当前位置:网站首页>OSI seven layer model
OSI seven layer model
2022-07-05 15:24:00 【Nineteen (drag on and on)】
OSI Seven layer model
List of articles
Preface : Model
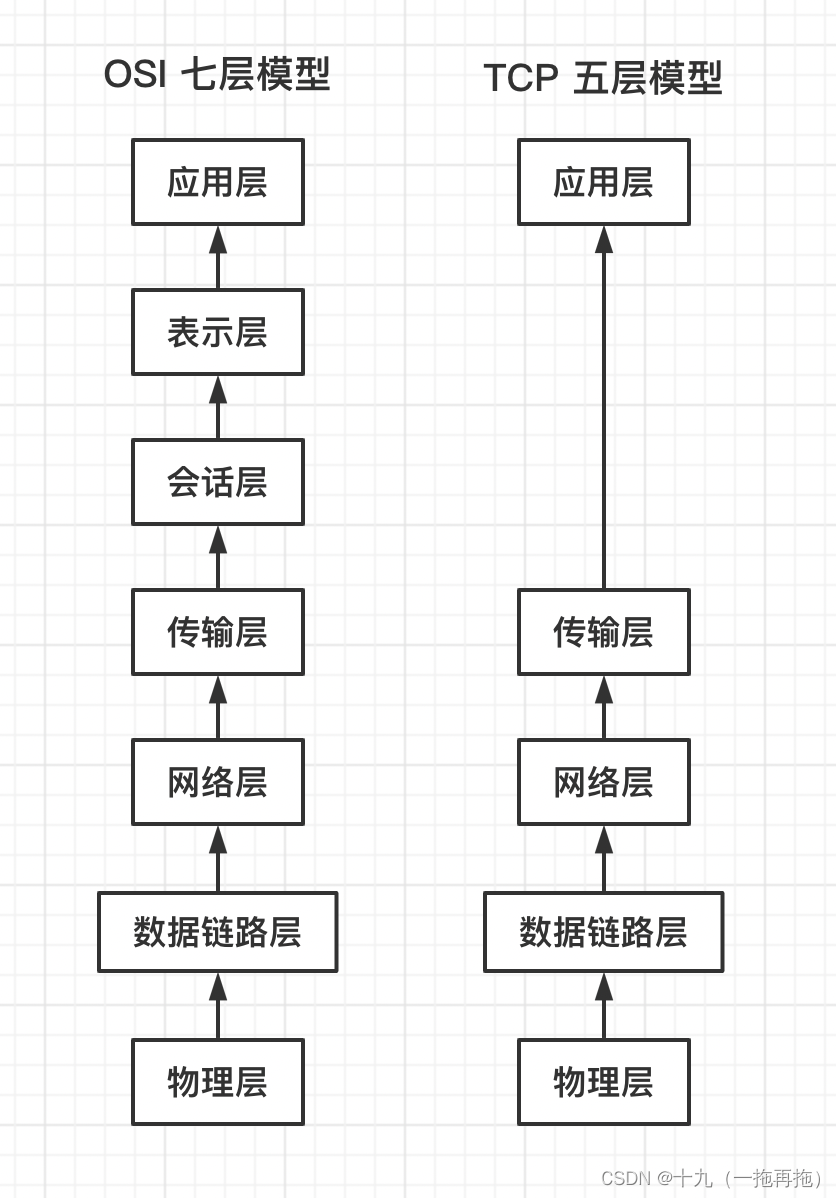
OSI Seven layer model :
- application layer
- The presentation layer
- The session layer
- Transport layer
- The network layer
- Data link layer
- The physical layer
TCP Five layer model :
- application layer
- Transport layer
- The network layer
- Data link layer
- The physical layer
1: The physical layer
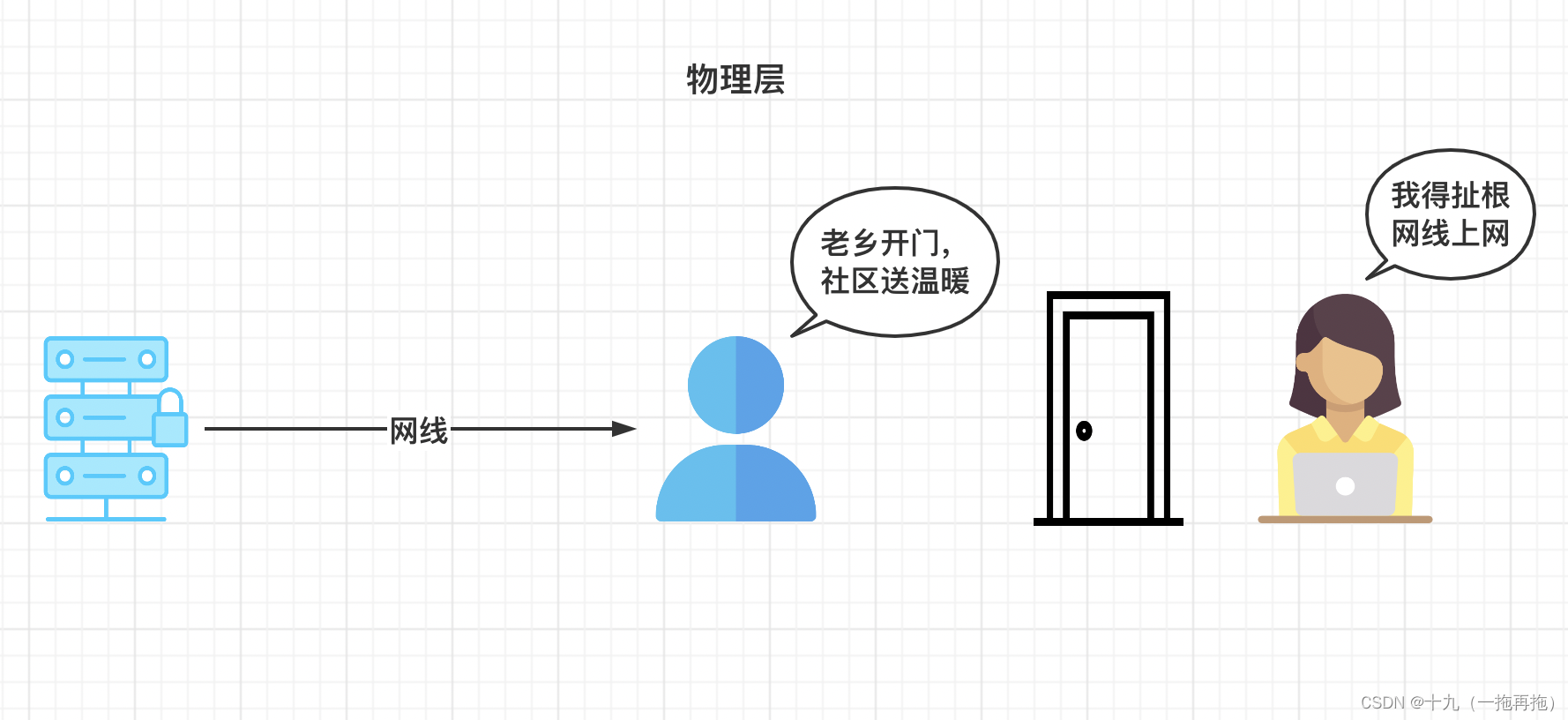
The physical layer defines the relationship between the device and the transmission medium . Such as copper cable 、 optical cable 、 voltage 、 Cable specification 、 A hub 、 Repeater 、 Network adapter, etc .
Main functions of physical layer : Establish connection or disconnection with the communication medium ; flow control ; Signal modulation or conversion between different equipment .
2: Data link layer
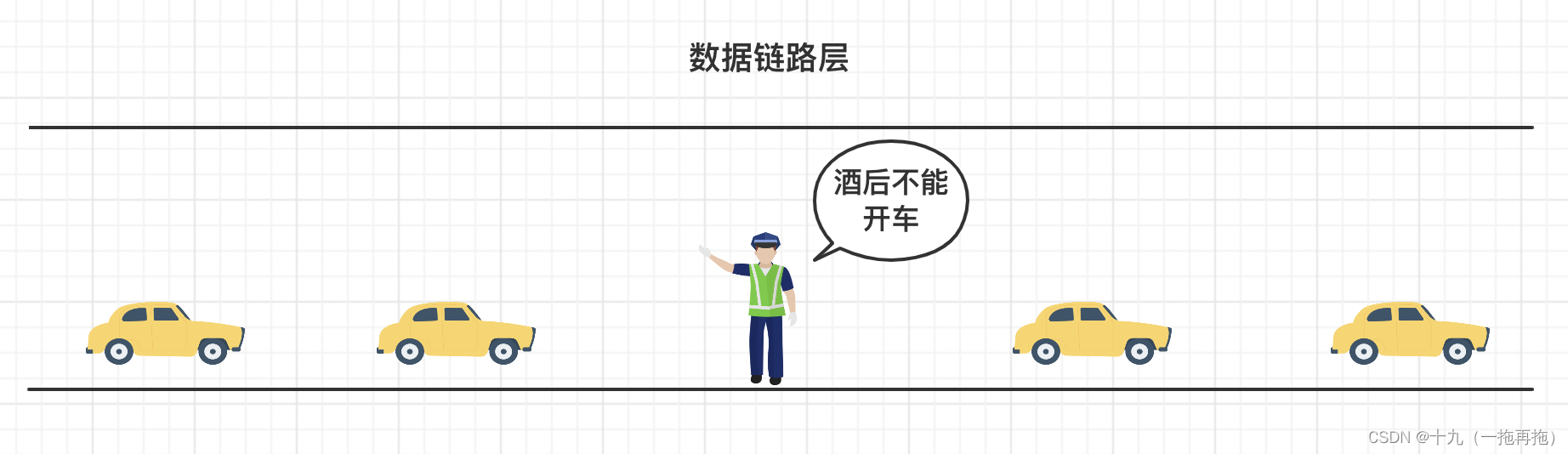
Data link layer : Main detection and correction The physical layer Possible errors .
3: The network layer
The network layer : Transmit variable length data sequences from source hosts on one network to target hosts on different networks , At the same time, ensure the request quality of the transport layer .
4: Transport layer
Transport layer : Provide services for communication between two host processes . Applications use this service to transport application layer messages .
5: The session layer
The session layer : Control the dialog connection between computers , establish 、 Manage and terminate connections between local and remote applications .
6: The presentation layer
The presentation layer : Enable communication applications to interpret the meaning of exchanged data . The service provided is data compression 、 Data encryption and data description .
7: application layer
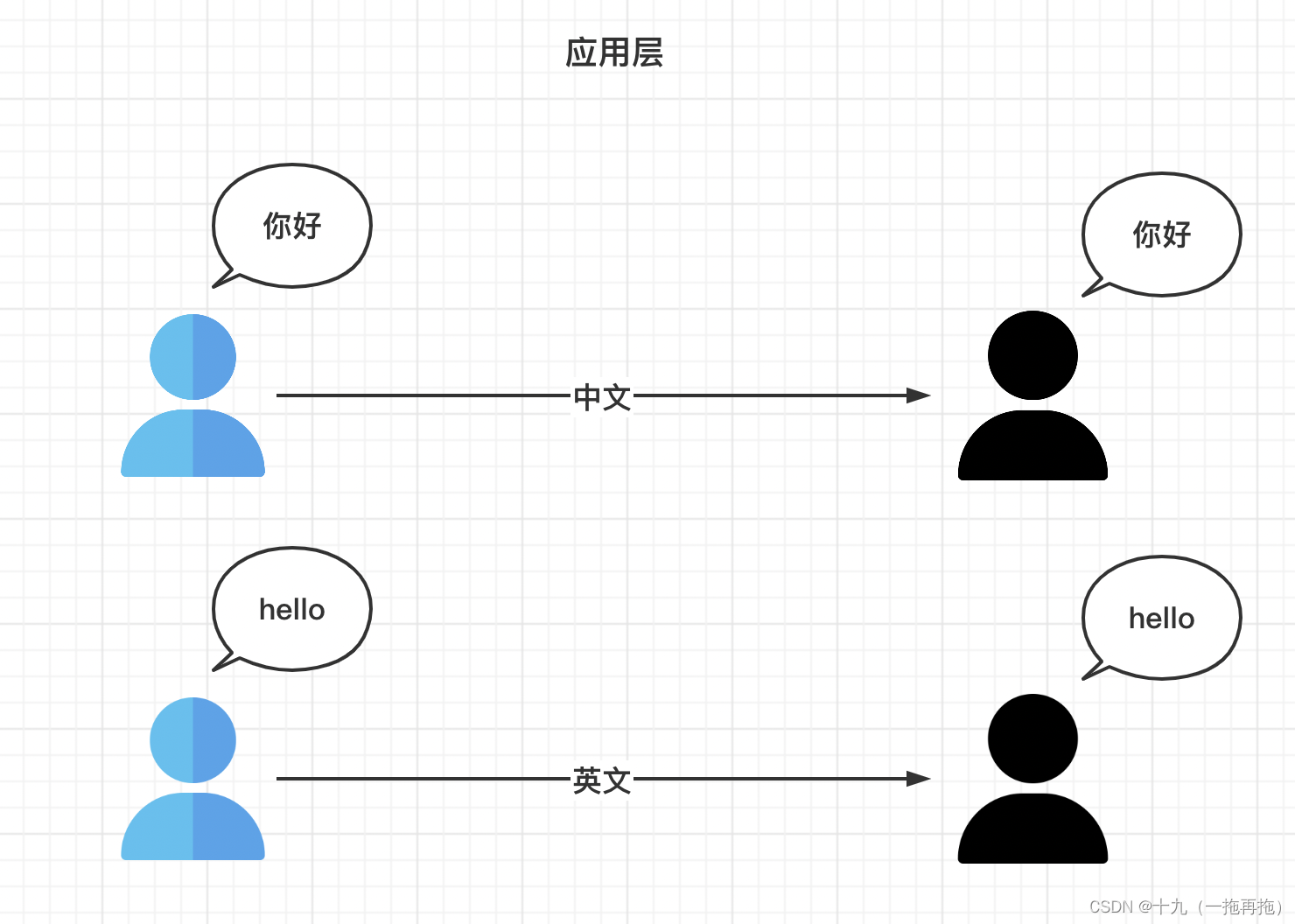
application layer : Defines the interaction rules between application processes , Provide services for different network applications through different application layer protocols . Such as HTTP agreement ,SMTP agreement .
边栏推荐
- Ctfshow web entry explosion
- Bubble sort, insert sort
- Visual task scheduling & drag and drop | scalph data integration based on Apache seatunnel
- Object. defineProperty() - VS - new Proxy()
- P1451 求细胞数量/1329:【例8.2】细胞
- Bugku's eyes are not real
- OSI 七层模型
- CODING DevSecOps 助力金融企业跑出数字加速度
- Photoshop plug-in - action related concepts - actions in non loaded execution action files - PS plug-in development
- 想问下大家伙,有无是从腾讯云MYSQL同步到其他地方的呀?腾讯云MySQL存到COS上的binlog
猜你喜欢
随机推荐
Hongmeng system -- Analysis from the perspective of business
12 MySQL interview questions that you must chew through to enter Alibaba
CODING DevSecOps 助力金融企业跑出数字加速度
Bubble sort, insert sort
Au - delà du PARM! La maîtrise de l'Université de Pékin propose diverse pour actualiser complètement le classement du raisonnement du NLP
Aike AI frontier promotion (7.5)
Creation and optimization of MySQL index
CSRF, XSS science popularization and defense
Bugku easy_ nbt
Good article inventory
计算中间件 Apache Linkis参数解读
How to paste the contents copied by the computer into mobaxterm? How to copy and paste
The difference between abstract classes and interfaces in PHP (PHP interview theory question)
Your childhood happiness was contracted by it
Redis distributed lock principle and its implementation with PHP (2)
go学习 ------jwt的相关知识
Stop B makes short videos, learns Tiktok to die, learns YouTube to live?
Common MySQL interview questions
Bugku's Eval
mapper.xml文件中的注释