当前位置:网站首页>【LeetCode】94. Middle order traversal of binary tree
【LeetCode】94. Middle order traversal of binary tree
2022-07-03 16:17:00 【onlywishes】


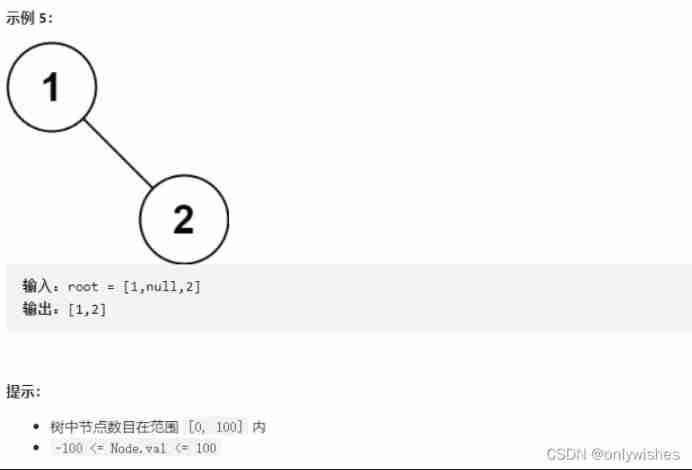
Their thinking :
( One )
The middle order of the binary tree is Left root right , First traverse the left half , Then the root node , And the right half .
The left half can be divided according to the initial state , The same is true for the right half , You can use recursion
Take the left node of the root node first and recurse , If the left node is empty, it means to the far left , At this time, this node is the root node of this layer , From left root to right , Add the root node without recursion to the stack , After recursion, the right child node of the root node , If not, return to
When implementing recursively , It's the function that calls itself , Nested layer by layer , operating system / Virtual machine automatically helps us use Stack To save each called function
Recursion is a tree structure , Literally, it can be understood as repetition “ Recurrence ” and “ Return to ” The process of , When “ Recurrence ” When you reach the bottom, you start “ Return to ”, The process is equivalent to the depth first traversal of the tree .
Call the process :
dfs(root.left)
dfs(root.left)
dfs(root.left)
by null return
Print nodes
dfs(root.right)
dfs(root.left)
dfs(root.left)
........
Recursive implementation
res = [] # Store node values
def dg(root):
if not root: # If the current node is empty , return , Add node value
return
dg(root.left) # Follow the left , Join root , Right way traversal
res.append(root.val)
dg(root.right)
dg(root) # Call yourself
return res( Two )
Use iteration : Activities that repeat the feedback process , The result of each iteration will be taken as the initial value of the next iteration .(A Repeated calls to B)
Iteration is a Ring structure , From the beginning , Every iteration goes through the loop , And update the status , Iterations until the end state is reached .
Explain : Start from the root node to the left node , Every node is stored in the stack , The last entry node is the leftmost node , And then out of the stack , Save its element value , View its right node , Some words , Push , Start from this node to the left node , If there is no right node , Keep going out of the stack , loop , Until all nodes are put into and out of the stack , end
if not root:
return []
res = [] # Store node values
stack = [] # Save the node temporarily , It's like a stack
cur = root # Set the pointer
while cur or stack: # When cur When the pointing value and stack are empty, there are no elements
while cur : # Add the path from root to left to the stack in turn
stack.append(cur)
cur = cur.left
node = stack.pop() # Reach the end , Just take out the value of the last node in the stack and add it to the result res in
res.append(node.val)
cur = node.right # Looking at the right child node of this node , loop
return res # When all nodes are added to the stack , After the last stack ,res边栏推荐
- Please be prepared to lose your job at any time within 3 years?
- Slam learning notes - build a complete gazebo multi machine simulation slam from scratch (II)
- Salary 3000, monthly income 40000 by "video editing": people who can make money never rely on hard work!
- First!! Is lancet hungry? Official documents
- Is it safe to open an account with tongdaxin?
- 用同花顺炒股开户安全吗?
- Getting started with Message Oriented Middleware
- Redis installation under windows and Linux systems
- Record a jar package conflict resolution process
- [redis foundation] understand redis master-slave architecture, sentinel mode and cluster together (Demo detailed explanation)
猜你喜欢
Low level version of drawing interface (explain each step in detail)
记一次jar包冲突解决过程
Slam learning notes - build a complete gazebo multi machine simulation slam from scratch (4)

How to thicken the brush in the graphical interface

“用Android复刻Apple产品UI”(2)——丝滑的AppStore卡片转场动画
Uploads labs range (with source code analysis) (under update)
TCP拥塞控制详解 | 3. 设计空间

NFT新的契机,多媒体NFT聚合平台OKALEIDO即将上线
![[proteus simulation] 74hc595+74ls154 drive display 16x16 dot matrix](/img/d6/3c21c25f1c750f17aeb871124e80f4.png)
[proteus simulation] 74hc595+74ls154 drive display 16x16 dot matrix

Embedded development: seven reasons to avoid open source software
随机推荐
[combinatorics] summary of combinatorial identities (eleven combinatorial identities | proof methods of combinatorial identities | summation methods)*
在ntpdate同步时间的时候出现“the NTP socket is in use, exiting”
ThreeJS 第二篇:顶点概念、几何体结构
特征多项式与常系数齐次线性递推
相同切入点的抽取
pyinstaller不是内部或外部命令,也不是可运行的程序 或批处理文件
Go language self-study series | if else if statement in golang
MongoDB 的安装和基本操作
Unity project optimization case 1
NSQ源码安装运行过程
Brush questions -- sword finger offer
Getting started with Message Oriented Middleware
工资3000,靠“视频剪辑”月入40000:会赚钱的人,从不靠拼命!
Expression of request header in different countries and languages
Thinking about telecommuting under the background of normalization of epidemic | community essay solicitation
Slam learning notes - build a complete gazebo multi machine simulation slam from scratch (I)
近视:摘镜or配镜?这些问题必须先了解清楚
用同花顺炒股开户安全吗?
SVN使用规范
Interviewer: how does the JVM allocate and recycle off heap memory