当前位置:网站首页>Copy mode DMA
Copy mode DMA
2022-07-05 16:53:00 【Four seasons sail】
1. DMA Principle and implementation of
DMA The principle is CPU Tell DMA, Include source address , The destination address and the length to be migrated , Then start DMA equipment ,DMA After the device receives the command , Just complete the corresponding operation , Finally, give feedback to the boss through interruption CPU, end .
In the realization of DMA When transmitting , yes DMA The controller controls the bus , in other words , There will be a problem of transfer of control , Of course we do , The largest in the computer BOSS Namely CPU, This DMA The bus control temporarily in charge is also CPU Given to , stay DMA After transmission , Will be notified by interruption CPU Take back control of the bus .
2. DMA Transmission process
A complete DMA The transmission process has to go through DMA request 、DMA Respond to 、DMA transmission 、DMA End these four stages .
DMA request :CPU Yes DMA Controller initialization , And to I/O Interface sends operation commands ,I/O Interface proposal DMA request
DMA Respond to :DMA The controller is right DMA Request discrimination priority and mask bit , Make a bus request to the bus arbitration logic , When CPU After the current bus cycle is completed, the bus control can be released . here , Bus arbitration logic outputs bus response , Express DMA Already in place , adopt DMA Controller notification I/O Interface start DMA transmission .
DMA transmission : stay DMA Under the guidance of the controller , Data transfer between memory and peripherals , There is no need to CPU Participation
DMA end : When the given operation is completed ,DMA The controller releases bus control , And to I/O The interface sends an end signal , When I/O After the interface receives the end signal , On the one hand, stop I/O The work of the equipment , On the other hand CPU Make an interrupt request , send CPU Never intervene in the state of liberation , And perform a period of inspection DMA Code for the correctness of transmission operation . Finally, continue to execute the original program with the result and status of this operation .

Peripherals can be used DMA Move data . Such as MMC, When it receives data , Will store the data in its own register , Either through CPU Loop through the registers to get these data ( Take up at this time CPU Time ); You can also use DMA Move the data of register to memory , When a certain amount is moved , notice CPU, then CPU Then read it from memory at one time (DMA In the process of moving ,CPU You can do other things ).
DMA Working hours , from DMA The controller sends address and control signals to memory , Make address changes , Make statistics on the transmitted data , And notify in the form of interruption CPU Data transmission completed .
3. DMA Resulting problems
DMA It will not only improve efficiency , Again , It also brings some problems , The most obvious problem is cache consistency . Imagine , modern CPU They all have their own L1 cache 、 L2 cache or even L3 cache , When CPU When accessing an address in memory , For now, write the new value into the cache , But the data in external memory is not updated , Suppose this happens DMA What is requested and operated is the memory address that is updated in the cache but not updated in the external memory , such DMA What you read is the non latest data ; same , If the external device passes DMA Write the new value to memory , however CPU Access the data in the actual cache , This will also result in not getting the latest data .
In order to do it correctly DMA operation , Necessary Cache operation ,Cache The operation of is mainly divided into invalidate( To void ) and writeback( Write back ), Sometimes they are used together . If DMA Used Cache, that Cache Consistency must be considered , The simplest solution is to prohibit DMA Of the target address range Cache function , But this will sacrifice some performance . therefore , stay DMA Whether to use cache On the issue of , According to DMA The expected retention time of the buffer is determined .DMA Be divided into : Uniformity DMA Mapping and streaming DMA mapping .
4. Solve cache consistency
Uniformity DMA , Because it adopts a section reserved by the system DMA Memory is used for DMA operation , This section of kernel has been reserved in the system startup stage , stay DMA In the process of memory application , You can directly disable this section of the memory reserved cache . Start with a ioremap_nocache Mapping , And then call the function. dma_cache_wback_inv Ensure that the cache has been flushed in place , When this memory is used later, there is no L2 cache ;
streaming DMA , Cache cannot be directly disabled , Because streaming DMA You can use any address range in the system ,CPU Never disable caching of all address spaces in the system , This is not scientific. , In order to achieve cache consistency , streaming DMA The cache needs to be invalidated constantly , tell CPU This cache is not trusted , It must be retrieved from memory . Uniformity DMA That is to disable the cache directly , And flow DMA Is to refresh the cache invalidation .
5. DMA channels
One DMA controller Can be done at the same time DMA The number of transmissions is limited , This is called DMA channels. It's just a logical concept , Because in view of the conflict of bus access , And memory consistency considerations , these Channels It is impossible to really work in parallel , Only time-sharing multiplexing ,DMA The controller acts as an arbiter . Since it is time-sharing multiplexing , Then we can also be based on a certain physics Channel, Abstract out multiple virtual Channel, The software is responsible for arbitration , To decide which virtual at a certain moment Channel To use physics Channel.
6. DMA request line
DMA Transmission is made by CPU Sponsored :CPU tell DMA controller , Help will xxx Local data moved to xxx place .CPU After giving the order , Just do something else . and DMA controller , Besides being responsible for how to move , Also decide when to start data handling .
because CPU launch DMA During transmission , I don't know whether the current transmission conditions are available , for example source Whether the equipment has data 、dest The equipment FIFO Are you free... Etc . Only the device knows when to start transmission , Therefore need DMA Transmission equipment and DMA Between controllers , There will be several physical connections ( namely DMA request,DRQ), Used to inform DMA The controller can start transmission .
7. To write DMA The general steps of equipment driving are as follows
/* 1. apply DMA passageway */
struct dma_chan *dma_request_channel(dma_cap_mask_t mask, dma_filter_fn filter_fn, void *filter_param);
/* 2. DMA Channel configuration , Can pass config Structure settings DMA The width of the passage 、 Data transmission broadband 、 Source address, destination address and other information . */
int dmaengine_slave_config(struct dma_chan *chan, struct dma_slave_config *config);
/* 3. Get the transport descriptor */
adopt device_prep_slave_sg() perhaps device_prep_dma_cyclic() perhaps device_prep_dma_memcpy() obtain desc, Then pass the callback function pointer to desc->callback
/* 4. Submit transmission */
call dmaengine_submit((struct dma_async_tx_descriptor *)desc), take desc Submitted to the DMA Waiting in line
/* 5. Start transmission */
dmaengine_issue_pending The call starts with the first descriptor . If DMA If the device driver has a callback function , It will be executed after the transmission is completed .8. DMA framework
stay drivers/dma Under the table of contents , There is one dmaengine.c file , The document is DMA The core of the framework , Provide registration down DMA host driver The interface of (dma_async_device_register), Provide operations up DMA The interface of ( apply DMA passageway 、 Start transmission, etc ).
边栏推荐
- 如何安装mysql
- 麻烦问下,DMS中使用Redis语法是以云数据库Redis社区版的命令为参考的嘛
- 为季前卡牌游戏 MotoGP Ignition Champions 做好准备!
- 【组队 PK 赛】本周任务已开启 | 答题挑战,夯实商品详情知识
- PHP 严格模式
- Win11如何给应用换图标?Win11给应用换图标的方法
- [deep learning] how does deep learning affect operations research?
- 帮忙看看是什么问题可以吗?[ERROR] Could not execute SQL stateme
- Learnopongl notes (II) - Lighting
- Accès aux données - intégration du cadre d'entité
猜你喜欢
【机器人坐标系第一讲】

【刷题篇】鹅厂文化衫问题
Domestic API management artifact used by the company
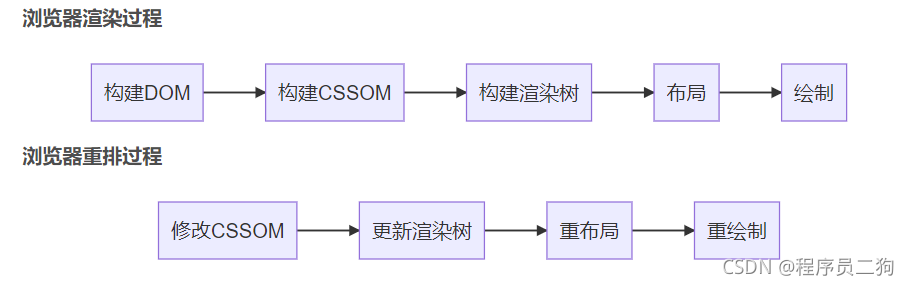
浏览器渲染原理以及重排与重绘
Games101 notes (II)

American chips are no longer proud, and Chinese chips have successfully won the first place in emerging fields
Solution of vant tabbar blocking content
Basic introduction to the control of the row component displaying its children in the horizontal array (tutorial includes source code)
解决CMakeList find_package找不到Qt5,找不到ECM
Jarvis OJ Webshell分析
随机推荐
File operation --i/o
composer安装报错:No composer.lock file present.
采用药丸屏的iPhone14或引发中国消费者的热烈抢购
Scratch colorful candied haws Electronic Society graphical programming scratch grade examination level 3 true questions and answers analysis June 2022
中间表是如何被消灭的?
Google Earth engine (GEE) -- a brief introduction to kernel kernel functions and gray level co-occurrence matrix
[echart] resize lodash to realize chart adaptation when window is zoomed
如何安装mysql
Flet教程之 11 Row组件在水平数组中显示其子项的控件 基础入门(教程含源码)
Flet教程之 12 Stack 重叠组建图文混合 基础入门(教程含源码)
养不起真猫,就用代码吸猫 -Unity 粒子实现画猫咪
[deep learning] [original] let yolov6-0.1.0 support the txt reading dataset mode of yolov5
Benji Banas membership pass holders' second quarter reward activities update list
Apple 已弃用 NavigationView,使用 NavigationStack 和 NavigationSplitView 实现 SwiftUI 导航
數據訪問 - EntityFramework集成
If you can't afford a real cat, you can use code to suck cats -unity particles to draw cats
Flet教程之 09 NavigationRail 基础入门(教程含源码)
HiEngine:可媲美本地的云原生内存数据库引擎
树莓派4b安装Pytorch1.11
【 brosser le titre 】 chemise culturelle de l'usine d'oies