当前位置:网站首页>User login function: simple but difficult
User login function: simple but difficult
2022-07-03 22:23:00 【Huawei cloud developer community】
Abstract : User login is just a common function , But its logic is not simple at all .
This article is shared from Huawei cloud community 《 User login of performance analysis TPS Low and CPU Filled with problem analysis 》, author :zuozewei .
User login is just a common function , But its logic is not simple at all . Because the login process needs to compare and verify personal information , During the verification process, the corresponding encryption algorithm must be called , Encryption algorithm is a function that requires high performance . The complex encryption algorithm has high security , But the performance is poor ; Uncomplicated encryption algorithm has good performance , But it's safe , This is a question of trade-offs .
Follow the design steps of the benchmark scenario of the test scheme , First, test the benchmark scenario of this interface .
● Problem phenomenon

As shown in the figure above , This phenomenon is becoming more and more obvious .
In the pressure measurement results TPS The average is 25 The average response time reached 993 ms.
● The analysis process
In terms of performance analysis logic , For the problem of long response time , The first thing to do is to split the time . Since this system has been deployed SkyWalking, Use it to see where time is mainly spent .

Look at the picture ,Tomcat Of SelfDuration The most. , In other words, time is almost consumed in the service itself .
● Global monitoring
First, check the resource level of the application server :

You can see 4C Of CPU Resources have been exhausted .
The container deployed here , Let's take a look at the resource usage of each container :

You can see that resources are mainly consumed by the service container .
● Service orientation analysis
First, enter the service container to view the resource consumption :

stay SkyWaking You can't see the complete call stack in , Consider connecting directly to the service Java The time consumption of the method in the process . Here we use Arthas Follow up .
Check out the busiest previous N Thread and print stack :
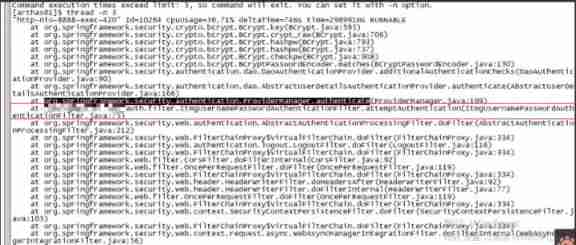
Here is the business code of the program .
therefore trace attemptAuthentication This method .
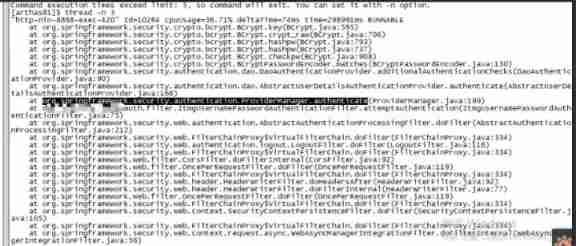
next trace authenticate This method .

Follow it layer by layer , Finally came here :

Since the crypt_raw The method takes a long time , Then decompile the source code to see what this paragraph is .
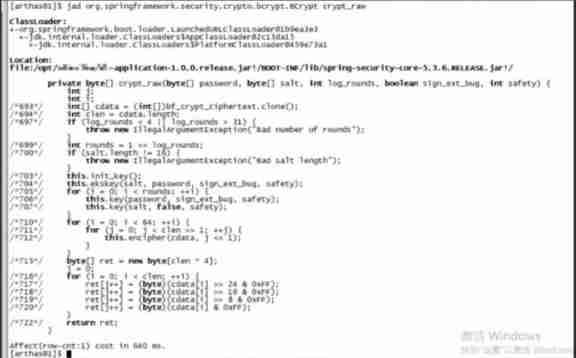
As you can see, here is an encryption algorithm BCrypt, So the conclusion is obvious BCrypt Although the encryption algorithm has high security , But the performance is poor .
● demo verification
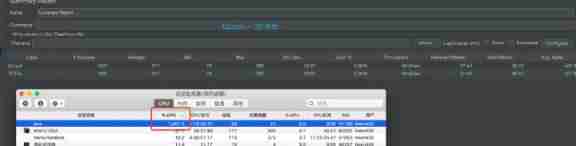
Use here SpringBoot Realization MD5 Encryption and BCrypt Encrypted instance .

JMeter Concurrent 20 MD5 Encryption result :

JMeter Concurrent 20 BCrypt Encryption result :
● Suggested optimization direction
Here's an explanation ,Bcrypt When encrypting , every time HASH The values are different , So it's very slow !
What exactly is Bcrypt Algorithm , You can refer to this article :https://www.jianshu.com/p/2b131bfc2f10
So that's the analysis , The optimization scheme is actually clear , That is to use faster encryption , Or remove the encryption algorithm .
Click to follow , The first time to learn about Huawei's new cloud technology ~
边栏推荐
- 2022 electrician (elementary) examination questions and electrician (elementary) registration examination
- The 14th five year plan and investment feasibility study report of China's industry university research cooperation Ⓧ 2022 ~ 2028
- How to obtain opensea data through opensea JS
- 油猴插件
- 1068. Consolidation of ring stones (ring, interval DP)
- 国泰君安证券开户是安全可靠的么?怎么开国泰君安证券账户
- How can enterprises and developers take advantage of the explosion of cloud native landing?
- Rest参考
- What is the difference between res.send() and res.end() in the node express framework
- How about agricultural futures?
猜你喜欢
![[automation operation and maintenance novice village] flask-2 certification](/img/9a/a9b45e1f41b9b75695dcb06c212a69.jpg)
[automation operation and maintenance novice village] flask-2 certification

On my first day at work, this API timeout optimization put me down!
How to switch between dual graphics cards of notebook computer

2022 G3 boiler water treatment registration examination and G3 boiler water treatment examination papers

How PHP gets all method names of objects
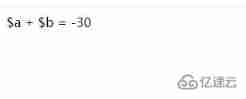
How PHP adds two numbers
![[Android reverse] application data directory (files data directory | lib application built-in so dynamic library directory | databases SQLite3 database directory | cache directory)](/img/b8/e2a59772d009b6ee262fb4807f2cd2.jpg)
[Android reverse] application data directory (files data directory | lib application built-in so dynamic library directory | databases SQLite3 database directory | cache directory)
Functions and differences between static and Const
Bluebridge cup Guoxin Changtian single chip microcomputer -- detailed explanation of schematic diagram (IV)
How to solve win10 black screen with only mouse arrow
随机推荐
How to store null value on the disk of yyds dry inventory?
Unique in China! Alibaba cloud container service enters the Forrester leader quadrant
Label coco format data and format data in the upper left corner and lower right corner are mutually converted
js demo 計算本年度還剩下多少天
Code in keil5 -- use the code formatting tool astyle (plug-in)
Can you draw with turtle?
Blue Bridge Cup Guoxin Changtian single chip microcomputer -- led lamp module (V)
[flax high frequency question] leetcode 426 Convert binary search tree to sorted double linked list
Pat grade A - 1164 good in C (20 points)
Buuctf, web:[geek challenge 2019] buyflag
Teach you how to run two or more MySQL databases at the same time in one system
Exness: the Central Bank of England will raise interest rates again in March, and inflation is coming
Leetcode week 4: maximum sum of arrays (shape pressing DP bit operation)
Team collaborative combat penetration tool CS artifact cobalt strike
Go Technology Daily (2022-02-13) - Summary of experience in database storage selection
WiFi 2.4g/5g/6g channel distribution
What are the common computer problems and solutions
Leetcode: a single element in an ordered array
Niuke winter vacation training camp 4 g (enumeration optimization, Euler power reduction)
Report on the development status and investment planning trends of China's data center industry Ⓡ 2022 ~ 2028