IOT communication technology
2022-07-03 13:46:00 【Silicon based workshop of slow fire rock sugar】
Preface :
The Internet of things (Internet of Things, abbreviation IoT) Means through various information sensor 、 RFID Technology 、 Global positioning system 、 Infrared sensors 、 Laser scanner and other devices and technologies , Real time acquisition any monitoring required 、 Connect 、 An interactive object or process , Gather the sound 、 light 、 heat 、 electric 、 Dynamics 、 chemical 、 biological 、 Location and other information needed , Through all kinds of possible network access , Realization and thing 、 The ubiquitous connection between things and people , Realize the control of items and processes Intelligent perception 、 Identify and manage .
The Internet of things is based on Internet 、 Traditional telecommunication network Information carrier , It allows all ordinary physical objects that can be independently addressed to form an interconnected network .
The Internet of things ( IoT ,Internet of things ) namely “ The Internet of things ”, It's an extension of the Internet , A huge network is formed by combining all kinds of information sensing devices with the network , Any time 、 Any place , people 、 machine 、 The interconnection of things .
The Internet of things is an important part of the new generation of information technology ,IT The industry is also called : Pan interconnection , Signification Things are connected , All things are connected . thus ,“ The Internet of things is the Internet connected with things ”. This has two meanings : First of all , Internet of things Core and foundation It's still the Internet , It's an extension and expansion of the Internet ; second , Its Client extensions and extensions here we are Anything and things Between , Information exchange and communication . therefore , The Internet of things is defined by RFID 、 Infrared sensors 、 Global positioning system 、 Laser scanner And other information sensing equipment , According to the agreement , Connect anything to the Internet , Information exchange and communication , In order to realize the intelligent identification of objects 、 location 、 track 、 A network of monitoring and management .
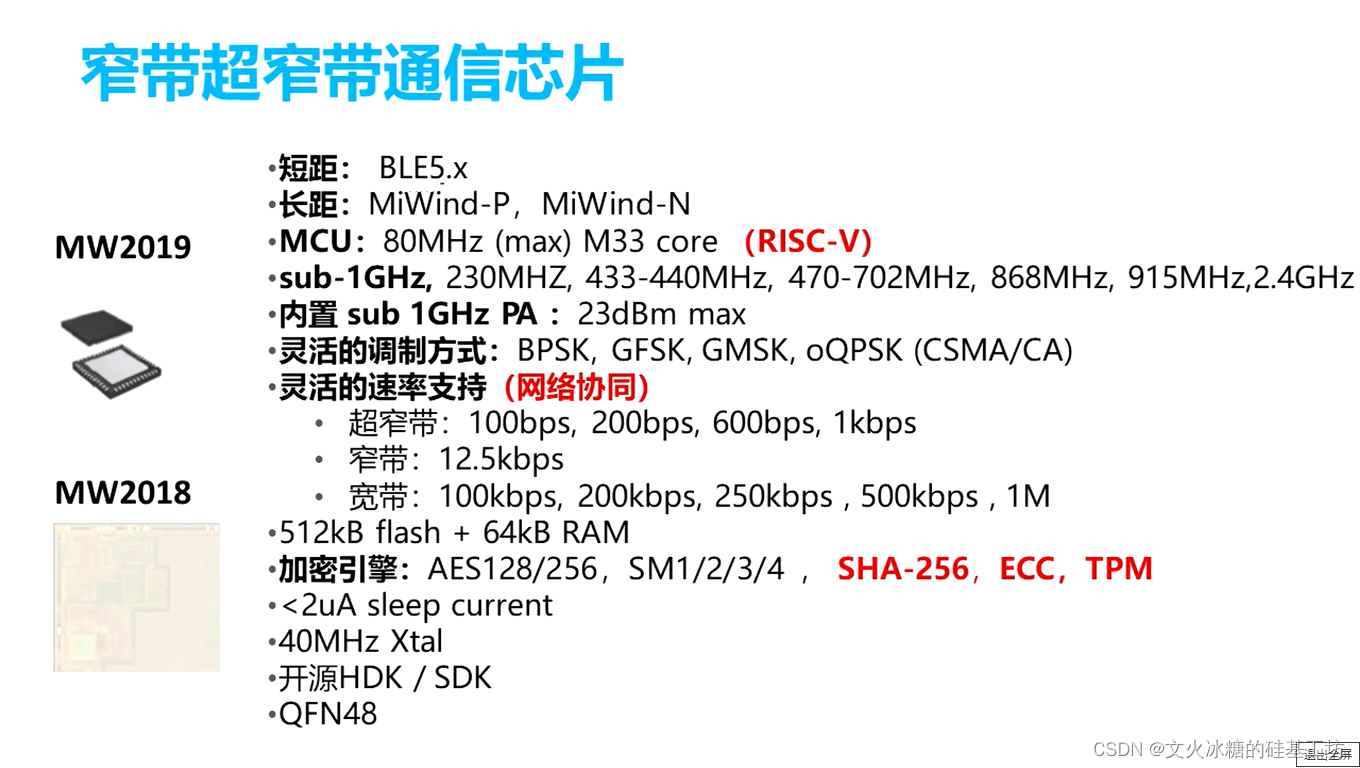
Key technologies include : RFID Technology 、 Sensor network 、M2M System framework 、 Cloud computing








边栏推荐
- Error running 'application' in idea running: the solution of command line is too long
- [sort] bucket sort
- 掌握Cypress命令行选项,是真正掌握Cypress的基础
- 服务器硬盘冷迁移后网卡无法启动问题
- Annotation and reflection
- Servlet
- Introduction to the implementation principle of rxjs observable filter operator
- 今日睡眠质量记录77分
- This math book, which has been written by senior ml researchers for 7 years, is available in free electronic version
- JS 将伪数组转换成数组
猜你喜欢

Kivy tutorial how to automatically load kV files
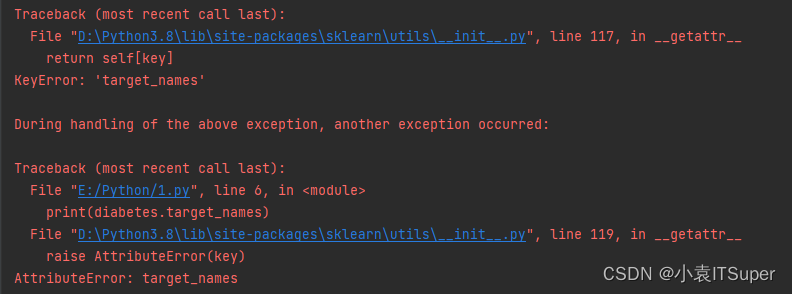
Resolved (error in viewing data information in machine learning) attributeerror: target_ names

道路建设问题
The latest BSC can pay dividends. Any B usdt Shib eth dividend destruction marketing can

AI 考高数得分 81,网友:AI 模型也免不了“内卷”!

Road construction issues

今日睡眠质量记录77分
MyCms 自媒体商城 v3.4.1 发布,使用手册更新
KEIL5出现中文字体乱码的解决方法

Annotation and reflection
随机推荐
Detailed explanation of multithreading
IBEM mathematical formula detection data set
RichView TRVStyle ListStyle 列表样式(项目符号编号)
使用tensorflow进行完整的DNN深度神经网络CNN训练完成图片识别案例
JS 将伪数组转换成数组
Resolved (error in viewing data information in machine learning) attributeerror: target_ names
Kivy tutorial how to load kV file design interface by string (tutorial includes source code)
树的深入和广度优先遍历(不考虑二叉树)
[redis] cache warm-up, cache avalanche and cache breakdown
父亲和篮球
[how to earn a million passive income]
json序列化时案例总结
Brief analysis of tensorboard visual processing cases
使用Tensorflow进行完整的深度神经网络CNN训练完成图片识别案例2
MyCms 自媒体商城 v3.4.1 发布,使用手册更新
untiy世界边缘的物体阴影闪动,靠近远点的物体阴影正常
又一个行业被中国芯片打破空白,难怪美国模拟芯片龙头降价抛售了
Start signing up CCF C ³- [email protected] chianxin: Perspective of Russian Ukrainian cyber war - Security confrontation and sanctions g
[sort] bucket sort
Shell timing script, starting from 0, CSV format data is regularly imported into PostgreSQL database shell script example