当前位置:网站首页>Redis' transaction mechanism
Redis' transaction mechanism
2022-07-05 15:04:00 【Back end regular developers】
List of articles
When it comes to business , I believe we are all familiar , The transaction ACID Four characteristics , It is also often asked during the interview , But in general , We may think of transactions in traditional relational databases , Actually ,Redis It also provides a transaction mechanism , This blog will explain Redis Transaction mechanism of .
One 、 Transaction presentation
Redis Transaction provides a way to package multiple command requests , And then one time 、 A mechanism for executing multiple commands sequentially .
During the execution of the transaction , The server does not interrupt transactions to execute command requests from other clients , It will complete the execution of all commands in the transaction , Then you can process the command requests of other clients .
The figure below shows a Redis The execution of a transaction :
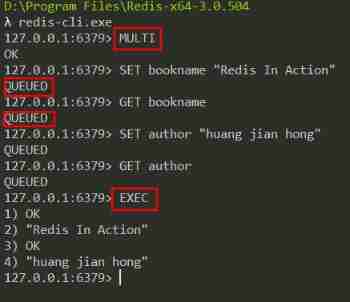
It can be seen that , Business to MULTI Command start , Then put multiple commands into the transaction , Finally by EXEC The command submits this transaction to the server for execution .
Two 、 Transaction implementation principle
A transaction will experience the following from the beginning to the end 3 Stages :
- The transaction start
- Order to join the team
- Transaction execution
2.1 The transaction start
MULTI The execution of the command marks the beginning of the transaction .
After executing the order , Client state flags Property will open REDIS_MULTI identification , Indicates that the client switches from non transactional state to transactional state .
2.2 Order to join the team
When a client is in a non transactional state , The command sent by this client will be executed by the server immediately :
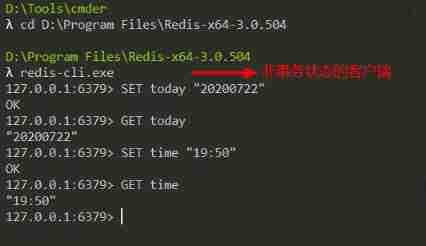
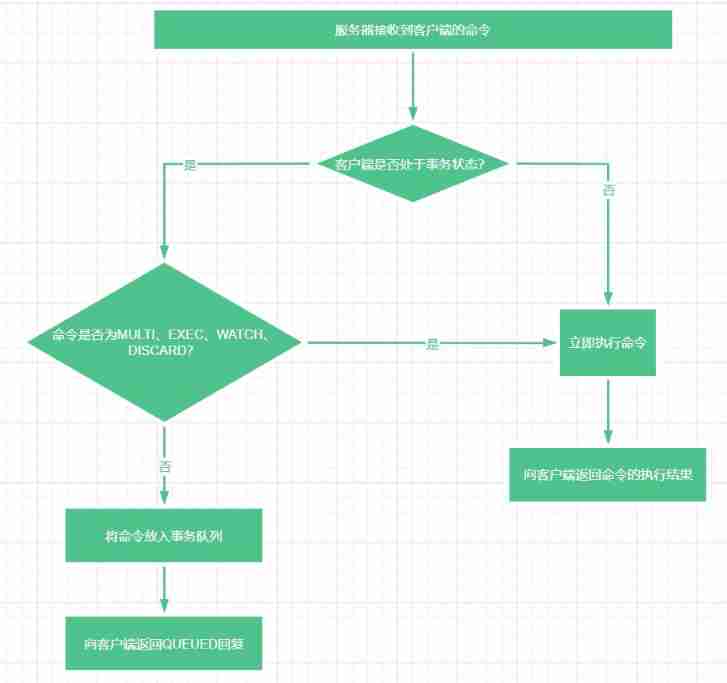
When a client is in a transactional state , The command sent by this client , Whether the server will execute immediately , Divided into the following 2 In this case :
- If the command sent by the client is
MULTI、EXEC、WATCH、DISCARDOne of the four commands 1 individual , The server will execute this command immediately . - If the command sent by the client is the above 4 Commands other than commands , The server will not execute this command immediately , Instead, put it in the transaction queue , And back to the client
QUEUEDreply .
The above process can be represented by the following flow chart :
First of all DISCARD command , This command is used to cancel the transaction , Give up executing all commands within the transaction block , As shown below :
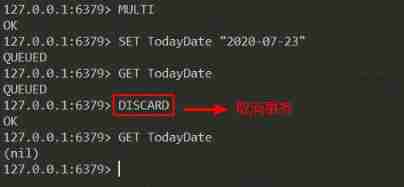
Then lift the transaction queue , Every Redis Each client has its own transaction state , The transaction state is stored in the client state mstates In the attribute :
The transaction state contains 1 Transaction queues and 1 Number of queued orders , As shown below :

The transaction queue is a multiCmd An array of types , Every... In the array multiCmd Structure stores information about a queued command , such as :
- Pointer to the command implementation function , Such as GET command 、SET command
- Arguments to the command
- Number of parameters
Transaction queue with fifo (FIFO) The way to keep the order to join the team .
2.3 Transaction execution
When a client in a transactional state executes EXEC On command , The server will traverse the transaction queue of this client , Execute all commands saved in the queue ( In first in first out order ), Then the result of executing the command is returned to the client at one time .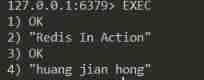
3、 ... and 、WATCH Command implementation principle
WATCH The command is used to monitor any number of database keys , And in EXEC When the order is executed , Detect whether the monitored key is modified , If it's modified , The server will refuse to execute the transaction , And return an empty reply to the client .
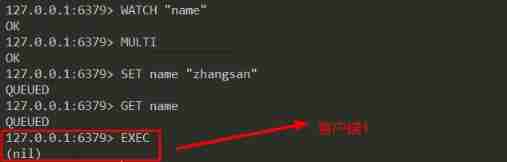
For better understanding , Let's make a demonstration , First , We open the client 1, perform WATCH Command monitor key “name”, And then start a transaction :
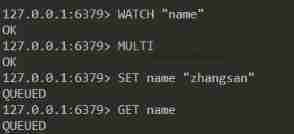
here , Don't execute EXEC command , Open client 2, Execute the following command to modify “name” Value of key :
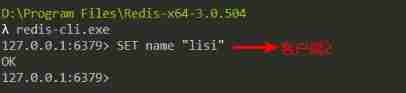
then , On the client side 1 perform EXEC On command , An empty reply will be returned , because “name” The value of the key is on the client 2 Has been modified :
that ,WATCH What is the principle of command implementation ? We start from 3 Analyze... In every way :
- Use
WATCHCommand monitor database key - Trigger of monitoring mechanism
- Determine whether the transaction is safe
3.1 Use WATCH Command monitor database key
Every Redis Databases are kept 1 individual watched_keys Dictionaries , The key of this dictionary is a certain quilt WATCH Database key for command monitoring , The value of a dictionary is a linked list , All clients monitoring the corresponding database key are recorded in the linked list .

for instance , If the client 1 Monitoring key “name”, client 2 Monitoring key “age”, that watched_keys The data stored in the dictionary is roughly as follows :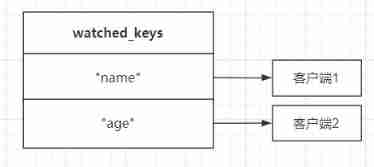
If the client at this time 3 Executed the following WATCH command :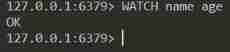
that watched_keys The data stored in the dictionary becomes :
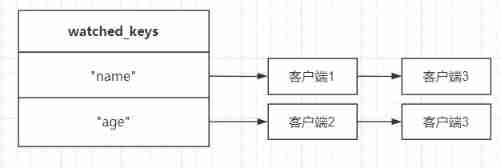
3.2 Trigger of monitoring mechanism
So here comes the question , since watched_keys The dictionary is stored by WATCH Command monitor key , So how is the monitoring mechanism triggered ?
The answer is all commands to modify the database , such as SET、LPUSH、SADD etc. , After the implementation, they will be right watched_keys Dictionary check , If a client is monitoring the key just modified by the command , Then all clients that monitor this key REDIS_DIRTY_CAS The logo will be opened , Indicates that the transaction security of the client has been compromised .
Pictured above is an example , If key “name” The value of is modified , So the client 1、 client 3 Of REDIS_DIRTY_CAS The logo will be opened .
3.3 Determine whether the transaction is safe
The last critical step is , When the server receives a client sent EXEC On command , The server will depend on whether the client is open REDIS_DIRTY_CAS Flag to decide whether to execute the transaction , The flow chart of judgment is as follows :
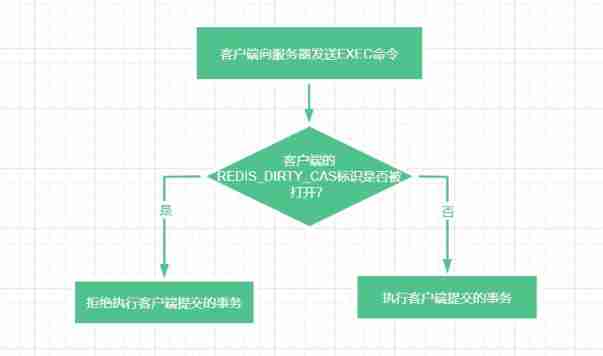
Four 、 Example of transaction execution failure
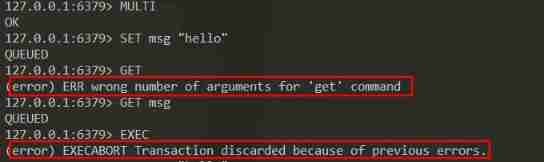
First of all, let's see No 1 An example , This transaction was rejected by the server due to an error in the command queue , All commands in the transaction will not be executed :
Look at the first 2 An example , A nonexistent command appeared when the transaction was queued , The server will refuse to execute this transaction :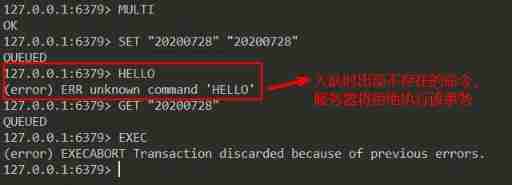
Look at the first 3 An example ,RPUSH An error is reported during the execution of the order , But the subsequent orders continue to be executed , And the previously executed commands have not been affected :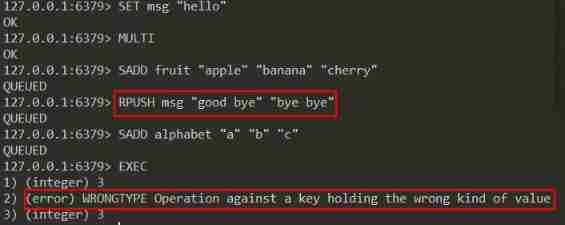
This example also shows Redis Transaction does not support rollback mechanism .
5、 ... and 、 summary
Redis Transaction provides a way to package multiple commands , And then one time 、 A mechanism for orderly execution ,
Its principle is that multiple commands will be queued into the transaction queue , Then press first in, first out (FIFO) Sequential execution ,
And the transaction will not be interrupted during execution , When all the commands in the transaction queue have been executed , It's the end of the business .
from :https://www.cnblogs.com/zwwhnly/p/13395106.html
边栏推荐
- 美团优选管理层变动:老将刘薇调岗,前阿里高管加盟
- 一键更改多个文件名字
- 数据库学习——数据库安全性
- 用 Go 跑的更快:使用 Golang 为机器学习服务
- sql server char nchar varchar和nvarchar的区别
- Anaconda uses China University of science and technology source
- 有一个强大又好看的,赛过Typora,阿里开发的语雀编辑器
- JMeter performance test: serveragent resource monitoring
- Install and configure Jenkins
- Machine learning notes - gray wolf optimization
猜你喜欢
两个BI开发,3000多张报表?如何做的到?

超越PaLM!北大碩士提出DiVeRSe,全面刷新NLP推理排行榜
12 MySQL interview questions that you must chew through to enter Alibaba
Talking about how dataset and dataloader call when loading data__ getitem__ () function
Crud of MySQL

Huiyuan, 30, is going to have a new owner
华为哈勃化身硬科技IPO收割机
Ctfshow web entry information collection

Ecotone technology has passed ISO27001 and iso21434 safety management system certification
CODING DevSecOps 助力金融企业跑出数字加速度
随机推荐
[12 classic written questions of array and advanced pointer] these questions meet all your illusions about array and pointer, come on!
Detailed explanation of usememo, memo, useref and other relevant hooks
Ecotone technology has passed ISO27001 and iso21434 safety management system certification
PostgreSQL 13 installation
Leetcode: Shortest Word Distance II
Jmeter性能测试:ServerAgent资源监控
Handwriting promise and async await
Interview shock 62: what are the precautions for group by?
Garbage collection mechanism of PHP (theoretical questions of PHP interview)
[recruitment position] Software Engineer (full stack) - public safety direction
Using tensorboard to visualize the training process in pytoch
qt creater断点调试程序详解
数据库学习——数据库安全性
Coding devsecops helps financial enterprises run out of digital acceleration
webRTC SDP mslabel lable
社区团购撤城“后遗症”
Easyocr character recognition
TS所有dom元素的类型声明
Photoshop plug-in action related concepts actionlist actiondescriptor actionlist action execution load call delete PS plug-in development
Interpretation of Apache linkage parameters in computing middleware