当前位置:网站首页>Encryption and decryption
Encryption and decryption
2022-07-04 04:57:00 【Lzg_ na】
List of articles
1. summary
Encryption is divided into One way encryption and Two way encryption
One way encryption : One way encryption is irreversible , After the ciphertext is generated, the original content cannot be obtained according to the ciphertext . Therefore, one-way encryption is often used to verify the integrity and originality of the content , Not for security . for example MD5 Algorithm
Two way encryption : Bidirectional encryption refers to the generation of ciphertext , It can be decrypted into plaintext . It is usually applied to secure transmission and permission Application . for example RSA Algorithm .
1.1 Introduction to bidirectional encryption
Bidirectional decryption can be roughly divided into Symmetric encryption and Asymmetric encryption Symmetric encryption : Encryption and decryption use the same secret key , Asymmetric encryption : Encryption and decryption use different keys , Encryption uses Private key , Decryption use Public key , It has to be used in pairs .
1.1.1 Symmetric encryption
- advantage : Symmetric encryption and decryption algorithms are faster , Suitable for encrypting large amounts of data .
- shortcoming : Because encryption and decryption use the same key , Easy to crack , A large number of keys are needed to encrypt and decrypt different messages .
1.1.2 Asymmetric encryption
- advantage : The public key is encrypted , The private key is decrypted . Or sign with the private key , Use public key to verify signature . High safety , Private key and public key are kept separately , No public key and key transmission .
- shortcoming : Asymmetric encryption is very performance consuming , Very, very .
At this point, we must talk about the role of public key and private key :
Public and private keys must appear in pairs , Both can be used for encryption , But you must use the other party to decrypt . Different scenarios use different .
- Public key encryption , Private key decryption : Ensure ciphertext transmission , Highlight confidentiality .
- Private key encryption , Public key decryption : Sign and verify , Ensure that the signature has not been modified , Highlight reality .
边栏推荐
- 【MATLAB】MATLAB 仿真模拟调制系统 — FM 系统
- Developing mqtt access program under QT
- 拼夕夕二面:说说布隆过滤器与布谷鸟过滤器?应用场景?我懵了。。
- MySQL indexes and transactions
- Intersection traffic priority, illustration of intersection traffic rules
- 2022年6月总结
- Unity 接入天气系统
- Self sharing of a graduate
- 【MATLAB】MATLAB 仿真 — 模拟调制系统 之 AM 调制过程
- 由于使用flash存放参数时,擦除掉了flash的代码区导致进入硬件错误中断
猜你喜欢
中职组网络安全—内存取证
中科磐云—D模块解析以及评分标准
Intersection traffic priority, illustration of intersection traffic rules
Capturing and sorting out external Fiddler -- Conversation bar and filter
附件六:防守工作簡報.docx
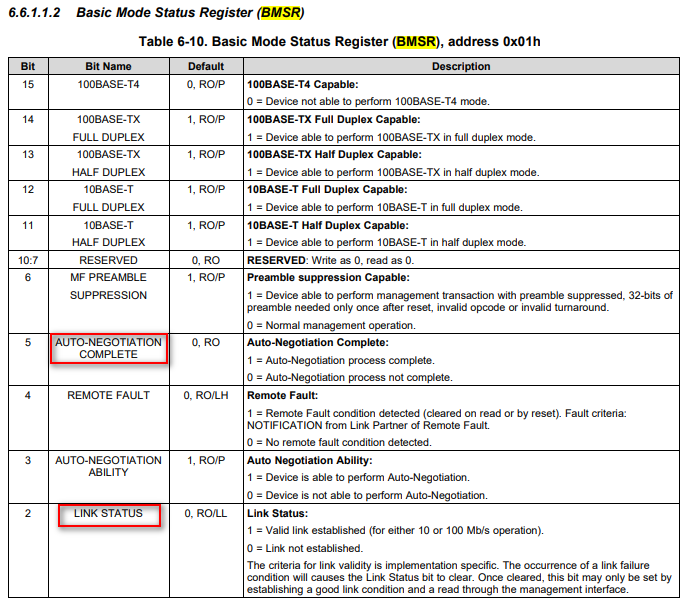
Dp83848+ network cable hot plug
Can closed data be deleted by DBCA? can
Drozer tool

2022广东省赛——编码信息获取 解析flag
Talking about JVM
随机推荐
Annex I: power of attorney for 202x XXX attack and defense drill
【MATLAB】MATLAB 仿真模拟调制系统 — SSB 系统
LeetCode136+128+152+148
What should a novice pay attention to when looking for an escort
【无标题】
Maui introductory tutorial series (5.xaml and page introduction)
RPC Technology
Unity中RampTex介绍和应用: 溶解特效优化
Change the background color of Kivy tutorial (tutorial includes source code)
[go] database framework Gorm
拼夕夕二面:说说布隆过滤器与布谷鸟过滤器?应用场景?我懵了。。
Test cs4344 stereo DA converter
LeetCode136+128+152+148
Zhengzhou zhengqingyuan Culture Communication Co., Ltd.: seven marketing skills for small enterprises
Kivy tutorial custom fonts (tutorial with source code)
令人头痛的延时双删
Share some of my telecommuting experience
中科磐云—D模块解析以及评分标准
附件2-2保密承诺书.docx
附件二:攻防演练保密协议.docx