当前位置:网站首页>Armv8-m (Cortex-M) TrustZone summary and introduction
Armv8-m (Cortex-M) TrustZone summary and introduction
2022-06-13 02:12:00 【Code changes the world CTW】
1、 brief introduction
First look at a software architecture diagram :

1.1、ARMV8-M Trustzone brief introduction
TrustZone The concept of technology is not new . The technology is already in Arm Cortex-A Series processors have been used for many years , And now it has been extended to cover Armv8-M processor .
At a higher level ,Armv8-M Of TrustZone The concept of technology is similar to Arm Cortex-A In the processor TrustZone technology . The processor has safe and unsafe States , Non secure software can only access non secure memory .Armv8-M The small energy-saving system is considered in the design . And Cortex-A In the processor TrustZone Different technology , Armv8-M Of Secure and Normal The world is Memory-based mapping Of , Conversion occurs automatically in exception handling code .
Armv8-M and Armv8-A Supported by the Trustzone Technologies differ in the following ways :
- Armv8-M Of TrustZone Technical support Multiple security entry points, And in the Cortex-A The processor TrustZone In technology ,Secure Monitor The handler is unique entry points.
- Execution can still handle non secure interrupts while in a safe state
In many microcontroller applications with real-time processing function , Deterministic behavior and low interrupt latency are important requirements . The ability to handle interrupt requests while running secure code is critical - By allowing register groups to be shared between safe and unsafe States ,Armv8-M The implemented power consumption can be similar to Armv6-M or Armv7-M
- Low overhead of state switching Allow secure and non secure software to interact frequently , This is common in the following cases . The security firmware contains software libraries , for example GUI Firmware or communication protocol stack

In possession of Armv8-M In the design of architecture security extension , Components that are critical to system security can be placed in a secure world . These key components include :
- Secure boot loader .
- Secret key .
- Flash programming support .
- High value assets( High value assets ).

Security (Trusted) And non safety (Non-trusted) Software can work together , However, non secure applications cannot directly access secure resources . contrary , Any right Secure Resources can be accessed through Secure Software provided API, these API Authentication can be implemented to determine if access to security services is allowed . Through this arrangement , Even if there are vulnerabilities in non secure applications , hackers
You can't attack the whole chip .
1.2、Armv8-M Trustzone Security requirements in the context
The word security can have many different meanings in embedded system design . In most embedded systems , Security may include, but is not limited to :
- Communication protection
This protection can prevent data transmission from being seen or blocked by unauthorized parties , And may include other technologies , For example, cryptography . - Data protection
This protection prevents unauthorized parties from accessing secret data stored in the device . - Firmware protection
This protection prevents on-chip firmware from being reverse engineered . - Operation protection
This protection prevents malicious intentional failures in critical operations . - Tamper Protection
In many security sensitive products , Tamper proof functionality is required to prevent the operation or protection mechanism of the device from being affected . Be overwritten .
TrustZone Technology can directly solve the following security requirements of embedded systems : - Data protection
Sensitive data can be stored in secure memory space , And can only be accessed by security software . Non secure software can only access secure API Providing services to non secure domains , And only after security checks or authentication . - Firmware protection
Preloaded firmware can be stored in secure memory , To prevent reverse engineering and malicious attacks .Armv8-M Of TrustZone Technology can also be used with additional protection technologies . for example , Device level readout protection , A technology commonly used in the industry today , Compatible Armv8-M Of TrustZone technology , Protect the finished firmware product . - Safe start
The secure boot mechanism gives you confidence in the platform , Because it always starts from safe memory .
TrustZone Technology can also be used with additional protection features used in advanced microcontrollers for the next generation (IoT) product . for example , Microcontrollers developed for Internet of things applications can contain a series of security functions .
TrustZone The use of technology helps to ensure that all these functions can only be used effectively entry point Of API To visit , The figure below shows :
By using TrustZone Technology to protect these security features , Designers can :
- Prevent untrusted applications from directly accessing security critical resources .
- Ensure that reprogramming is done only after verification and inspection Flash image .
- Prevent firmware from being reverse engineered .
- Store confidential information with software level protection
Security of wireless communication interface
In other application scenarios , For example, a wireless with a certified built-in radio stack SoC,TrustZone Technology can protect standardized operations , For example, wireless communication behavior .
TrustZone Technology ensures that customer-defined applications do not invalidate authentication , As shown in the figure below .
2、Trustzone Two extended security states
Trustzone Two security states under technology (Security State): Non-Secure State and Secure State.
stay TF-M It is also called : NSPE(NON-Secure Processing Environment) and SPE(Secure Processing Environment)
About reset
- If security extensions are implemented , Memory areas and other critical resources marked as safe are only available in PE Only when executed in a safe state can access
- If security extensions are implemented , It's in Cold reset and Warm reset when ,PE Will enter the Secure state
- If security extensions are implemented , It's in Cold reset and Warm reset when ,PE Will enter the NON-Secure state
About banked
After implementing security extensions , The following registers are banked by security:
- In a general-purpose register R13(SP)
- In a special register : MASK register (PRIMASK, BASEPRI, FAULTMASK)、CONTROL register 、 Stack pointer limit register (MSPLIM ,PSPLIM)
- System Control Space (SCS)

msr/mrs Instruction code
MRS and MSR In instruction coding bit[7] Indicates which set of registers is being operated on (Secure or NON-Secure)
Supplementary terms
RAZ:Read-As-Zero What you read is always 0
WI :Writes Ignoredx Write invalid
RAO:Read-As-Oned What you read is always 1
SBZP:Should-Be-Zero-or-Preserved on writes Write always 0
SBOP : Should-Be-One-or-Preserved on writes. Write always 1
UNK:unknown Unknown return value when reading or writing
See :ARM Glossary
cortex-A Trustzone and cortex-M Trustzone Comparison of :
stay cortex-M On , Dual system switching , It uses Secure Gateway (SG) Instructions , But only in special memory On the call SG, Even if NSC(non-secure callable)
Safe state switching
There are two ways to switch the security state :
- Direct function calls and returns (non-secure callable)
- abnormal / Interrupt entry and exit

3、 The partition of memory
If security extensions are implemented , be 4GB The memory space will be divided into Security and Non safety Memory area .
The safe memory space is further divided into two types : Security (S) And unsafe callable (NSC : Non-secure Callable)
NSC Is a special type of safe memory . This type of memory is Armv8-M The processor allows saving SG A type of memory for instructions , Enables software to transition from an unsafe state to a safe state .
By way of SG The function of the instruction is limited to NSC In the memory , The security software creator does not need to accidentally include... In the normal security memory SG Instruction or data share encoded values , contain NSC Memory location .
Usually NSC The memory area contains small branch jumps (entry points) Table of . To prevent unsafe applications from branching to invalid entry points , Here you are Secure Gateway (SG) Instructions .
When an unsafe program calls a function on the safe side :
- API The first instruction in must be SG Instructions .
- SG The instruction must be located by Security attribute unit (SAU :Security Attribution Unit) Or implement defined attribute units ( IDAU : Implementation Defined Attribution Unit) Defined NSC In the region .
introduce NSC The reason for memory is to prevent other binary data , Look up tables, for example , Its value and SG The opcodes of the instructions are the same , As the entry function to enter the safe state . By separating NSC and Secure Memory type , Containing binary data Secure Program code can be safely placed in Secure In the region , Without direct exposure to Normal The world , And only use NSC A valid entry point in memory .
4、Attribution units (SAU and IDAU)
- SAU :Security Attribution Unit
- IDAU : Implementation Defined Attribution Unit
When you reset SAU yes disabled Of
If SAU yes disabled Of , And the system does not contain IDAU, And because of reset The default state is Secure Security State, Then the system will not be able to switch to Non-secure state , All switches non-secure Security The operation of the state will produce Fault error 
SAU Summary of registers 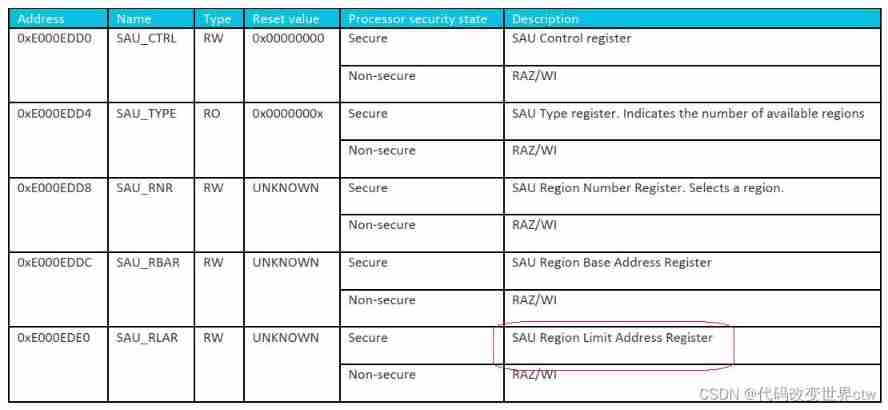

SAU After opening :
- Not in the SAU region Within the scope of , Are considered safe memory
- SAU_RLAR.NSC=0 Indicates unsafe memory
- SAU_RLAR.NSC=1 Express NSC Memory

5、Secure and Non-secure State switch of



边栏推荐
- Compiling minicom-2.7.1 under msys2
- Application circuit and understanding of BAT54C as power supply protection
- 【 unity】 Problems Encountered in Packaging webgl Project and their resolution Records
- Restrict cell input type and display format in CXGRID control
- 1000 fans ~
- Learning notes 51 single chip microcomputer keyboard (non coding keyboard and coding keyboard, scanning mode of non coding keyboard, independent keyboard, matrix keyboard)
- Laptop touch pad operation
- Barrykay electronics rushes to the scientific innovation board: it is planned to raise 360million yuan. Mr. and Mrs. Wang Binhua are the major shareholders
- Record: how to solve the problem of "the system cannot find the specified path" in the picture message uploaded by transferto() of multipartfile class [valid through personal test]
- C language conditional compilation routine
猜你喜欢
![[the second day of actual combat of smart lock project based on stm32f401ret6 in 10 days] GPIO and register](/img/eb/9bd411be74937371de0bbf3f04267e.jpg)
[the second day of actual combat of smart lock project based on stm32f401ret6 in 10 days] GPIO and register

Review the history of various versions of ITIL, and find the key points for the development of enterprise operation and maintenance

华为设备配置虚拟专用网FRR

ROS learning-7 error in custom message or service reference header file

STM32 IIC protocol controls pca9685 steering gear drive board
![[learning notes] xr872 GUI littlevgl 8.0 migration (file system)](/img/9b/0bf88354e8cfdbcc1ea91311c9a823.jpg)
[learning notes] xr872 GUI littlevgl 8.0 migration (file system)

C language compressed string is saved to binary file, and the compressed string is read from binary file and decompressed.

Build MySQL environment under mac
![[learning notes] xr872 audio driver framework analysis](/img/1a/008a89f835dc1b350a1f1ff27bee00.jpg)
[learning notes] xr872 audio driver framework analysis
![[pytorch]fixmatch code explanation - data loading](/img/0f/1165dbe4c7410a72d74123ec52dc28.jpg)
[pytorch]fixmatch code explanation - data loading
随机推荐
rsync 傳輸排除目錄
[pytorch]fixmatch code explanation (super detailed)
[open source] libinimini: a minimalist ini parsing library for single chip computers
Basic exercises of test questions Fibonacci series
Day 1 of the 10 day smart lock project (understand the SCM stm32f401ret6 and C language foundation)
Ctrip reshapes new Ctrip
Get started quickly cmake
反爬虫策略(ip代理、设置随机休眠时间、哔哩哔哩视频信息爬取、真实URL的获取、特殊字符的处理、时间戳的处理、多线程处理)
柏瑞凱電子沖刺科創板:擬募資3.6億 汪斌華夫婦為大股東
Differences between constants and variables (detailed description) (learning note 3 -- variables and constants)
【Unity】打包WebGL項目遇到的問題及解决記錄
STM32 IIC protocol controls pca9685 steering gear drive board
Leetcode daily question - 890 Find and replace mode
cmake_ example
[keras] train py
[single chip microcomputer] single timer in front and back platform program framework to realize multi delay tasks
The scientific innovation board successfully held the meeting, and the IPO of Kuangshi technology ushered in the dawn
js获取元素
Padavan mounts SMB sharing and compiles ffmpeg
1000粉丝啦~