当前位置:网站首页>Hcip day 16 notes
Hcip day 16 notes
2022-07-03 22:38:00 【xiaoxiaoxyxz】
MPLS VPN To configure
establish VRF Space
[r2]ip vpn-instance a
[r2-vpn-instance-a]
To configure VRF Space
[r2-vpn-instance-a]route-distinguisher 100:100— To configure RD value
[r2-vpn-instance-a-af-ipv4]vpn-target 100:1 export-extcommunity — Configure outbound RT
[r2-vpn-instance-a-af-ipv4]vpn-target 100:2 import-extcommunity — Configure inbound RT
[r2-GigabitEthernet0/0/0]ip binding vpn-instance a---- The interface is bound to the corresponding VRF In the space
[r2]display ip routing-table vpn-instance a---- see VRF Spatial routing table
[r2]ping -vpn-instance a 192.168.2.1
[r2]ip route-static vpn-instance a 192.168.1.0 24 192.168.2.1---- Configure static routing in the spatial routing table
MP-BGP Jianlin
[r2]bgp 1
[r2-bgp]router-id 2.2.2.2
[r2-bgp]peer 4.4.4.4 as 1
[r2-bgp]peer 4.4.4.4 connect-interface LoopBack 0
[r2-bgp]ipv4-family vpnv4
[r2-bgp-af-vpnv4]peer 4.4.4.4 enable
MP-BGP Route Publishing
[r2-bgp]ipv4-family vpn-instance a
[r2-bgp-a]import-route direct
[r2-bgp-a]import-route static
[r2]display bgp vpnv4 vpn-instance a routing-table ---- Look inside the space BGP surface
[r2]display fib vpn-instance a— Look inside the space FIB surface
[r2]rip 1 vpn-instance a ---- stay VRF Start in space RIP process
[r2-rip-1]v 2
[r2-rip-1]network 192.168.2.0
[r4]ospf 2 vpn-instance b router-id 4.4.4.4---- stay VRF Start in space
ospf process
The three-tier architecture of the enterprise ---- Suggestions for building an enterprise network 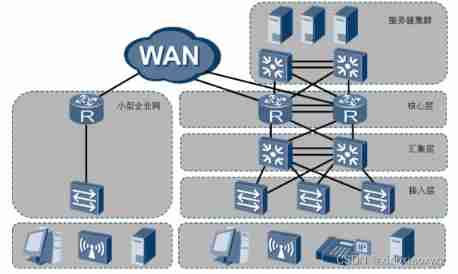
Campus network : factory 、 The government authority 、 Office buildings 、 campus 、 Park, etc , The networks built in these public places to realize data exchange can be called campus networks . Different campus networks may have different emphases .
Wireless is always the last kilometer of wired
Wireless connections need to rely on wireless devices that can transmit and receive wireless signals , These devices also need to be connected to the network through wired access .
AP— Wireless access point ( Finally, it also needs to be connected to wired devices )
WLAN: WLAN ----- In a broad sense, it refers to radio waves , laser , Infrared ray, etc. to replace part or all of the transmission media of the wired LAN, all the networks constructed .
Wireless networks are inherently flawed :
1、 Poor penetration of wireless signals — Use low frequency band transmission
Wireless uses Ethernet Technology ---- The reason why Ethernet transmission rate is fast ---- Frequency division — The civil wireless network uses the low-frequency band for data transmission , The congenital defect of low frequency band is poor penetration .
2、 The transmission rate of wireless network is related to the signal strength , and , Its transmission rate refers to the bidirectional rate
1000/80.85=106.25( The cable )
200/8/20.85=10.625( wireless )
3、 Wireless network transmission efficiency is low , Slower
Conflict domain : The scope of the conflict ----- A hub is in a conflict domain
CSMA/CD technology ---- Carrier sense multiple access / Conflict detection technology
WLAN is equivalent to in the same conflict domain , The wireless technology is used to solve the conflict CSMA/CA
CSMA/CA technology ---- Carrier sense multiple access / Conflict avoidance techniques — Its transmission efficiency is higher than CD Lower technology
The wireless device cannot detect the cause of the conflict : The dynamic range of wireless signal strength is very large , Often the received signal strength may be much less than the sent signal strength , This makes it difficult to detect conflicts ( It can increase hardware performance and improve strength )
CA Technology to avoid conflict :
1、 When no message is sent in the listening range , Don't send signals directly , It is , Set yourself a random timer first .
2、CSMA/CA The technology adopts stop flow control .
Access layer : The main purpose is to connect the terminal equipment to the network , Provide access port ----- Generally, layer-2 switches are used ( rely on MAC Address table realizes two layer forwarding )
Convergence layer : The main purpose is to gather the traffic collected by the access layer , Generally, three-tier switches are used — The layer-3 switch has a layer-2 interface similar to that used by ordinary layer-2 switches , It also has a three-tier interface similar to that used by routers or computers . The biggest difference between the second floor opening and the third floor opening is whether there is IP Address .
The layer-3 switch can pass through MAC Address table realizes two layer forwarding , Three layer forwarding can also be realized through routing table .
The core of the three-tier architecture of enterprise network ---- redundancy ---- Backup
1、 Line redundancy
2、 Equipment redundancy
3、 Gateway redundancy
4、UPS redundancy —UPS— Uninterruptible power supply ---- Ensure that the power supply of enterprise equipment reaches 6 individual 9 The usability of .99.9999%( Guarantee within one year 99.9999% Time without electricity ( Power failure at most 32 second ))
A real three-tier architecture must have redundancy .
Core layer : The main function is to complete the rapid forwarding of data between public and private networks ------ Generally, the router is selected as the core layer device .
VLAN
V---- fictitious
LAN— LAN — Networks with small geographical coverage
MAN---- Metropolitan area network
WAN---- Wide area network
LAN— Broadcast area
VLAN— Virtual LAN — Switches and routers work together , Logically divide the original broadcast domain into multiple .
First step : establish VLAN
[Huawei]display vlan— see VLAN Information
VID: VLAN ID ---- Distinguish and calibrate different VLAN----IEEE Organize and issue 802.1Q The standard requires —VID Must be by 12 Bit binary structure . Value range 0 -4095,0 and 4095 Is the reserved number , therefore , The available value range is 1 -4094
[Huawei]vlan 2— establish VLAN
[Huawei]vlan batch 4 to 100— Batch creation VLAN
[Huawei]undo vlan batch 4 to 10— Batch deletion VLAN
The second step : Put the interface into VLAN( Two-layer switch )
VID Configure the interface mapped to the switch , Realization VLAN Division ----- First floor VLAN/ Physics VLAN
VID Configure the mapping to data MAC Address , Realization VLAN Division — On the second floor VLAN
VID Configure the type fields mapped to the data (type), Realization VLAN Division ----- Three layers VLAN

VLAN Can also be based on IP Address division , It can even be done according to the strategy VLAN Divide .
802.1Q Standard design VLAN The label of , By 4 Bytes make up , It includes 12 Bit VID, Used to distinguish between different VLAN Of traffic . And add this label to Ethernet Ⅱ Type frame source MAC Between address and type fields .
802.1Q The standard stipulates , Frames with labels are called tagged Frame or or 802.1Q frame , Frames without labels are called untagged frame
According to this feature , We call the link between the switch and the computer ACCESS link , also ,ACCESS The interface on the switch side of the link is called ACCESS Interface .ACCESS The link can only pass through untagged frame , also , These frames can only belong to the same VLAN. We call the link between switches trunk link ,trunk The interfaces at both ends of the link are called trunk Interface .trunk The link is allowed to pass through tagged frame , And these frames can belong to multiple VLAN.
The third step : To configure trunk main rd
The second step is configuration
[sw1-GigabitEthernet0/0/1]port link-type access
[sw1-GigabitEthernet0/0/1]port default vlan 2
[sw1]port-group group-member GigabitEthernet 0/0/3 GigabitEthernet 0/0/4
[sw1-port-group] — Create an interface group
Step 3 configuration
[sw1-GigabitEthernet0/0/5]port link-type trunk
[sw1-GigabitEthernet0/0/5]port trunk allow-pass vlan all
Hybrid---- Hybrid interface
[SW1]display port vlan active------vlan Logical table of work
Link type---- Huawei equipment , The default interface type of all interfaces is hybridPVID — Huawei gives every interface , You need to configure a PVID, That is, the interface belongs to VID. All interfaces have not been changed PVID Default PVID The value is 1.
Huawei system regulations : All data entering the switch through the interface , All interfaces must be marked PVID The label of , in other words , All data inside the switch is labeled .
ACCESS Interface
1、 When ACCESS The interface received a message from the link untagged After the frame , Swap opportunities add... To this frame VID Interface for PVID yes tag, Then look at this VID Whether it is in the Allow list , If in , Then for what you get tagged Forward frames .
2、 When tagged The frame goes from other ports of the switch to one ACCESS After a mouth , Then the exchange opportunity checks the data in this frame tag Of VID Whether you are in your allow list , If in , Will tag After stripping, it will be forwarded from the link , If not , Then discard .
3、 If ACCESS The interface received a message from the link tagged After the frame , Then you can directly see the label of the data belongs to VID Whether you are in your allow list , Forward in , No longer discard .
trunk Interface
1、 When trunk The interface received a message from the link untagged frame , The switch first adds a... To the data frame VID by PVID Of tag, Then according to VID View the Allow List , If there is , Then forward , without , Then discard
2、 When one tagged The frame goes from other ports of the switch to one trunk After the port , If tag Of VID stay trunk In the allowed list of , Then forward ( If VID and trunk Interface PVID Phase at the same time , The label needs to be peeled off when transferring out , If not PVID The same label , Then directly transfer out ), If not , Throw away
3、 If trunk The port receives a message from the link tagged After the frame , View tag Medium VID, If in the Allow List , Then forward , be not in , Then discard
Different interfaces have different modification permissions when customizing the forwarding table .
ACCESS Modify permission of interface
You can modify PVID, You can also modify the Allow List ( however , The Allow list can only have one VID, And it has to be with PVID identical ), The export packaging method is only non packaging .
trunk Modify permission of interface
You can modify PVID, You can also modify the Allow List , The Allow list can be set to more than one VID, Export packaging is only packaging ( and PVID same VID If it is in the Allow list, it is fixed as no label )
[sw1-GigabitEthernet0/0/5]port trunk pvid vlan 2 ---- You can modify trunk Of PVID
hybrid — Modify permission of hybrid interface
You can modify PVID, You can also modify the Allow List , There can also be more than one allowed list VID, The packaging method can also be modified .
[sw1-GigabitEthernet0/0/1]port link-type hybrid
[sw1-GigabitEthernet0/0/1]port hybrid pvid vlan 2— modify hybrid Interface PVID
[sw1-GigabitEthernet0/0/1]port hybrid untagged vlan 2 3 4— Define allow list
边栏推荐
- Programming language (2)
- [actual combat record] record the whole process of the server being attacked (redis vulnerability)
- Yyds dry goods inventory Prometheus alarm Art
- SDMU OJ#P19. Stock trading
- Learning notes of raspberry pie 4B - IO communication (SPI)
- Sow of PMP
- IPhone development swift foundation 08 encryption and security
- On my first day at work, this API timeout optimization put me down!
- Blue Bridge Cup -- Mason prime
- [dynamic planning] counting garlic customers: the log of garlic King (the longest increasing public subsequence)
猜你喜欢
Go Technology Daily (2022-02-13) - Summary of experience in database storage selection

How to solve the problem of computer networking but showing no Internet connection

Covariance
C deep anatomy - the concept of keywords and variables # dry inventory #

Programming language (2)
2022 electrician (elementary) examination questions and electrician (elementary) registration examination
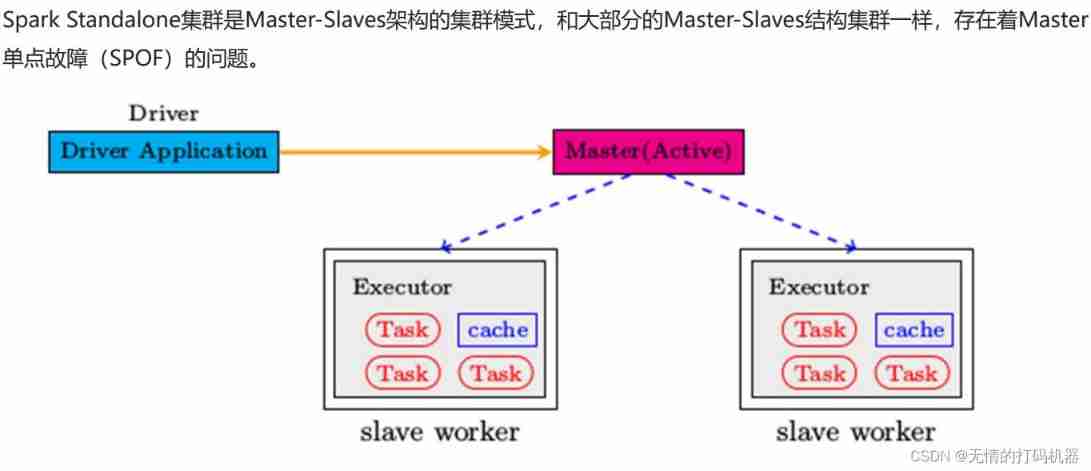
4 environment construction -standalone ha
How to connect a laptop to a projector
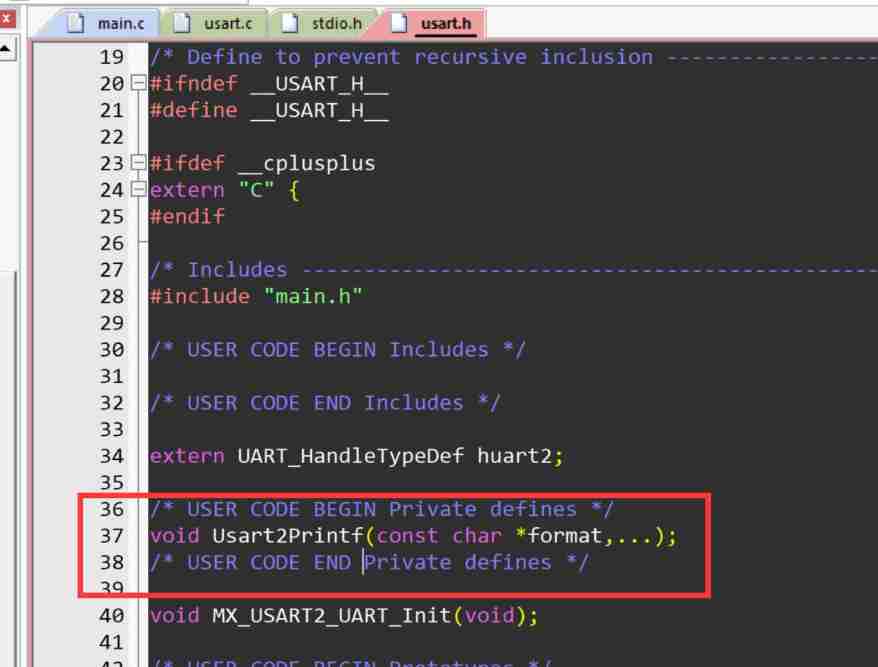
STM32 multi serial port implementation of printf -- Based on cubemx

In 2022, 6G development has indeed warmed up
随机推荐
On my first day at work, this API timeout optimization put me down!
Team collaborative combat penetration tool CS artifact cobalt strike
How to switch between dual graphics cards of notebook computer
Can you draw with turtle?
Programming language (2)
Rest reference
Wisdom tooth technology announced that it had completed the round D financing of US $100million and had not obtained a valid patent yet
How can enterprises and developers take advantage of the explosion of cloud native landing?
How to connect a laptop to a projector
Yyds dry goods inventory Spring Festival "make" your own fireworks
Buuctf, misc: sniffed traffic
Summary of fluent systemchrome
Pointer concept & character pointer & pointer array yyds dry inventory
pivot ROP Emporium
Bluebridge cup Guoxin Changtian single chip microcomputer -- hardware environment (I)
Code in keil5 -- use the code formatting tool astyle (plug-in)
[dynamic programming] Jisuan Ke: Jumping stake (variant of the longest increasing subsequence)
Teach you to easily learn the type of data stored in the database (a must see for getting started with the database)
webAssembly
string