当前位置:网站首页>12.RNN应用于手写数字识别
12.RNN应用于手写数字识别
2022-07-07 23:11:00 【booze-J】
代码运行平台为jupyter-notebook,文章中的代码块,也是按照jupyter-notebook中的划分顺序进行书写的,运行文章代码,直接分单元粘入到jupyter-notebook即可。整体代码给出的注释还是挺简单明了的。这里我们以使用
SimpleRNN为例。 1.导入第三方库
import numpy as np
from keras.datasets import mnist
from keras.utils import np_utils
from keras.models import Sequential
from keras.layers import Dense
from keras.layers.recurrent import SimpleRNN
from tensorflow.keras.optimizers import Adam
2.加载数据及数据预处理
# 载入数据
# 数据长度-一行有28个像素
input_size=28
# 序列长度-一共有28行
time_steps=28
# 隐藏层cell个数
cell_size=50
# 载入数据
(x_train,y_train),(x_test,y_test) = mnist.load_data()
# (60000,28,28)
x_train = x_train/255.0
x_test = x_test/255.0
# 换one hot格式
y_train = np_utils.to_categorical(y_train,num_classes=10)
y_test = np_utils.to_categorical(y_test,num_classes=10)
3.训练模型
# 创建模型
model = Sequential()
# 循环神经网络
model.add(SimpleRNN(
units=cell_size,# 输出
input_shape=(time_steps,input_size),# 输入
))
# 输出层
model.add(Dense(10,activation="softmax"))
# 定义优化器 设置学习率为1e-4
adam = Adam(lr=1e-4)
# 定义优化器,loss function,训练过程中计算准确率
model.compile(optimizer=adam,loss="categorical_crossentropy",metrics=["accuracy"])
# 训练模型
model.fit(x_train,y_train,batch_size=64,epochs=10)
# 评估模型
loss,accuracy=model.evaluate(x_test,y_test)
print("test loss:",loss)
print("test accuracy:",accuracy)
代码运行结果: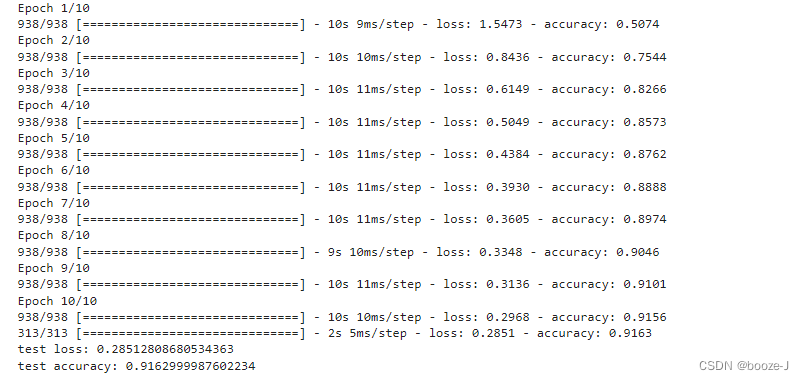
代码中需要注意的一些点,在代码注释中也给出了解释和提醒。从运行结果中可以看到RNN训练出来的模型在测试集上的准确率相对于10.CNN应用于手写数字识别中CNN训练出来的模型在测试集上的准确率效果要更差一些。
边栏推荐
- From starfish OS' continued deflationary consumption of SFO, the value of SFO in the long run
- letcode43:字符串相乘
- QT adds resource files, adds icons for qaction, establishes signal slot functions, and implements
- Marubeni official website applet configuration tutorial is coming (with detailed steps)
- Deep dive kotlin synergy (XXII): flow treatment
- Hotel
- 3 years of experience, can't you get 20K for the interview and test post? Such a hole?
- 炒股开户怎么最方便,手机上开户安全吗
- Vscode software
- 【愚公系列】2022年7月 Go教学课程 006-自动推导类型和输入输出
猜你喜欢
赞!idea 如何单窗口打开多个项目?

RPA cloud computer, let RPA out of the box with unlimited computing power?
Interface test advanced interface script use - apipost (pre / post execution script)
基于卷积神经网络的恶意软件检测方法
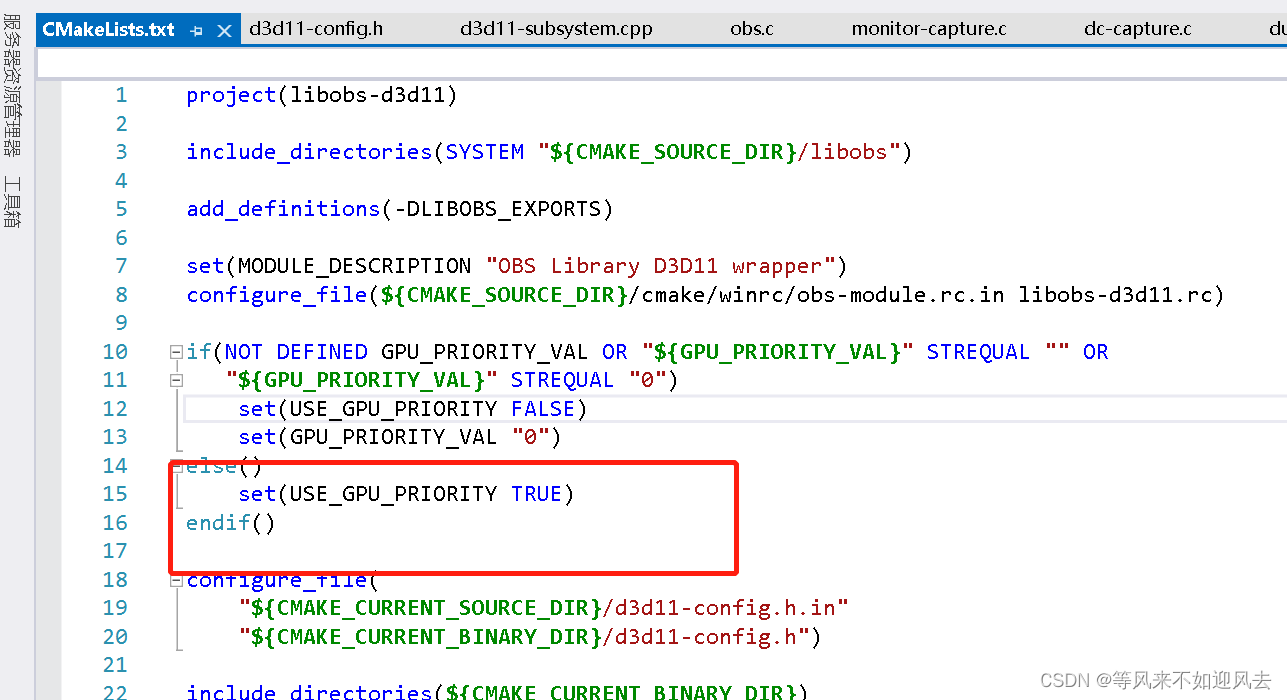
【obs】官方是配置USE_GPU_PRIORITY 效果为TRUE的
![[note] common combined filter circuit](/img/2f/a8c2ef0d76dd7a45b50a64a928a9c8.png)
[note] common combined filter circuit
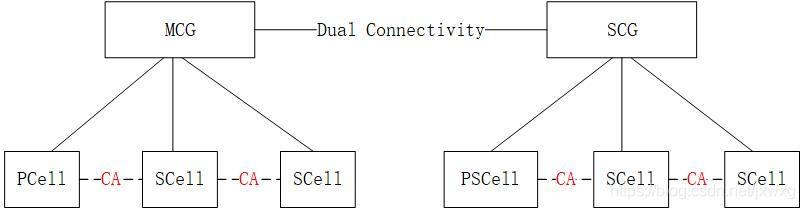
5g NR system messages
![[necessary for R & D personnel] how to make your own dataset and display it.](/img/50/3d826186b563069fd8d433e8feefc4.png)
[necessary for R & D personnel] how to make your own dataset and display it.
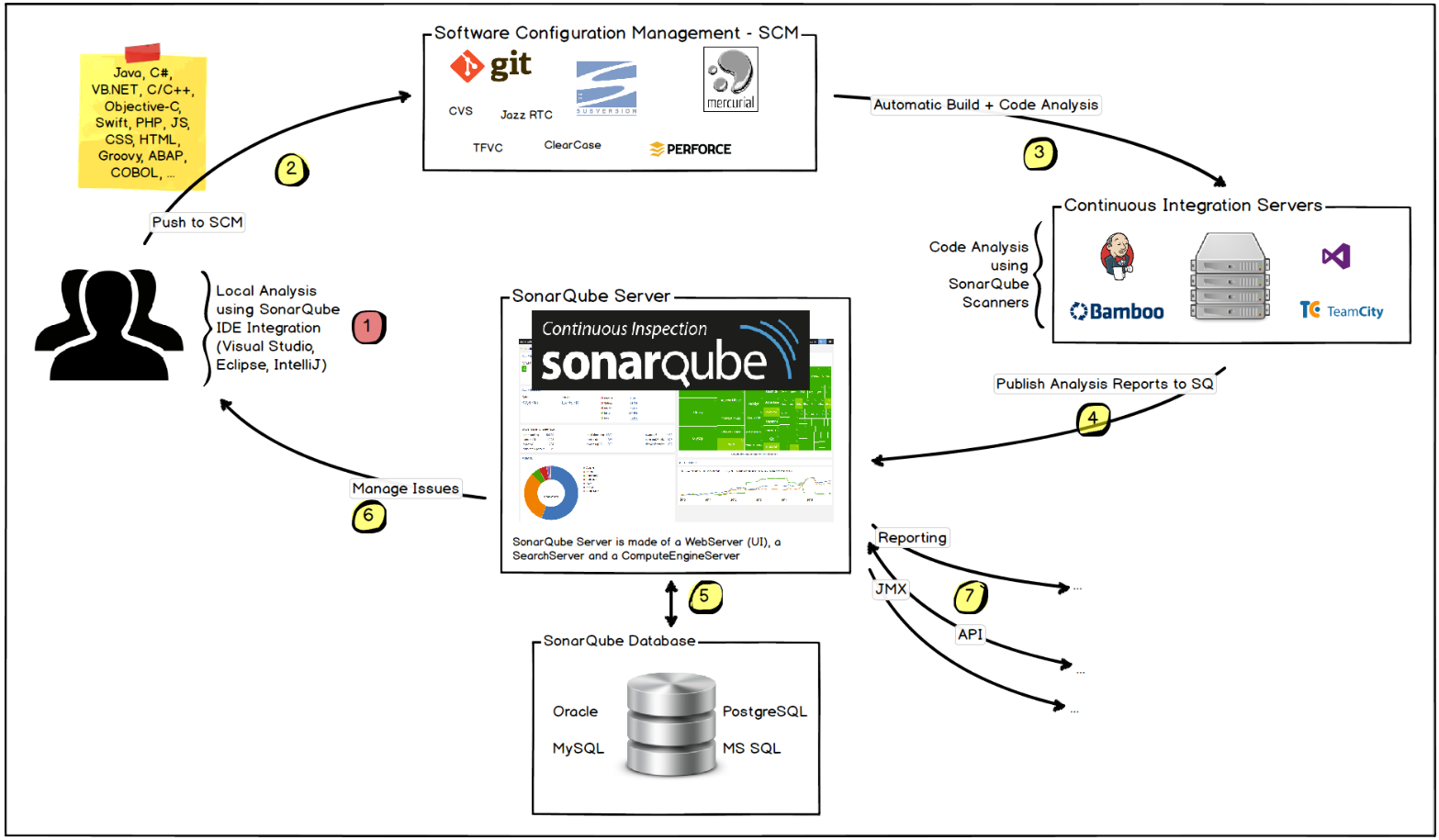
Jouer sonar

Codeforces Round #804 (Div. 2)(A~D)
随机推荐
串口接收一包数据
ABAP ALV LVC模板
Malware detection method based on convolutional neural network
Play sonar
德总理称乌不会获得“北约式”安全保障
Leetcode brush questions
NVIDIA Jetson测试安装yolox过程记录
Installation and configuration of sublime Text3
接口测试要测试什么?
How does the markdown editor of CSDN input mathematical formulas--- Latex syntax summary
Reentrantlock fair lock source code Chapter 0
攻防世界Web进阶区unserialize3题解
【愚公系列】2022年7月 Go教学课程 006-自动推导类型和输入输出
丸子官网小程序配置教程来了(附详细步骤)
New library launched | cnopendata China Time-honored enterprise directory
Codeforces Round #804 (Div. 2)(A~D)
Which securities company has a low, safe and reliable account opening commission
[note] common combined filter circuit
哪个券商公司开户佣金低又安全,又靠谱
Operating system principle --- summary of interview knowledge points