当前位置:网站首页>Create files, file permissions, ownership, and sticky bits
Create files, file permissions, ownership, and sticky bits
2022-07-25 21:39:00 【51CTO】
If you need to create a file of a given size , have access to dd command .
dd Will put the given input , Clone a copy and write it to the output .
stdin、 Both device files and ordinary files can be used as input ,stdout、 Device files and ordinary files can also be used as output .
if Represents the input file ,/dev/zero It's a character device , Will keep coming back 0 Value bytes .
of Represents the output file .
bs Represents the block size ,count Number of Representatives , Multiplying the two is the file size .
The unit of measure of block size :
c byte 1B
w word 2B
b block 512B
k kilobytes 1024B
M Megabytes 1024KB
G 1024MB
dd Command can be used to test the operation speed of memory .
Linux Every file in the system is associated with multiple permission types . In these permissions , It usually includes three types of permissions , user 、 User groups and other entities .
user user It's the owner of the document , User group group It's a collection of multiple users , The system allows these users to access files in some form , Other users others Is any user other than these two .
Command ls -l You can list the permissions of the file , The first column of output results is often as follows :
-rw-r--r--
drwxr-xr-x
The first letter indicates the type of file :
-: Ordinary documents
d: Catalog
c: Character device
b: Block device
l: A symbolic link
s: Socket
p: The Conduit
The remaining nine characters are divided into three groups , The first group of corresponding users user jurisdiction , The second group corresponds to the user group group jurisdiction , The third group corresponds to other users others jurisdiction .
The three characters of each group of permissions correspond to the file reading 、 Write and executable permissions , If permission is specified , Will write the corresponding characters , If you don't have permission , It will say “-”.
The first character corresponds to the read permission , If it can be read , Just write “r”.
The second character corresponds to write permission , Can rewrite , Just write “w”.
The third character corresponds to the executable permission , Executable , Just write “x”.
user user Another one is called setuid(S) Authority , Appears in executable permissions x Location .setuid Permissions allow users to execute executables with the permissions of their owners , Form the following :
-rwS------
The directory is also read 、 Write and execute permissions , However, the read permission of the directory is to allow reading the list of files and subdirectories in the directory , Write permission allows you to create or delete files or subdirectories in a directory , Execution permission is to allow access to files and subdirectories in the directory .
The permissions of the second and third groups are the same as those of the user group . However, there is no user group setuid Of , The corresponding is setgid. It allows files to be executed with the same valid group permissions as the group of the directory owner . Form the following :
----rwS---
No other users setuid and setgid.
The directory has a special permission , It is called viscous position (sticky bit), You can understand it as write protection , When a directory has the sticky bit set , Only the user who created the directory can delete the files in the directory , Even user groups and other users have write permission . Sticky bits are written in other user permission groups x Location , Use t perhaps T To express . If there is only viscous bit , Namely t, If the execution permission and sticky bit are set at the same time , Just use T. Form the following :
-------rwt
边栏推荐
- Oxford University: many common insomnia drugs lack long-term safety data
- Handwriting distributed configuration center (1)
- Airtest solves the problem that a password needs to be entered in the process of "automatic packaging" (the same applies to random bullet frame processing)
- How to choose sentinel vs. hystrix current limiting?
- Stm3 (cubeide) lighting experiment
- Detailed explanation of Ag search tool parameters
- es6--解构赋值
- yuv422转rgb(422sp转420p)
- Array of arm disassembly
- 大厂面试官:千万级数据量的表,如何进行快速查询?
猜你喜欢

工作面试总遇秒杀? 看了京东 T8 大咖私藏的秒杀系统笔记, 已献出膝盖

Ijcai2022 meeting! Microsoft and other tutorials on domain generalization

IJCAI2022开会了! 微软等《领域泛化Domain Generalization》教程

SSH private key realizes login to remote target server

2022 latest examination questions and answers of eight members (standard staff) of Shanghai Architecture
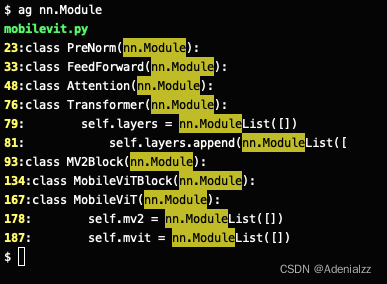
ag 搜索工具参数详解

Zero basic learning canoe panel (17) -- panel CAPL function

Test cases and defect report templates

Oxford University: many common insomnia drugs lack long-term safety data
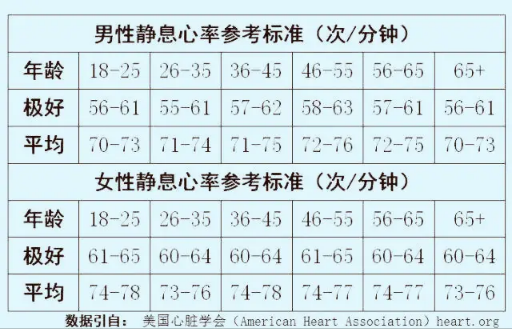
Programmer's Guide to health quenching 5: introduction to sports Basics
随机推荐
MPI学习笔记(二):矩阵相乘的两种实现方法
How to choose sentinel vs. hystrix current limiting?
[JS] the problem pointed by this
[interview: concurrent Part 24: multithreading: comprehensive exercise] sequence control
立创EDA——器件的创建01-电阻(二)
【leetcode天梯】链表 · 021 合并两个有序链表
yuv422转rgb(422sp转420p)
大厂面试官:千万级数据量的表,如何进行快速查询?
Huawei occupies half of the folding mobile phone market, proving its irreplaceable position in the high-end market
YUV422 to RGB (422sp to 420p)
ONEFLOW V0.8.0 officially released
How to evaluate hardware resources (number of CPUs, memory size) when Oracle migrates from small computers to x86 architecture? Is there a measurement index or company?
Fastjson deserialization vulnerability utilization analysis collection
Naming rules for BSP of Quanzhi chip
Rent two or three things
工作面试总遇秒杀? 看了京东 T8 大咖私藏的秒杀系统笔记, 已献出膝盖
IJCAI2022开会了! 微软等《领域泛化Domain Generalization》教程
Database SQL statement exercise "suggestions collection"
Protobuf的简单使用
Autojs learning - file depth search